Data transmission ciphering and integrity checking method
A technology for integrity verification and data transmission, which is applied in transmission systems, electrical components, wireless communications, etc., can solve the problems of destroying shared serial number attacks, inability to resist, and inability to stop, so as to solve data tampering behavior and improve security , performance-enhancing effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0012] Embodiments of the present invention will be described in detail below in conjunction with the accompanying drawings. This embodiment is carried out on the premise of the technical solution of the present invention, and the detailed implementation and specific operation process are given; but the protection scope of the present invention is not limited to the following embodiments.
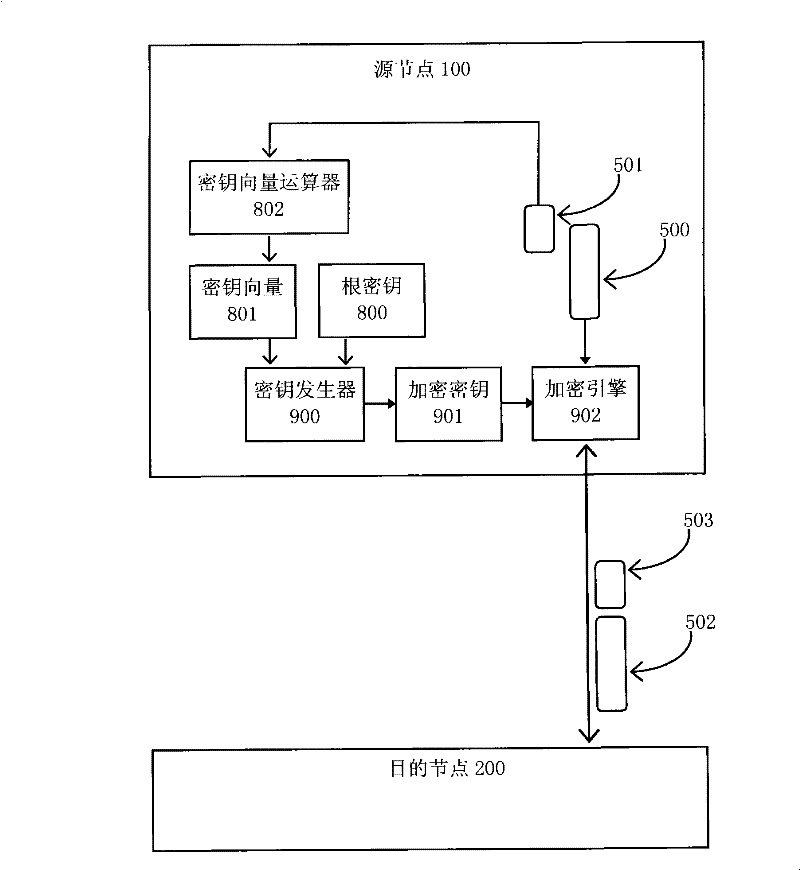
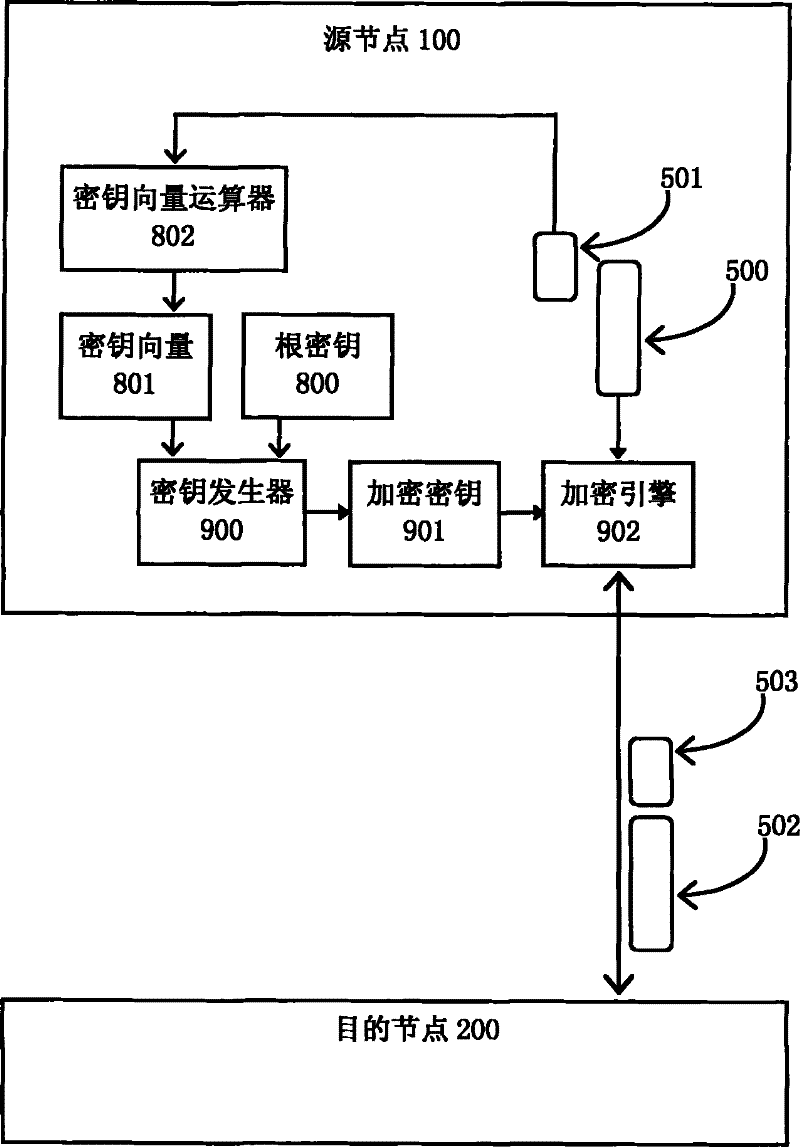
[0013] Such as figure 1 As shown, data 500 is currently being transmitted from source node 100 to destination node 200 . In order to encrypt the transmitted data 500 and implement integrity verification, the source node performs the following process:
[0014] Generate message authentication code 501 for data 500;
[0015] Encrypt data 500 to obtain ciphertext data 502;
[0016] The result sent to the transmission path is ciphertext data 502 and message authentication code 503;
[0017] If the message authentication code is not encrypted, the sent message authentication code 503 is the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com