Remote access communication method, apparatus and system
A technology for remote access and communication systems, which is applied in the fields of remote access communication methods, equipment and systems, and can solve the problems of complex management and maintenance and high cost.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
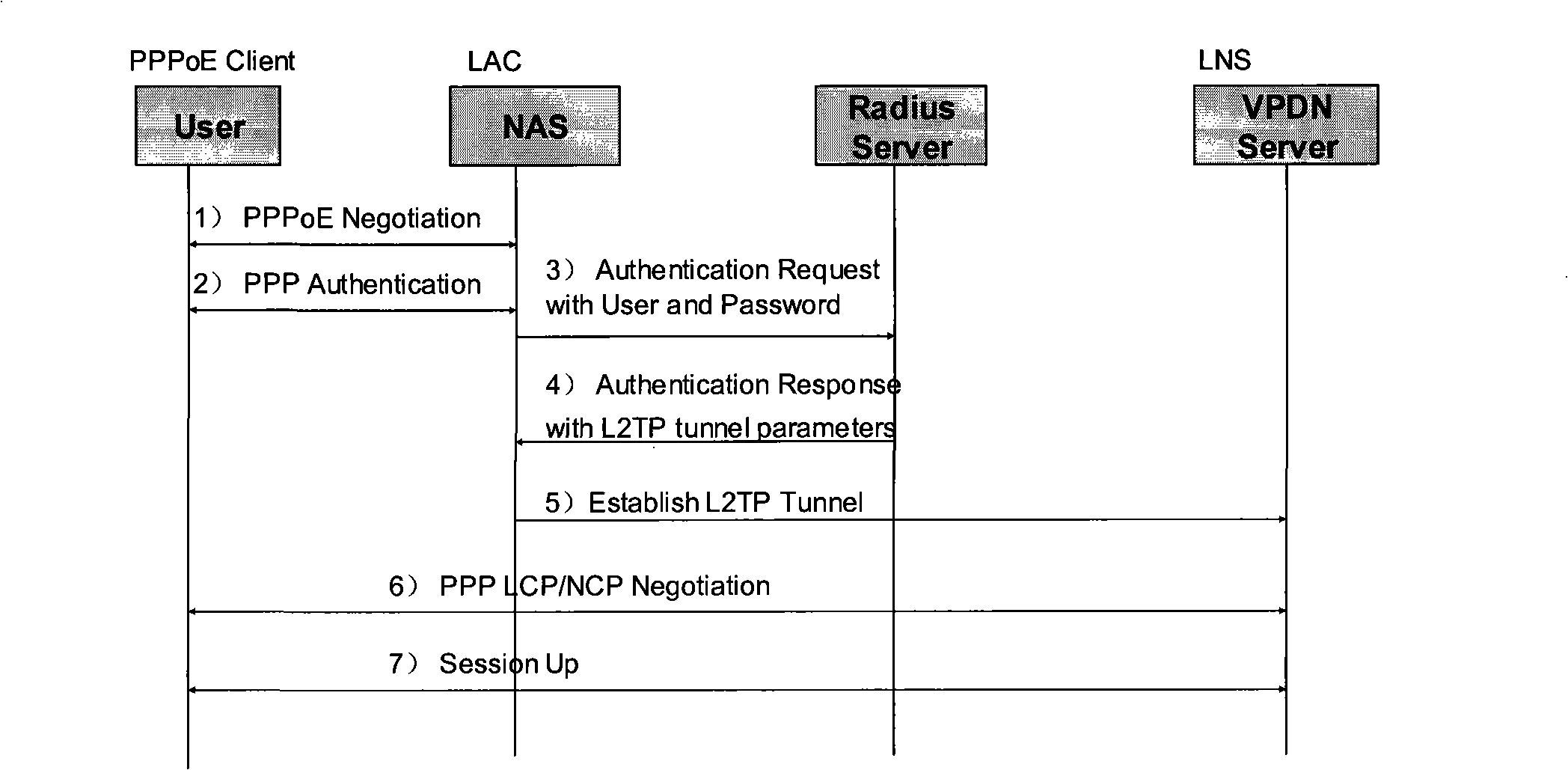
[0027] Call flow for accessing a virtual private network (VPN) through implicit authentication. Let's take the user initiates an IP session call as an example, see figure 2 Shown is the establishment process of implicitly authenticated IP Session dynamic access VPN, as follows:
[0028] S201: The user (User) turns on a network terminal device such as a computer, sends a discovery message DHCP Discover of the Dynamic Host Configuration Protocol through the DHCP client agent, and starts the address allocation process;
[0029] S202: The access point (Access Node, AN) captures the DHCPDiscover message sent by the user terminal equipment, and inserts the receiving port number or DSL port number of the captured message into the DHCP Discover in the format of Option 82 (82 option) message, and then forward the modified message;
[0030] The access point here can implement the Layer 2 DHCP relay (L2 DHCP Relay) function, such as the digital subscriber line access aggregation devic...
