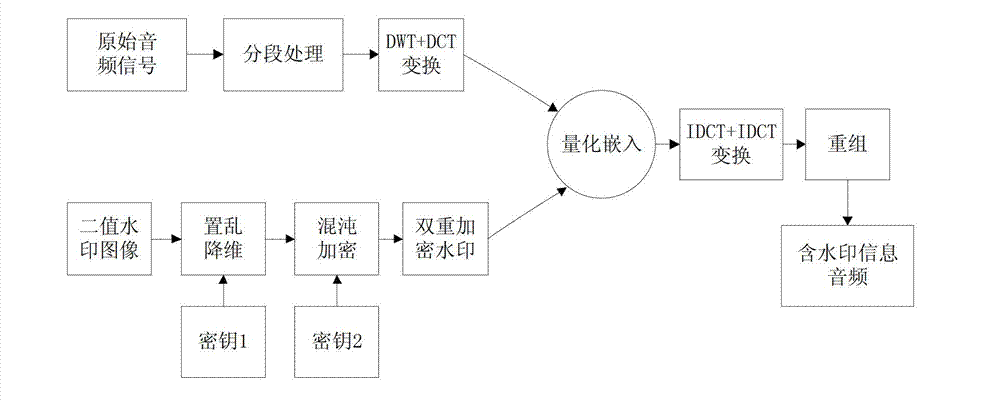
Dual encryption based discrete wavelet transform-discrete cosine transform (DWT-DCT) domain audio public watermarking algorithm
A double encryption, domain audio technology, applied in the field of image information security, can solve the problem of not effectively resisting watermark shearing attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0086] In order to verify the effectiveness of the watermarking algorithm of the present invention, we conduct simulation experiments under the environment of MATLAB7. The original audio signal of the experiment selects a monophonic digital audio signal with a sampling frequency of 44.1KHZ, a resolution of 16 bits, and a length of 9.75 seconds. The binary image of 32×32 is used as the original watermark image; among them, the number of selected coefficient segments n is 5, DWT (discrete wavelet transform) uses Daubechie-4 as wavelet base, DWT series L is 2, Arnold scrambling times is 9, Logistic chaotic sequence λ is 2, X 0 is 0.6.
[0087] The simulation results are as follows:
[0088] 1. The watermark algorithm of the present invention improves the security of the watermark. Such as figure 2 The result shown is the combination of sampling and chaos modulation of the binary watermark image. Visually, no useful information can be seen, and the image information becomes ch...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com