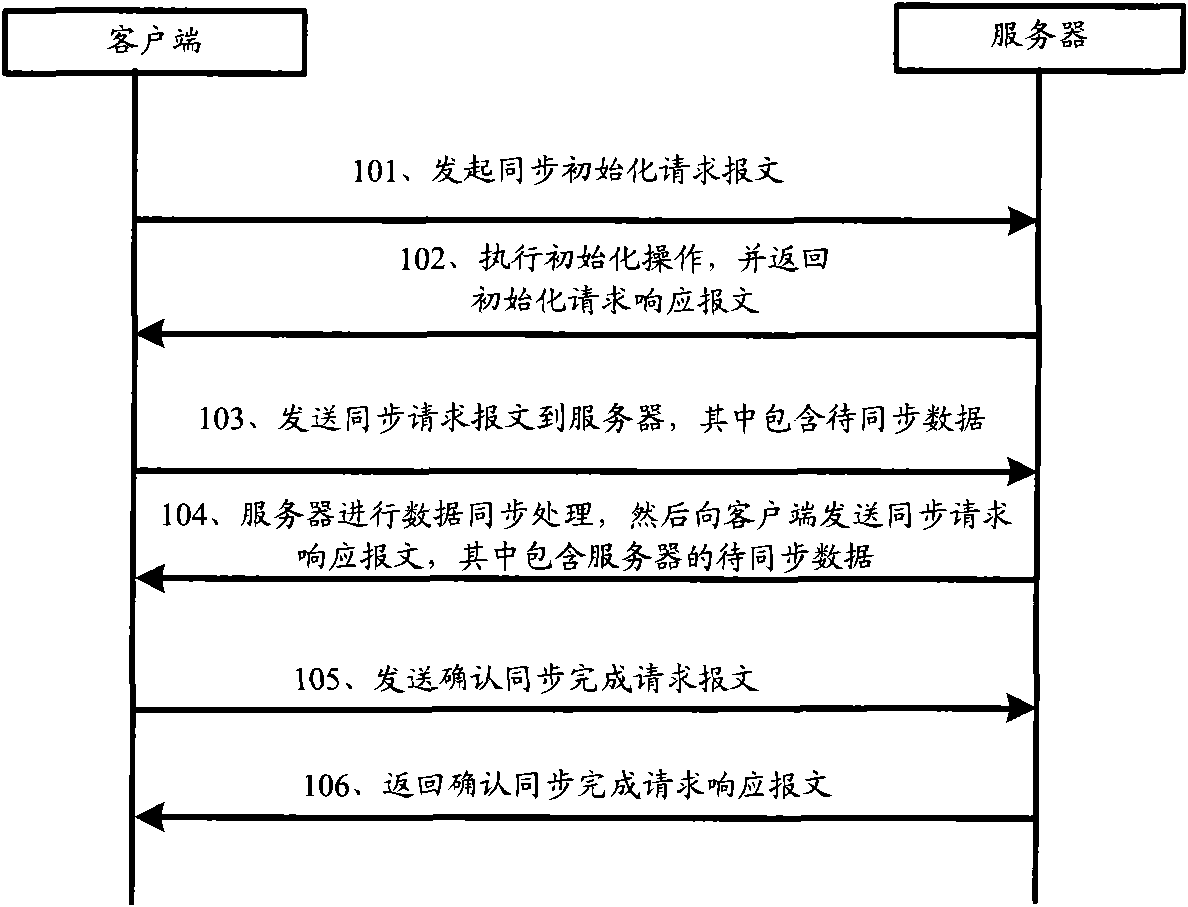
Data synchronous method, client, server and system
A data synchronization and client-side technology, applied in the field of communications, can solve the problems of large amount of data transmission, low transmission efficiency, and inability to synchronize data compression, and achieve the effect of large amount of transmitted data and high transmission efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 2
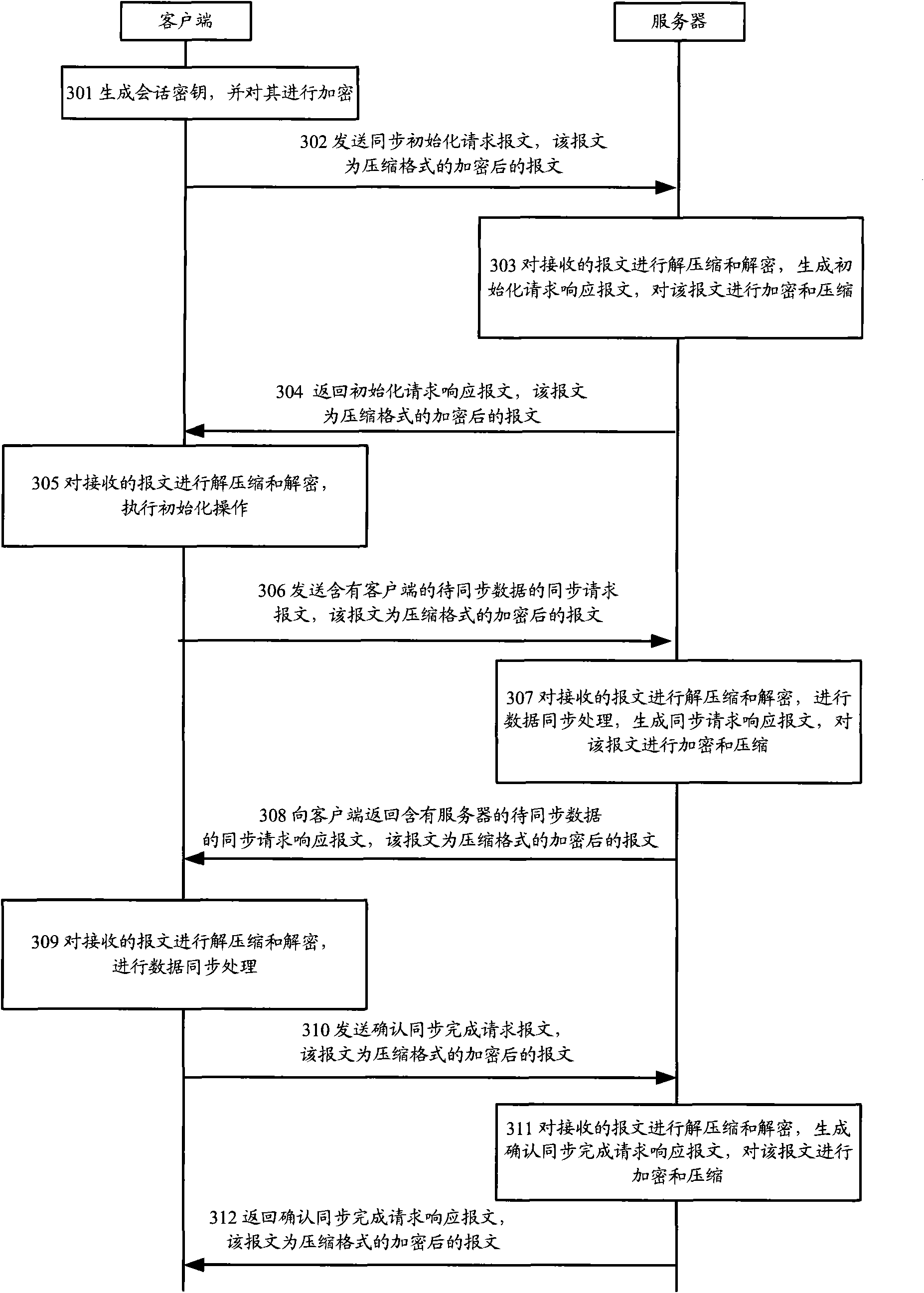
[0046] In Embodiment 2, the server requires the message from the client to be encrypted, and the client has pre-installed or downloaded the server's certificate from the network side. The certificate is an asymmetric key, and the public key is used for client encryption, where The private key of the server is used for decryption by the server, and the server considers the client requesting access to be trusted, and does not require the client's certificate.
[0047] image 3 Including:
[0048] 301. The client generates a session key and encrypts it;
[0049]After the client confirms that it has installed the server's certificate and that the certificate is within the validity period, it generates a session key for encrypting messages, encrypts the generated session key with the public key of the server certificate, and uses the session key to Use the key to encrypt the initialization request message to be transmitted, and then use the specified format in the request message...
Embodiment 3
[0131] Embodiment 3 By defining the path separator negotiation method between the client and the server, it is avoided when the path separator (such as " / ") supported by the client is different from the path separator (such as "\") sent by the server. Data synchronization between client and server is abnormal or fails.
[0132] The steps of the third embodiment are basically the same as those of the second embodiment, except that there are some changes in the processing in the initialization phase.
[0133] Embodiment 3 In the initialization request message sent from the client to the server, an element , used to indicate the path separator that the client can handle (such as the unix operating system path separator " / " or the windows operating system path separator "\", etc.), that is, the response message that the server is required to return All path separators in must conform to the value defined by PathSeparatorType.
[0134] In addition, an element , used to indicate th...
Embodiment 4
[0157] Embodiment 4 mainly sets the information about the maximum number of commands contained in a message supported by the client and informs the server, so as to avoid the failure problem caused by the number of commands contained in a message sent by the server exceeding the processing capacity of the client.
[0158] The steps of the fourth embodiment are basically the same as those of the second embodiment, except that the processing process in the initialization phase has some changes.
[0159] Embodiment 4 In the initialization request message sent by the client to the server, an element , used to indicate the maximum number of commands in a message that the client can process, that is, the number of commands contained in the response message returned by the server cannot exceed the value defined by MaxCmdCnt.
[0160] The following is an example of the revised DevInf of the embodiment of the present invention:
[0161]
[0162] 1.1
[0163] huawe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com