Method and apparatus for error control in network system
A control device and error technology, applied in the field of error control, can solve the problems that cannot be aggregated and analyzed, and cannot analyze the type of errors, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
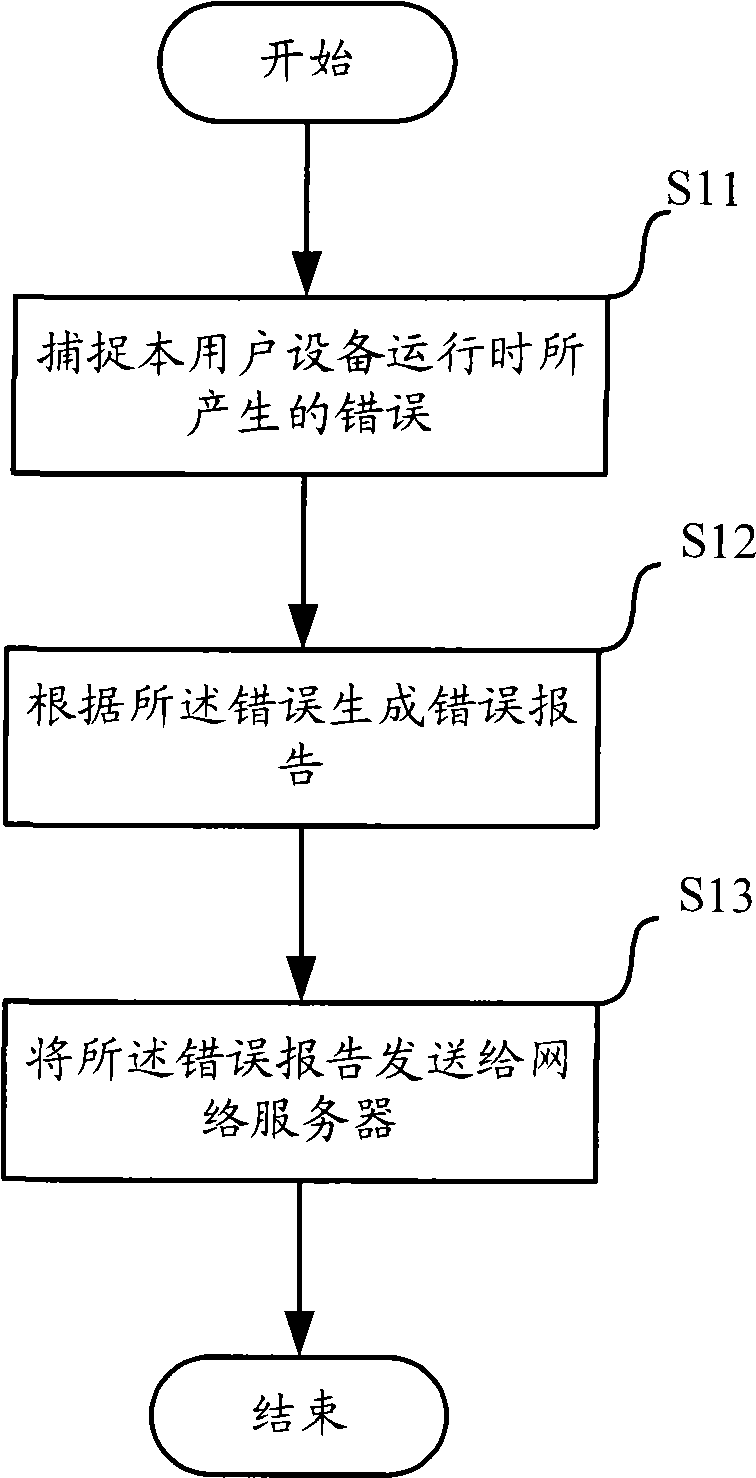
[0038] Embodiment 1: A memory out-of-bounds error occurs when a single user equipment runs corresponding software.
[0039] In order to save relatively few memory resources, the operating system generally divides the memory into different levels of memory according to the size of the memory. When applying for a memory block for a specific application program running related software on a single user device, it is necessary to declare the required memory size. The operating system Then return the corresponding memory block to the application. The general memory length segmentation is defined as: 16, 32, 64, 128, and 256 bytes.
[0040] image 3 It shows a schematic structural diagram of a storage structure of the memory of the user equipment using a one-way linked list with a head node. refer to image 3 , it can be seen that by visiting the head node, the chain head node can be accessed from "pointing to the chain head node". All nodes of the linked list. In memory, linke...
no. 2 example
[0048] The second embodiment: the code error related to the version of the corresponding software run by the user equipment.
[0049] In practice, due to the incompleteness of the software function test, there are always more or less code errors in the software, so the software version is always constantly upgraded.
