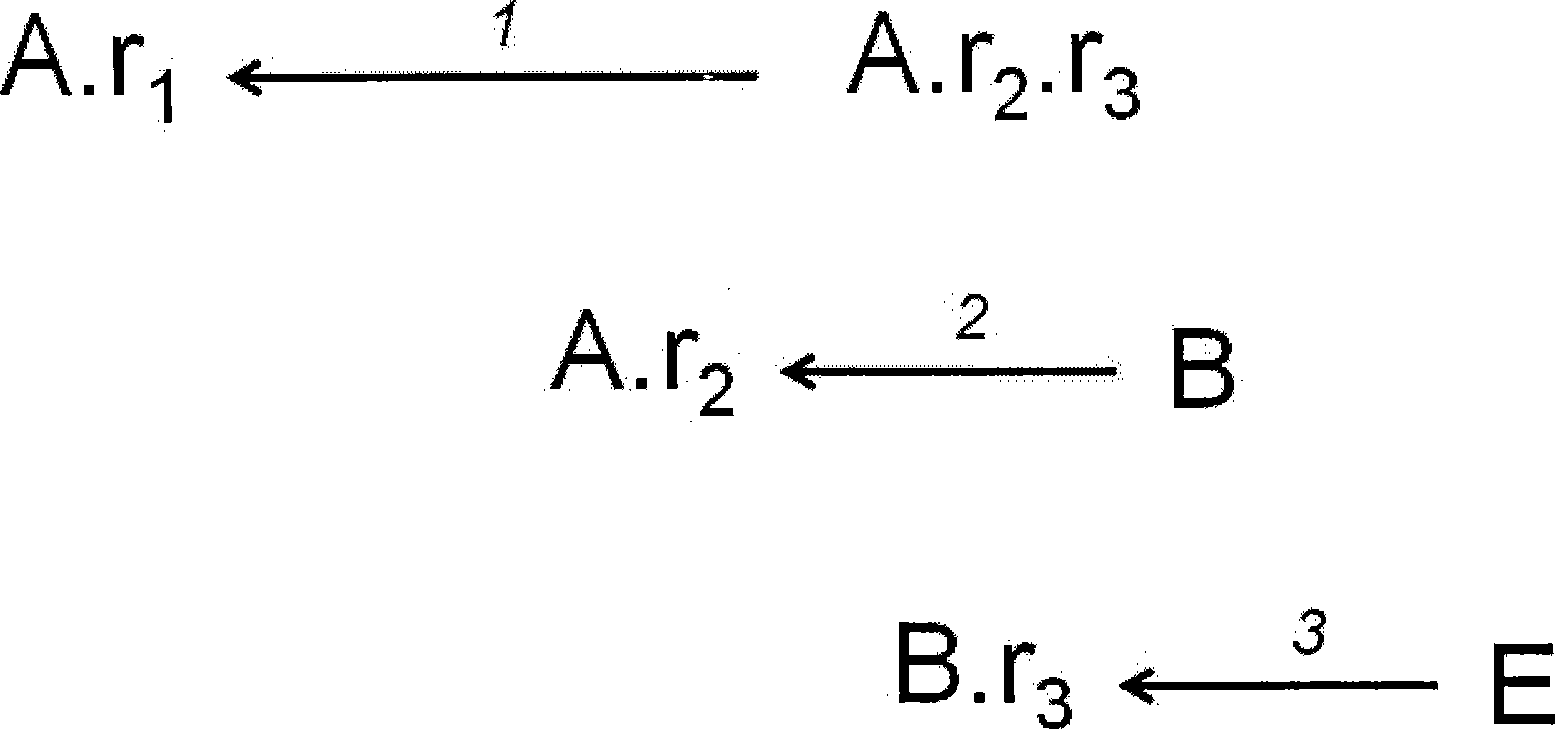Method for searching optimum certificate chain facing risk evaluation
A technology of risk assessment and certificate chain, which is applied in the field of optimal certificate chain search, can solve the problems that the certificate set cannot complete the search process within an effective time, the optimal certificate chain search method is not ideal, and the security analysis is complicated.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0025] In the role-based trust entrustment management system oriented to certificate risk assessment, the optimal certificate chain search method provided by the present invention can be used to accurately and effectively search for the optimal certificate chain. The specific implementation steps are as follows:
