Unified management method and device thereof
A management method and technology for managing devices, which are applied in the field of unified management methods and devices, can solve problems such as repetitive labor, large maintenance workload, and complicated use of audit functions, and achieve the effects of reducing occupation and maintenance work.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
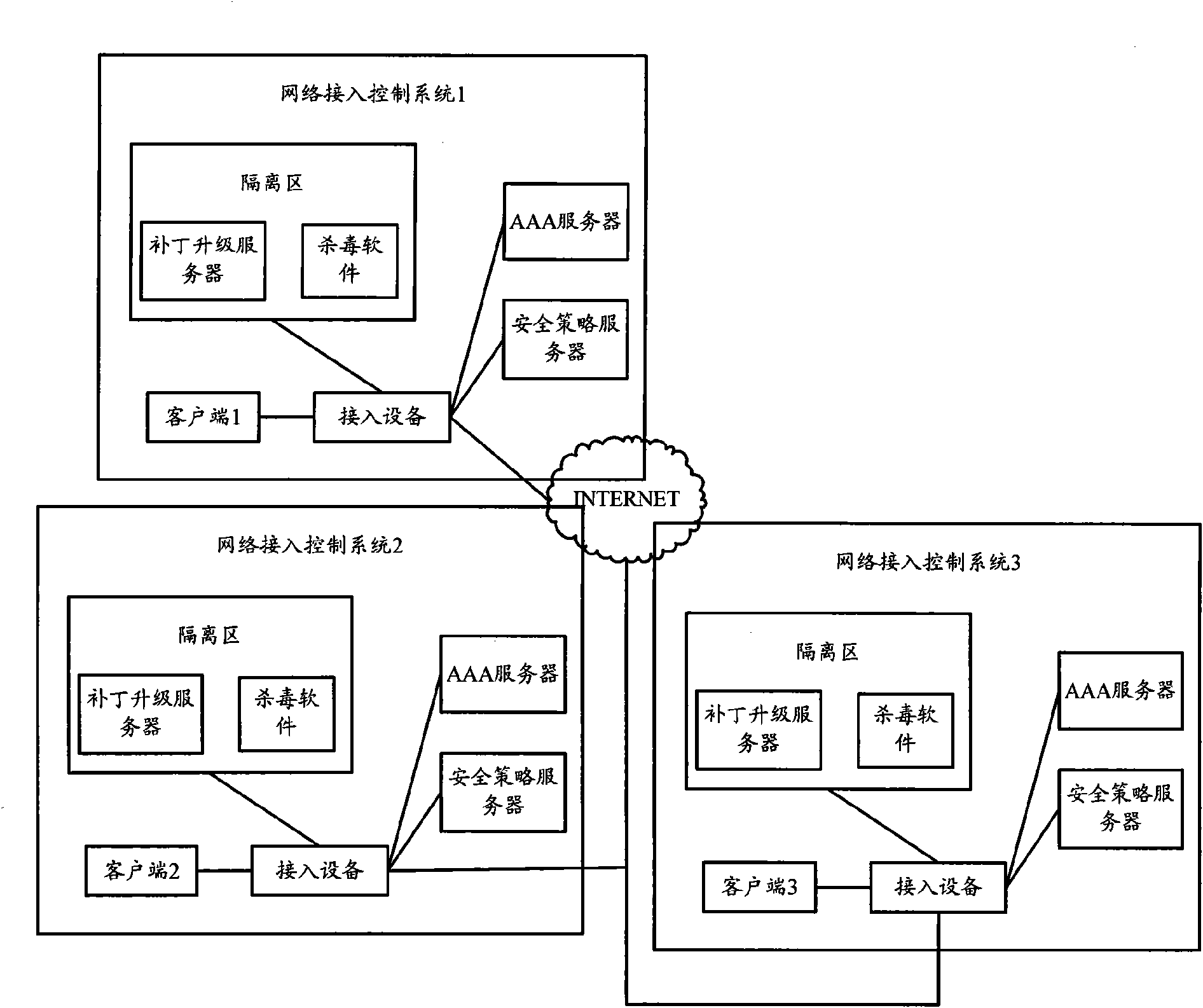
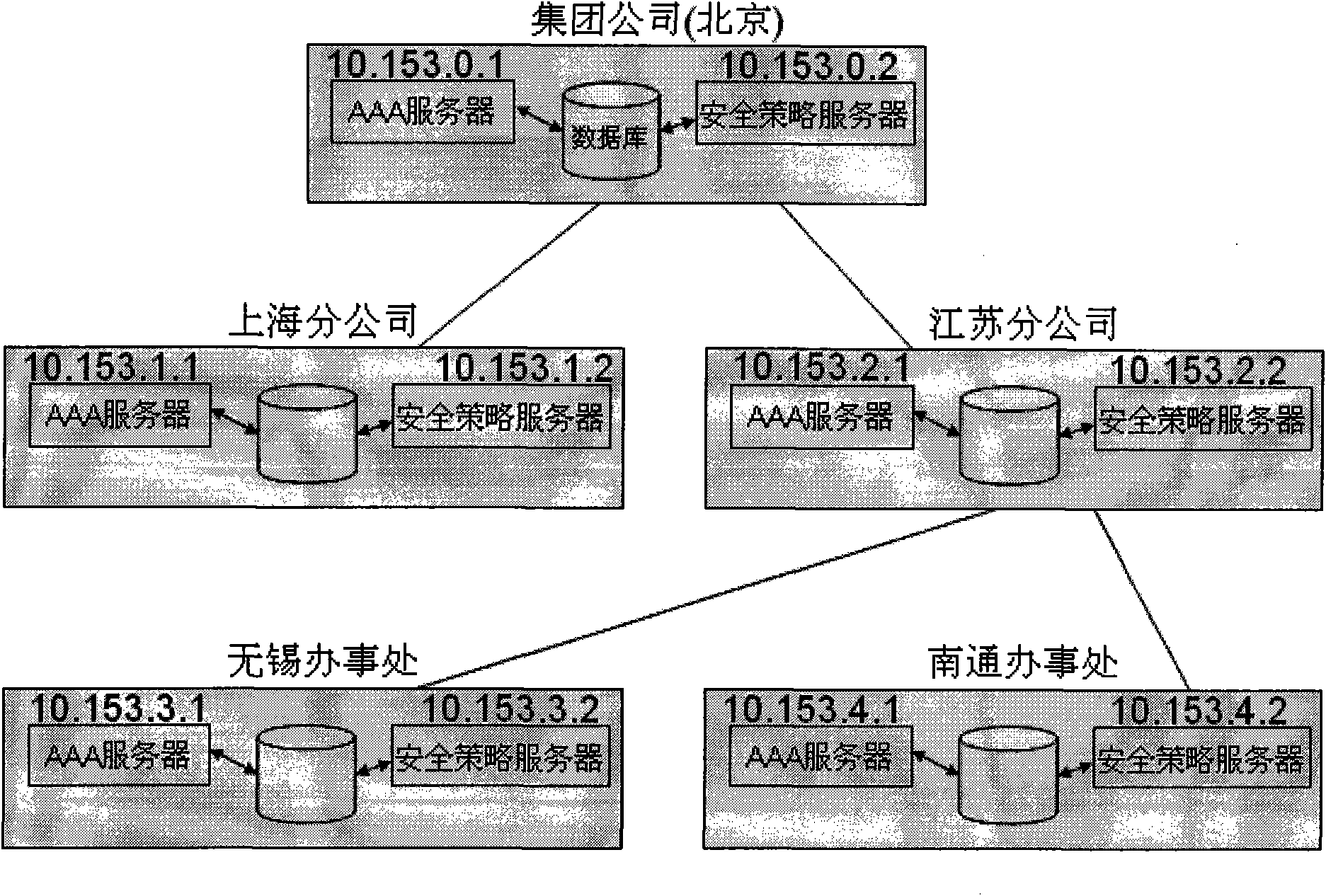
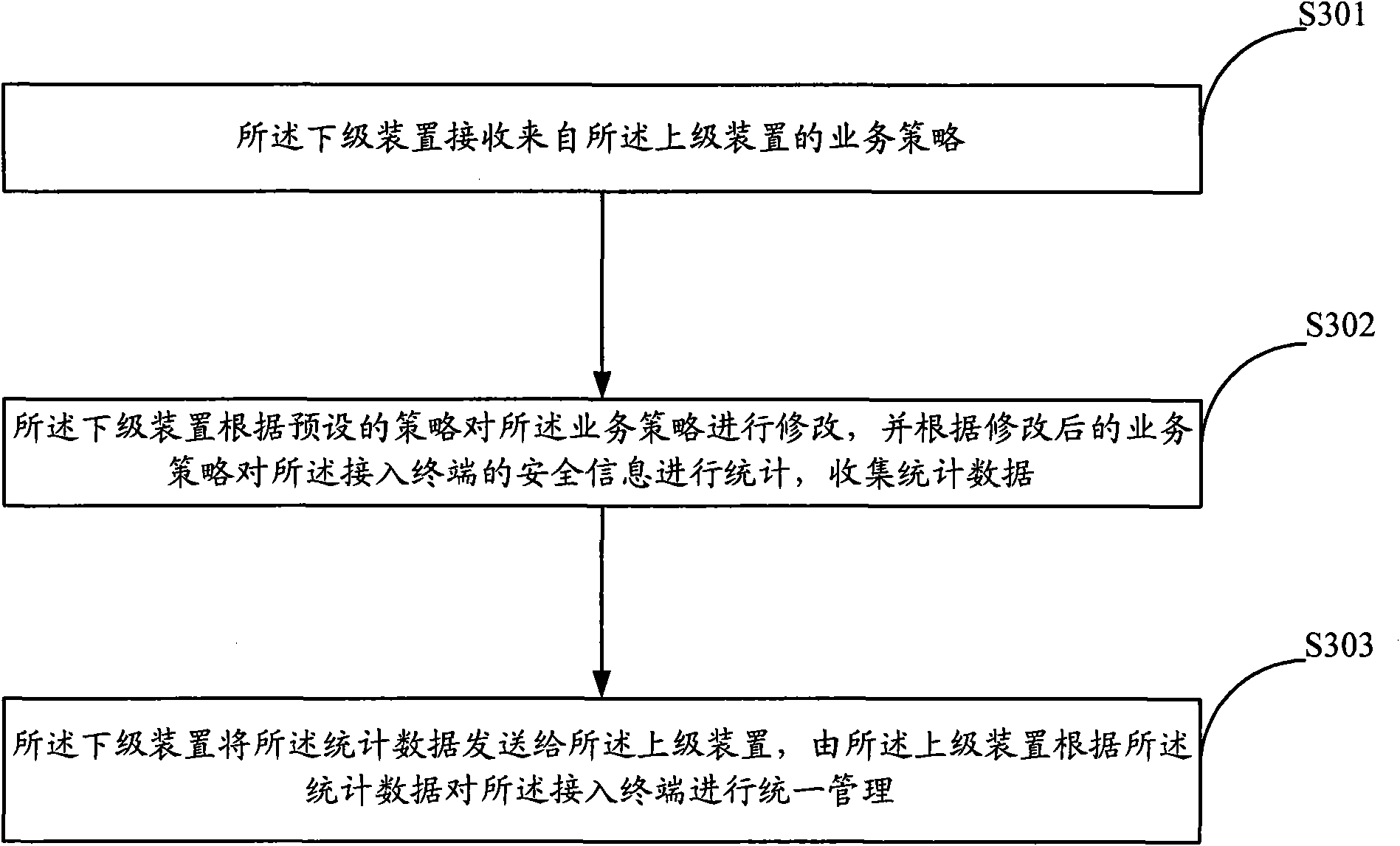
[0063] The core idea of the present invention is in the network access control system of distributed deployment (the network control systems of each branch are in an equal relationship, each branch uses its own independent database, and the network control systems of each branch operate independently) , all the branches are divided into multi-level relationships, and the business policy is uniformly formulated by the upper-level branch structure, and the business policy is manually distributed to the lower-level branches or automatically distributed to the lower-level branches. Wherein, the business strategy includes an authentication strategy and a security strategy, the authentication strategy is a set of binding information related to authentication (for example, the binding relationship between terminal name, identifier, IP address, and terminal name), and the security strategy is a set of binding information related to authentication. Relevant data (for example, traffic ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com