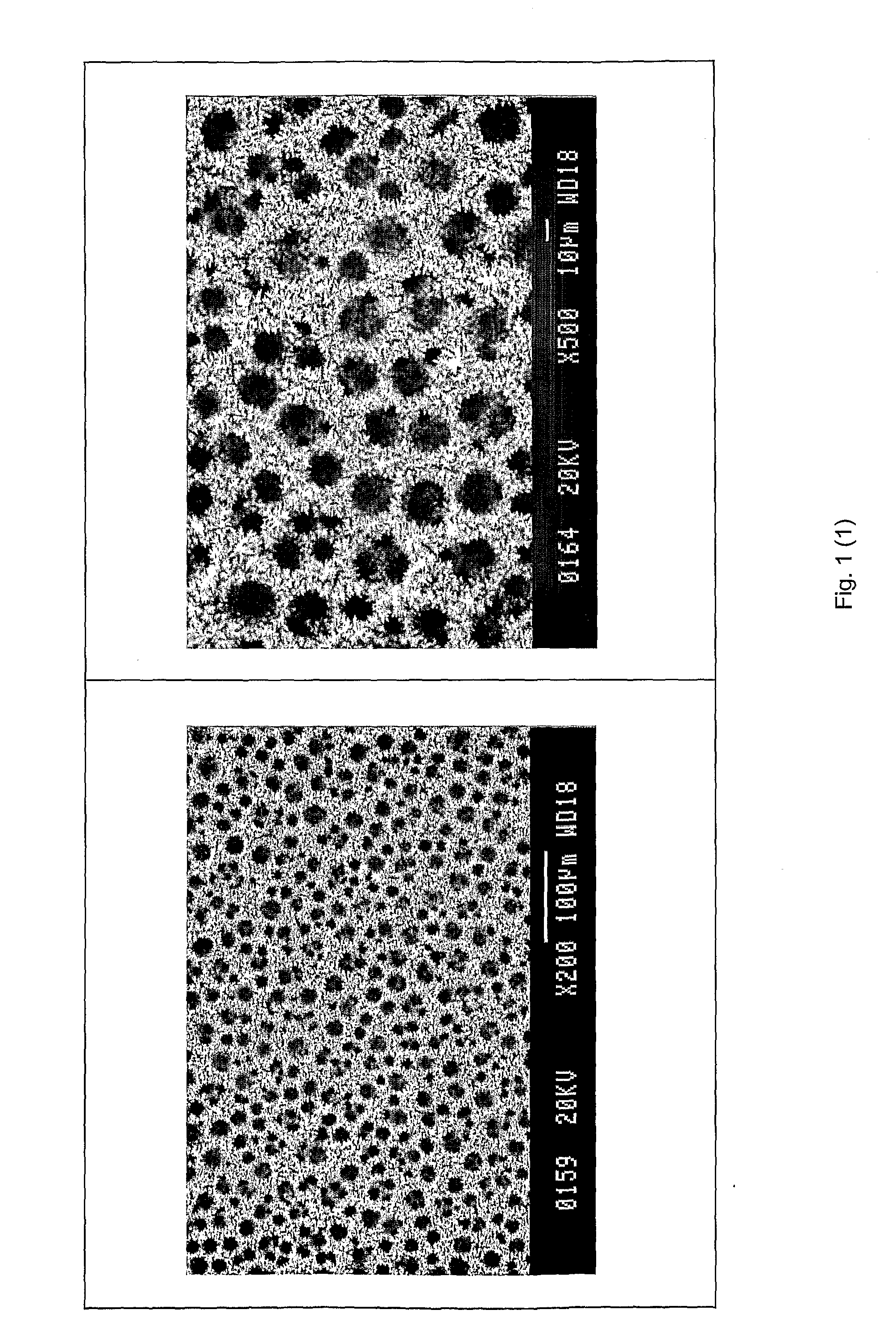
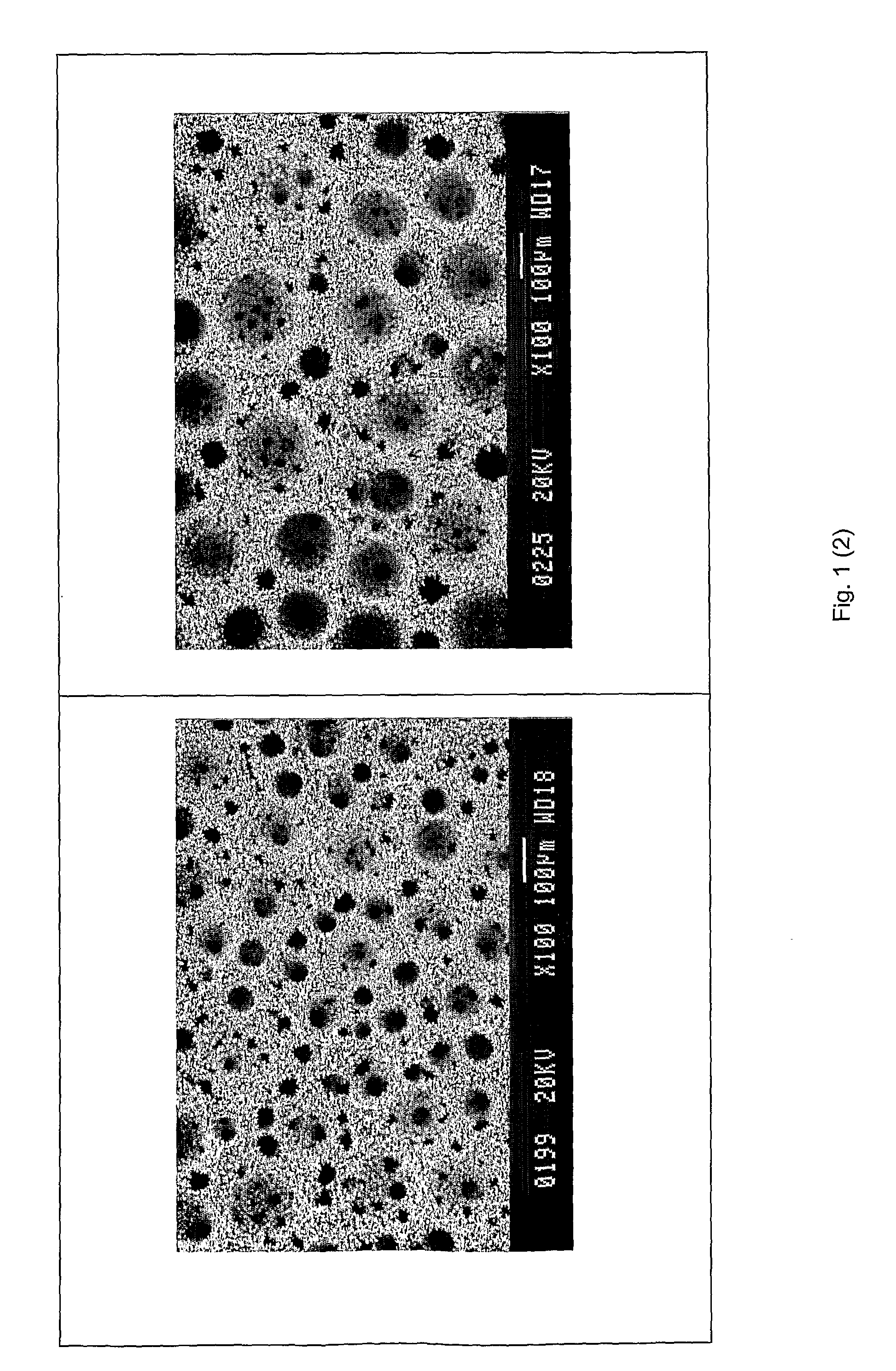
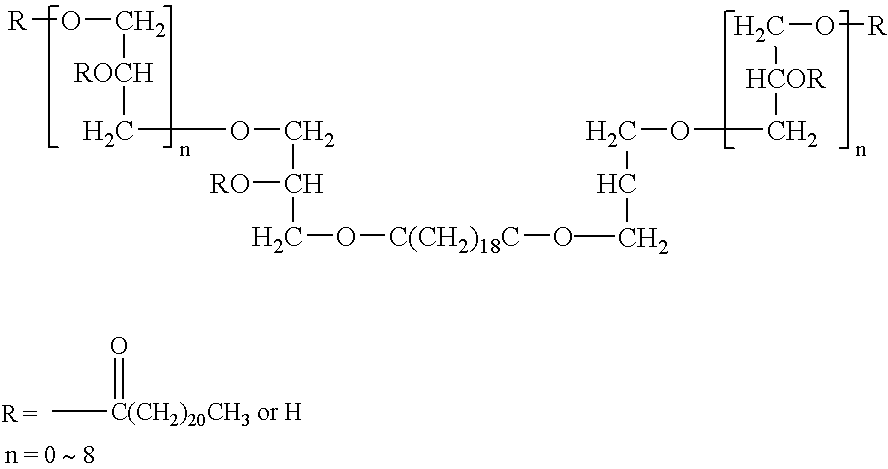
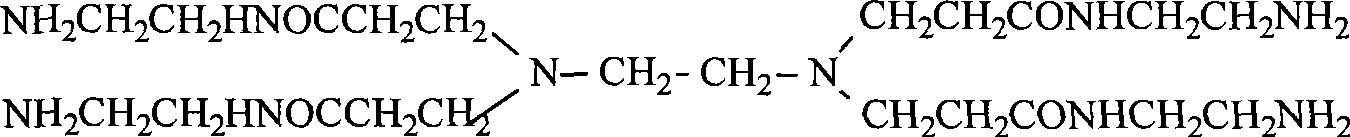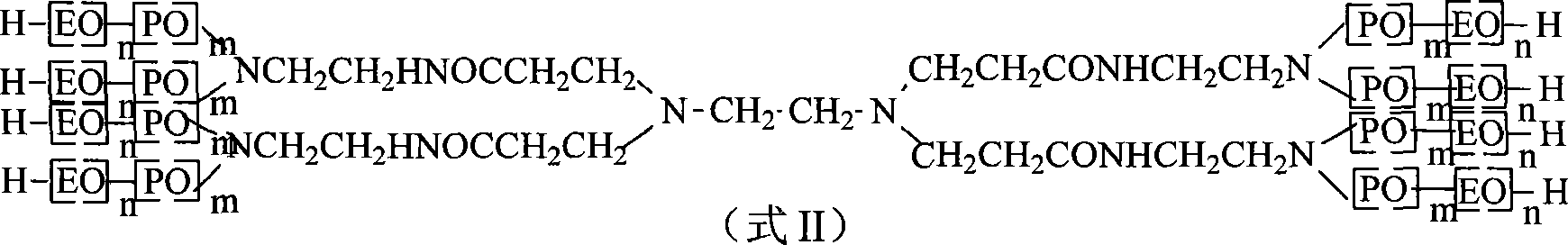Patents
Literature
804 results about "Branch structure" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Branch Structure. UNISON has a clear branch structure to ensure that all members have their say. Each year the Annual General Meeting elects the Branch Officers and Stewards for the coming year. Local stewards are there to represent you at work and help find the answers to your problems.
Non-leaching non-fouling antimicrobial coatings
InactiveUS20090155335A1Solve the lack of flexibilityPromote adequate mobilityAntibacterial agentsPeptide/protein ingredientsDendrimerFiber
Compositions containing one or more types of membrane-targeting antimicrobial agents immobilized on a substrate with activity in relevant biological environments, and methods of making and using thereof, are described herein. The antimicrobial agents retain their activity in the presence of blood proteins and / or in vivo due to improved molecular structures which allow for cooperative action of immobilized agents and hydrophilic chemistries which resist non-specific protein adsorption. Suitable molecular structures include branched structures, such as dendrimers and randomly branched polymers. The molecule structures may also include hydrophilic tethers which provide both flexibility and resistance to non-specific protein adsorption. The membrane targeting antimicrobial agent coatings can be applied to a variety of different types of substrates including medical implants such as vascular grafts, orthopedic devices, dialysis access grafts, and catheters; surgical tools, surgical garments; and bandages. The substrates can be composed of metallic materials, ceramics, polymers, fibers, inert materials such as silicon, and combinations thereof. The compositions described herein are substantially non-leaching, resistant to non-specific protein adsorption, and non-hemolytic.
Owner:ARROW INT INC
N-way serial-channel interconnect
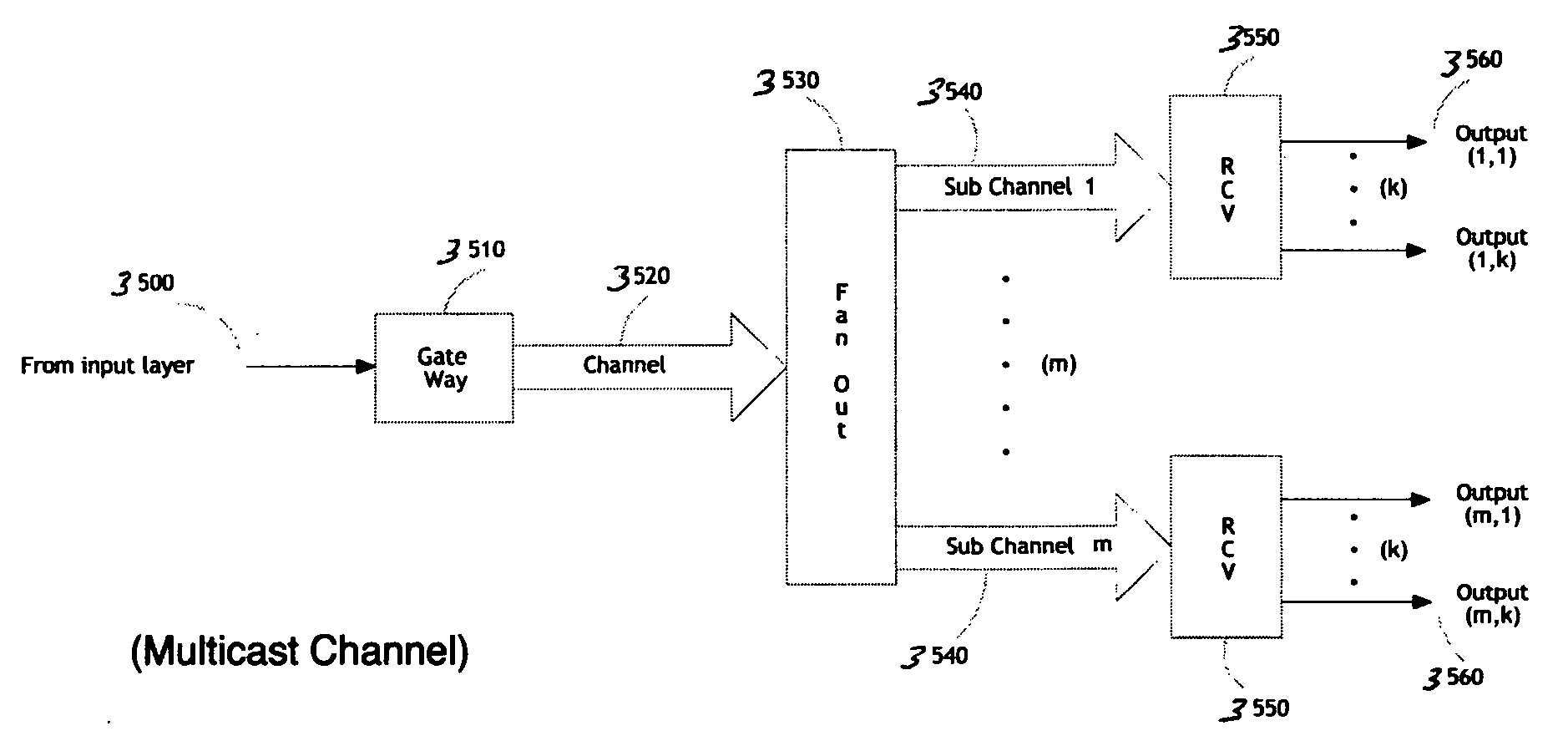
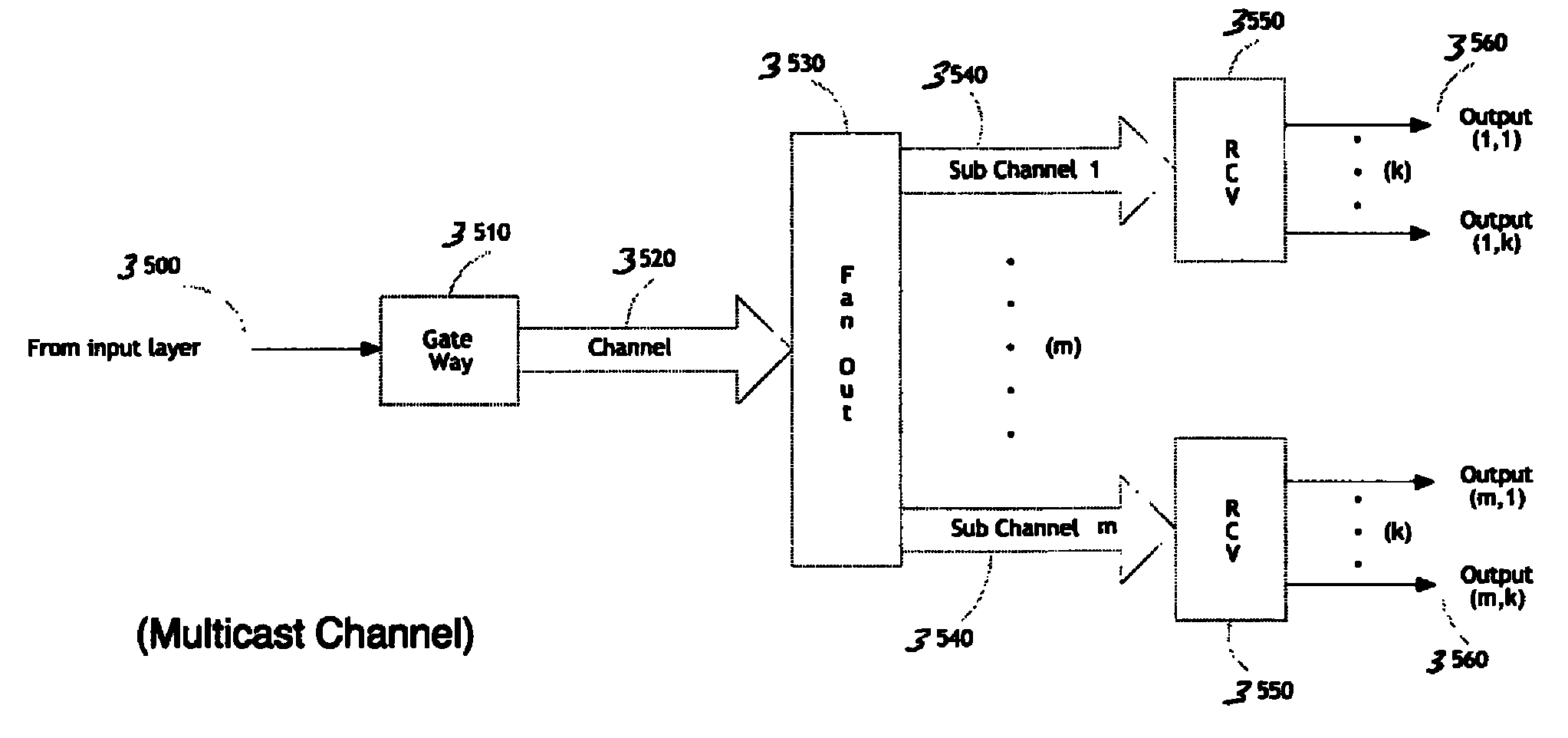
Methods and apparatus are described for an n-Way, Serial-Channel interconnect. An apparatus includes a communications network interconnect including an input layer including a plurality of input channels; a multicast channel branching fabric coupled to the input layer; and a modular output layer coupled to the multicast channel branching fabric layer, the modular output layer including a plurality of individual serial data channels; and a plurality of sets of endpoints, each set of endpoints coupled to one of the plurality of individual serial data channels.
