Method and system for implementing authentication
An authentication system and portal system technology, applied in the field of authentication, can solve problems such as inability to integrate filters, increase the difficulty of development and testing, and achieve the effect of solving security risks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0053] The technical solutions of the present invention will be further described below in conjunction with the drawings and specific implementations.
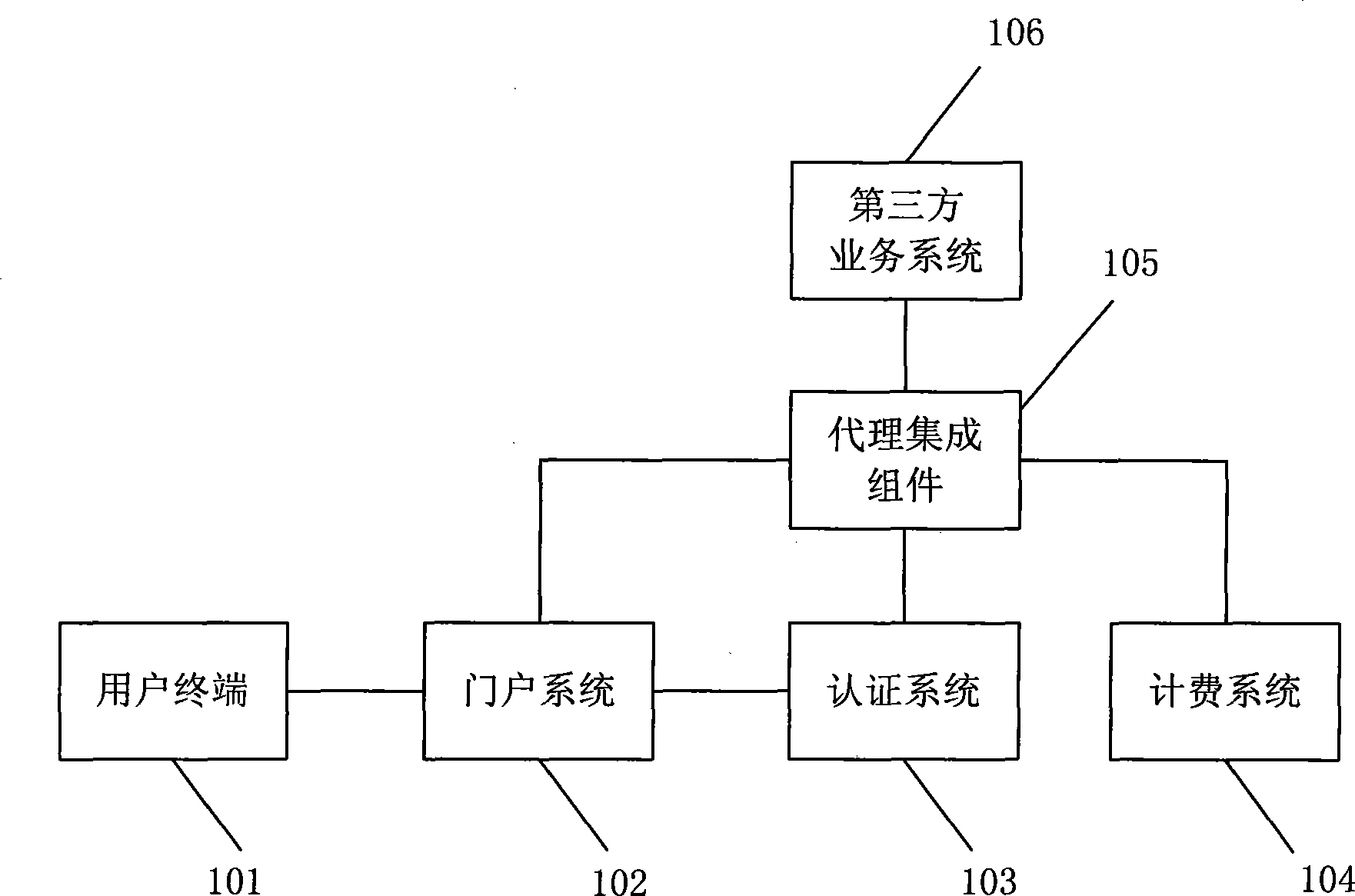
[0054] The main idea of the technical scheme of the present invention is to use Proxy Integrated Component (Proxy Integrated Component, PIC) to realize the security integration between systems in the field, which can act as a proxy for a business system to be integrated into the existing security system to complete security authentication, business authentication and Data exchange.
