Cryptographic-equipment-oriented energy leakage acquisition method and system
A cryptographic device and energy leakage technology, applied in the field of information security, can solve problems such as physical security threats of embedded cryptographic devices, achieve effective resistance to energy analysis attacks, flexible sampling conditions, good scalability and configurability Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0056] At the same time, the command line mode can be quickly integrated into other complex energy analysis systems as a tool software module. At the same time, for the fixed parameters that are often executed and set, it can be conveniently configured through XML files.
[0057] The present invention will be described in further detail below in conjunction with the accompanying drawings.
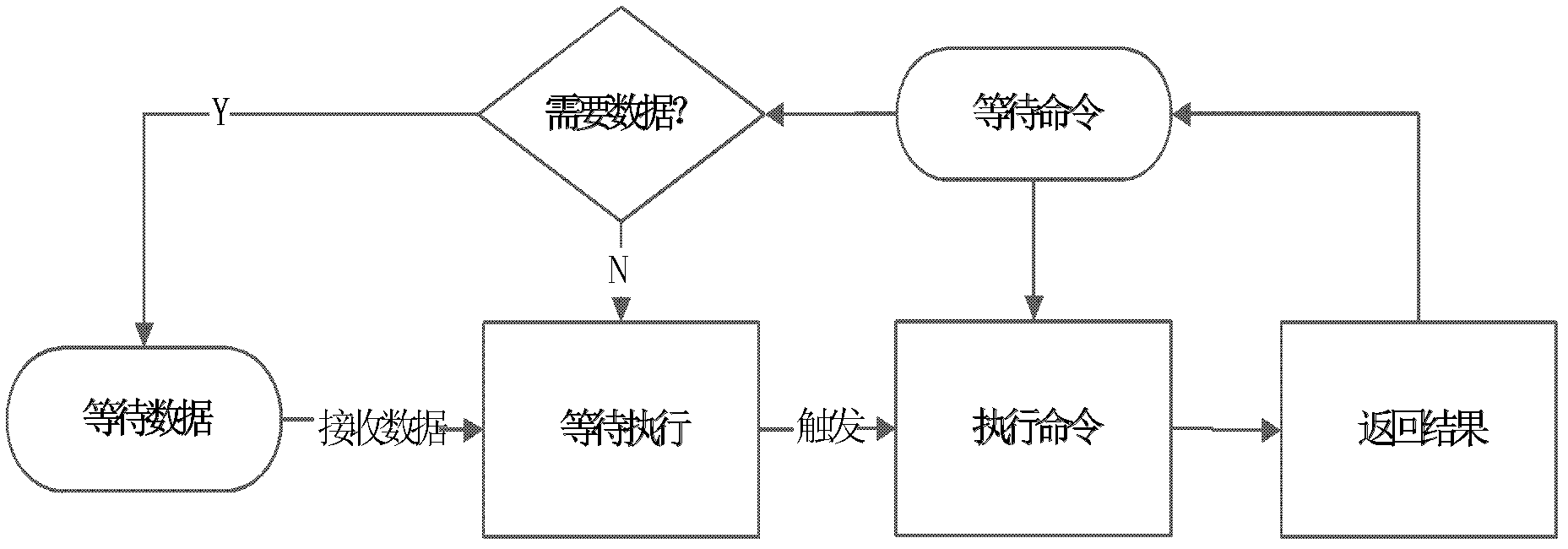
[0058] It first introduces the specific architecture of the system and the connection methods of each part of the system, then describes the detailed functions of each part, and finally introduces the workflow of the entire system.
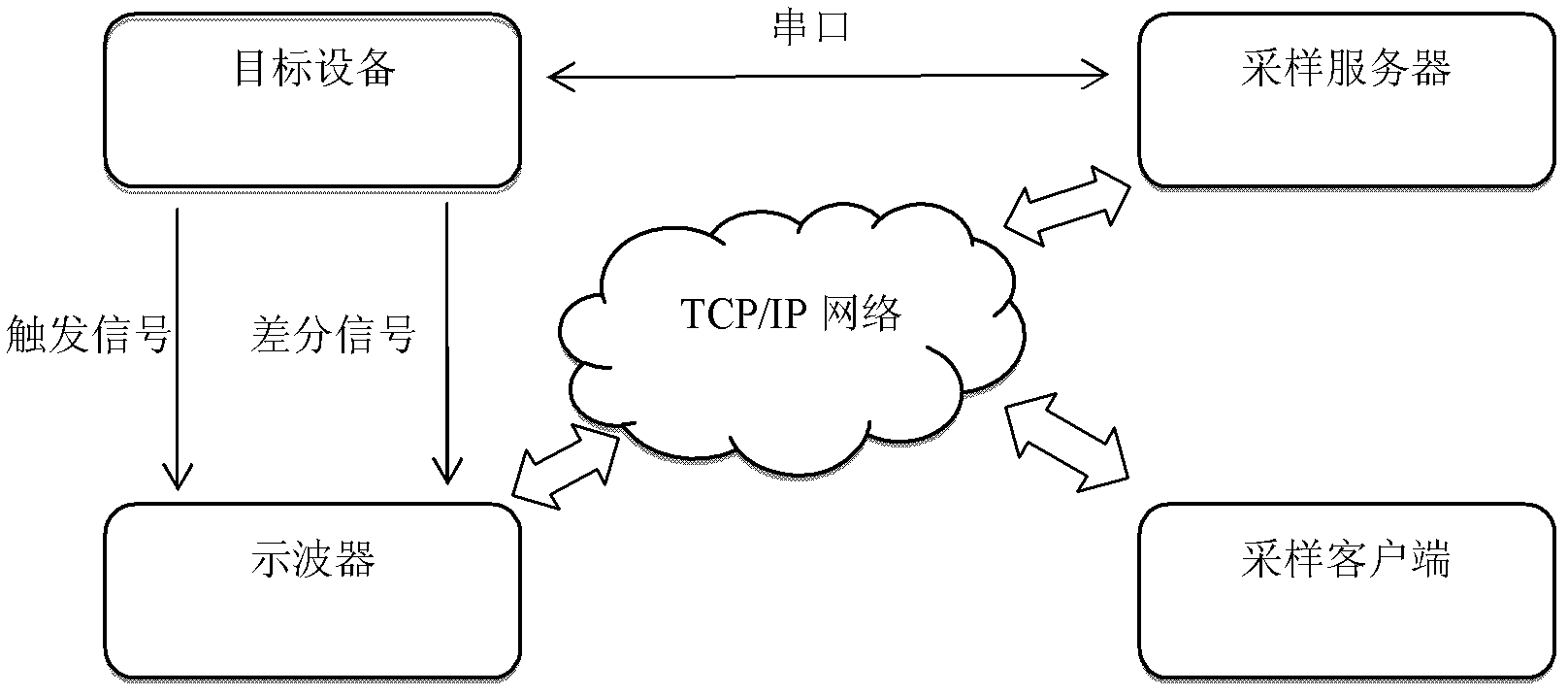
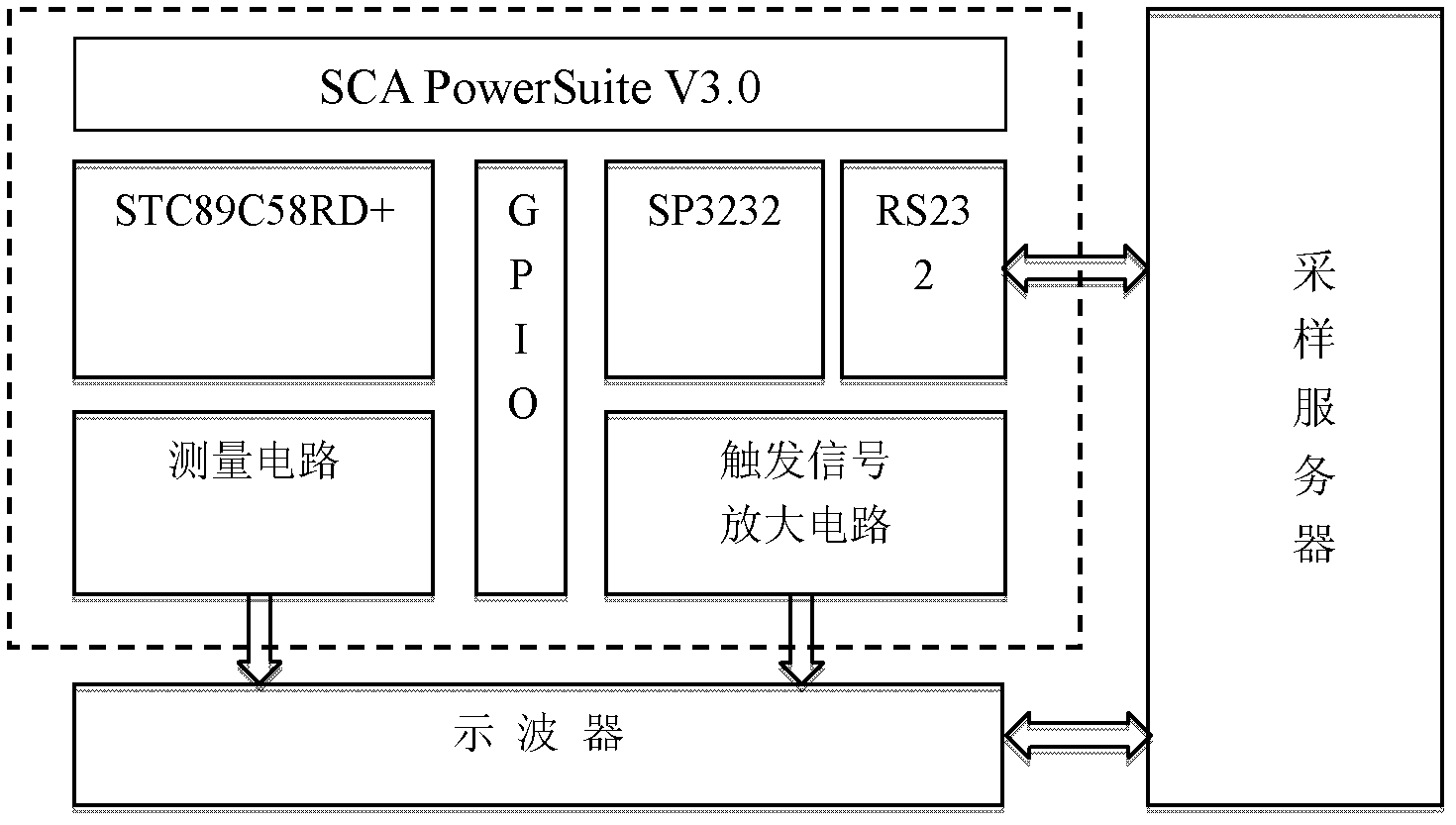
[0059] The overall system consists of four parts: target device, sampling server, sampling client and oscilloscope. The overall structure and connection methods are as follows: figure 1 shown. The target device is connected to the sampling server through a serial port. The oscilloscope collects the energy leakage information of the target device through a di...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com