Method and device for authenticating terminal and telecommunication smart card
A terminal authentication and smart card technology, which is applied in the field of data security, can solve problems such as maintenance inconvenience, no solution, and terminal failure rate increase, and achieve the effects of avoiding the loss of call charges, maintaining tariff policies, and curbing machine-card separation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0031] In order to illustrate the technical solutions of the embodiments of the present invention more clearly, the embodiments of the present invention will be described in detail below in conjunction with the accompanying drawings. The following descriptions are only some embodiments of the present invention. For those of ordinary skill in the art, Other implementations of the present invention can also be obtained according to these embodiments without any creative effort.
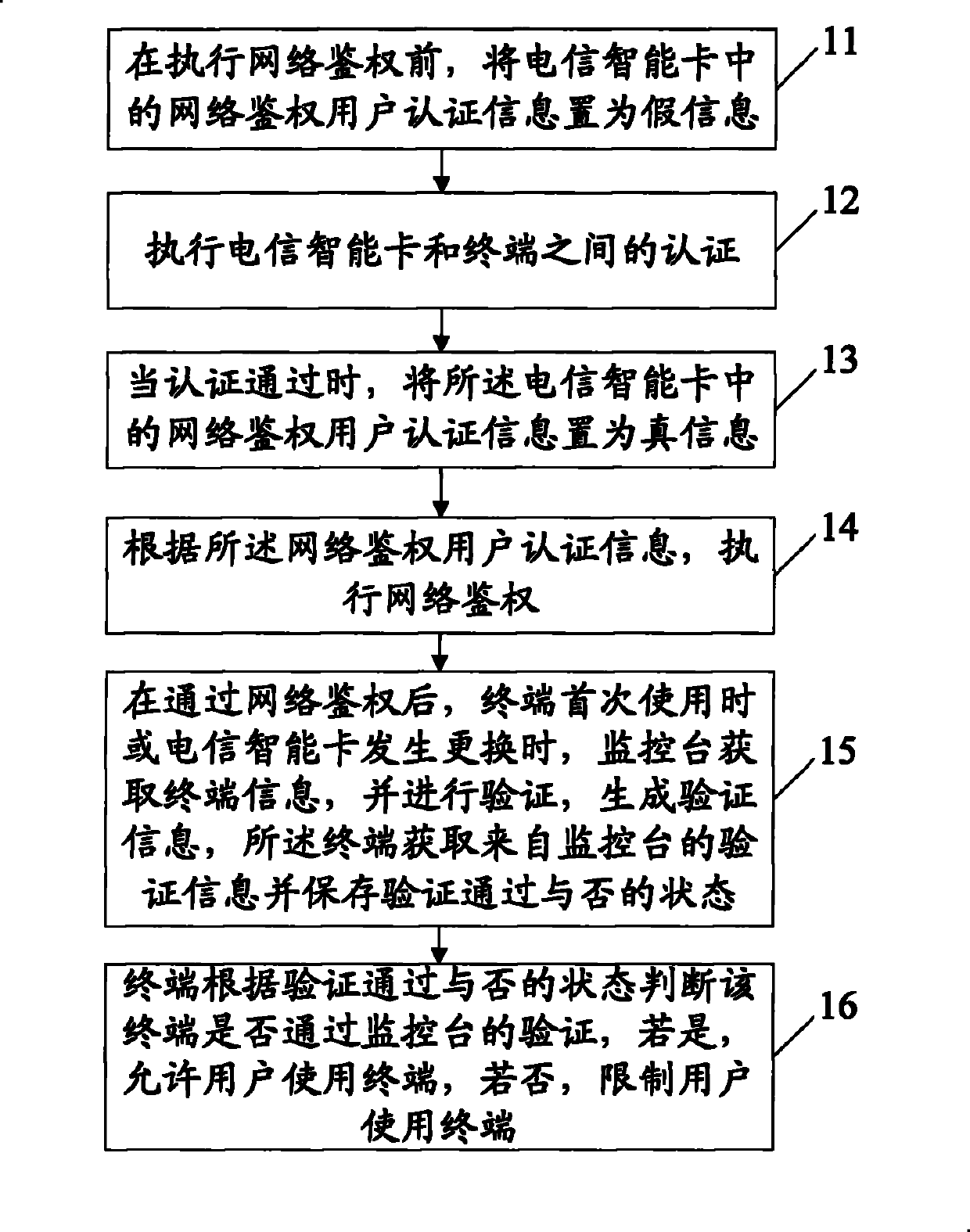
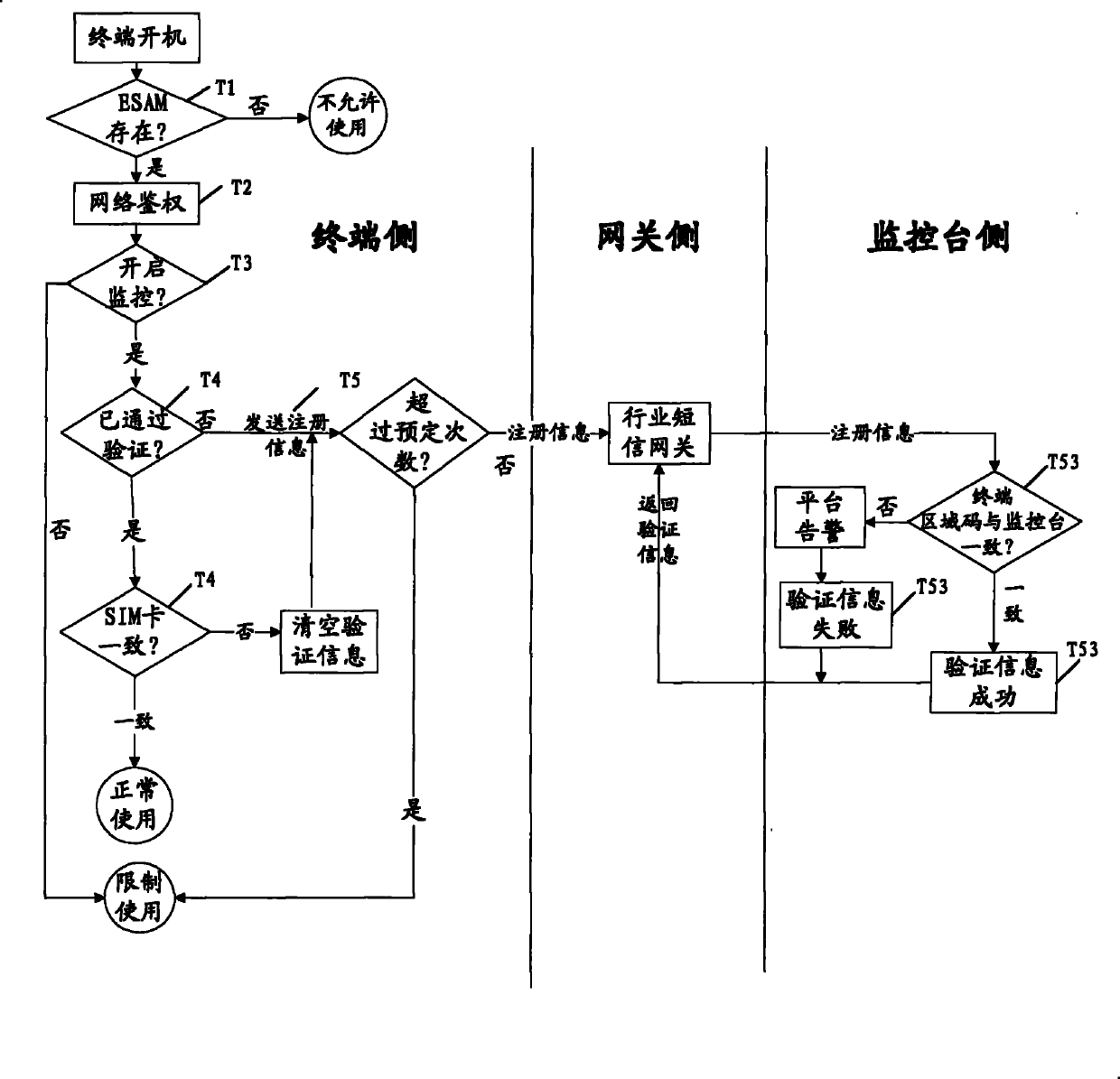
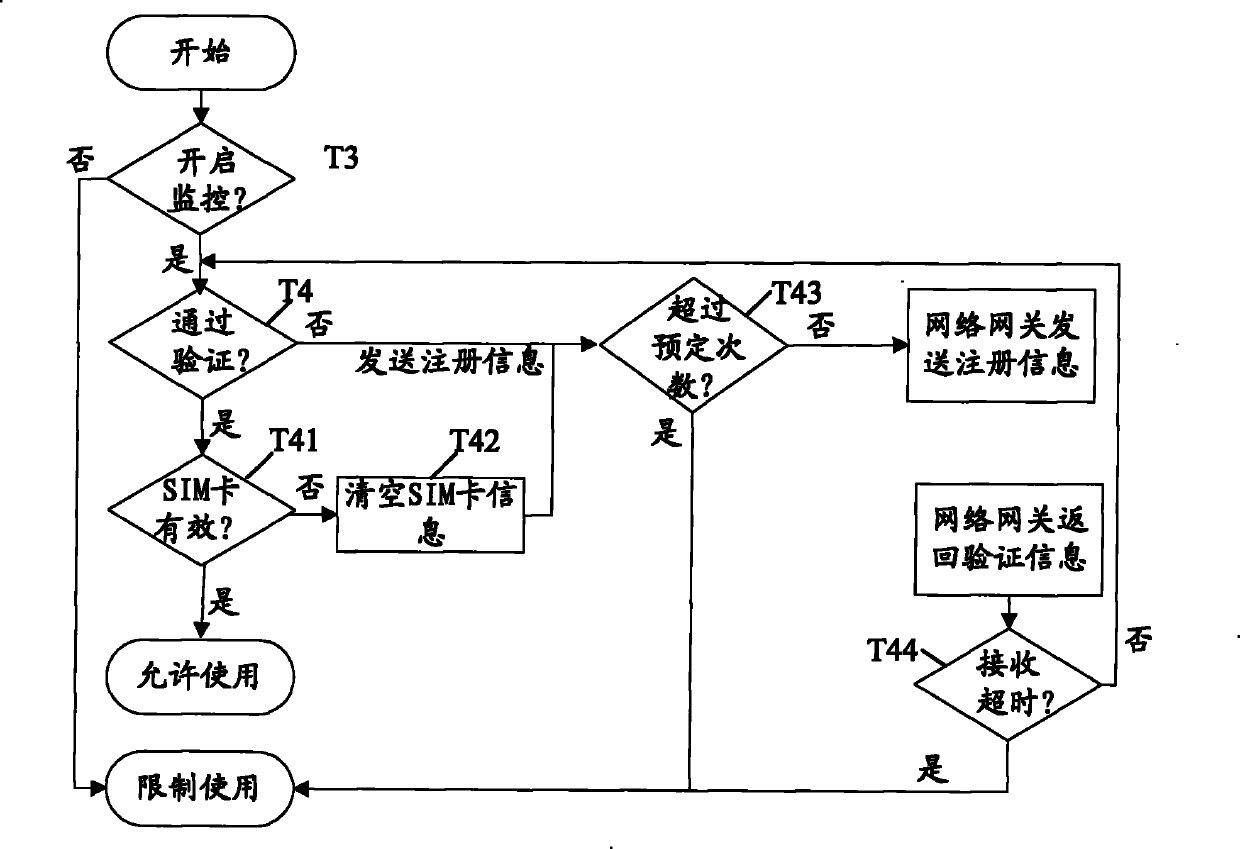
[0032] Embodiment 1 of the present invention mainly solves the problems of SIM cards being stolen and terminals being set out, etc. through a terminal verification combined with platform management scheme. In terms of terminal verification, it is preferable to use the terminal and an embedded security module (Embedded Security Access Module, ESAM) for authentication, without modifying the standard hardware, which saves costs and is easy to set up and maintain, and has a low failure rate; On the one hand...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com