Personal identification system and method
An identification and radio frequency identification technology, applied in the field of identification and anti-counterfeiting, can solve the problems of unguaranteed security, unguaranteed repeatability of identification, failure, etc. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
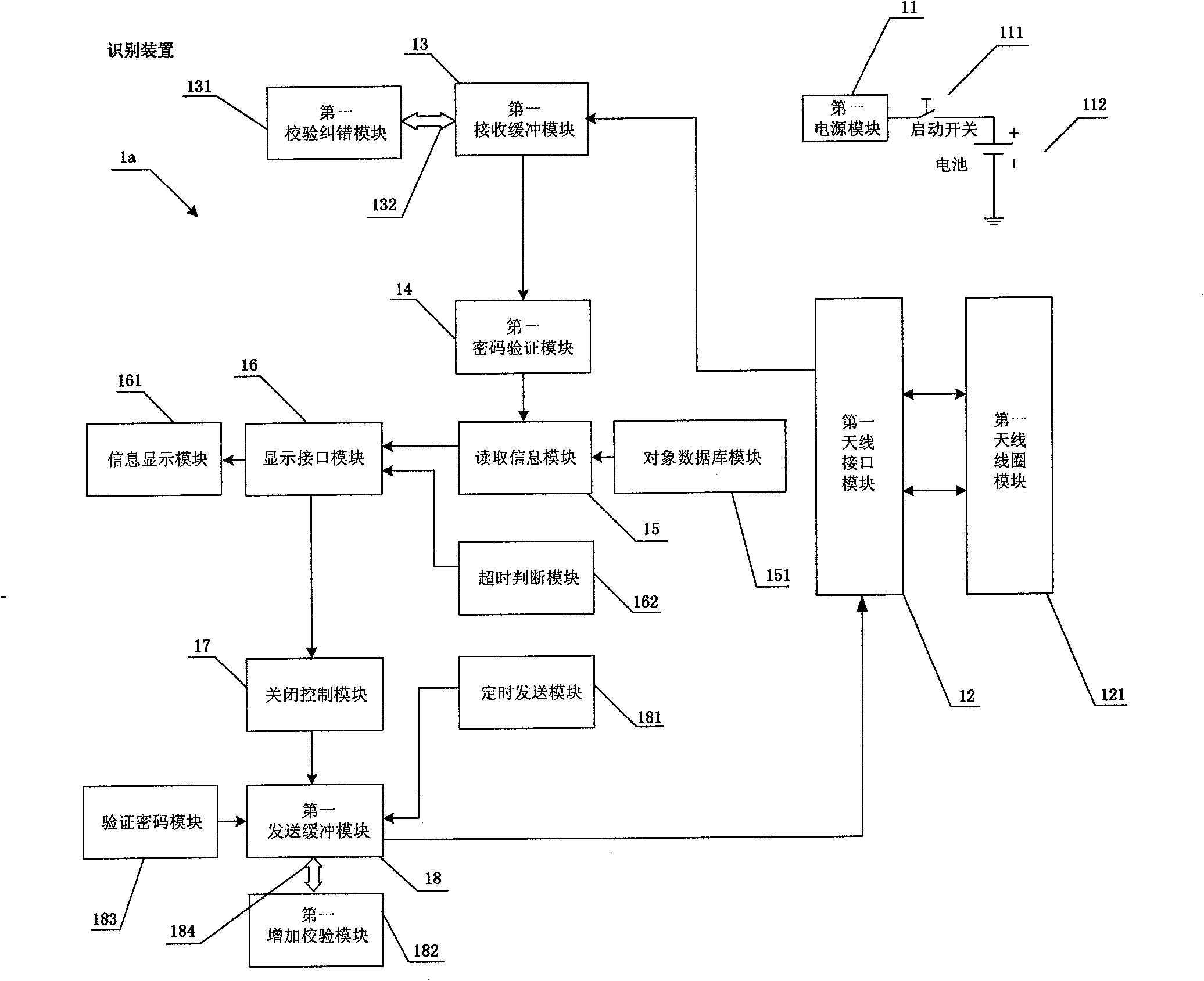
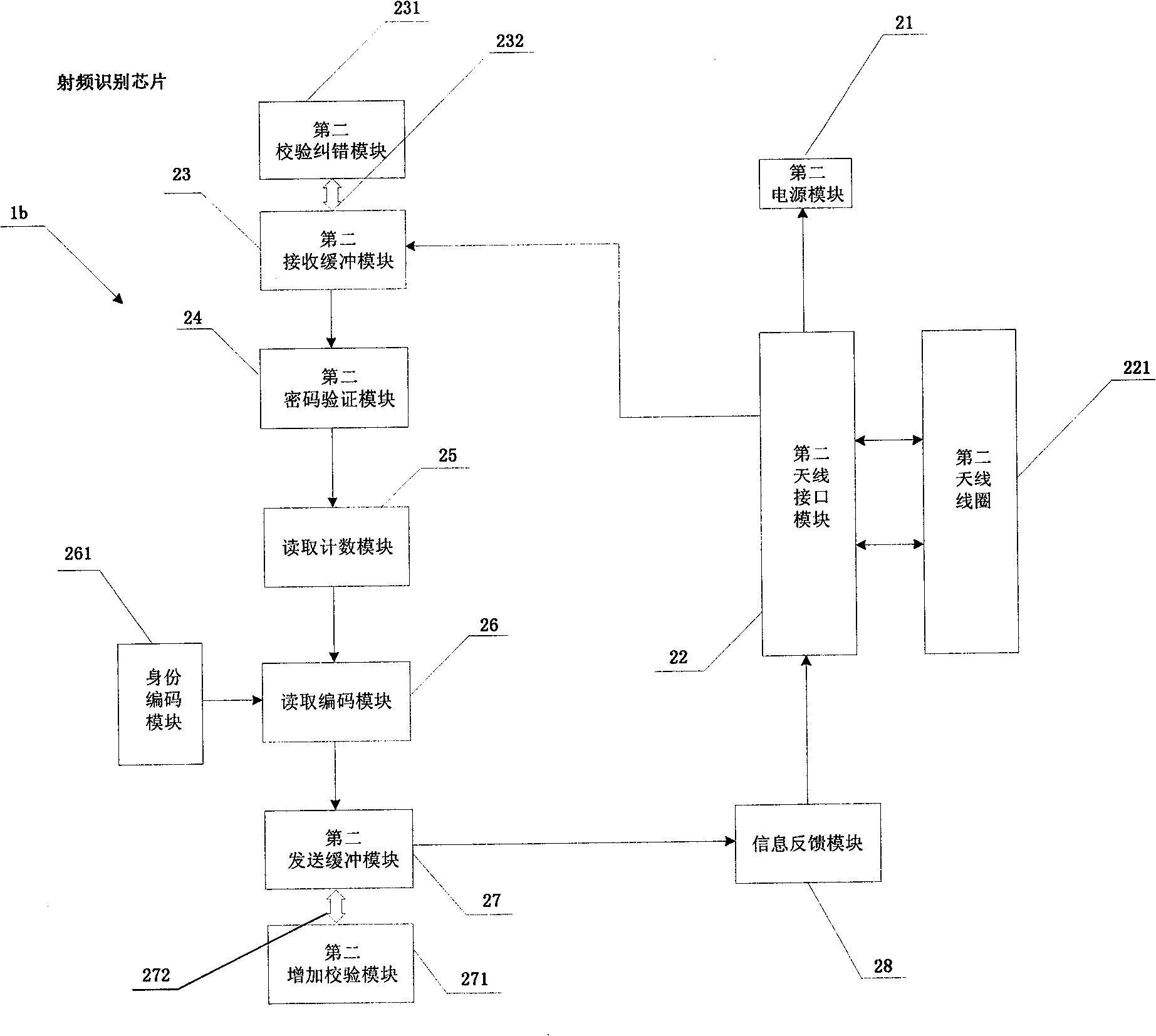
[0031] Embodiment one: if figure 1 and figure 2 As shown, an identification system includes a customized radio frequency identification chip 1b for storing the unique identity code of the identified object and an identification device 1a matched with the radio frequency identification chip 1b. The identification device 1a is provided with a first power supply module 11 that provides working power for the identification device 1a, a first antenna interface module 12, a first receiving buffer module 13, a first password verification module 14, a reading information module 15, a display An interface module 16 , a shutdown control module 17 and a first sending buffer module 18 . The first antenna interface module 12 is provided with a first antenna coil 121, the first power supply module 11 is connected with a start switch 111, one end of the start switch 111 is connected with a battery 112, the start switch 111 is turned on to provide working power for the identification device...
