SQL resisting injection technology using regular expression
A technology of expression and technology, applied in the field of anti-SQL injection technology using regular expressions, can solve problems such as scalability limitations, and achieve the effect of avoiding stack overflow
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0033] Embodiments of the present invention will be described in detail below.
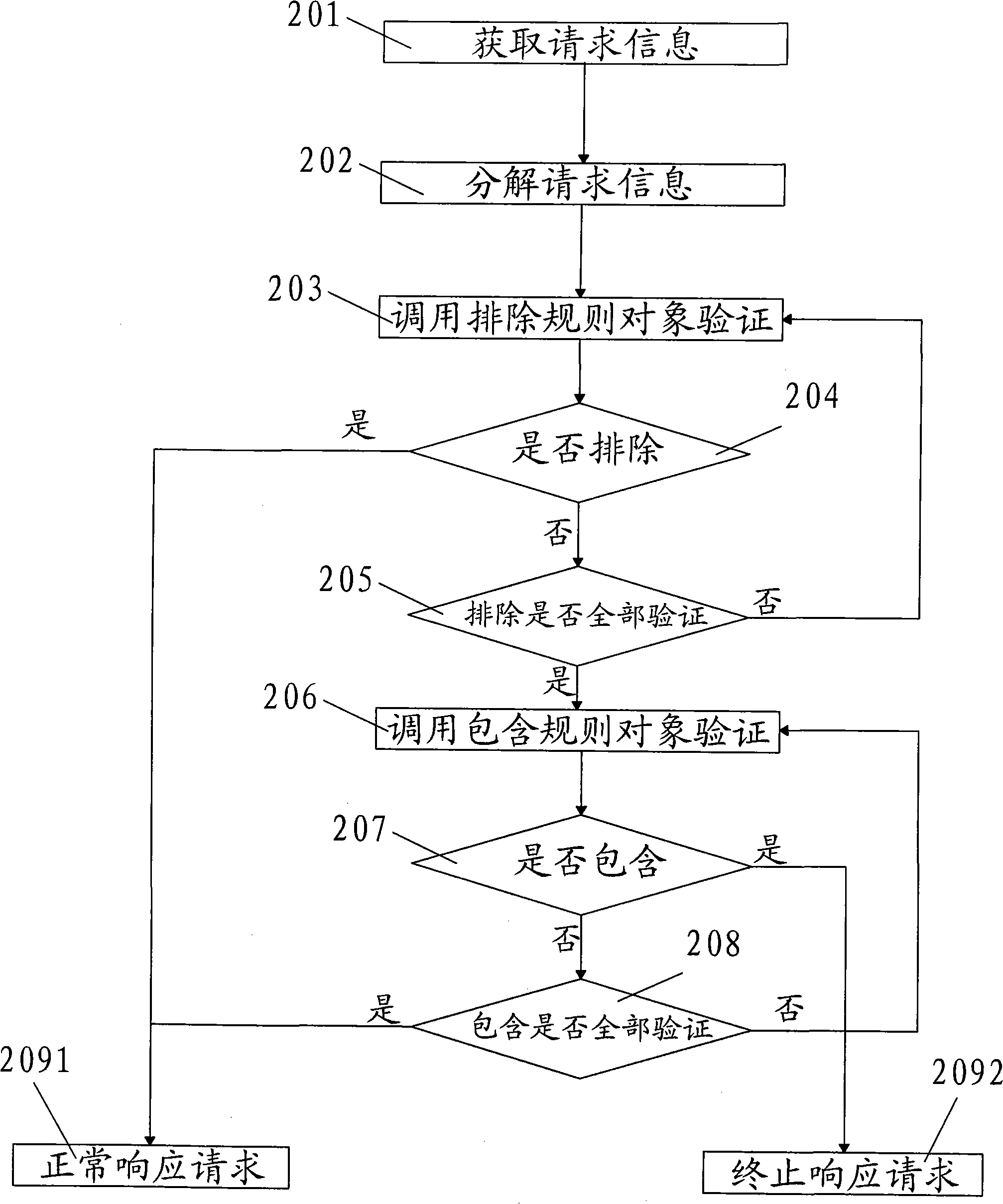
[0034] An anti-SQL injection technology using regular expressions, which first performs process initialization and then performs verification.
