Disposal authentication method for network access and service application oriented to user
A technology for user authentication and network access. It is applied to electrical components, transmission systems, and data exchange through path configuration. It can solve problems such as service management platform performance impact and user feeling slow, and achieve easy implementation, small changes, and high efficiency. high effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0022] The present invention will be described more fully hereinafter with reference to the accompanying drawings, in which exemplary embodiments of the invention are illustrated.
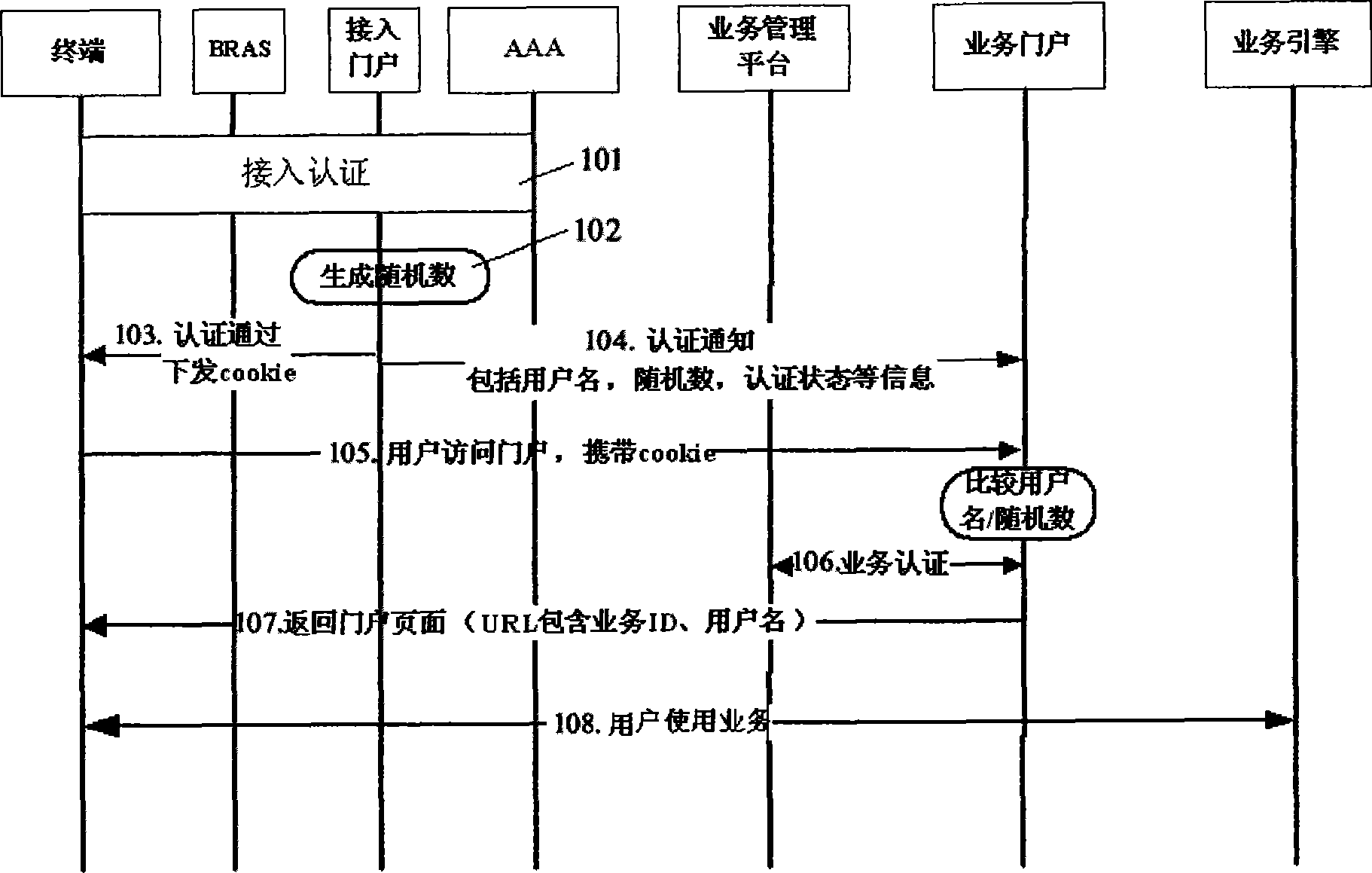
[0023] The one-time authentication method for user-oriented network access and service use provided by the present invention mainly includes: after the user terminal passes the first authentication, the access portal sends the user authentication information to the user terminal and the service portal for storage respectively ; When the user terminal accesses the service portal, the service portal obtains the user authentication information saved by the user terminal, compares it with the user authentication information stored locally, and performs legality authentication and authentication at the business level.
[0024] see figure 1 As shown, the present invention proposes a business process of a preferred embodiment of a method for one-time authentication of user-oriented WLAN access and service...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com