Method, system, equipment and server for packet authentication
A technology for authenticating messages and registering servers, applied in transmission systems, public keys for secure communications, user identity/authority verification, etc. It can solve the problem of not being able to prevent P2P overlay network attacks, not considering the problem of terminal identification invalidation, invalid passwords, etc. It can prevent the attack of sending malicious packets to the network, reduce the process of message interaction, and reduce the management effect.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
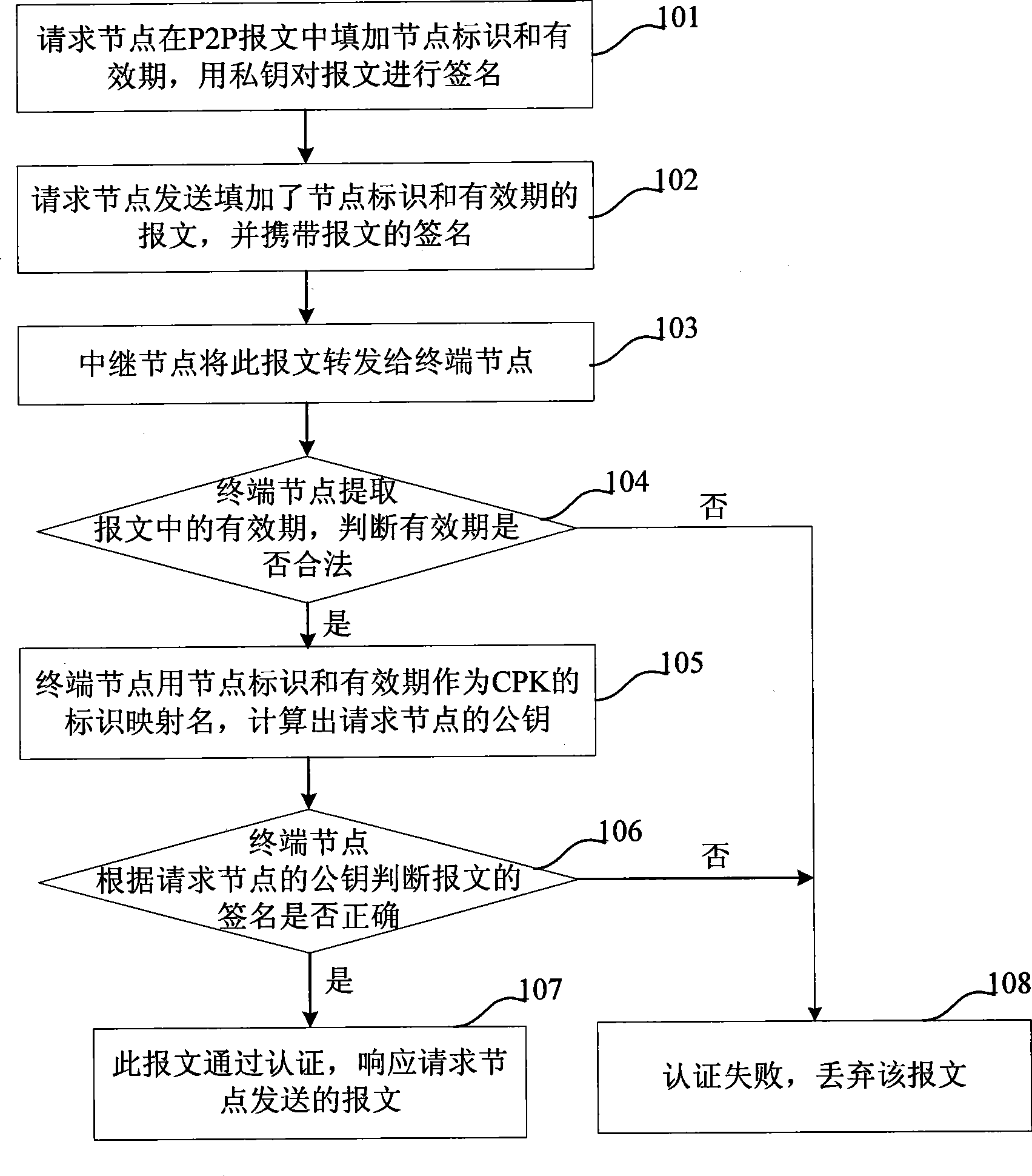
[0054] This embodiment provides a method for authenticating a message, including:
[0055] Request the node to add the pre-acquired node ID and validity period to the message, sign the added message with the private key, and send the added message, which carries the message signature;
[0056] After receiving the message, the terminal node judges that the validity period in the message is legal, calculates the public key of the requesting node according to the node ID and validity period, and uses the public key to verify whether the signature is correct. If it is correct, the message passes the authentication.