[0050] Specifically, in this embodiment, it is taken that the user equipment 1 runs network transmission software based on the P2P protocol as an example. In the above step S11, if the error phenomenon captured by the user equipment 1 is an out-of-bounds error in the code memory of the 50th line of the software, according to the error phenomenon, the cause of the error is analyzed as the application for the 10th line of the software code. The memory length is inconsistent with the length of the data actually written in line 50. The user equipment 1 determines that the type of the error is a code error of the software run by the user equipment 1 according to the ...
no. 3 example
[0057] Embodiment 3: The user equipment runs the network transmission software to download the media file from the download source, resulting in a file or file fragmentation error.
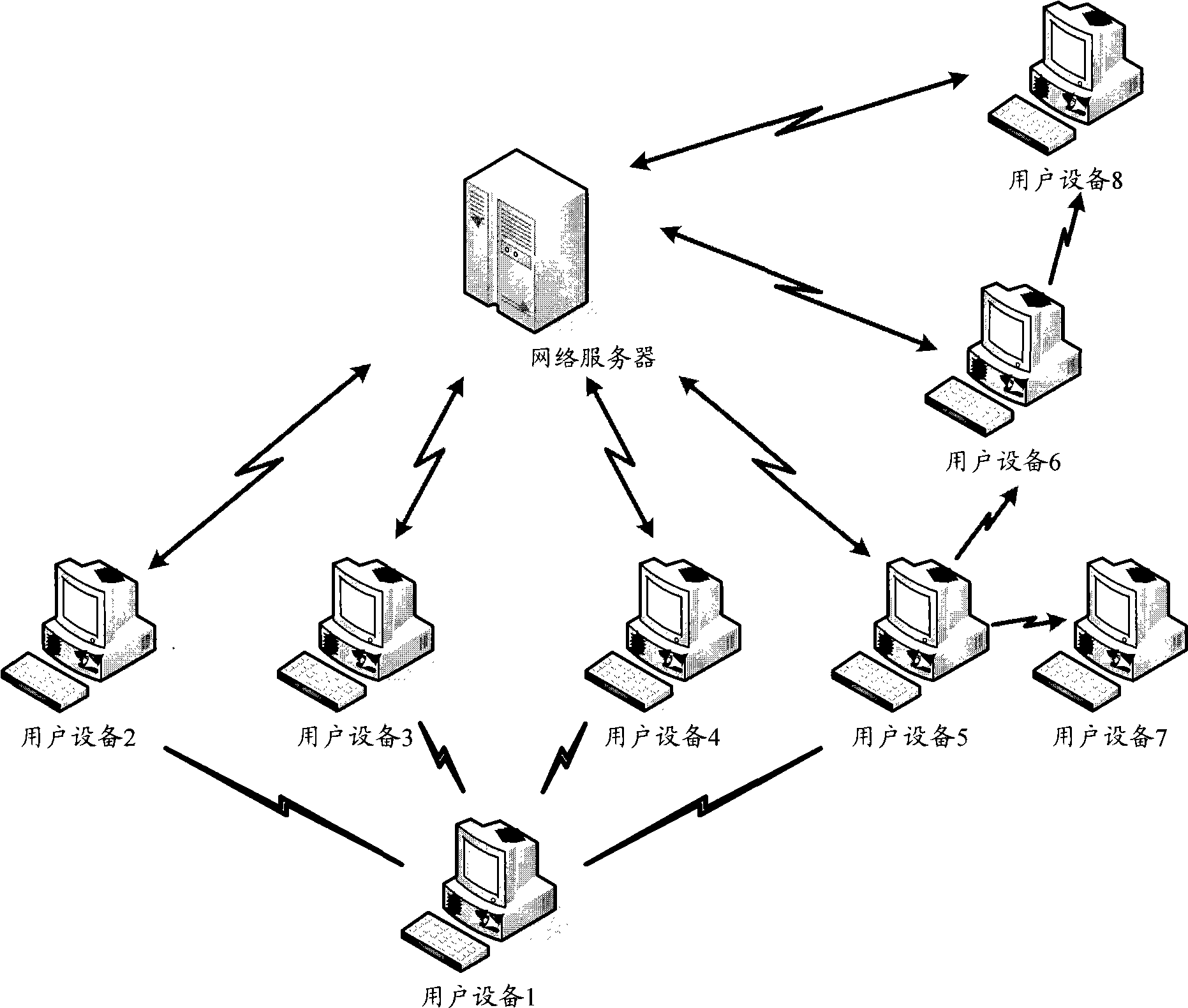
[0058] refer to figure 1 , the network based on the P2P protocol in this embodiment includes multiple user equipments and one network server.
[0059] Usually, the network server generates a file list according to all the file information therein, and the file list includes a check value of each file and / or each file fragment, such as an MD5 check value. The user equipment first obtains the file list from the network server or other user equipment. After the user equipment obtains a certain file or a certain file fragment in the file list, the obtained file or file fragment is subjected to MD5 verification processing to obtain an MD5 verification value; the obtained MD5 verification value is compared with Compare the MD5 check value corresponding to the file or file fragment in the previously ob...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com