Security information management system and method based on general normalized labeling language
A security information and management system technology, applied in the direction of security communication devices, transmission systems, digital transmission systems, etc., can solve the problems of self-defined calculation of unextractable data, unstandardized data types, etc., and achieve the effect of facilitating on-site maintenance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0036] Embodiment 1 This embodiment describes the grammar rules of the VNML language in detail.
[0037] The VNML language is based on the XML language, using the elements of the XML language to represent categories, and the attributes of XML to represent characteristics. At the same time, some extended features are introduced, mainly including types, constants, and functions. Regarding the VNML language grammar rules, the detailed description is as follows
[0038] 1. Naming convention
[0039] Combinations of capitalized English letters, numbers, and underscores, such as Name and SubNet, are legal names.
[0040] 2. Type
[0041] The concept of type is introduced in VNML language, a type is used to represent the data of the same format and meaning, and these types correspond to the types in C and C++ languages.
[0042] 3. Constants
[0043] Constants in the VNML language use some specific numbers to represent specific meanings, for example, the number 1024 represents an ...
Embodiment 2
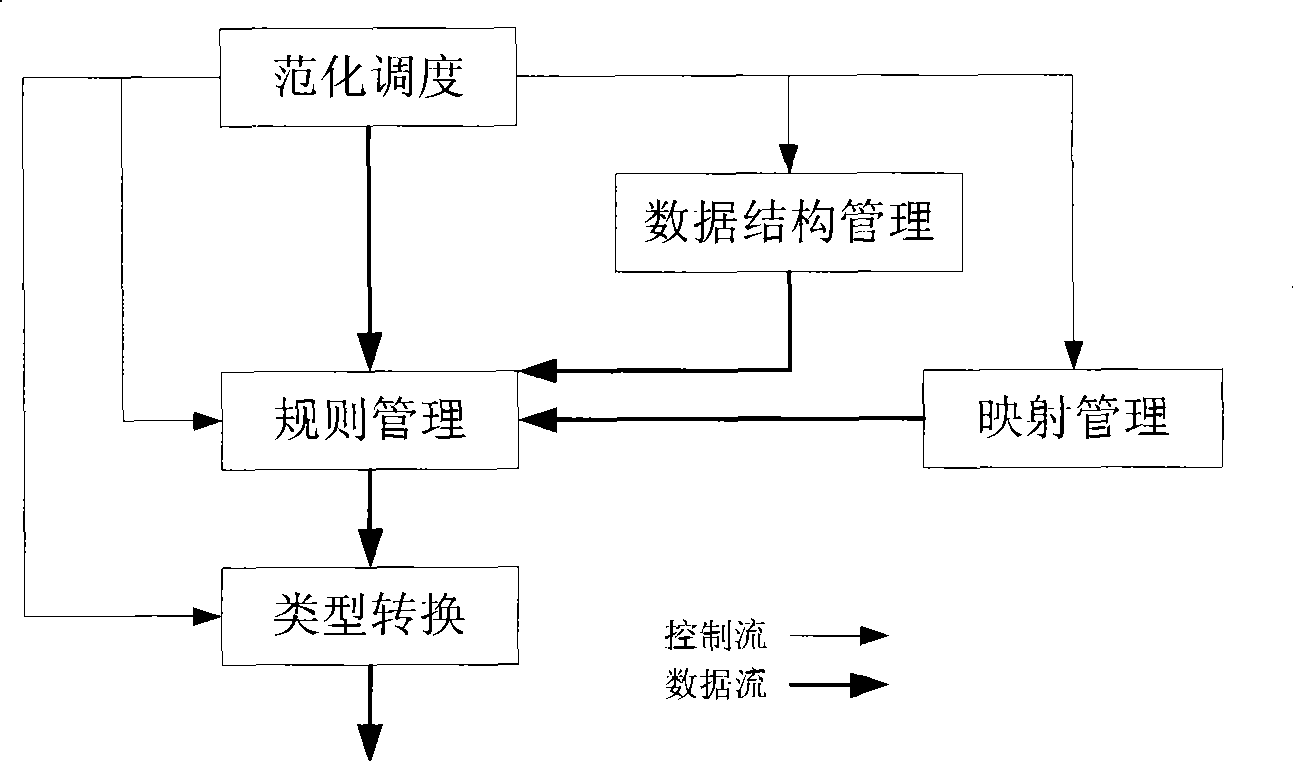
[0120] Example 2 as figure 1 As shown, the system shown in this figure is a specific embodiment of the composition structure of a normalization engine. The normalization engine shown in the figure can realize the interpretation and compilation of VNML language; complete log sample data normalization, data format and type conversion; and output data according to the specified data structure. The normalization engine is mainly composed of five modules: data structure module, normalization scheduling module, rule management module, mapping management module and type conversion module. The specific functions of each module are as follows:
[0121] Normalized scheduling module: it is the main module of the normalized engine, such as figure 1 According to the processing flow shown in the system design, the normalized scheduling module is responsible for scheduling and managing four major functional modules, including the data structure management module, rule management module, ma...
