Acceleration method and apparatus for GHASH computation in authenticated encryption Galois counter mode
A technology for authenticating encryption and accelerating devices, which is used in user identity/authority verification, electrical components, transmission systems, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
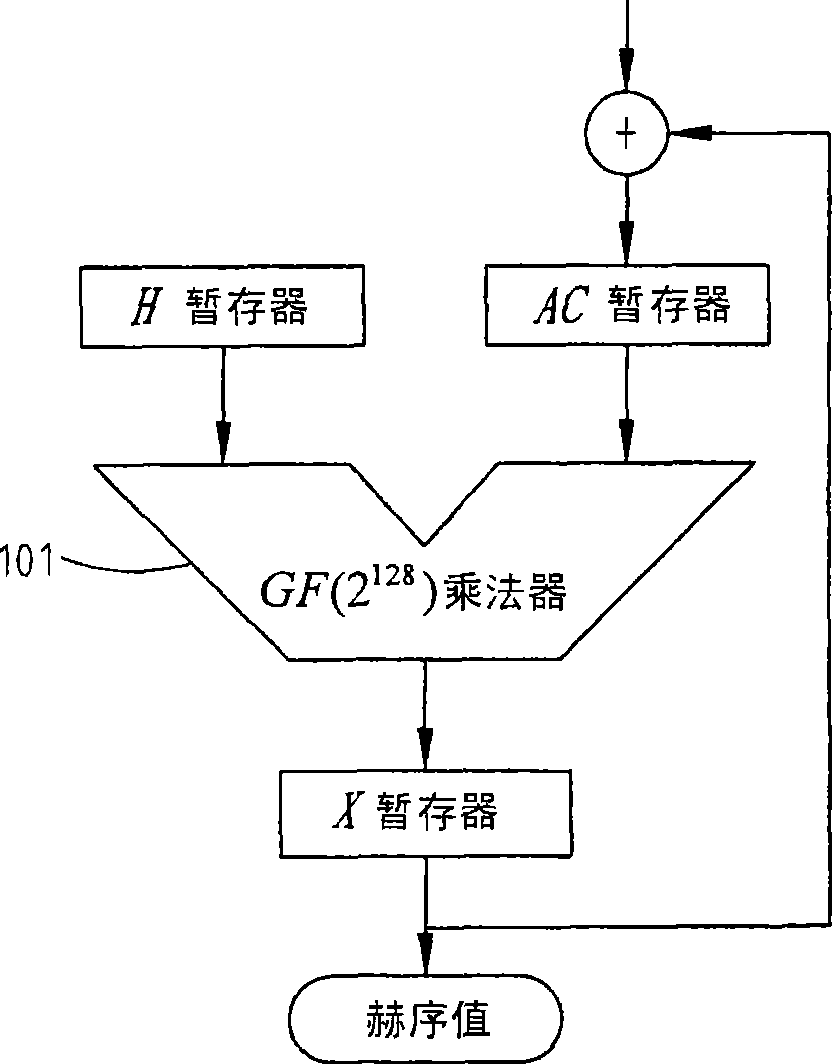
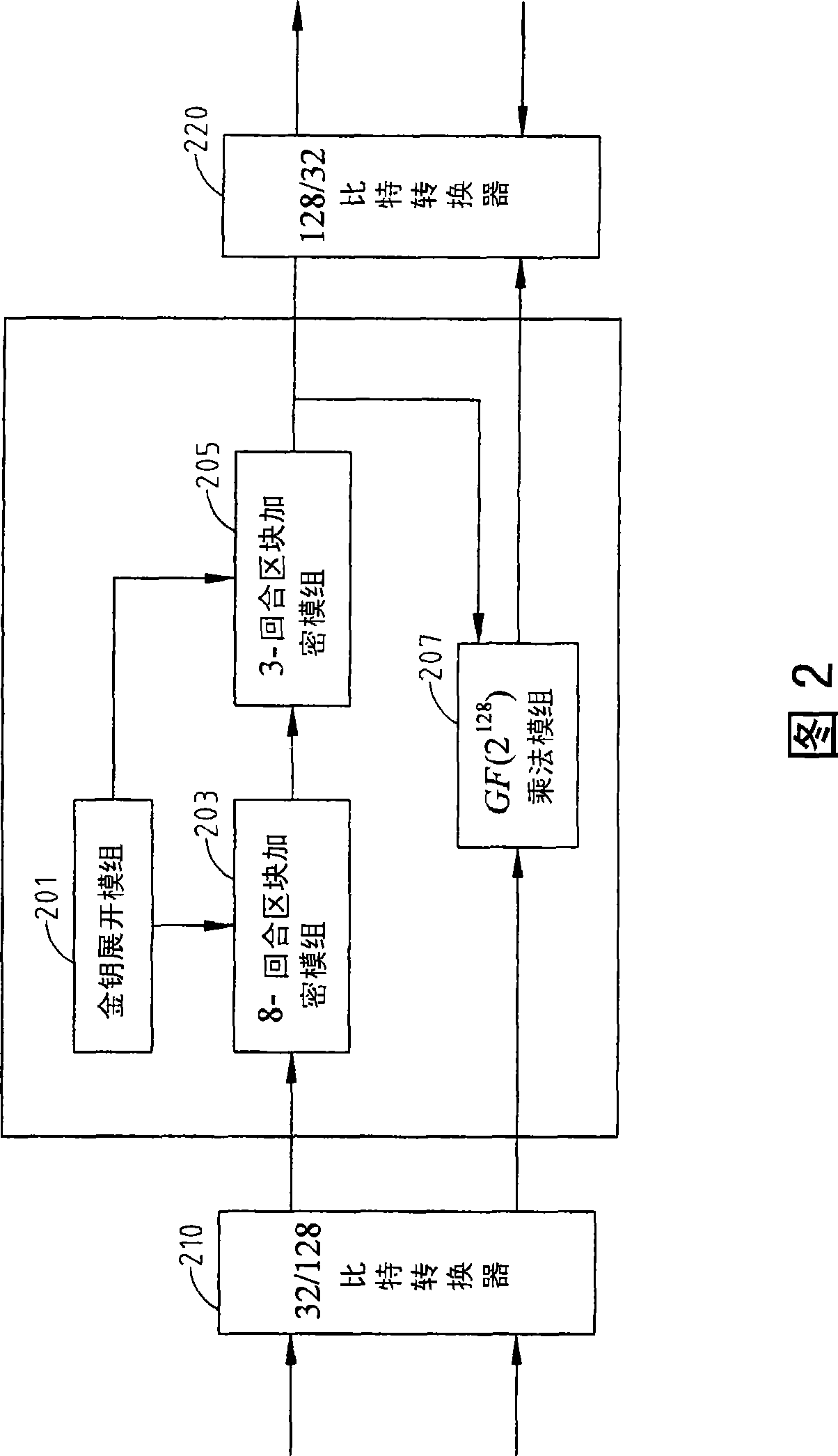
[0031] The GHASH function has three inputs, the three inputs are the additional authentication data A and ciphertext C defined in the GCM specification, and the HASH key value H. Without loss of generality, in the example described below, a block cipher is a 128-bit block, the length len(A) of the additional authentication data A is