Program decomposing process
A technology of program decomposition and program, which is applied in the field of information security and software engineering, can solve security threats and other problems, achieve the effect of low complexity, reduce workload and improve efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0059] Embodiments of the present invention will be described in more detail below in conjunction with the accompanying drawings.
[0060] The program decomposition method used for vulnerability mining in this embodiment includes the following steps:
[0061] Step 1: Set the initial function and final function.
[0062] In this embodiment, fread is used as the initial function, and execv is used as the final function.
[0063] Step 2: Use the function set composed of the initial function and the function that directly or indirectly calls the initial function as Source; use the function set composed of the final function and the function that directly or indirectly calls the final function as Sinks.
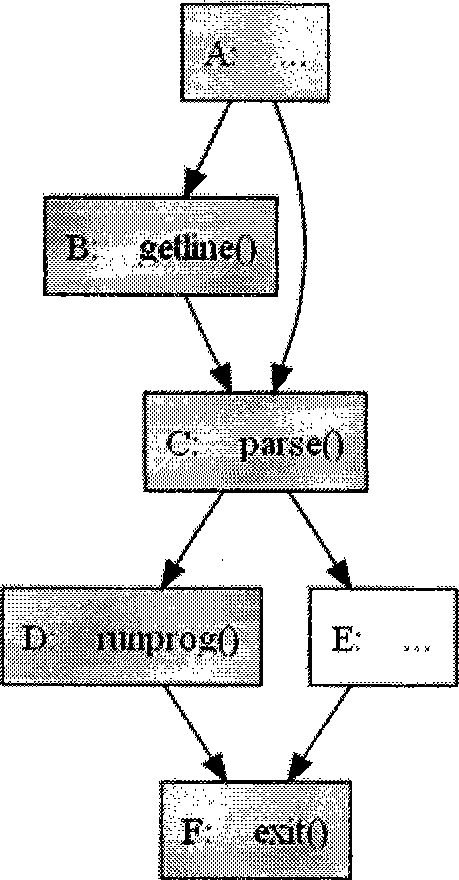
[0064] For example, if figure 1 As shown, getline directly calls fread, so it is added to Source, and main indirectly calls execv through getline, so it is also added to Source.
[0065] In this example, the typical running results are:
[0066] Source={fread, getline, main} ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com