Semi-fragile watermarking method for color image tamper localization and recovery
A digital watermarking and color image technology, applied in image data processing, image data processing, image coding, etc., can solve the problems that algorithms rarely resist lossy compression, limit the application scope of image authentication, and have no special processing for color images. To achieve the effect of increasing the amount of embedded information, enhancing concealment, and restoring good quality
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
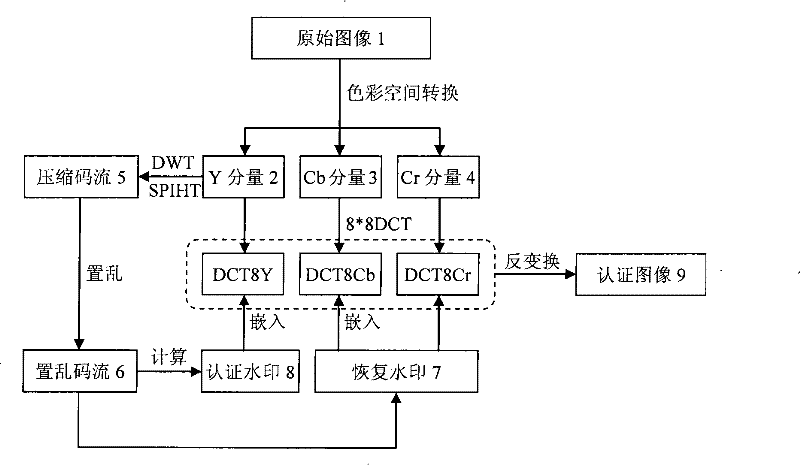
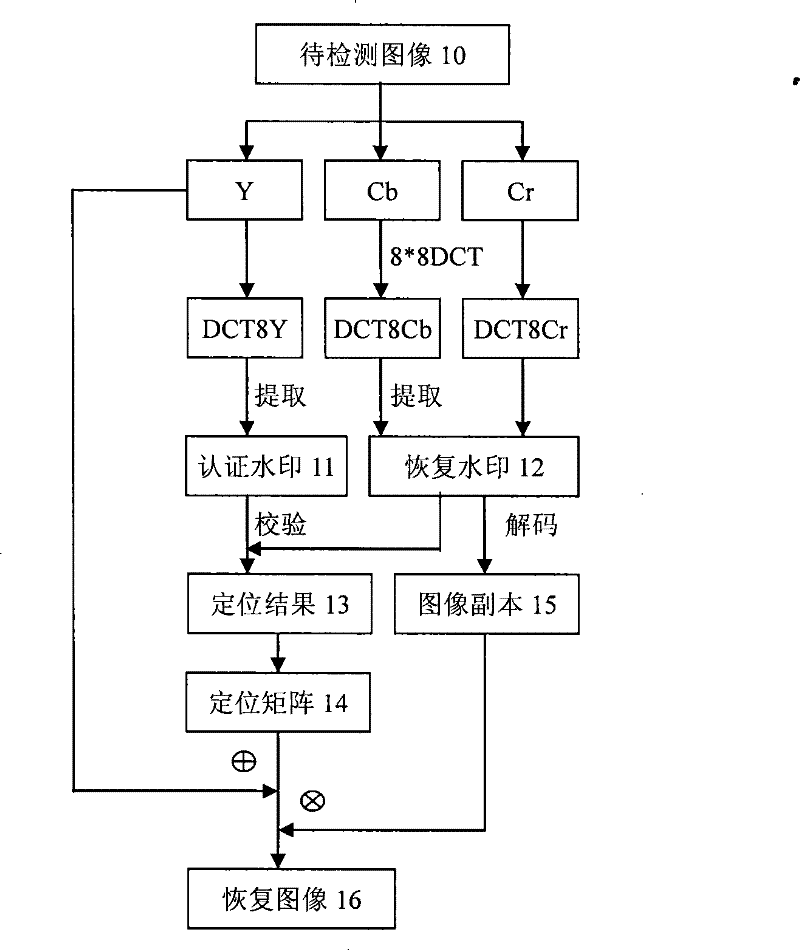
[0034] The watermark embedding and extraction process of the semi-fragile digital watermarking method for color image tampering location and restoration can be divided into the following steps: a) Convert the image to the YCbCr color space; b) Divide the Y component into blocks, and discrete each block Wavelet transform; c) Use the SPIHT algorithm to compress each image block to generate a compressed code stream; d) Use diagonal exchange and chaotic sequence to rearrange the compressed code stream; e) Calculate the recovery watermark and authentication watermark; f) Make the original image 8×8 DCT transformation, the recovery watermark is embedded into the DCT coefficient matrix of the Cb and Cr components, and the authentication watermark is embedded into the DCT coefficient matrix of the Y component; g) The DCT coefficient matrix after the watermark is embedded is subjected to an 8×8 DCT inverse transformation, And convert back to RGB color space; h) Use affine transformation...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com