no. 2 example
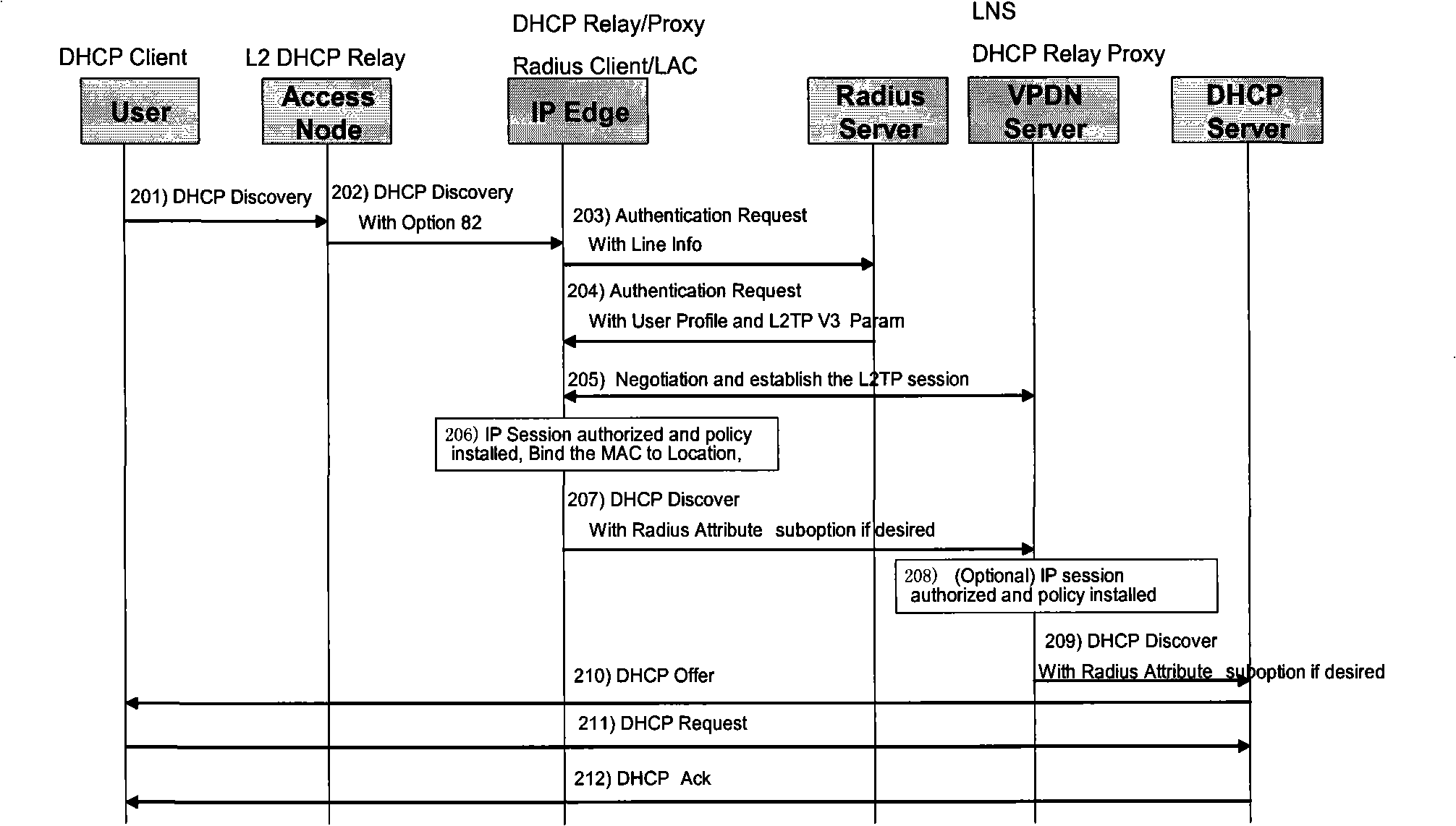
[0043] A call flow for accessing a virtual private network (VPN) through an authentication mode of the Protocol for carrying Authentication for Network Access (PANA). Let's take the user initiates an IP session call as an example, see image 3 Shown is the establishment process of PANA-authenticated IP Session dynamic access VPN, as follows:
[0044] S301: The user opens a network terminal such as a computer, sends a DHCP Discovery (Dynamic Host Configuration Protocol discovery message), and starts the address assignment process (IP config), so that the user obtains an IP address from DHCPServer1 and completes the address configuration process (such as the PANA authentication process flow same);
[0045] S302: After the address is allocated successfully, the user initiates a PANA authentication process to the IP edge device;
[0046] S303: After the Radius Server (authentication server) passes the PANA authentication, it carries the user policy in the authentication response...