[0055] figure 1 It is a schematic diagram of the structure of an authentication system in the digital television field in the specific embodiment of the present invention. Such as figure 1 As shown, the authentication system includes a user terminal 101, a portal system 102, an authentication system 103, a billing system 104, an agent integration component 105, and a third-party service system 106.
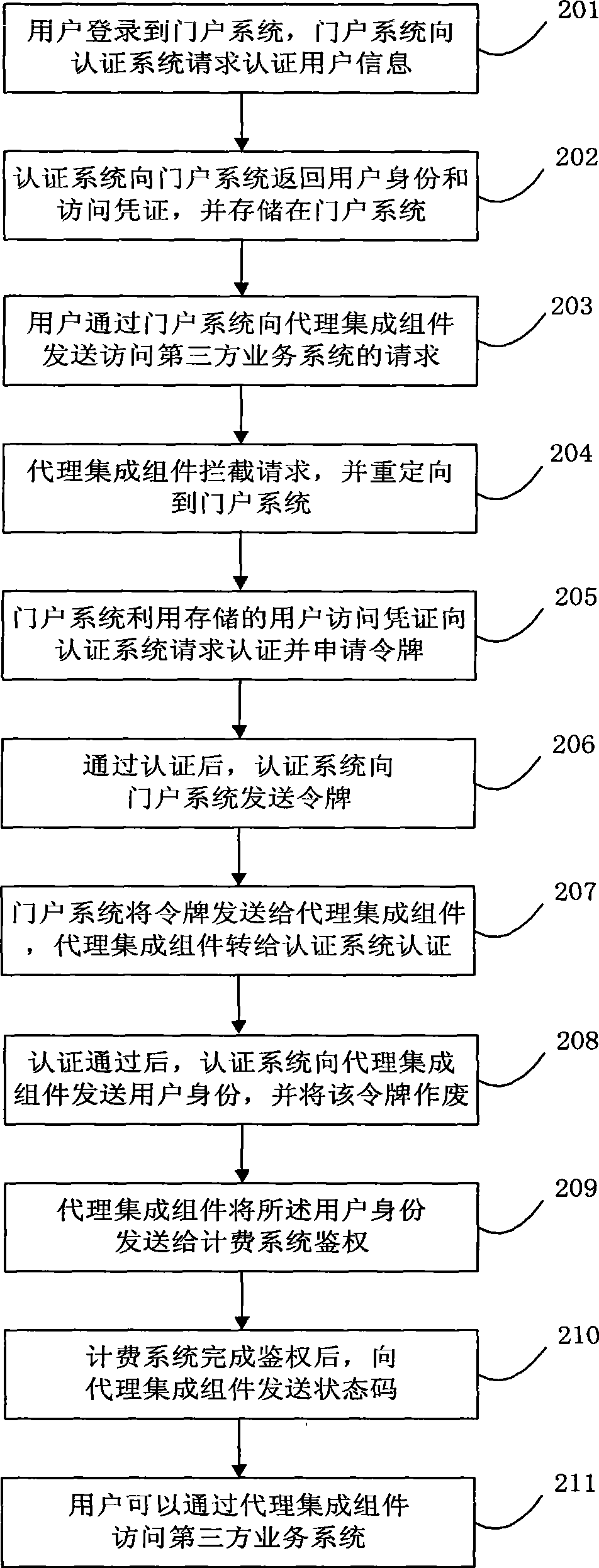
[0056] The user sends user information to the p...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com