Owner:LIGHTFLEET CORP
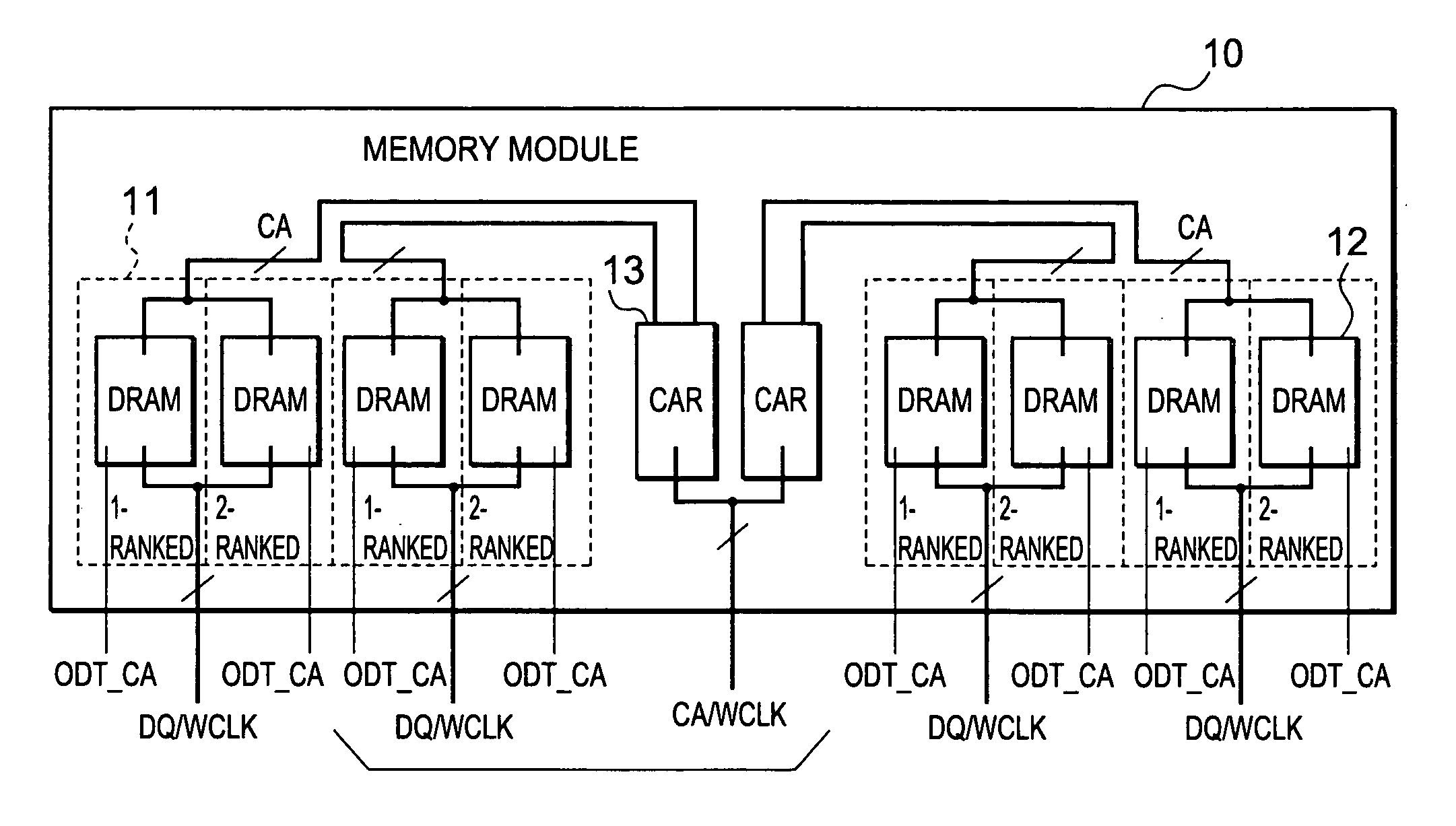
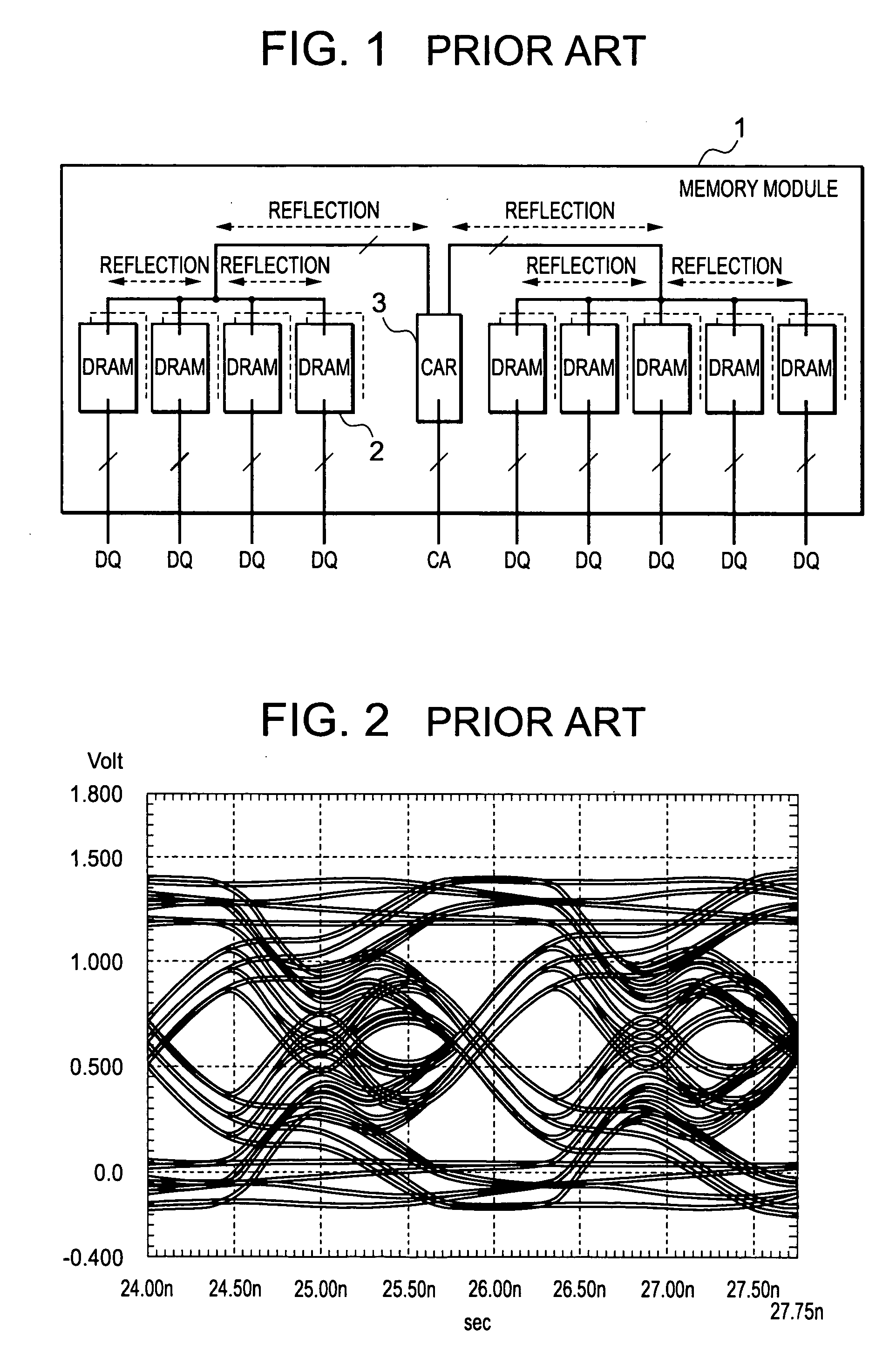
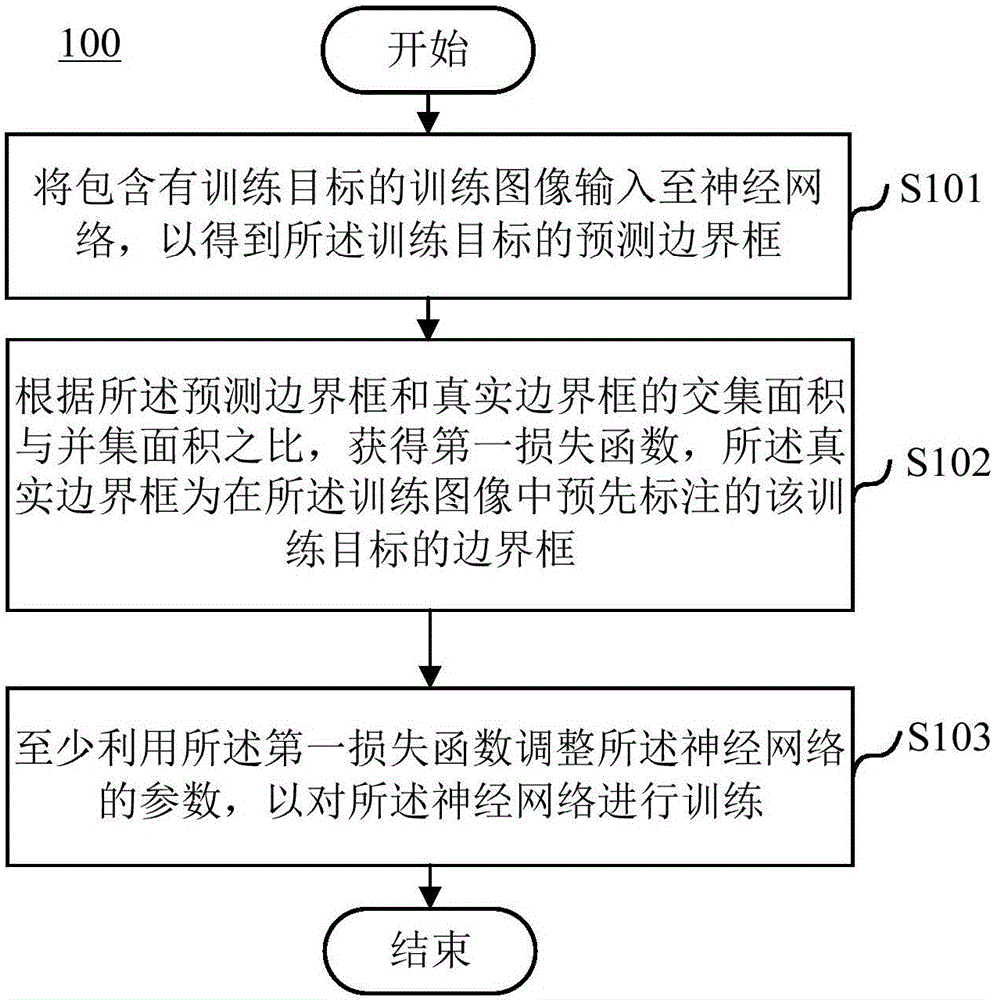
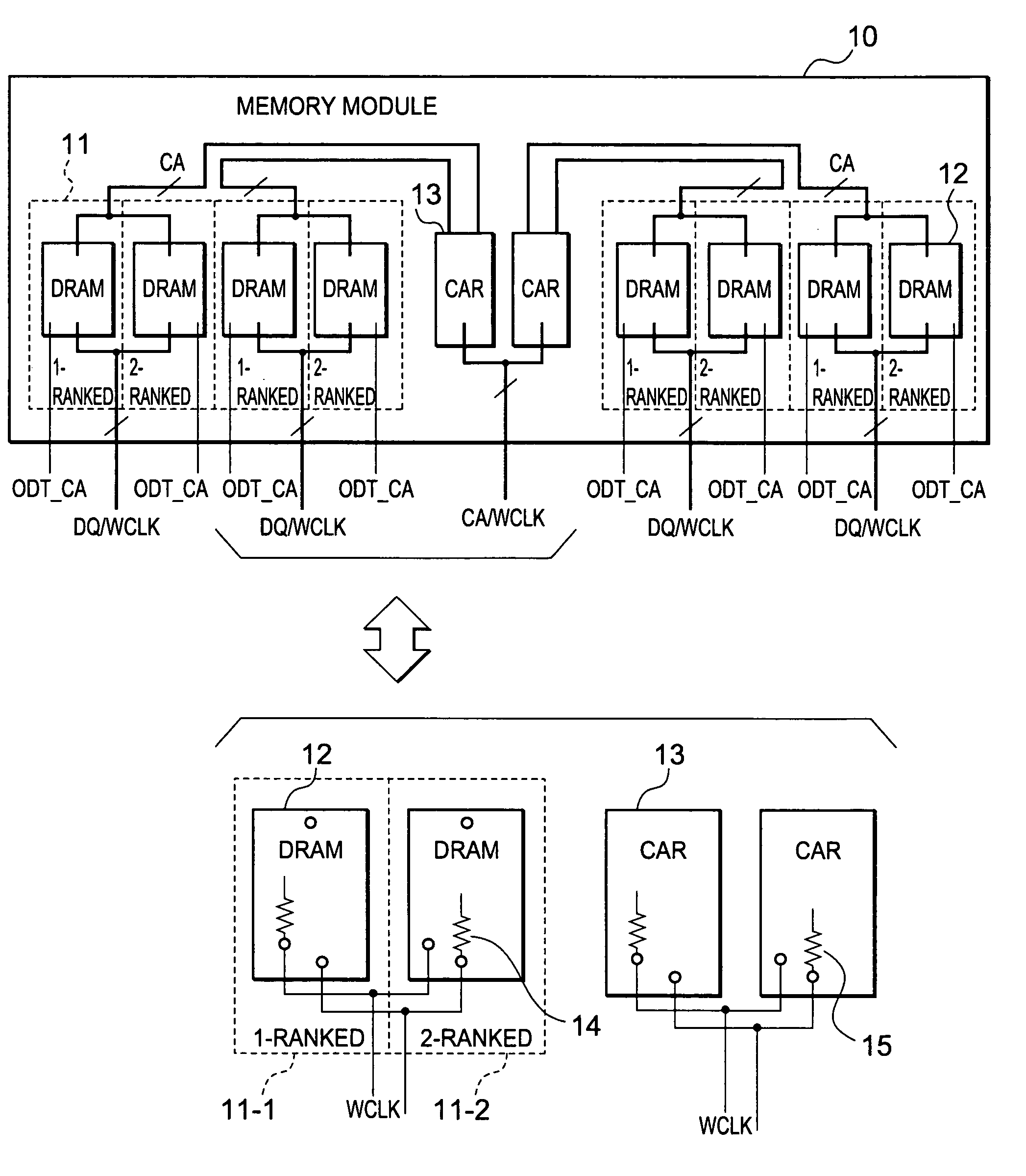
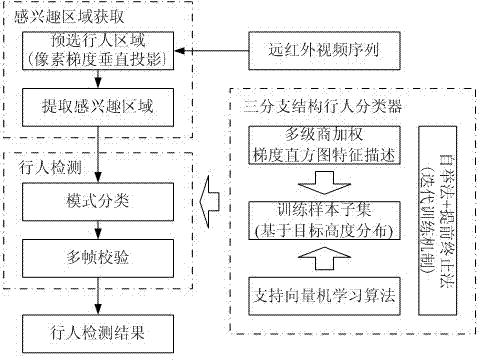
Memory module, memory chip, and memory system
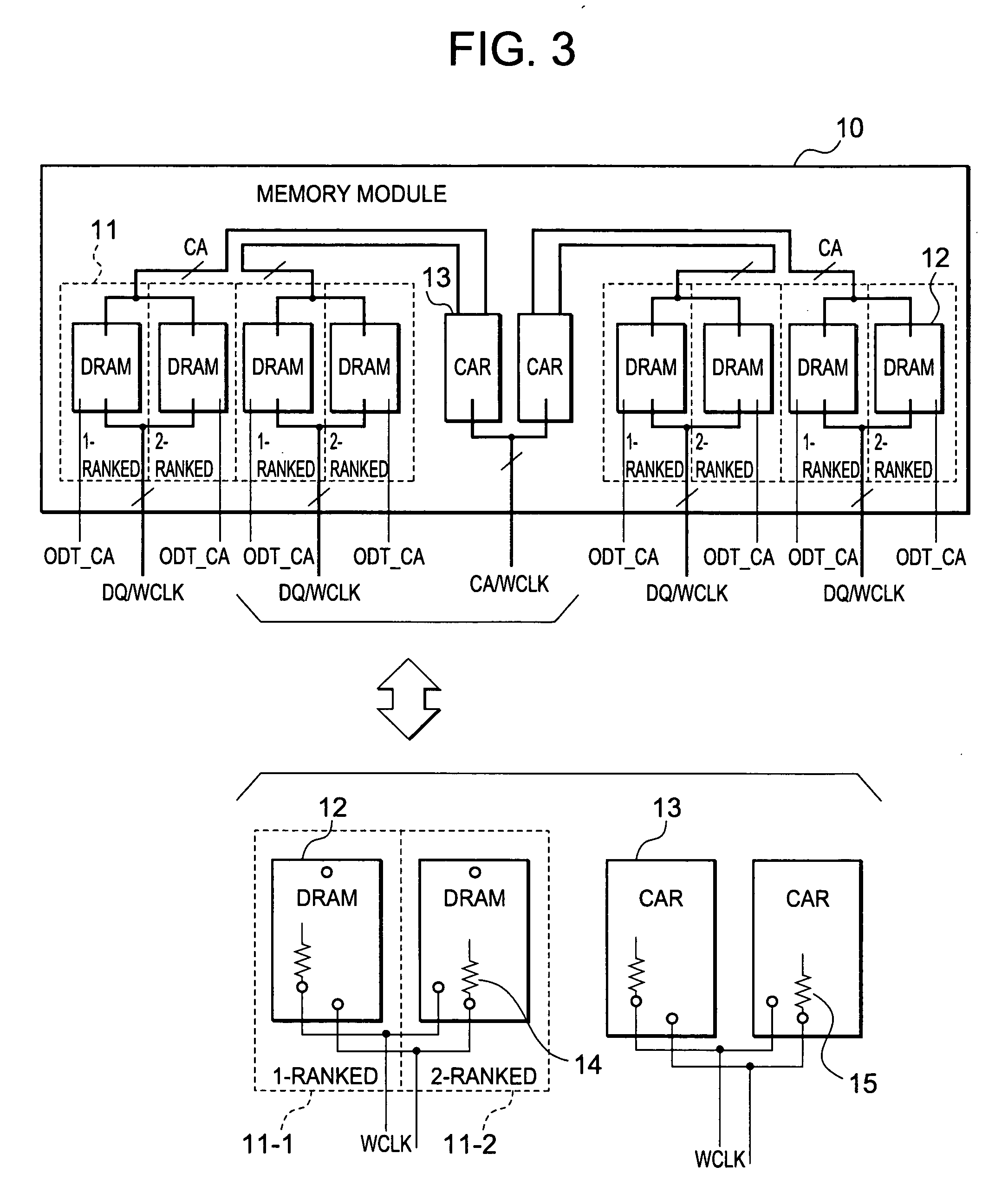
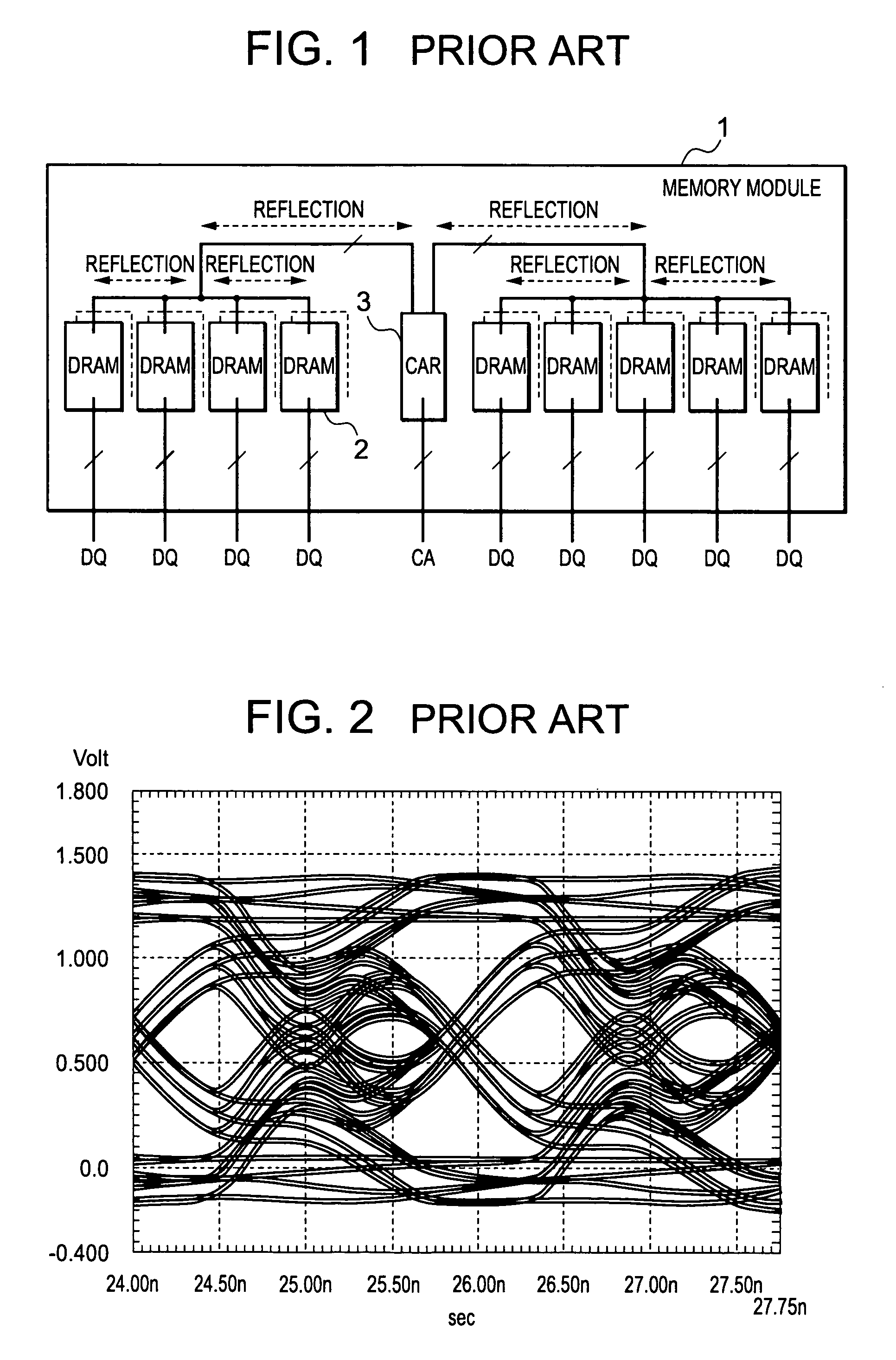
InactiveUS20050105318A1Reduce waveform distortionMemory capability with reliabilityMemory adressing/allocation/relocationDigital storageMemory chipParallel computing
A memory module includes at least one CAR and a plurality of DRAMs provided so as to be close and adjacent to one another on one face and the other face of a module substrate. The DRAMs are divided into a plurality of memory groups. Memory groups adjacent to each other of these memory groups are paired with each other. One of this pair is a 1-ranked memory group and the other is a 2-ranked memory group. This pair of the memory groups is connected to the CAR via short wiring with a T-branch structure having a short stub. One of the pair of the memory groups on the signal-reception side functions as an open end. Active termination is performed by a termination resistor of the other of the pair of the memory groups on the signal-non-reception side. Subsequently, signal reflections can be reduced.
Owner:LONGITUDE SEMICON S A R L
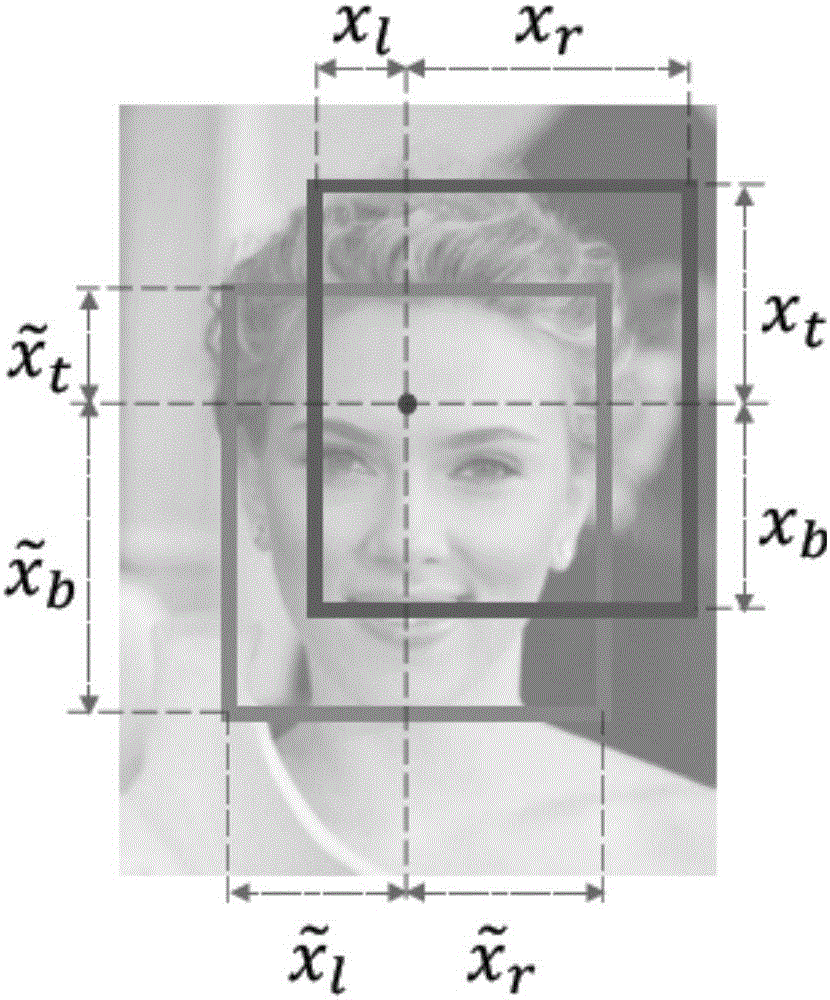
Neural network training and construction method and device, and object detection method and device
ActiveCN106295678AChange sizePrecise and effective target betting resultsImage enhancementImage analysisMachine learningObject detection
The embodiment of the invention provides a neural network training and construction method and device for object detection, and an object detection method and device based on a neural network. The neural network training and construction method for object detection comprises the steps: inputting a training image comprising a training object into the neural network, so as to obtain a prediction boundary frame of the training object; obtaining a first loss function according to the ratio of the intersection area and union area of the prediction boundary frame and a real boundary frame, wherein the real boundary frame is the boundary frame of the training object marked in the training image in advance; and adjusting the parameters of the neural network at least through the first loss function, so as to carry out the training of the neural network. According to the invention, the first loss function is employed for the regression of a target boundary frame into an integrated unit, and the object detection precision of the neural network is remarkably improved. Moreover, the training and detection efficiency of the neural network can be effectively improved through two branch structures of the neural network.
