Picture identifying code creation method and device
A technology of picture verification code and generating device, which is applied in the field of picture verification code generation, can solve problems such as being unable to effectively resist verification code cracking, and achieve the effect of preventing cracking
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
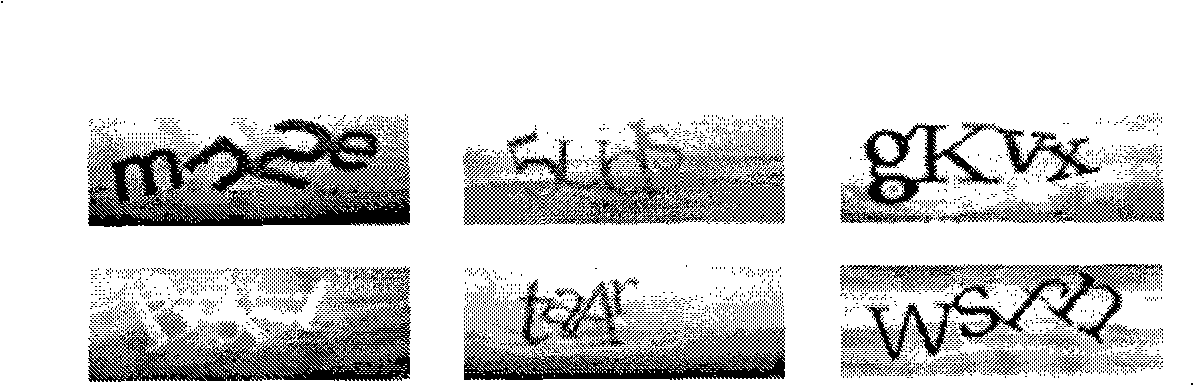
[0046] Figure 3a It is a plan view at the initial moment of a layer structure of the present invention, the layer structure includes two layers, the two layers are parallel, and the vertical distance between the layers is not limited. Among them, the layer at the bottom includes the verification code graphic AJMKI ( Figure 3a Not shown in ), the verification code graphic AJMKI is included in the rectangular picture 321 ( Figure 3a not shown in), such as Figure 3b As shown; this picture 321 can be the form of static picture verification code in the prior art, and picture 321 can also include other graphics such as noises that do not affect the observation verification code figure, is not limited here; An opaque rectangular picture 311 .
[0047] Assuming that the length of picture 311 and picture 321 is a and the width is b, the content contained in picture 311 is not limited, but it is preferably distinguishable from the verification code graphics. For example, in this ...
Embodiment 2
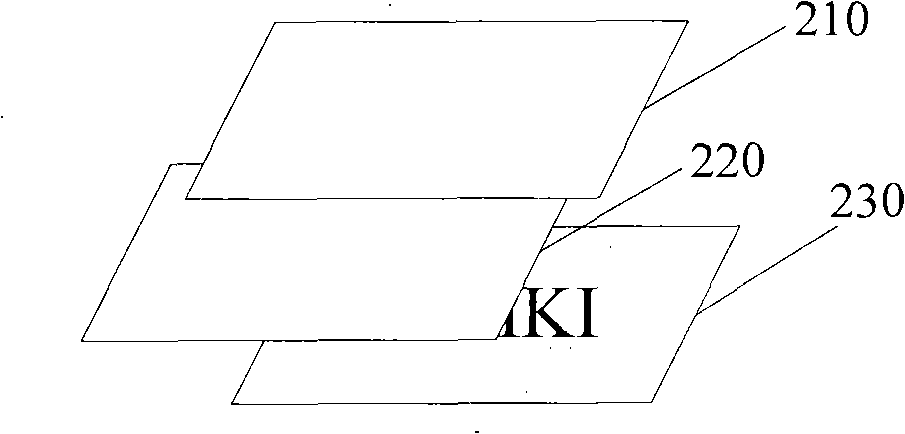
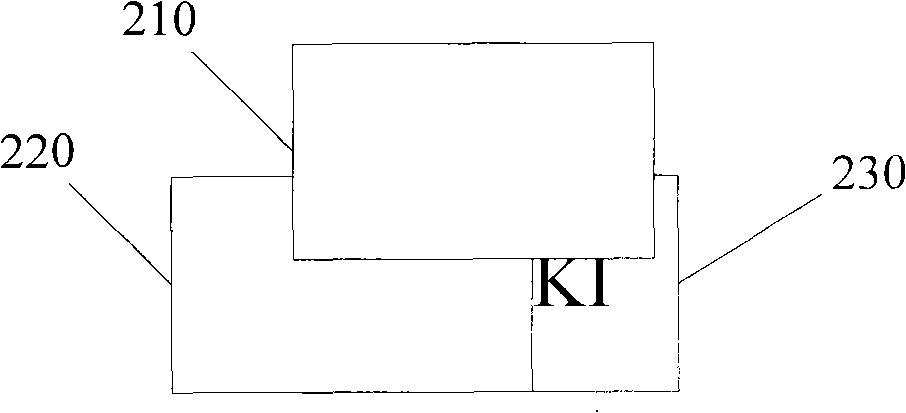
[0053] Figure 4 It is another layer structure side view of the present invention, such as Figure 4 As shown, the layer structure includes a layer 410 and a layer 420, wherein the layer 420 is located under the layer 410, and the layer 410 and the layer 420 are not parallel, and there is a certain angle, and the specific angle is not limited.
[0054] Such as Figure 4 and Figure 4a As shown, the layer 420 includes a verification code graphic AJMKI, which is included on the rectangular picture 421, and exists in the plane where the layer 420 is located in the form of a static picture verification code in the prior art, and the picture 421 Other graphics such as noises that do not affect the observation of the verification code graphics may also be included in , which is not limited here. Assuming that the length of the rectangular picture 421 is a and the width is b, the layer 410 includes a rectangular picture 411 with a length of 3a / 5 and a width of b / 2 in the top view....
Embodiment 3
[0057] Figure 5a Shown is a side view of the initial moment of another layer structure, such as Figure 5a As shown, the verification code includes three layers, wherein the bottom layer includes a verification code graphic 531, and the verification code in the verification code graphic 531 is specifically AJMKI (not shown in the figure); while other layers Include picture 511 and picture 521 respectively. In this embodiment, picture 511 is white and opaque, and contains a through hole (not shown in the figure) above, through which can expose the Content; picture 521 is opaque and contains horizontal stripes. Of course, the picture 511 and the picture 521 may also contain other content that will not confuse the verification code graphic 531 , which will not be repeated here.
[0058] The top view of the layer structure at the initial moment is as follows Figure 5b As shown, at this time, since the verification code pattern 531 and the picture 521 are completely covered by...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com