[0057] The validity period refers to the effective use time of the key (public key and private key) corresponding to each node ID. For example, the usage time of the public key and private key with node ID 123 is specified as 1 year, and it needs to be regenerated after one year New public key and private key, which ensures that the public key and private key of each ...
Embodiment 2
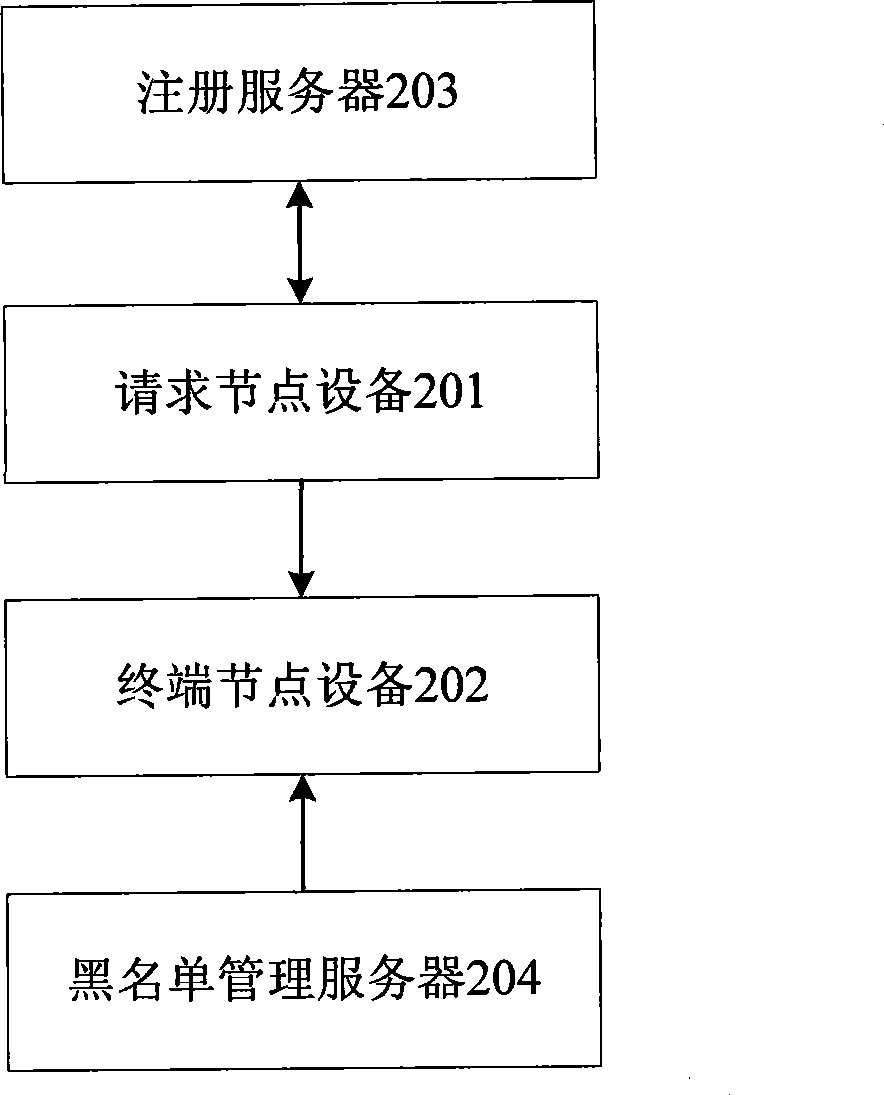
[0082] see figure 2 , this embodiment provides a system for authenticating messages, including:
[0083] The requesting node device 201 is used to add the pre-acquired node identification and validity period to the message, sign the added message with a private key, and send the signed message;
[0084] The terminal node device 202 is configured to receive the message sent by the requesting node device 201, determine whether the validity period in the message is legal, calculate the public key of the requesting node device 201 according to the node identifier and the validity period, and use the public key to verify whether the signature is correct, If correct, the message is authenticated.