Owner:BEIJING KUANGSHI TECH +1
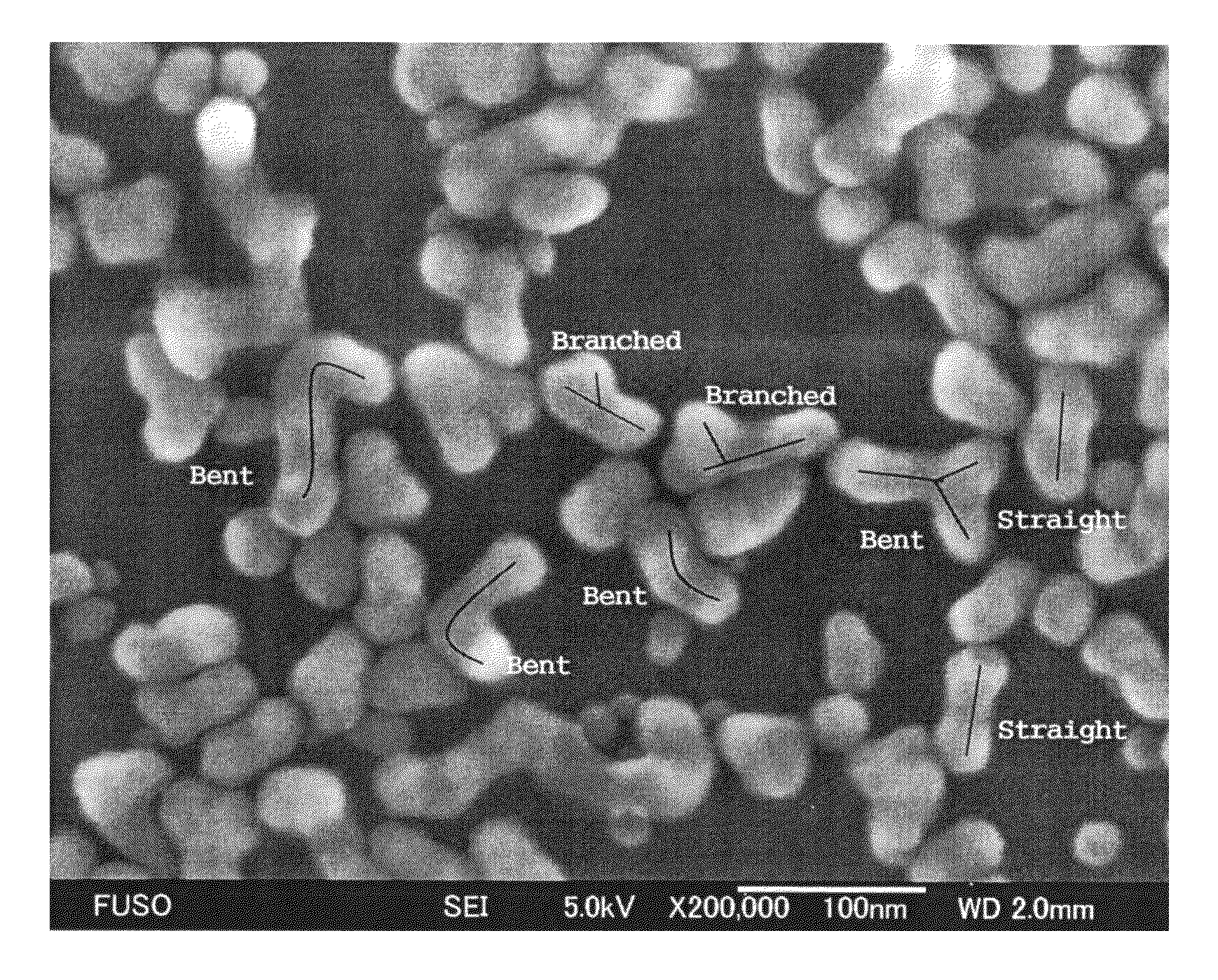
Colloidal silica containing silica secondary particles having bent structure and/or branched structure, and method for producing same
ActiveUS8529787B2Improve polishing rateLarge aspect ratioSilicaOther chemical processesColloidal silicaColloid
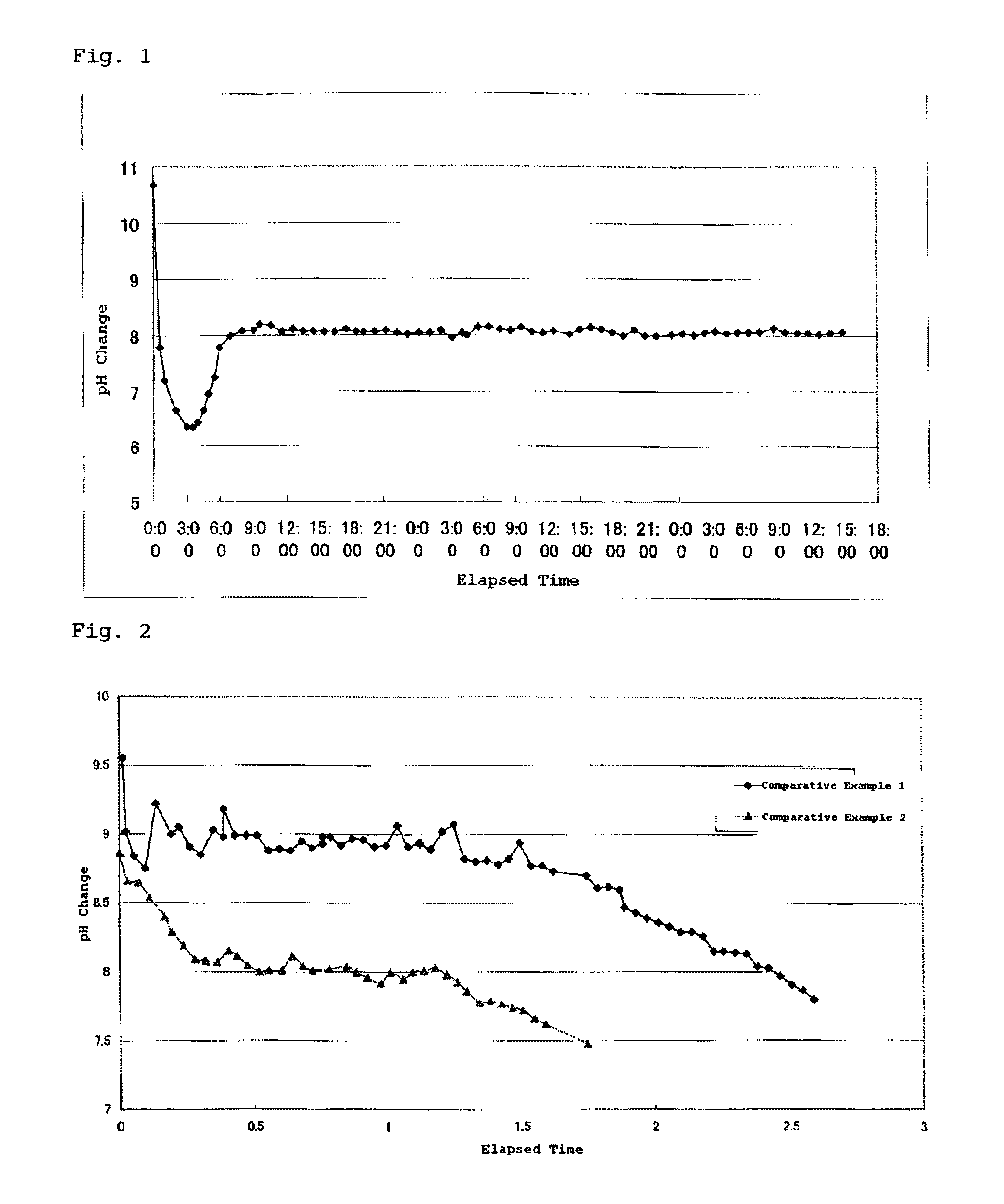
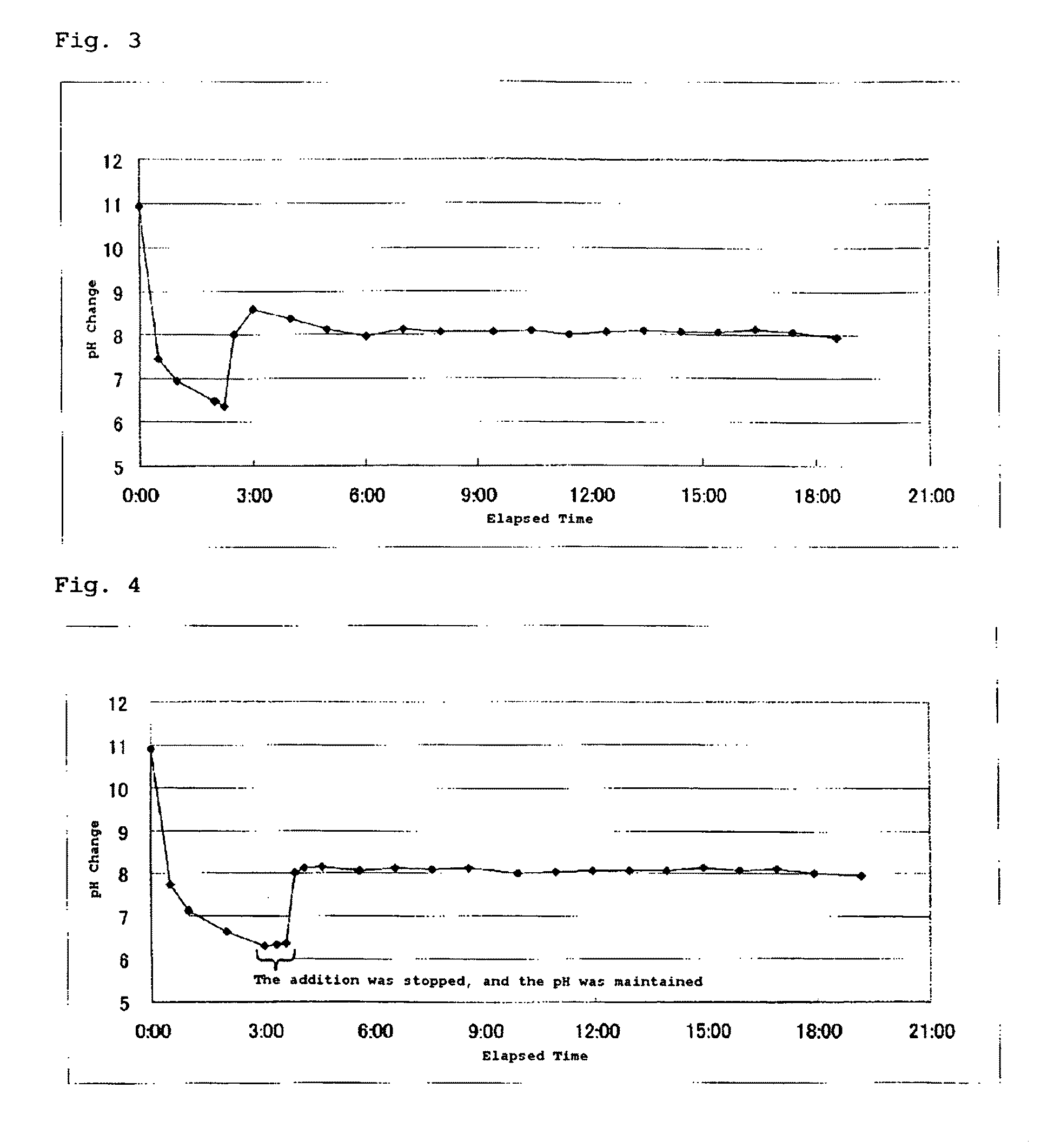
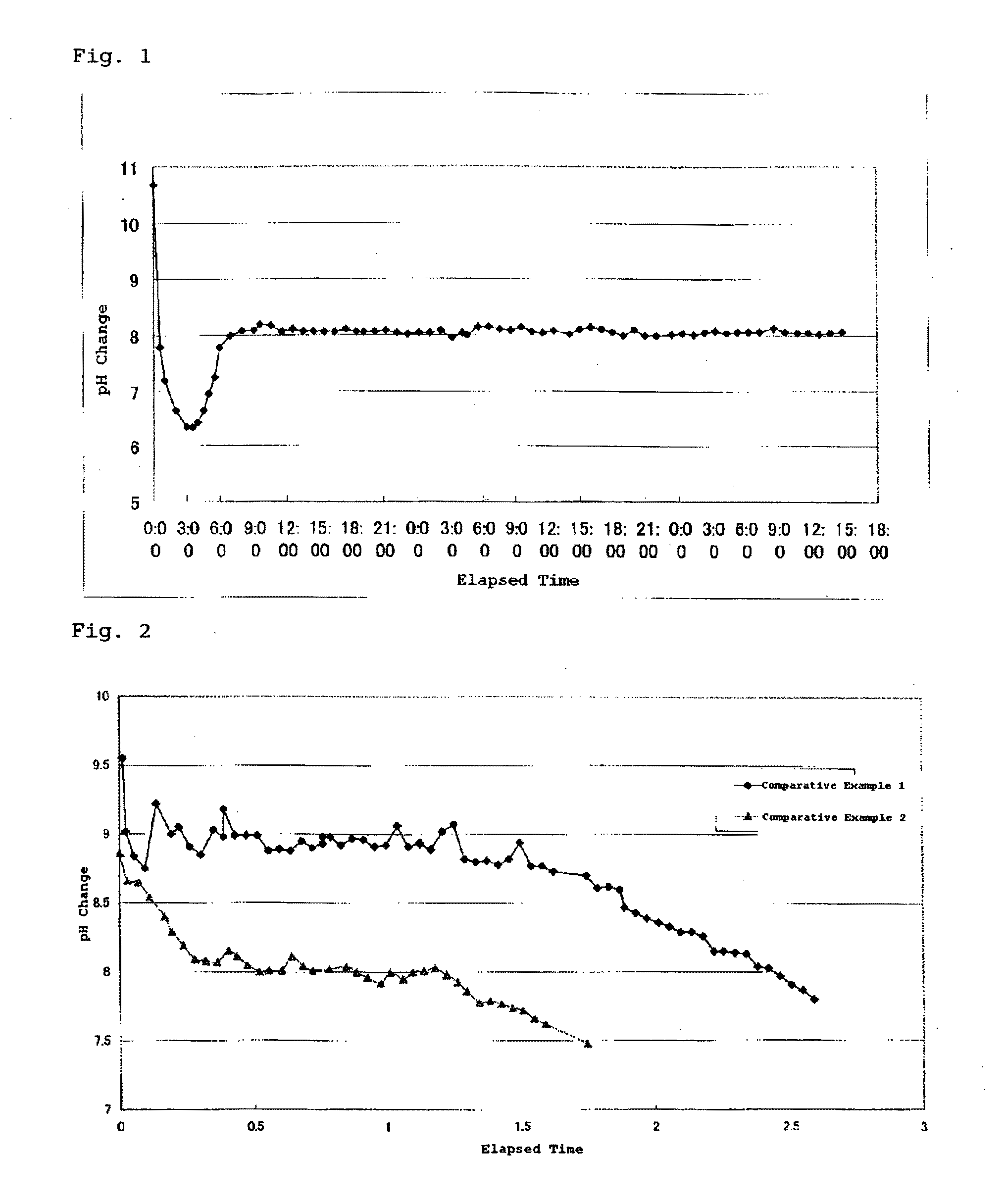
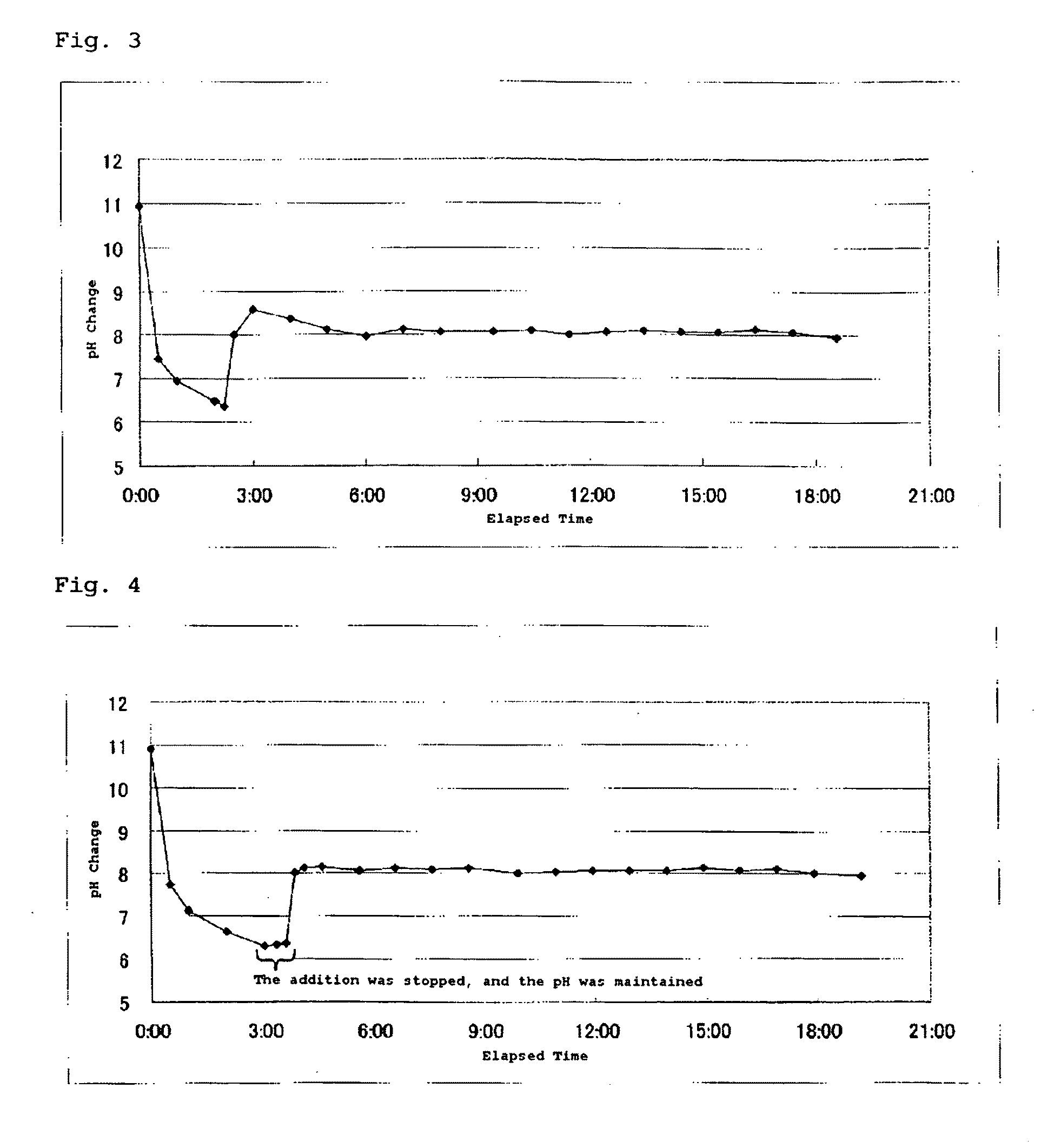
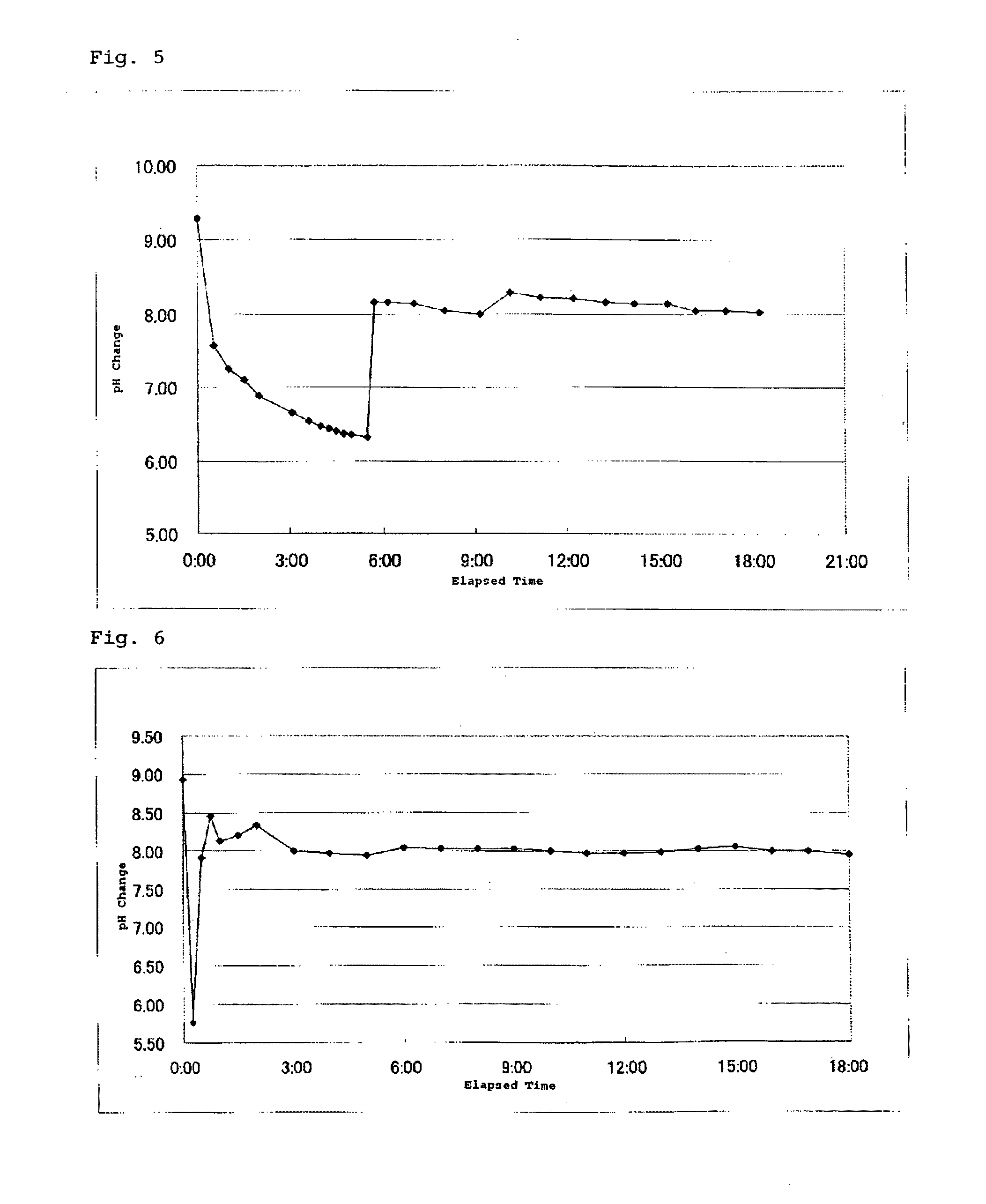
This invention provides a dense, high-purity colloidal silica containing silica secondary particles having a branched and / or bent structure, and a production method thereof. Specifically, this invention provides a method for producing a colloidal silica, comprising the steps of 1) preparing a mother liquid containing an alkali catalyst and water, and having a pH of 9 to 12; and 2) adding a hydrolysis liquid obtained by hydrolysis of an alkyl silicate to the mother liquid, wherein the step of adding the hydrolysis liquid to the mother liquid sequentially comprises A) step 1 of adding the hydrolysis liquid until the pH of the resulting liquid mixture becomes less than 7; B) step 2 of adding an aqueous alkali solution until the pH of the liquid mixture becomes 7 or more; and C) step 3 of adding the hydrolysis liquid while maintaining the pH of the liquid mixture at 7 or more, and a colloidal silica containing silica secondary particles having a branched and / or bent structure, obtained by this method.