m, and the length len(C) of the ciphertext C is n. In other words, the GCM uses a 128-bit block cipher to provide both authentication and encryption, and the additional authentication material A and ciphertext C are divided into m and n 128-bit blocks, respectively.
[0032] If the operation of GHASH in GCM is performed by using the equation (2) of the known technology, it takes m+n+1 working clocks to obtain the operation result of the GHASH function.
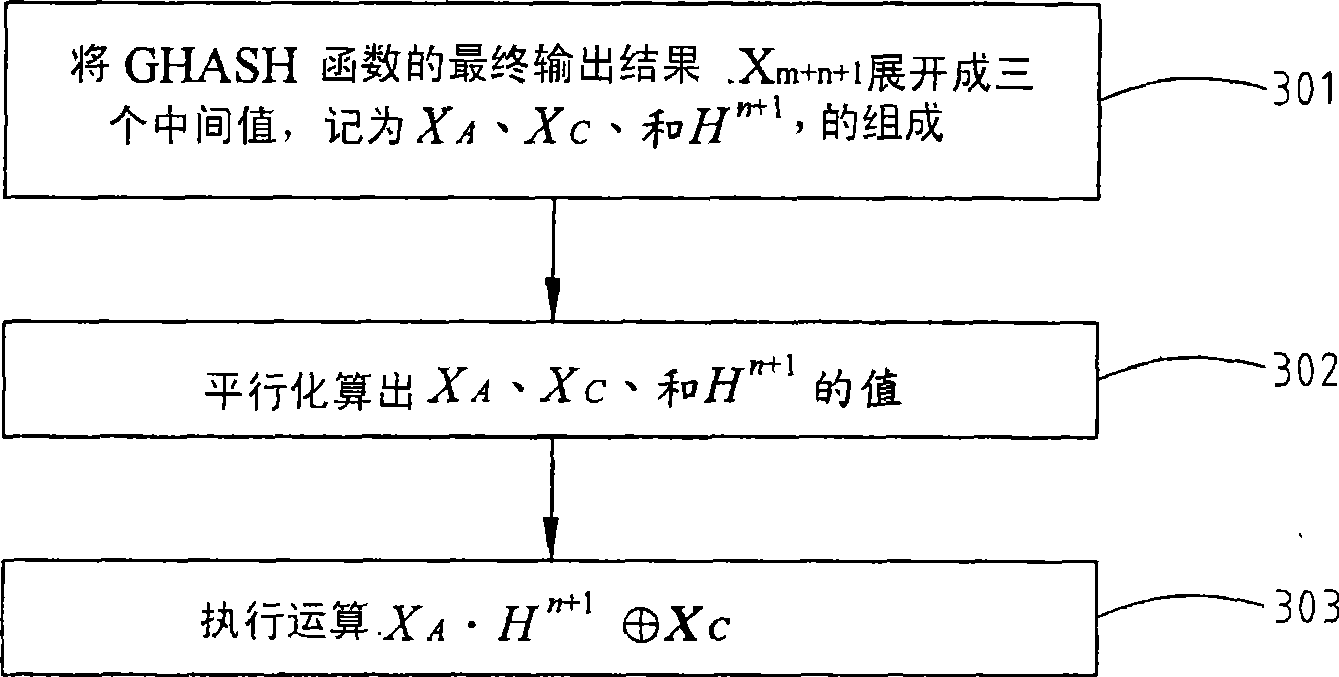
[0033] According to the present invention, the acceleration method of GHASH operation in the GCM of authentication encryption, its flow example is image 3 shown. First, the final output of the G...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com