Method and device for identifying congestion status of data transmission channel
A congestion state and transmission channel technology, applied in digital transmission systems, transmission systems, data exchange networks, etc., can solve problems such as hardware or software complexity, high hardware requirements, and processing capacity limitations, and achieve data priority scheduling , Simplify the processing flow, and ensure the effect of service quality
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
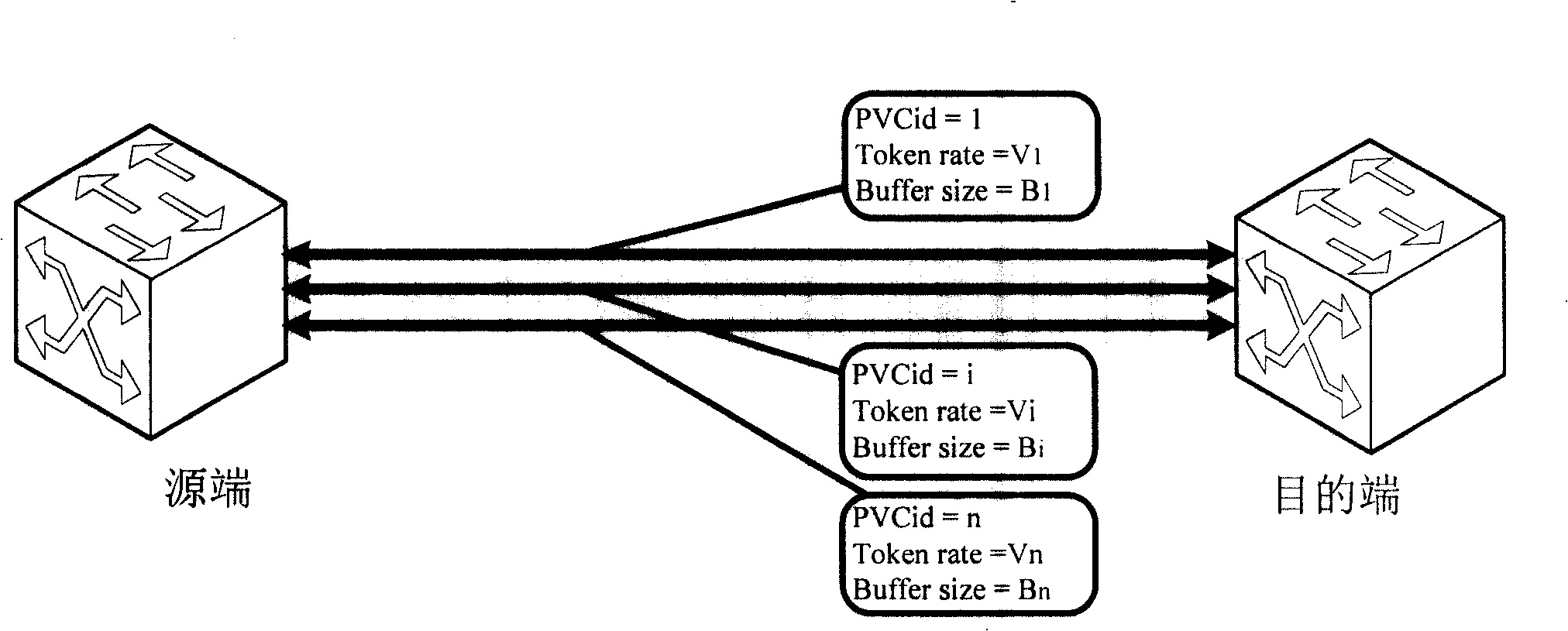
[0067] see figure 2 , is a schematic diagram of a network model in Embodiment 1. Data is transmitted between two endpoint network devices through the PVC data channel. In the figure, the source end sends data packets to the destination end. For example, the physical bandwidth between the two ends is 155Mbps. Each PVC is configured with a label (PVCid) to identify the channel, a corresponding token rate (Token rate), and a configuration Buffer queue capacity (Buffer size), etc., the above configuration parameters can be configured according to the ratio of the predetermined bandwidth allocation. For example, the configuration information of the three PVC channels in the figure are:
[0068] PVCid=1, Token rate=V1, Buffer size=B 1;
[0069] PVCid=i, Token rate=Vi, Buffer size=Bi;
[0070] PVCid=n, Token rate=Vn, Buffer size=Bn.