Owner:FUSO CHEM
Four freedom parallel robot mechanism with passive bound branch
InactiveCN1644312ADoes not affect the nature of movementStructural symmetryProgramme-controlled manipulatorLarge fixed membersDegrees of freedomControl theory
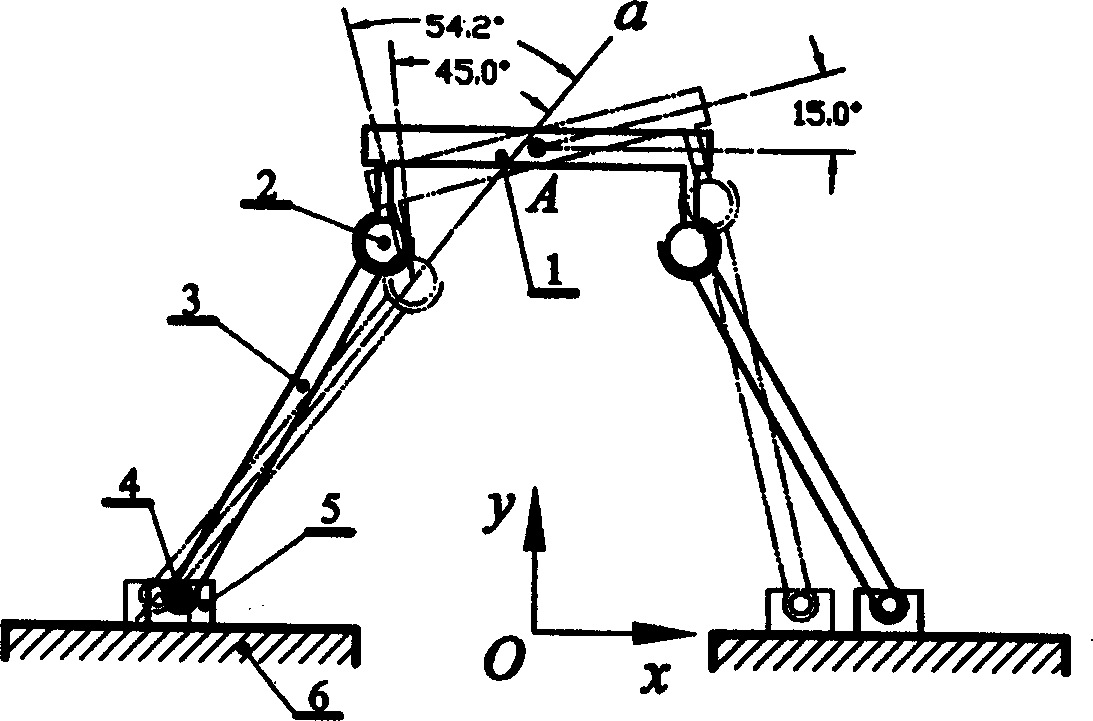
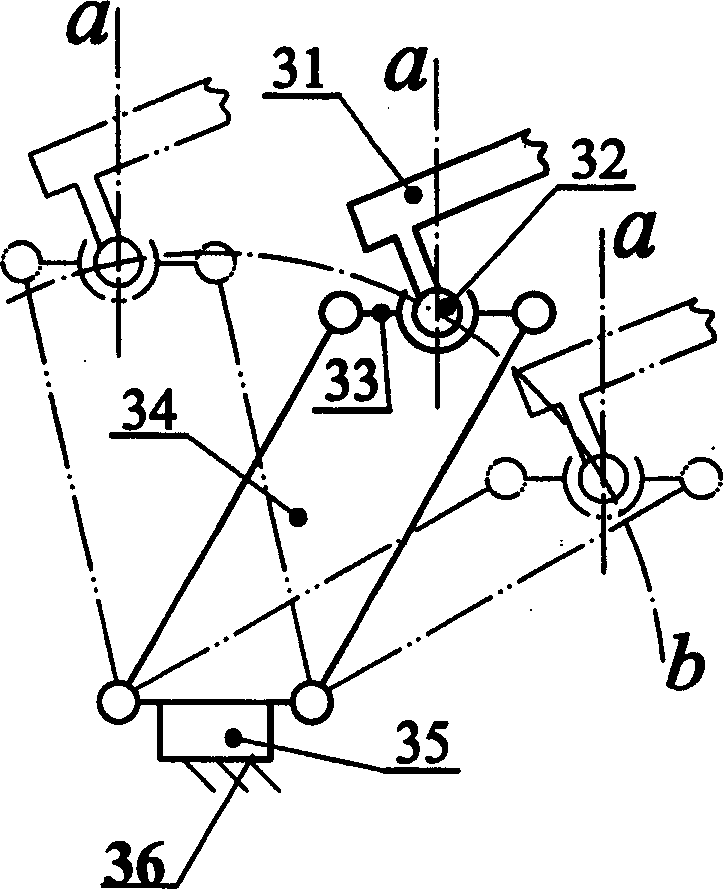
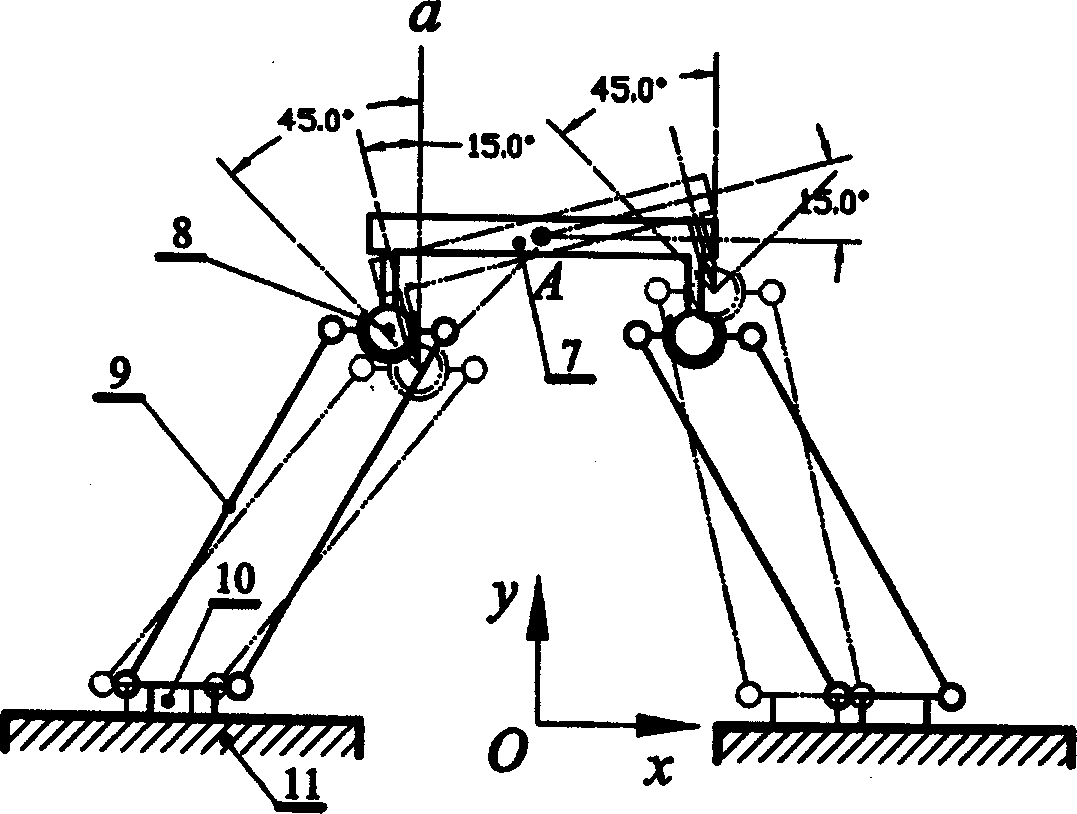
A 4-freedom parallel robot structure with passive constraint branch is disclosed, which contains different two passive constraint branch structures and can be used for robot to realize one axial movement and three different rotations. Its advantages are high parallel rigidity and load-bearing power, simple structure, high precision and low cost.
Owner:YANSHAN UNIV
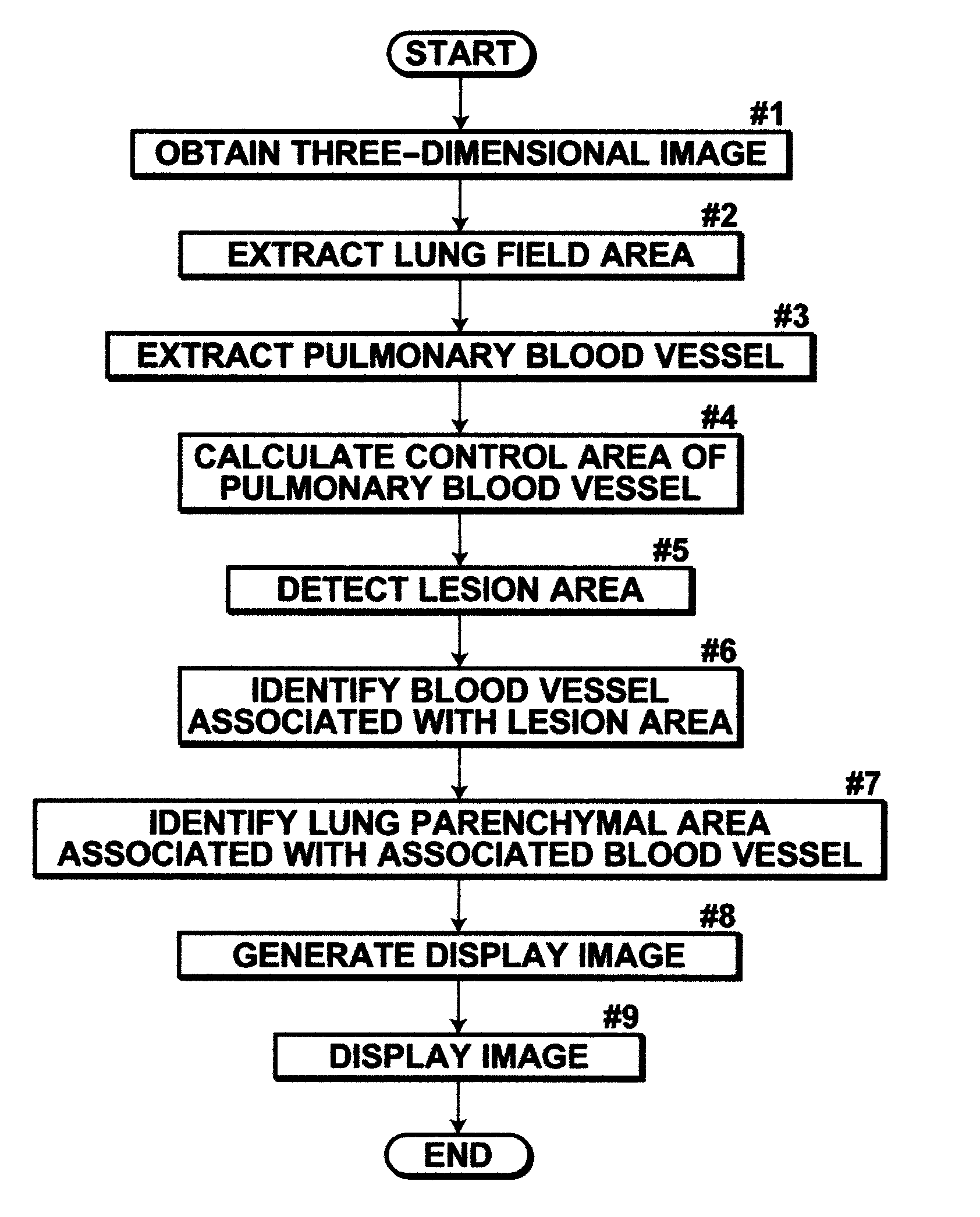
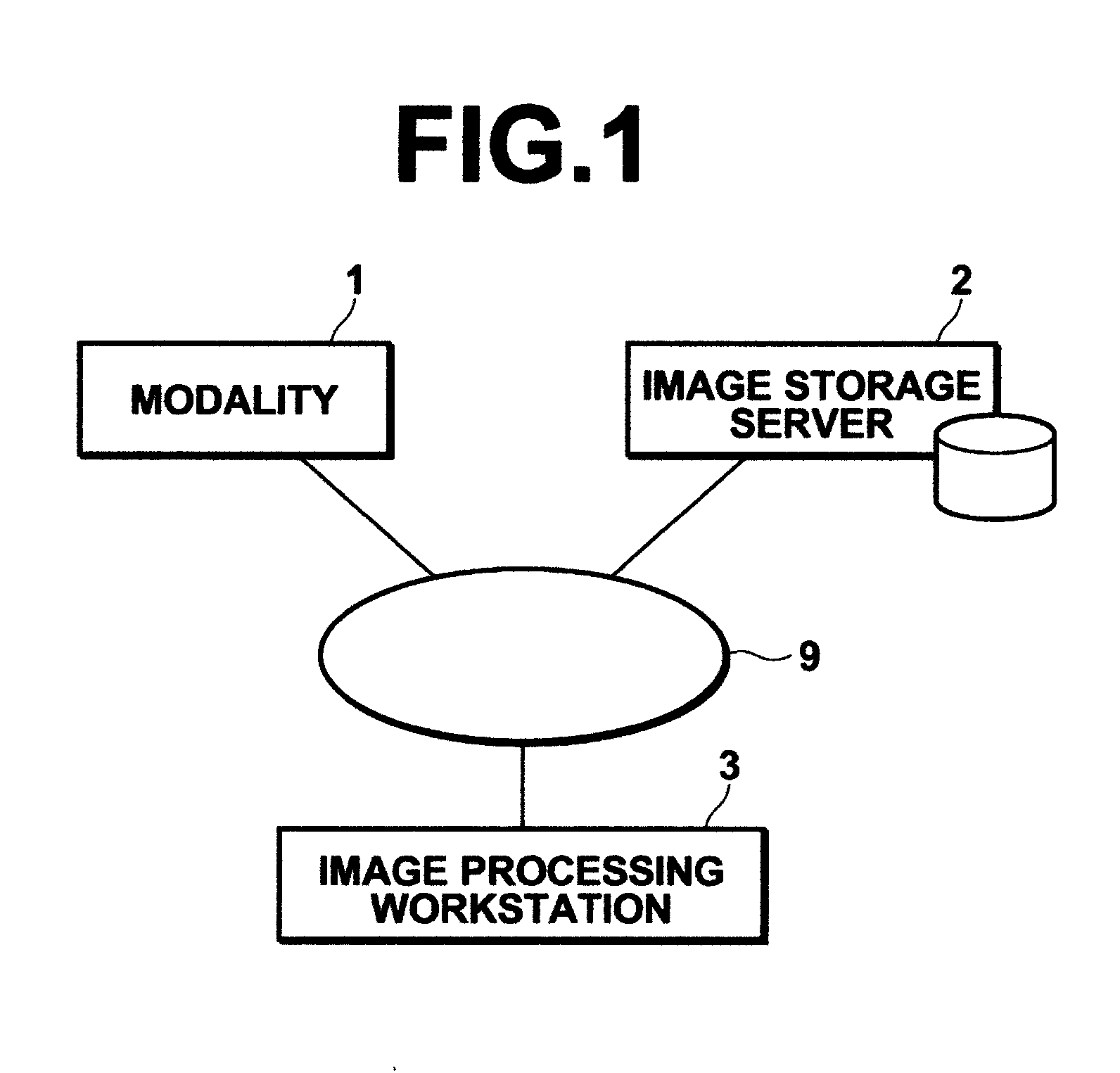
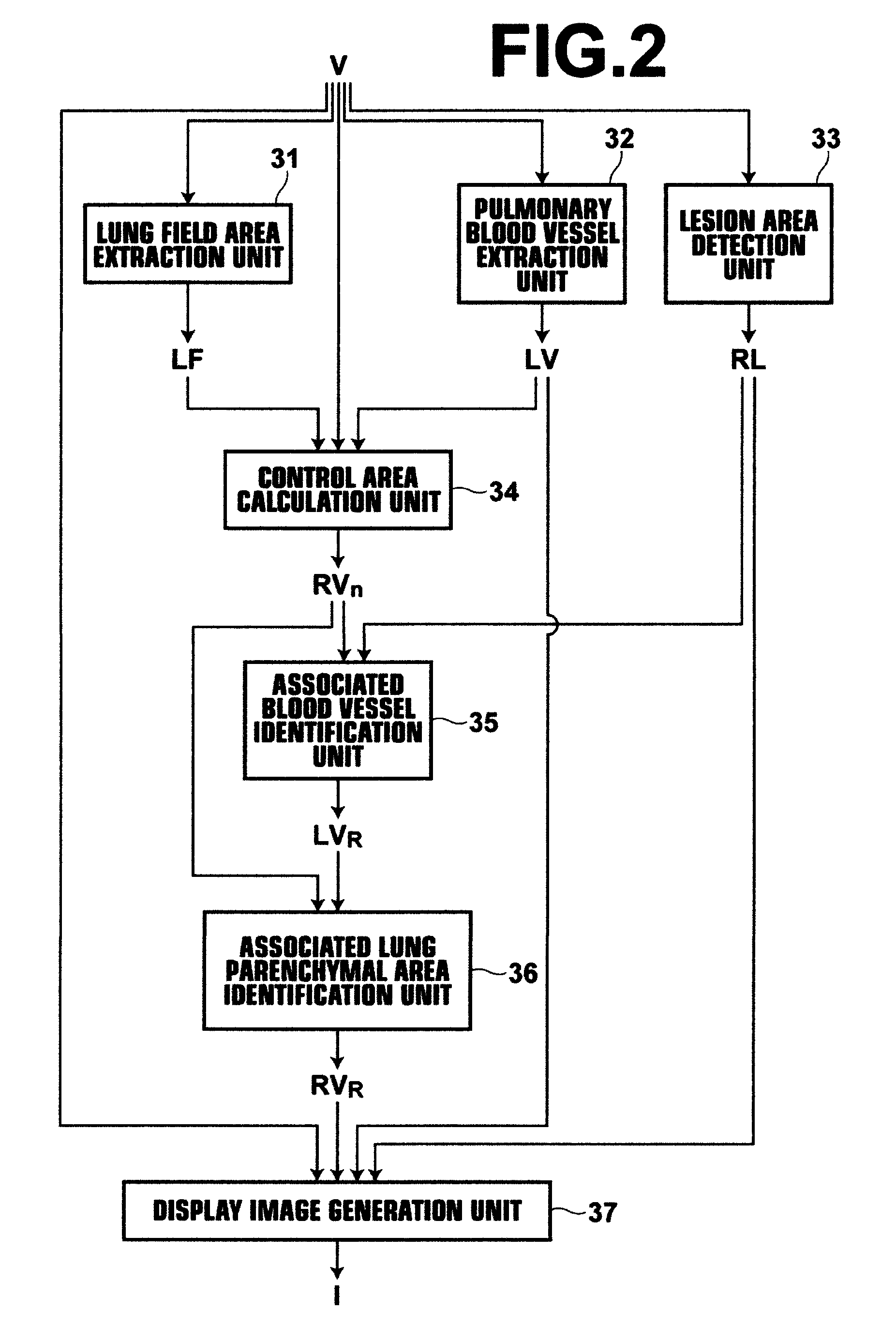
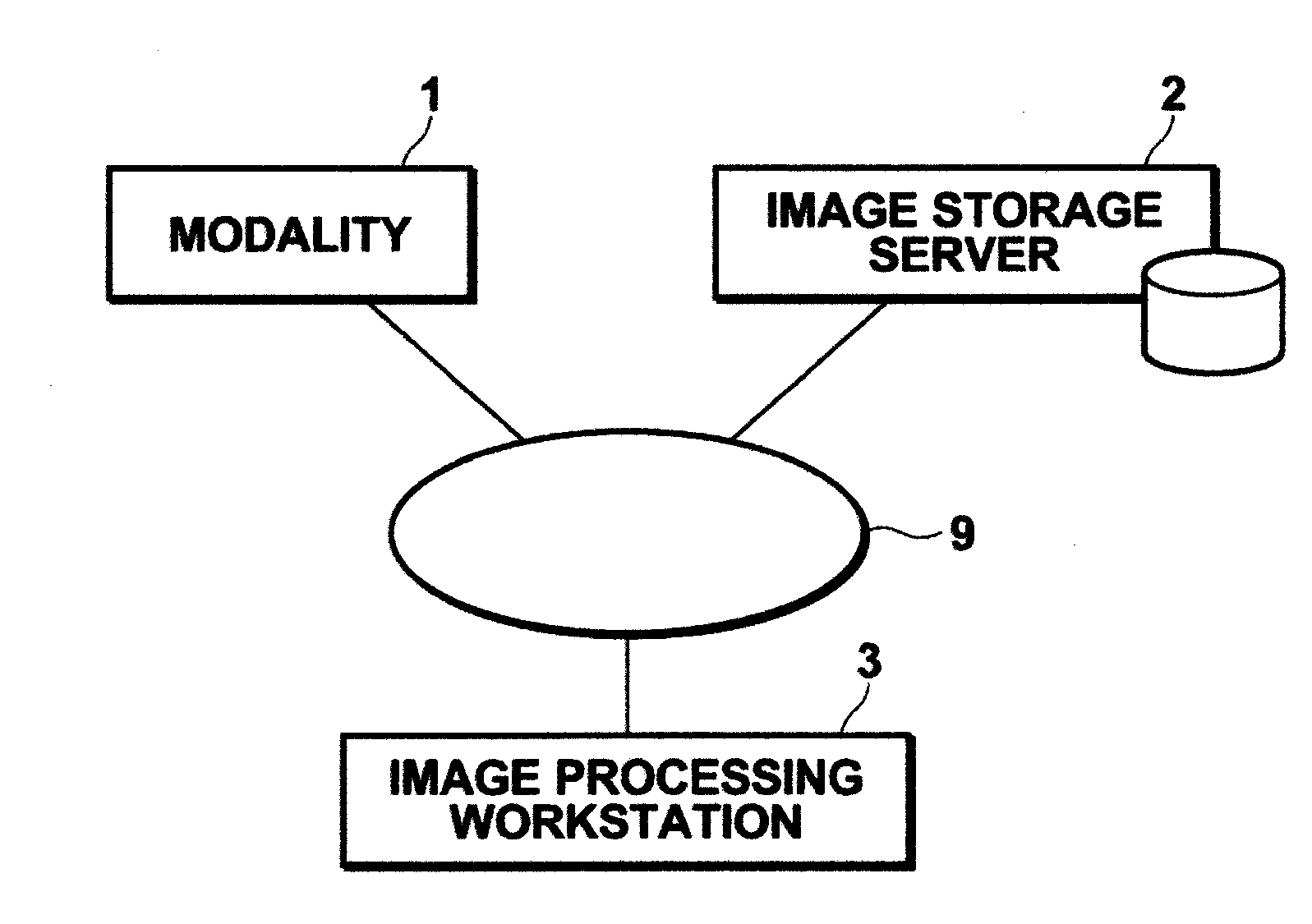
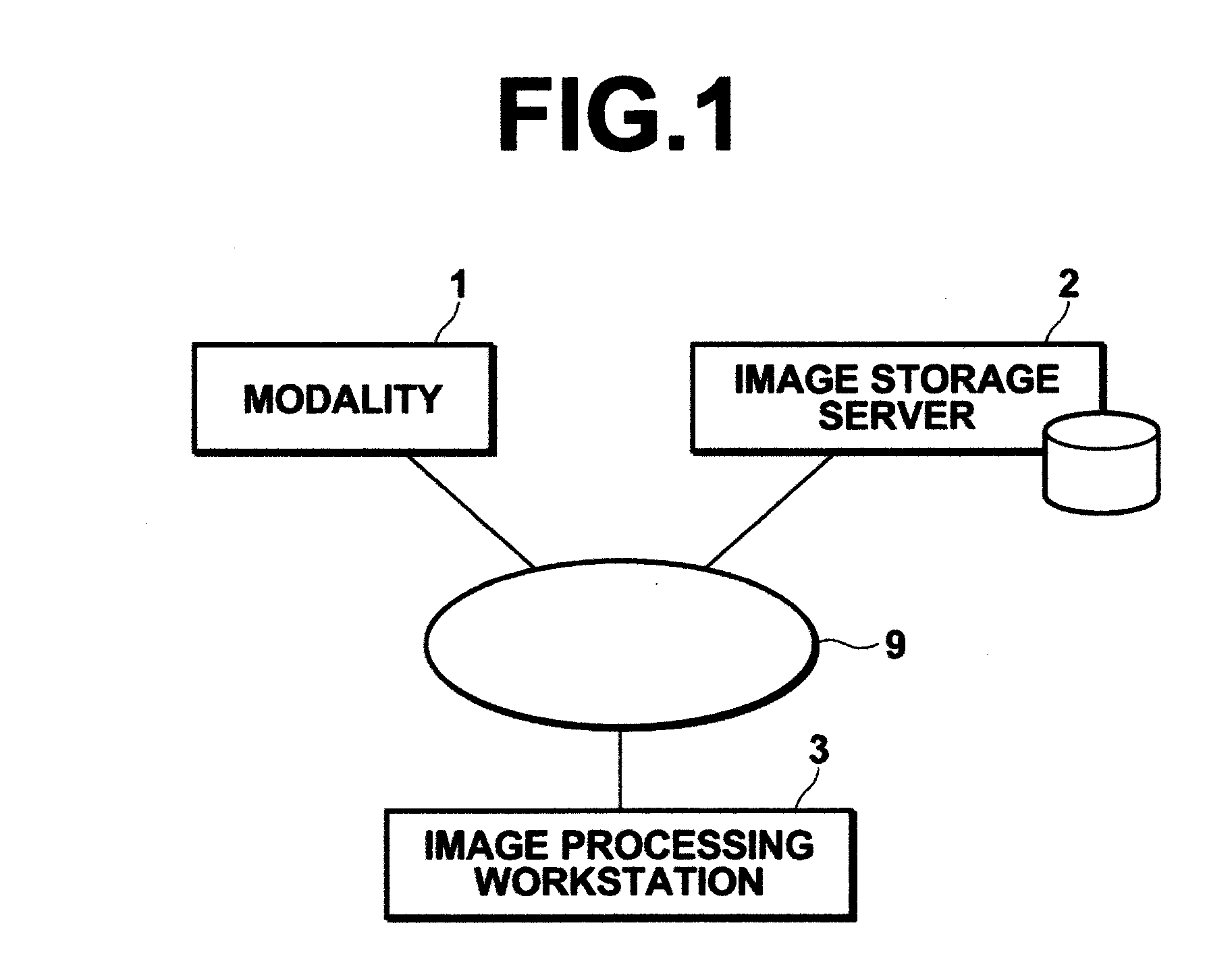