[0085] Wherein, the requesting node device 201 also includes:
[0086] The registration module is used to send the registration request and receive the registration response information;
[0087] Accordingly, the system also includes:
[0088] The registration server 203 is used to r...
Embodiment 3
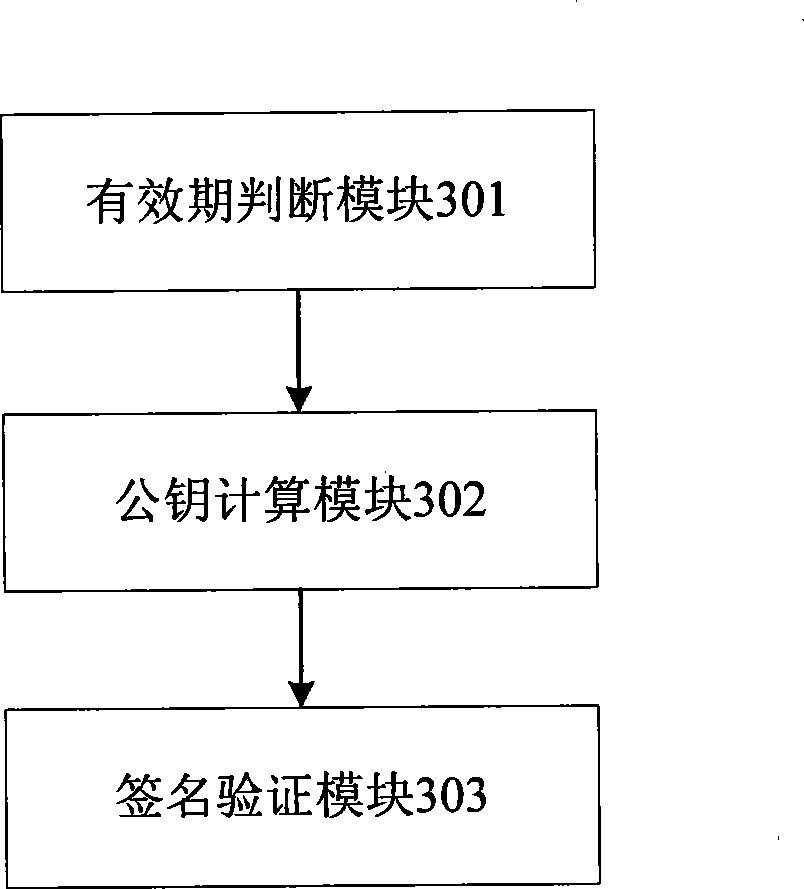
[0094] see image 3 , the present embodiment provides a device, comprising:
[0095] Valid period judging module 301, after receiving message, judges whether the valid period in the message is legal;
[0096]The public key calculation module 302 is used to calculate the public key of the requesting node according to the node identification and the validity period in the message after the valid period judging module 301 determines that the valid period is legal;
[0097] The signature verification module 303 is configured to use the public key calculated by the public key calculation module 302 to verify whether the signature in the message is correct, and if it is correct, the message passes the authentication.
[0098] The equipment includes:
[0099] The node identification judging unit is used to judge whether the node identification in the message is in the blacklist, if yes, the message authentication fails, otherwise, notify the public key calculation module 302 to cal...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com