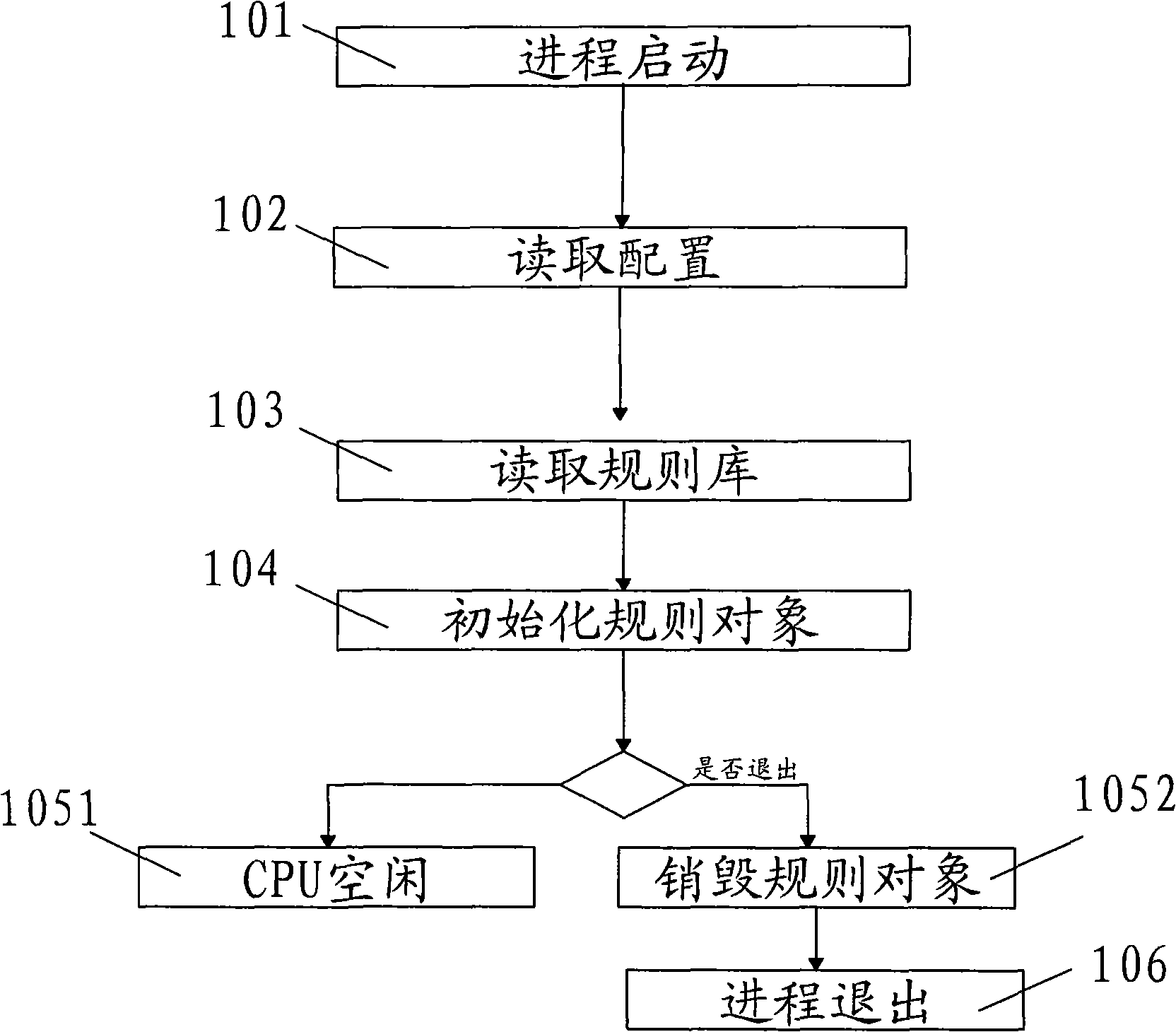
[0035] The initialization process is as follows figure 1 As shown, the process starts at step 101, and the process starts.
[0036] Then enter step 102, read the configuration, and for the flexibility of the system, some parameters are specified by manual configuration through configuration. Because the configuration information affects the running process of the system, it is the first action to be executed after the process starts.
[0037] Then go to step 103, read the rule base, and write the rule information into the configuration file for easy scalability and maintainability of the program. The purpose of this step is to read the content in the rule base into the memory.
[0038] Then enter step 104 to initialize rule objects. In order to improve...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com