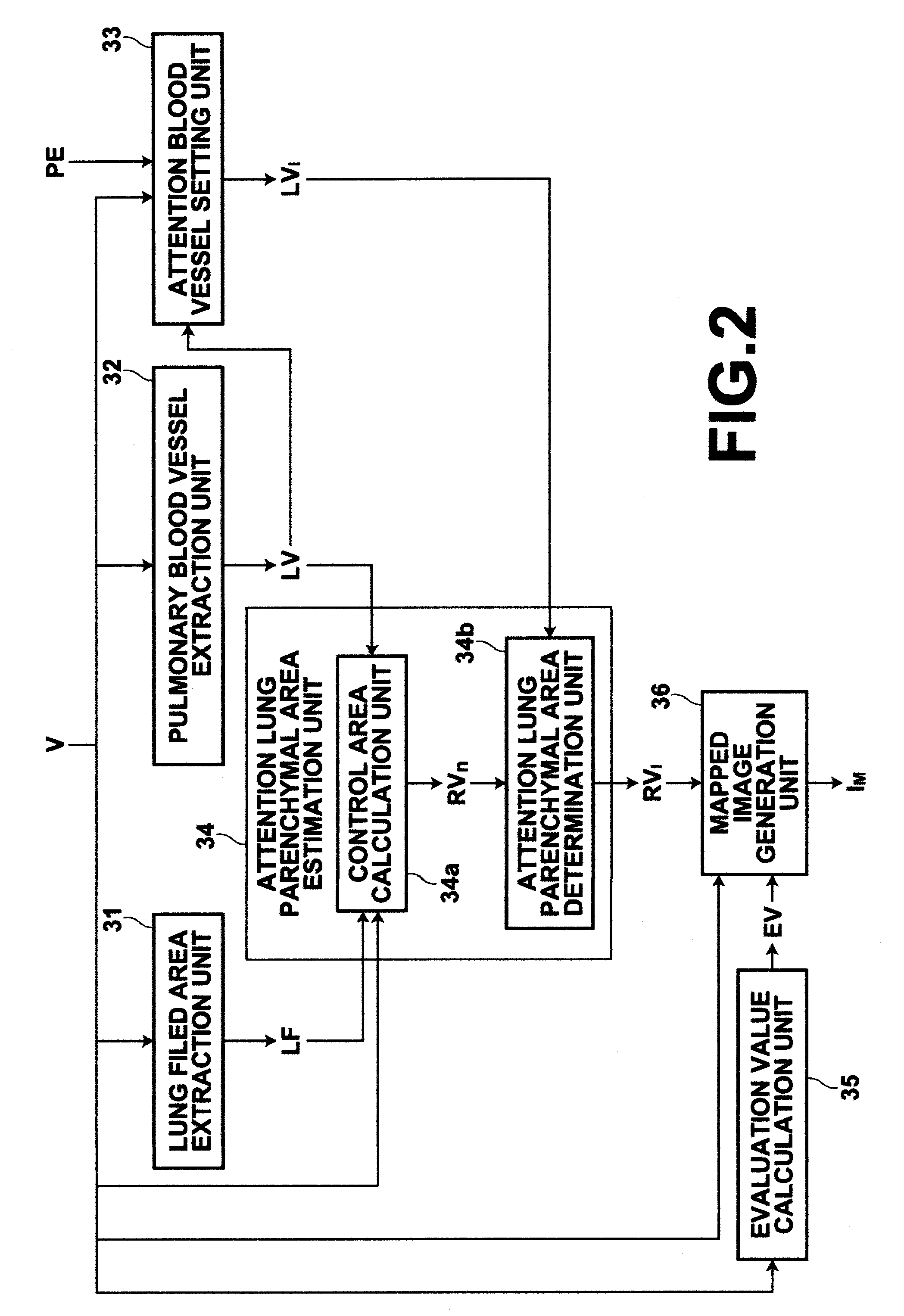
Apparatus, method, and computer readable medium for assisting medical image diagnosis using 3-D images representing internal structure
A lesion area detection unit detects an abnormal peripheral structure (lesion area), a pulmonary blood vessel extraction unit extracts a branch structure (pulmonary blood vessel) from the three-dimensional medical image, an associated blood vessel identification unit identifies an associated branch structure functionally associated with the abnormal peripheral structure based on position information of each point in the extracted branch structure, and an associated lung parenchymal area identification unit identifies an associated peripheral area (lung parenchyma) functionally associated with the identified associated branch structure based on the position information of each point in the extracted branch structure.