Embodiment 3
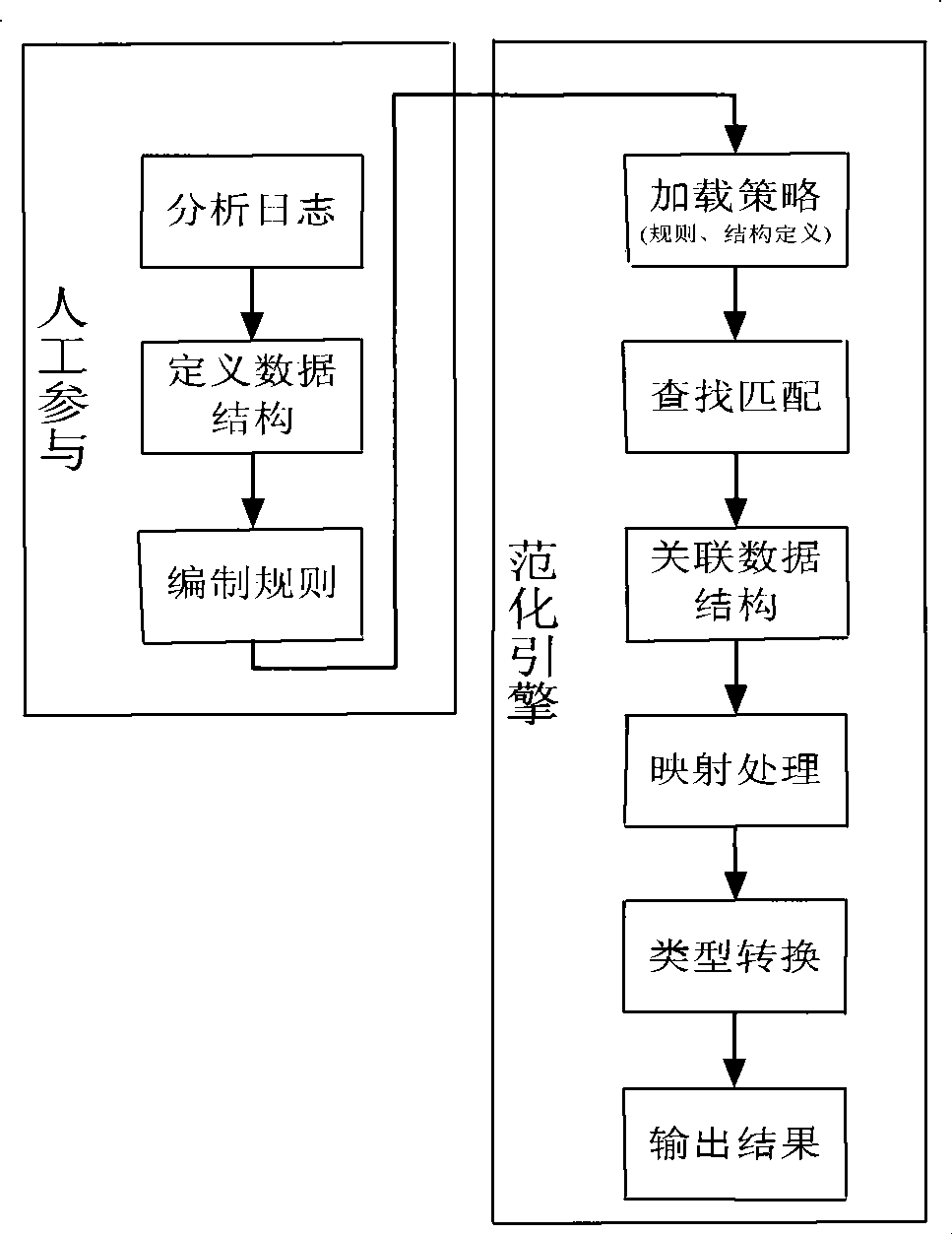
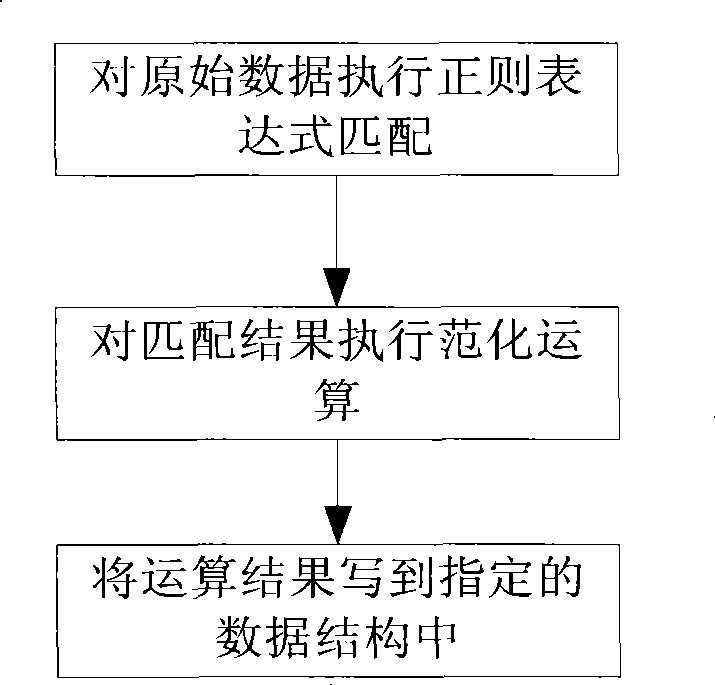
[0126] Example 3 as figure 2 As shown, the specific steps of the present invention are as follows: first, the manual analysis and definition stage: analyze the log sample data, and define the data structure of normalization, and apply the self-defined VNML language definition to reasonably normalize the data structure of the given log sample; then It loads the defined data structure, normalization rules and mapping rules, and normalizes the log sample data through the normalization engine.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com