no. 3 example
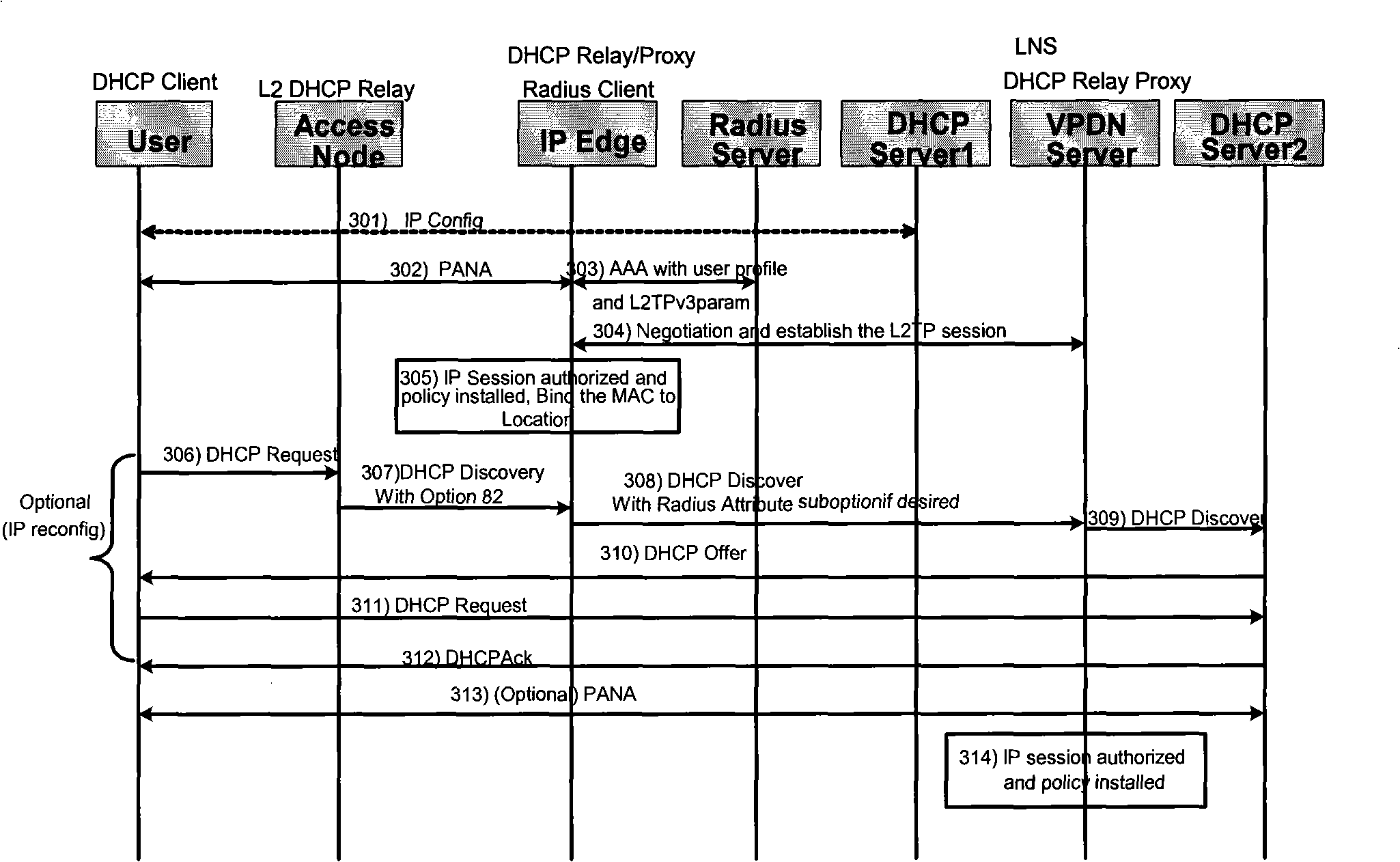
[0059] Call flow for accessing a virtual private network (VPN) through Dynamic Host Configuration Protocol (DHCP) authentication. Let's take the user initiates an IP session call as an example, see Figure 4 shown as DHCP Auth认证 The establishment process of IPSession dynamic access virtual private network is as follows:
[0060] S401: The user turns on a network terminal such as a computer, sends a DHCP Discovery (Dynamic Host Configuration Protocol discovery message), and starts the address allocation process;
[0061] S402: The access node (such as a DSLAM-data subscriber line access converging device) captures the user's DHCP Discover message and inserts the receiving port number or DSL port number of the message into the Option82 (82 option) format DHCP Discover message, and then forward the modified message;
[0062] In addition, thereafter, the access node may not modify subsequent messages (offer, request, and Ack) of the DHCP, but directly forward them.
[0063] S4...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com