Owner:FUJIFILM CORP
Heat-meltable fluororesin fibers
InactiveUS6479143B1Intermingling property can be enhancedEasy to produceSynthetic resin layered productsNon-woven fabricsFiberHot melt
To provide the heat-meltable fluorine-containing resin fiber having excellent intermingling property and various materials for fiber products obtained therefrom. The heat-meltable fluorine-containing resin such as ETFE having a branched structure is used solely or mixed to other fiber such as an electrically conductive fiber to be formed into a non-woven fabric.
Owner:DAIKIN IND LTD
N-way serial-channel interconnect
Owner:LIGHTFLEET CORP
A multi-modal motion recognition method based on depth neural network
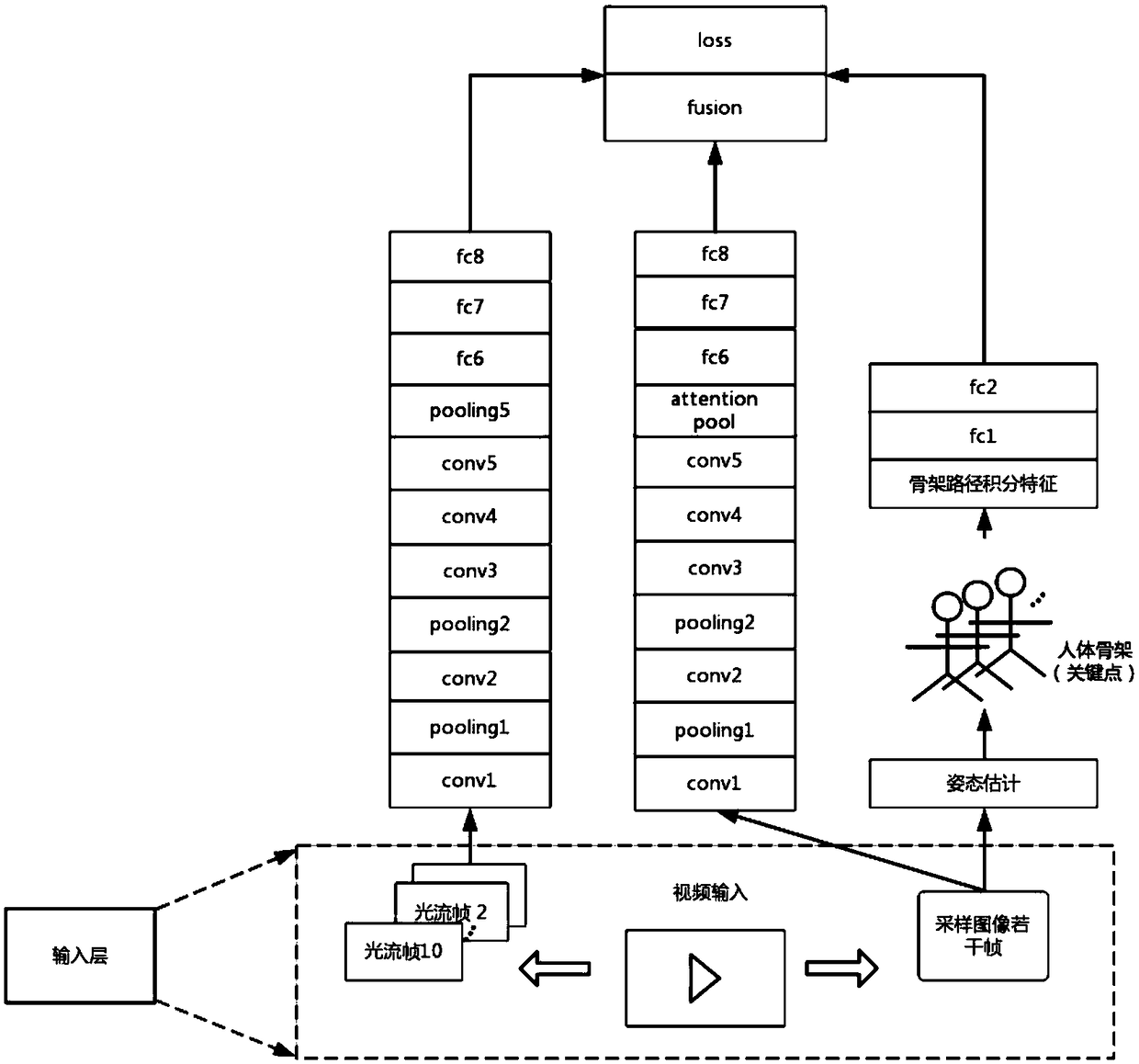
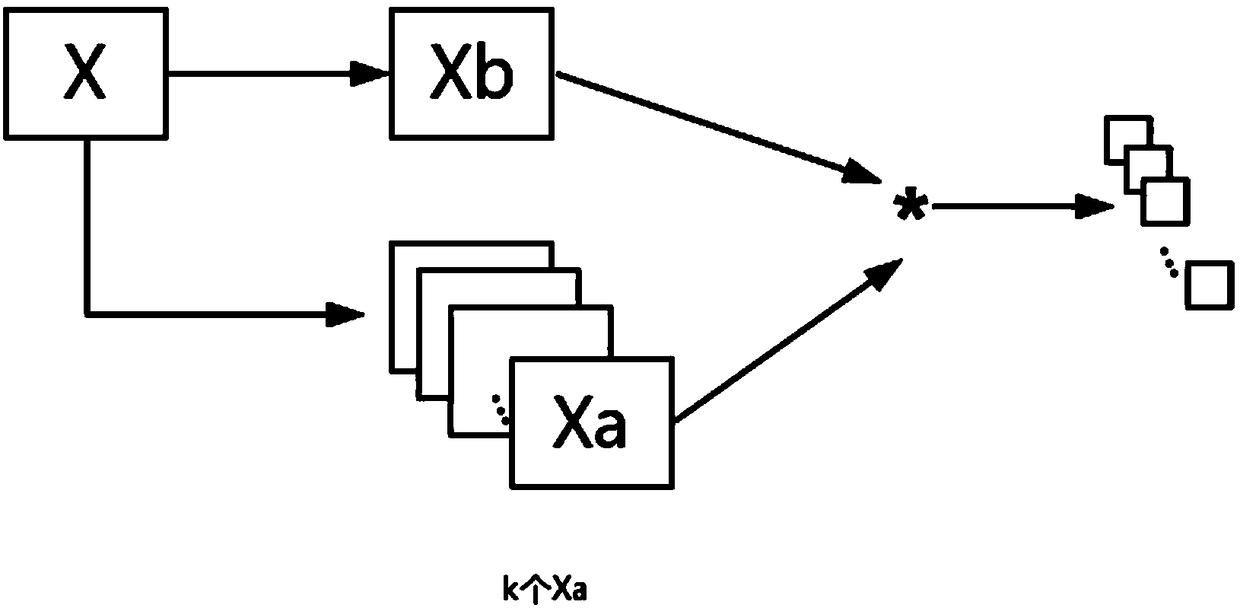
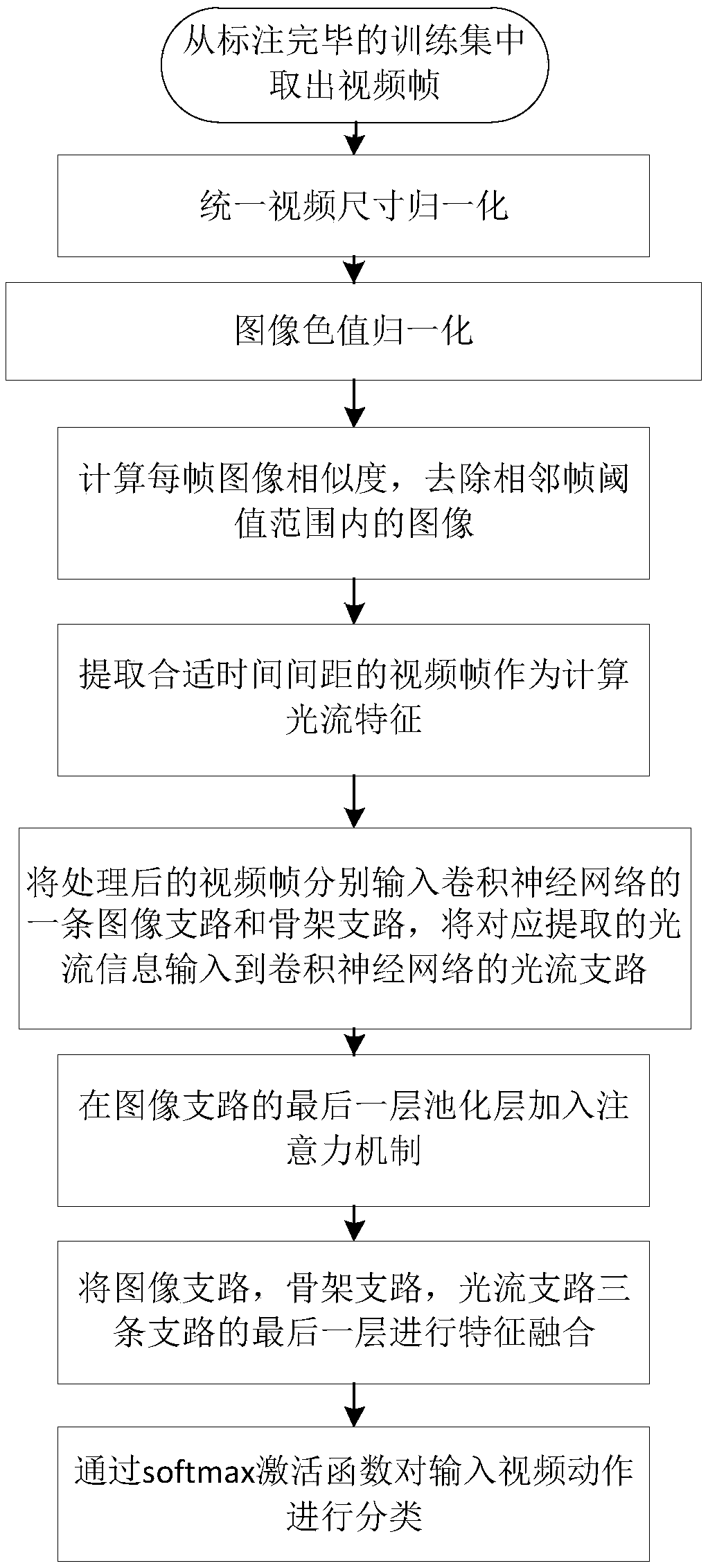
InactiveCN109460707AAchieve fine characterizationSmall amount of calculationCharacter and pattern recognitionNeural architecturesOptical flowHuman skeleton
The invention discloses a multi-modal action recognition method based on a depth neural network. The method comprehensively utilizes multi-modal information such as video images, optical flow diagramsand human skeleton. The specific steps are as follows: firstly, a series of preprocessing and compression are performed on the video; Obtaining an optical flow graph based on adjacent frames of the video; The human skeleton is obtained from the video frame by using the attitude estimation algorithm, and the path integral characteristics of the skeleton sequence are calculated. The obtained optical flow graph, skeleton path integration feature and original video image are input into a depth neural network with multi-branch structure to learn the abstract spatio-temporal representation of humanmotion and correctly judge its motion category. In addition, the pooling layer based on attention mechanism is connected to the video image branch, which enhances the abstract features closely related to the final motion classification results and reduces the irrelevant interference. The invention comprehensively utilizes multimodal information, and has the advantages of strong robustness and high recognition rate.
Owner:SOUTH CHINA UNIV OF TECH
Memory module, memory chip, and memory system
InactiveUS6937494B2Reduce distortionShorten the lengthMemory adressing/allocation/relocationDigital storageMemory chipParallel computing
A memory module includes at least one CAR and a plurality of DRAMs provided so as to be close and adjacent to one another on one face and the other face of a module substrate. The DRAMs are divided into a plurality of memory groups. Memory groups adjacent to each other of these memory groups are paired with each other. One of this pair is a 1-ranked memory group and the other is a 2-ranked memory group. This pair of the memory groups is connected to the CAR via short wiring with a T-branch structure having a short stub. One of the pair of the memory groups on the signal-reception side functions as an open end. Active termination is performed by a termination resistor of the other of the pair of the memory groups on the signal-non-reception side. Subsequently, signal reflections can be reduced.
Owner:LONGITUDE SEMICON S A R L
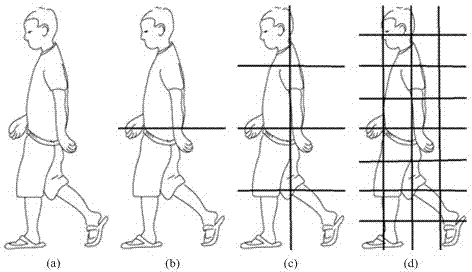
Real-time robust far infrared vehicle-mounted pedestrian detection method
InactiveCN103198332AExact searchDetailed descriptionCharacter and pattern recognitionVertical projectionFar infrared
The invention discloses a real-time robust far infrared vehicle-mounted pedestrian detection method. The method comprises the steps of catching a potential pedestrian pre-selection area in an input image through a pixel gradient vertical projection, searching an interest area in the pedestrian pre-selection area through a local threshold method and morphological post-processing techniques, extracting a multi-stage entropy weighing gradient direction histogram for feature description of the interest area, inputting the histogram to a support vector machine pedestrian classifier for online judgment of the interest area, achieving pedestrian detection through multi-frame verification and screening of judgment results of the pedestrian classifier, dividing training sample space according to sample height distribution, building a classification frame of a three-branch structure, and collecting difficult samples and a training pedestrian classifier in an iteration mode with combination of a bootstrap method and an advanced termination method. According to the real-time robust far infrared vehicle-mounted pedestrian detection method, not only is accuracy of pedestrian detection improved, but also a false alarm rate is reduced, input image processing speed and generalization capacity of the classifier are improved, and provided is an effective night vehicle-mounted pedestrian-assisted early warning method.