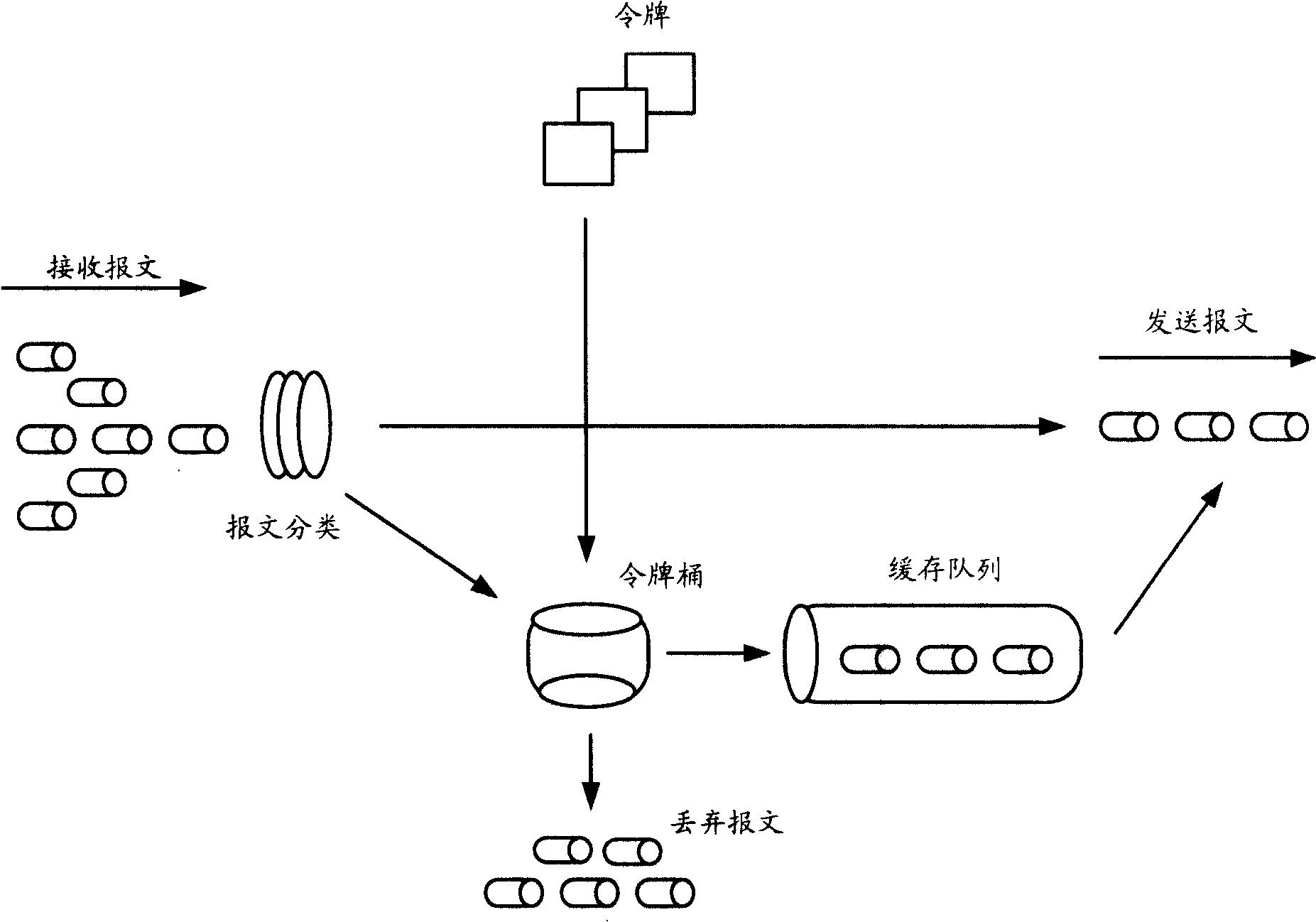
[0071] In this embodiment, on the basis of the existing ordinary token bucket mechanism, combined with the characteristics of AAL2 itself, the de...
specific Embodiment 2
[0081] Embodiment 1 processes the service data sent in a unified manner, while Embodiment 2 adopts different flow control methods according to the priority of data packets from the perspective of ensuring high-priority service quality.