[0026] 1. Maintain X, Y, and Z three role expression sets:
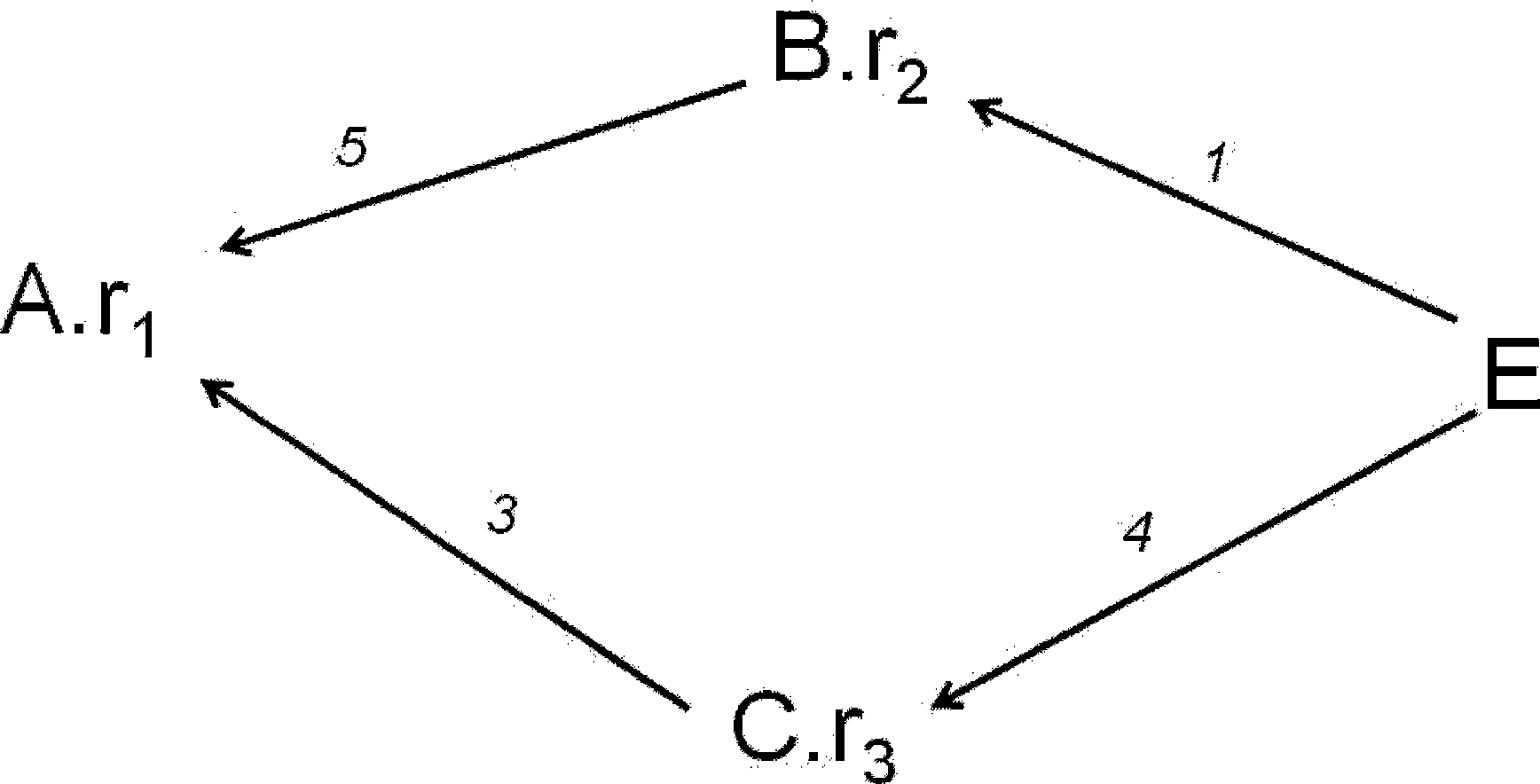
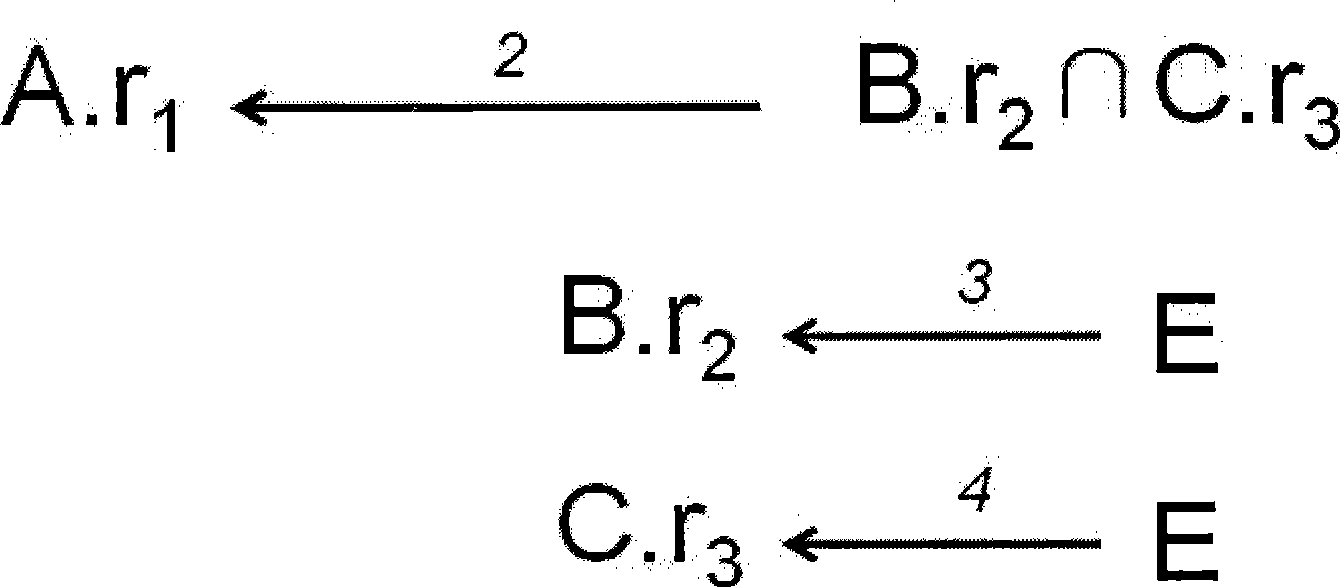
[0027] Among them, the X set is the role expression that has found the certificate chain with the smallest cumulative risk value starting from the given role, the Y set is the role expression that can be reached within one step from a role expression in the X set, and the Z set for the rest of the character expressions; with figure 1 As an example, the maintenance operation steps for these three collections are:
[0028] 1) At the beginning, set X set to be empty, set Y set to have only one given starting role, and all other role expressions are placed in Z set;
[0029] For example: in figure 1 In the s...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap