Anti-tamper verification method for key data in database
A technology of key data and inspection methods, applied in the fields of electrical digital data processing, special data processing applications, instruments, etc., can solve problems such as inability to detect and monitor core data, and achieve the effect of ensuring accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0019] The present invention will be described in detail below with reference to the accompanying drawings and in combination with embodiments.
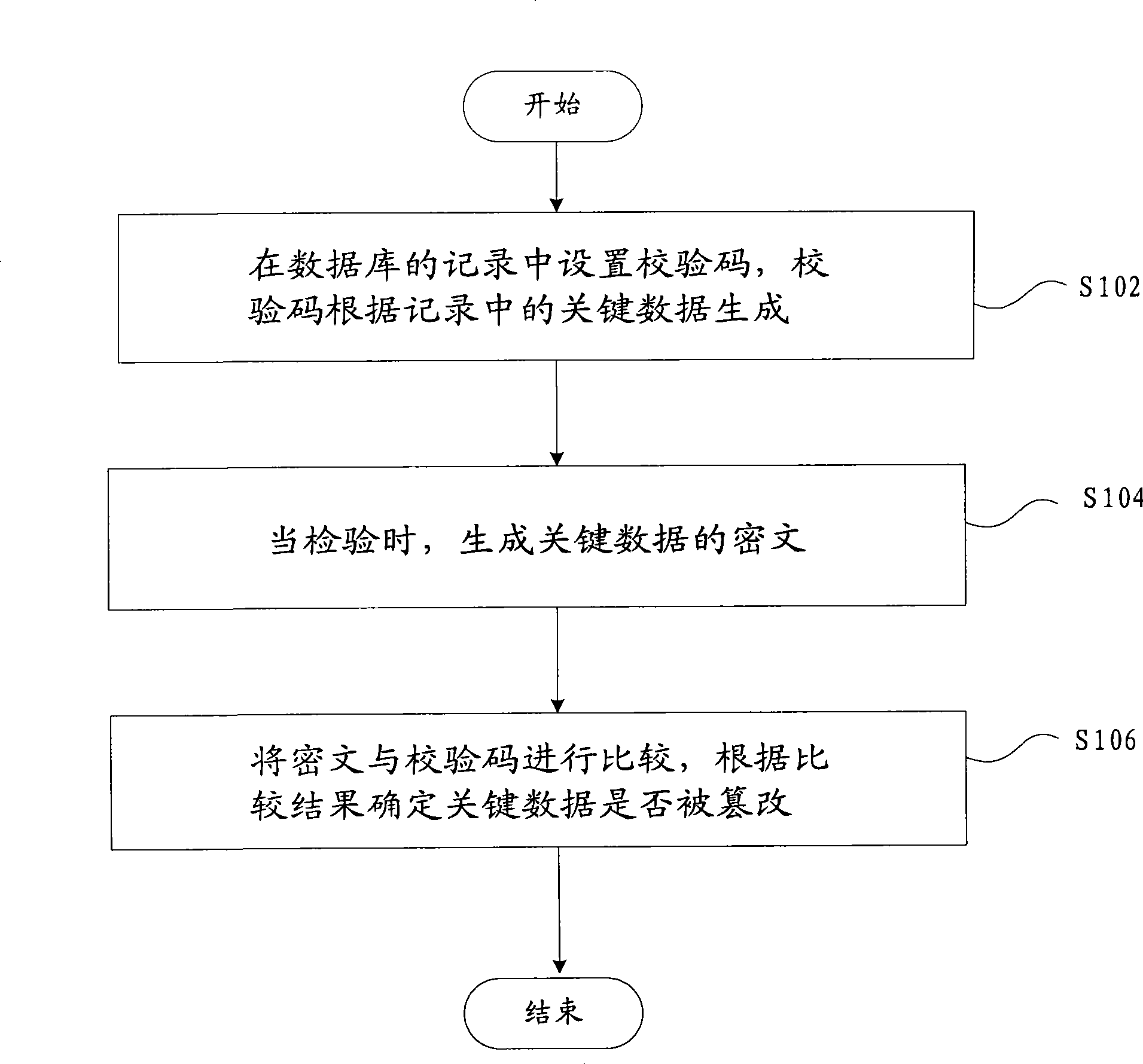
[0020] figure 1 It shows a flow chart of a tamper-proof inspection method for database key data according to an embodiment of the present invention, including the following steps:
[0021] S102, setting a check code in the record of the database, the check code is generated according to the key data in the record;
[0022] S104, when checking, generate the ciphertext of the key data;
[0023] S106, comparing the ciphertext with the check code, and determining whether the key data has been tampered with according to the comparison result.
[0024] The above-mentioned embodiment generates ciphertext by combining the key data with the key configured in the system, compares the ciphertext with the check code generated in the same way stored in the database, and determines whether the key data has been tampered with according to the com...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com