Embodiment 2
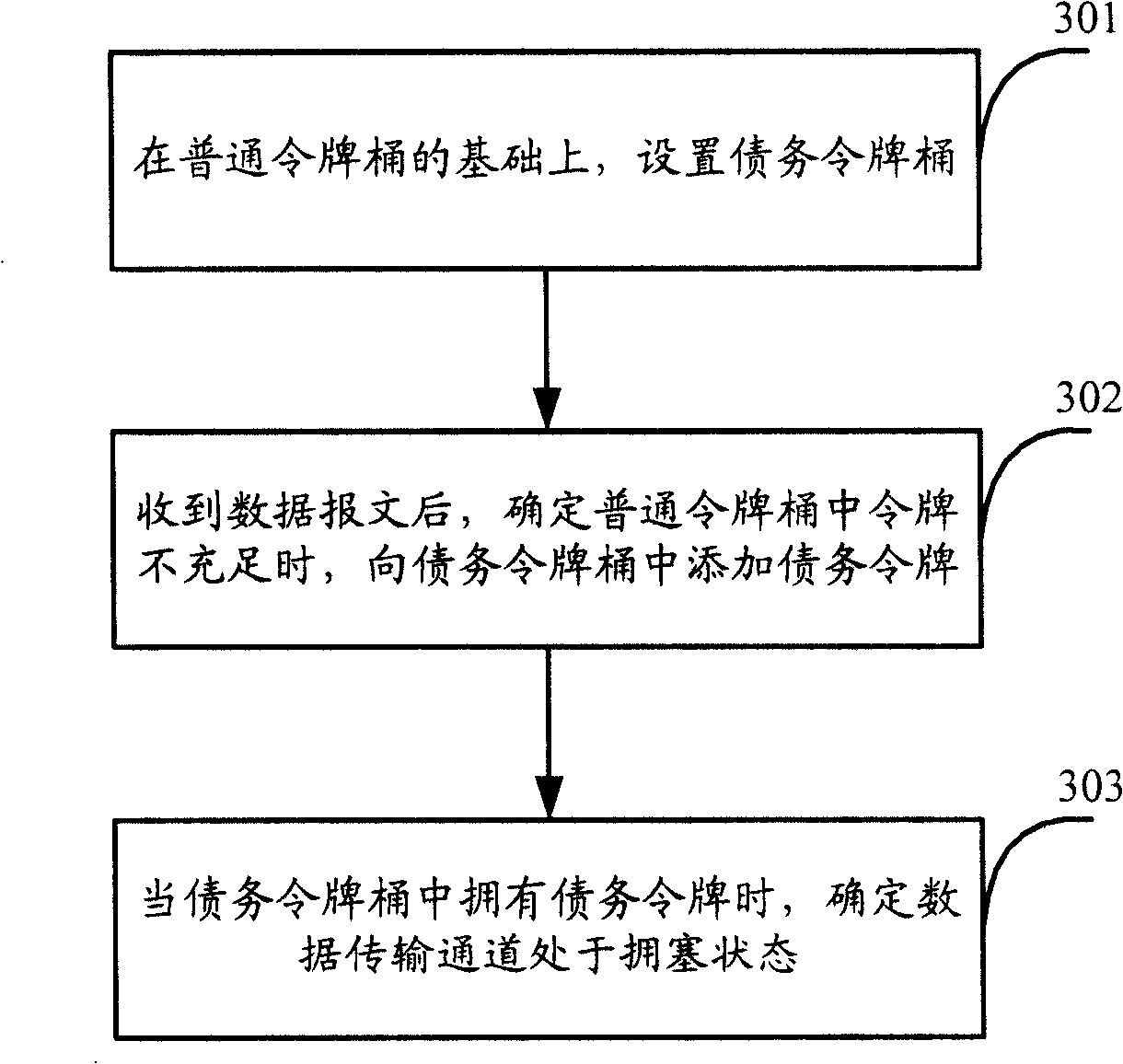
[0082] Embodiment 2 On the basis of Embodiment 1, high-priority messages can properly occupy idle bandwidth, thereby ensuring that high-priority messages can receive priority services; and low-priority messages are only debts in the debt token bucket. Only when the token has been repaid can it participate in scheduling, otherwise it will be cached or even discarded, so as to ensure that high-priority packets participate in scheduling first.
[0083] See Figure 4 , is the flow chart of Embodiment 2. Embodiment two includes:
[0084] Step 401: Check whether the data message is received, if so, execute step 402; otherwise, execute step 411;
[0085] Step 402: Check the CID priority corresponding to the message. For a high-priority message, perform step 403; for a low-priority message, perform step 406;
[0086] Step 403: Check whether there are enough tokens in the common token bucket? If yes, execute step 404; otherwise, execute step 405;
[0087] Step 404: Deduct the corr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com