Embodiment 2
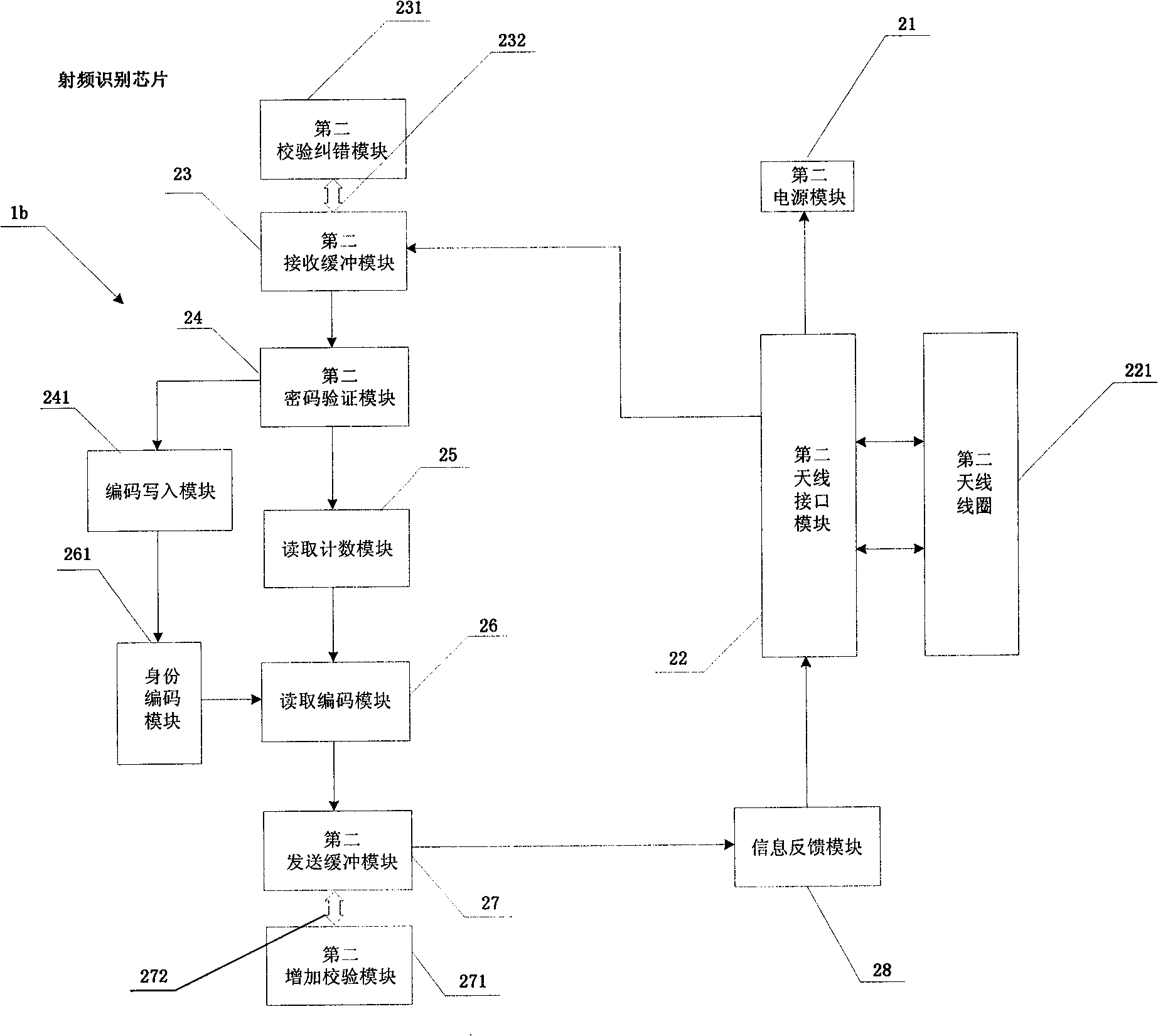
[0035] Embodiment two: the structure of this embodiment is basically the same as the structure of embodiment one, the only difference is that a code writing module can be set between the second password verification module 24 and the identity coding module 261 of the radio frequency identification chip 1b according to actual needs 241, such as image 3 As shown, the second password verification module 24 , the code writing module 241 , the identity coding module 261 and the reading code module 26 are sequentially connected, and the identity code can be written into the identity coding module 261 through the code writing module 241 .
[0036] based on figure 1 and figure 2 The identity recognition system of the first embodiment shown, Figure 4 An identification method is provided, which includes the following steps:
[0037] a. Press the start switch to provide working power for the identification device through the first power module, and the identification device is powe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com