Owner:SOUTH CHINA UNIV OF TECH
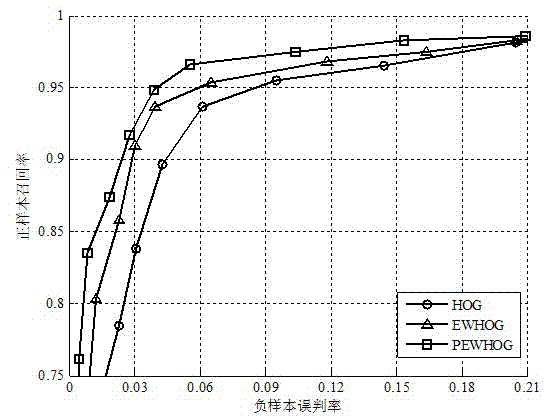
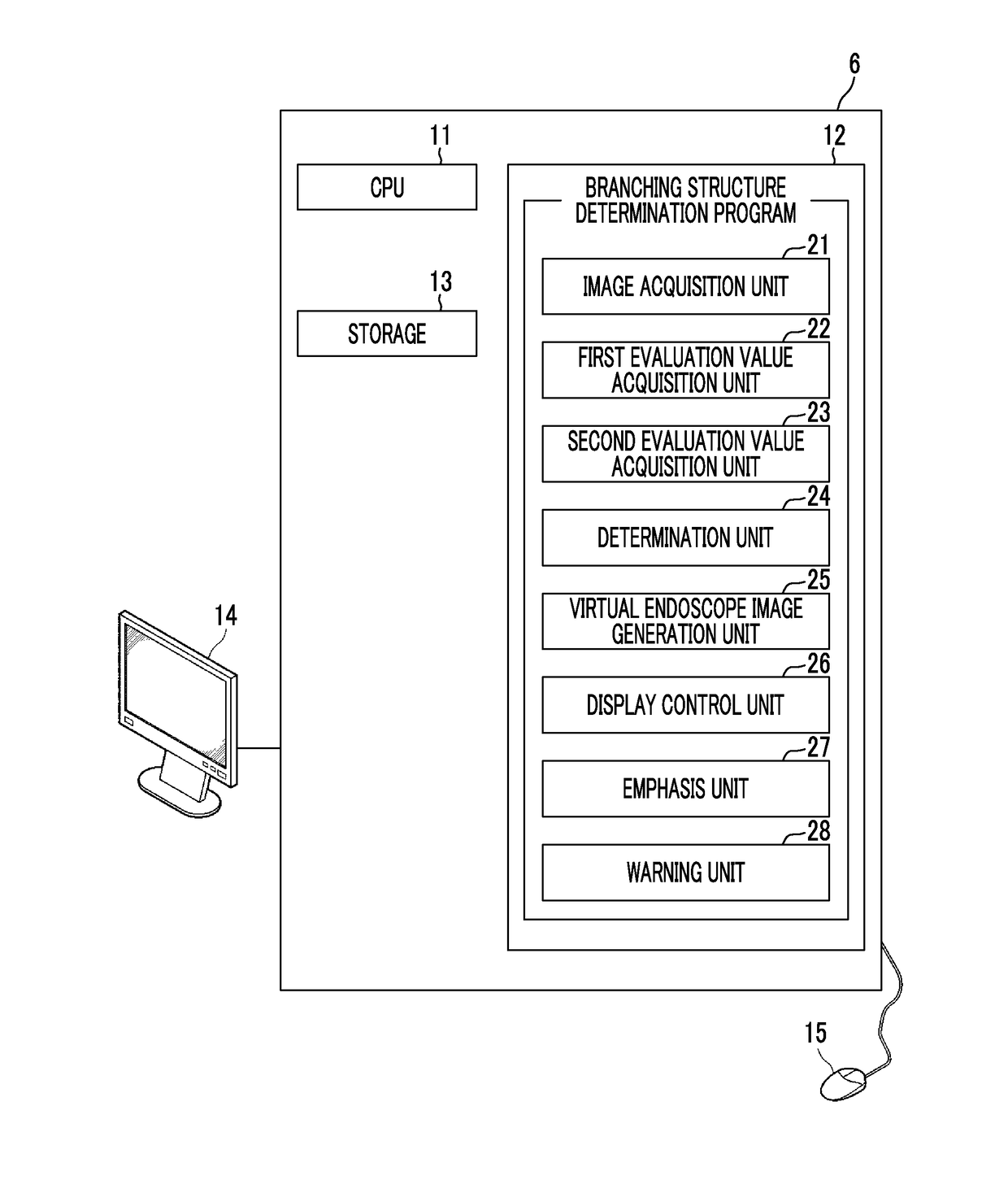
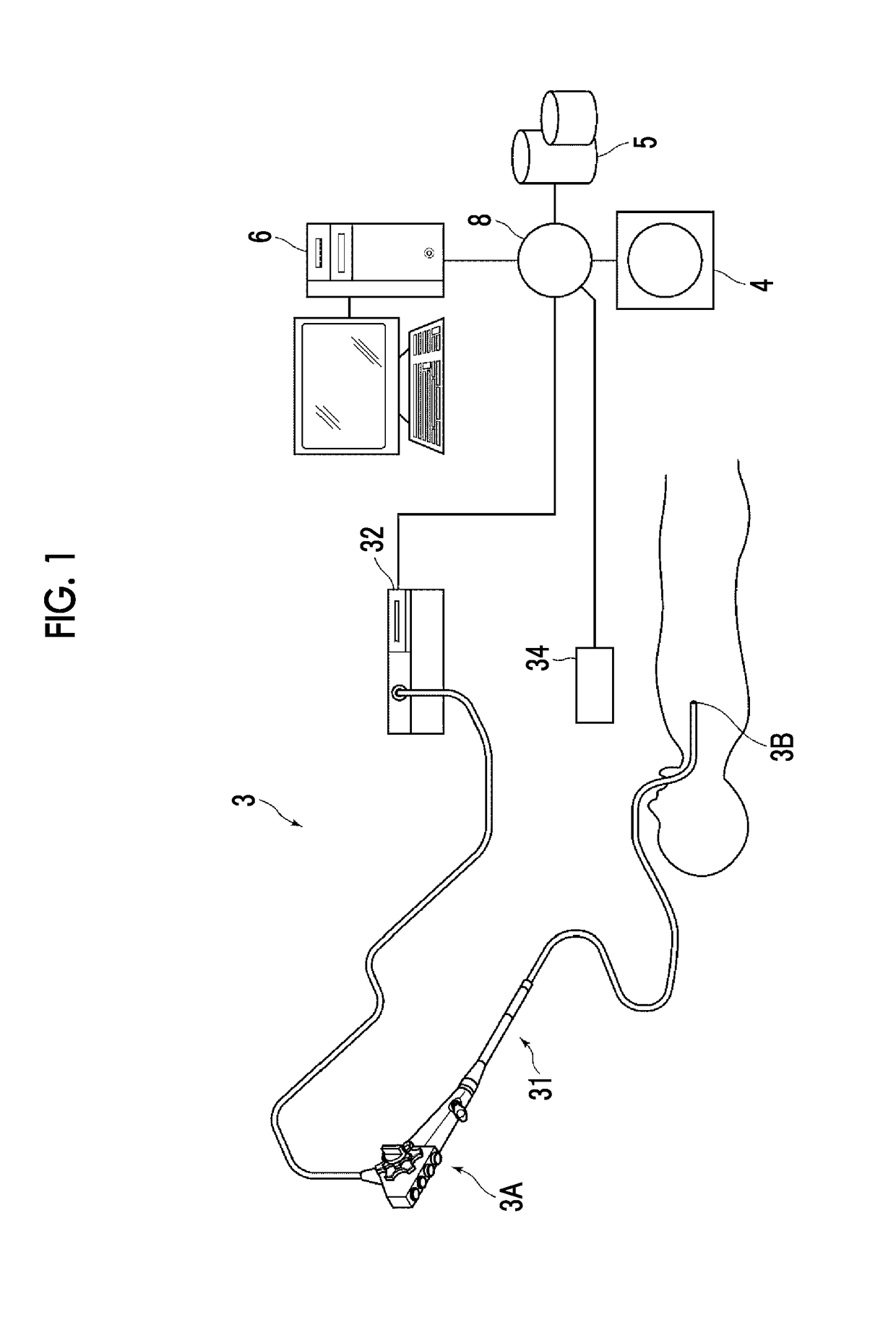
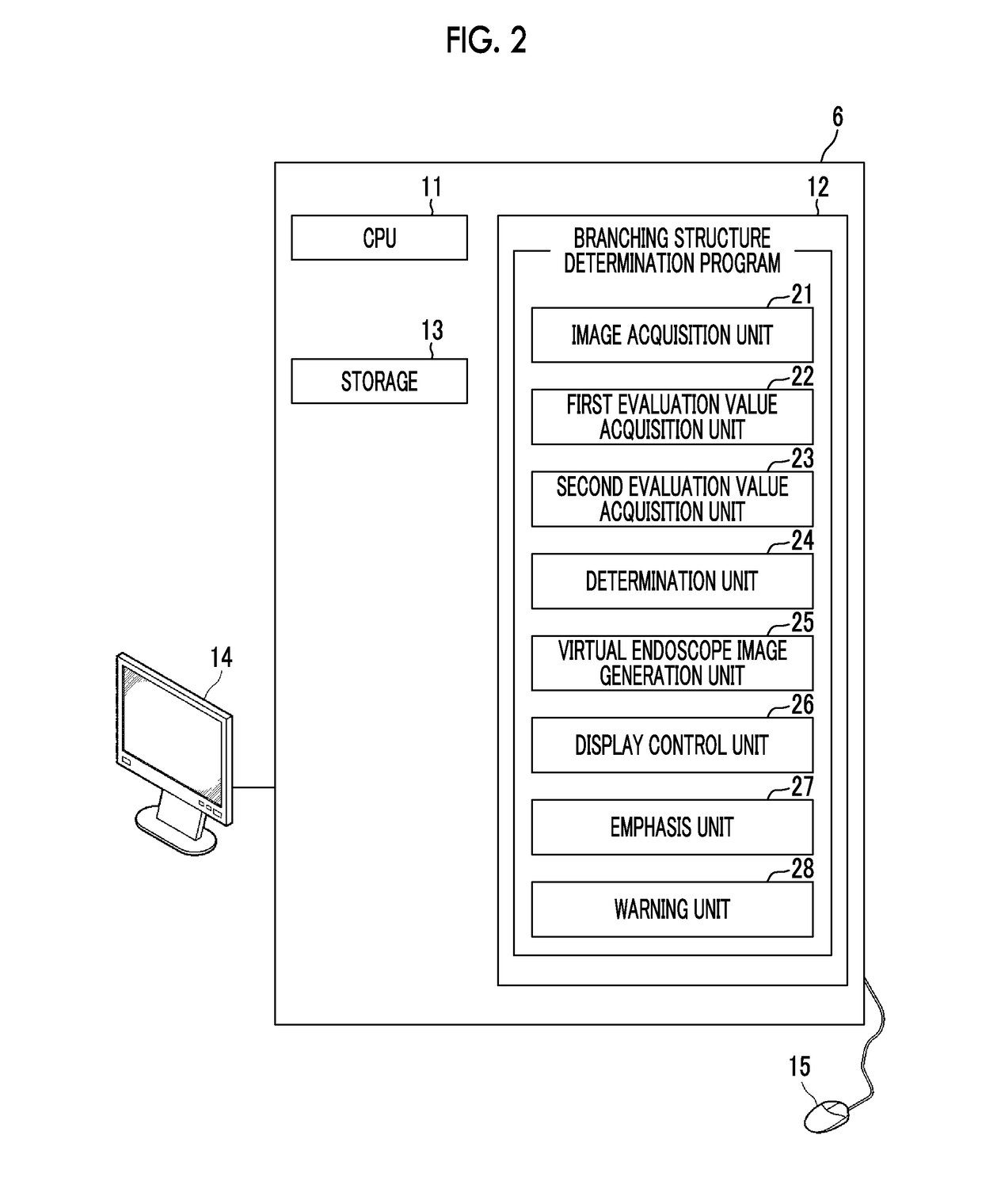
Branching structure determination apparatus, method, and program
InactiveUS20170296032A1Accurately determineAccurately determinedBronchoscopesImage enhancementBronchus/BronchialDisplay device
An image acquisition unit acquires a real endoscope image. A first evaluation value acquisition unit acquires a first evaluation value indicating the hole likeness of the insertion destination of an endoscope, and a second evaluation value acquisition unit acquires a second evaluation value indicating the boundary likeness of a plurality of bronchi at the bronchial branch. A determination unit determines whether or not a branching structure is included in the real endoscope image using both the first and second evaluation values. When it is determined that a branching structure is included, a virtual endoscope image generation unit generates a virtual endoscope image, and a display control unit displays the real endoscope image and the virtual endoscope image on a display.
Owner:FUJIFILM CORP
Linkage branch mechanism of parallel robot and six freedom parallel robot mechanism
InactiveCN1472046AImprove the rotation effectIncrease stiffnessProgramme-controlled manipulatorEngineeringMulti degree of freedom
A connecting branch structure for the parallel robot is composed of the sequentially connected multi-freedom hinge, parallelogram mechanism and moving set. A six-freedom parallel robot using said connecting branch structure consisting of movable platform, fixed platform and three said connecting branch structures. Its advantages are high flexibility and high rigidity.
Owner:刘辛军
Phosphorous acid concrete super plasticizer with polyethyleneimine structure as well as preparation method and application thereof
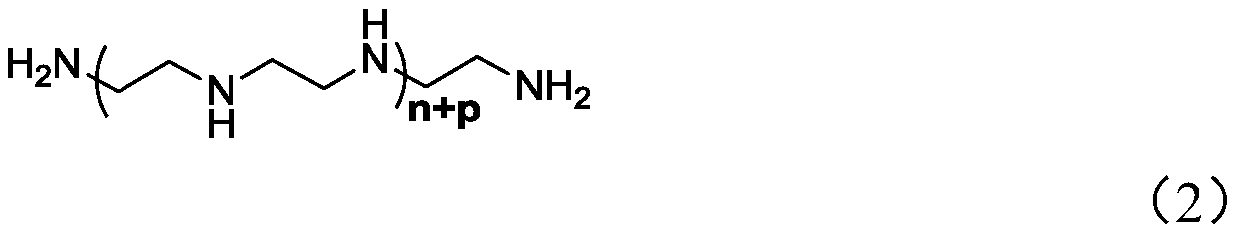
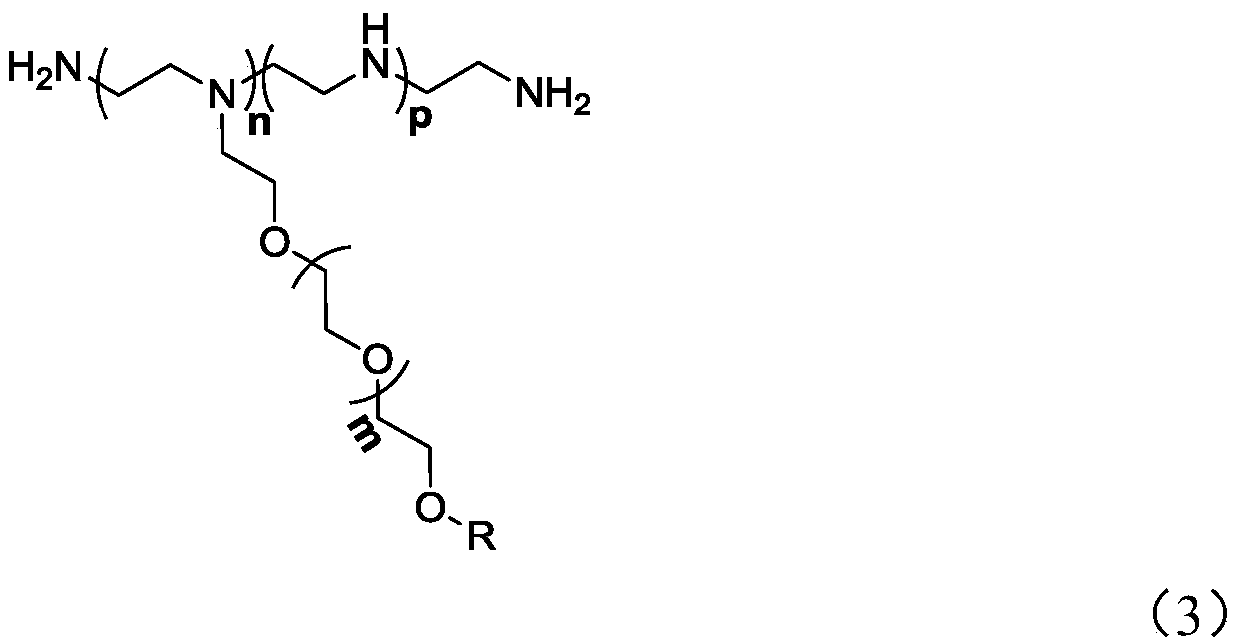
The invention provides a new phosphorous acid concrete super plasticizer with a polyethyleneimine structure as well as a preparation method and an application thereof. The phosphorous acid concrete super plasticizer with a polyethyleneimine structure can effectively improve the concrete fluidity, and the preparation method is simple and effective. The preparation method comprises the following steps: a) making chloro-substituted polyether react with polyethyleneimine so that a part of amino groups H of the polyethyleneimine are substituted to obtain polyethyleneimine with a polyoxyethylene ether branch structure, wherein the molar ratio of the chloro-substituted polyether to the imino groups contained in the polyethyleneimine is 1:(3-8); and b) performing phosphorylation of the remaining amino groups H of the polyethyleneimine with a polyoxyethylene ether branch structure to obtain the phosphorous acid concrete super plasticizer with a polyethyleneimine structure.
Owner:JIANGSU SOBUTE NEW MATERIALS
Crude de-emulsifier and its preparing process
InactiveCN101418230AHigh molecular weightImprove surface propertiesHydrocarbon oil dewatering/demulsificationEpoxyEmulsion
The invention discloses a de-emulsifying agent and a method for preparing the same. The de-emulsifying agent is a polyether compound prepared by alkoxylation reaction of poly (amidoamine) (PAMAM) and epoxy compounds. The invention adopts the PAMAM with a dendritic multi-branch structure as an initiator for synthesis the de-emulsifying agent. The obtained de-emulsifying agent has the characteristics of a plurality of branched and large molecular weight. The de-emulsifying agent has good interfacial activity, infiltrability, good crude oil emulsion de-emulsifying performance, and wide applications in crude oil exploration, oil refining and other fields.
Owner:INST OF CHEM CHINESE ACAD OF SCI
Method of forming branched structures
InactiveUS20060131265A1Decorative surface effectsSemiconductor/solid-state device manufacturingPolyelectrolyteColloidal particle
The present invention provides a method of forming a branched structure which comprises applying colloidal-sized particles over structures. The coated structures are then etched such that the structures are etched through the colloidal particles to form branched structures. The etch may be a reactive ion etch. The structures may be microstructures formed as high aspect ratio microstructures. The colloidal-sized particles may be applied as a colloidal solution and a polyelectrolyte (PE) layer may be applied to the microstructures prior to the colloidal solution to promote adsorption of the colloidal particles.
Owner:AGENCY FOR SCI TECH & RES
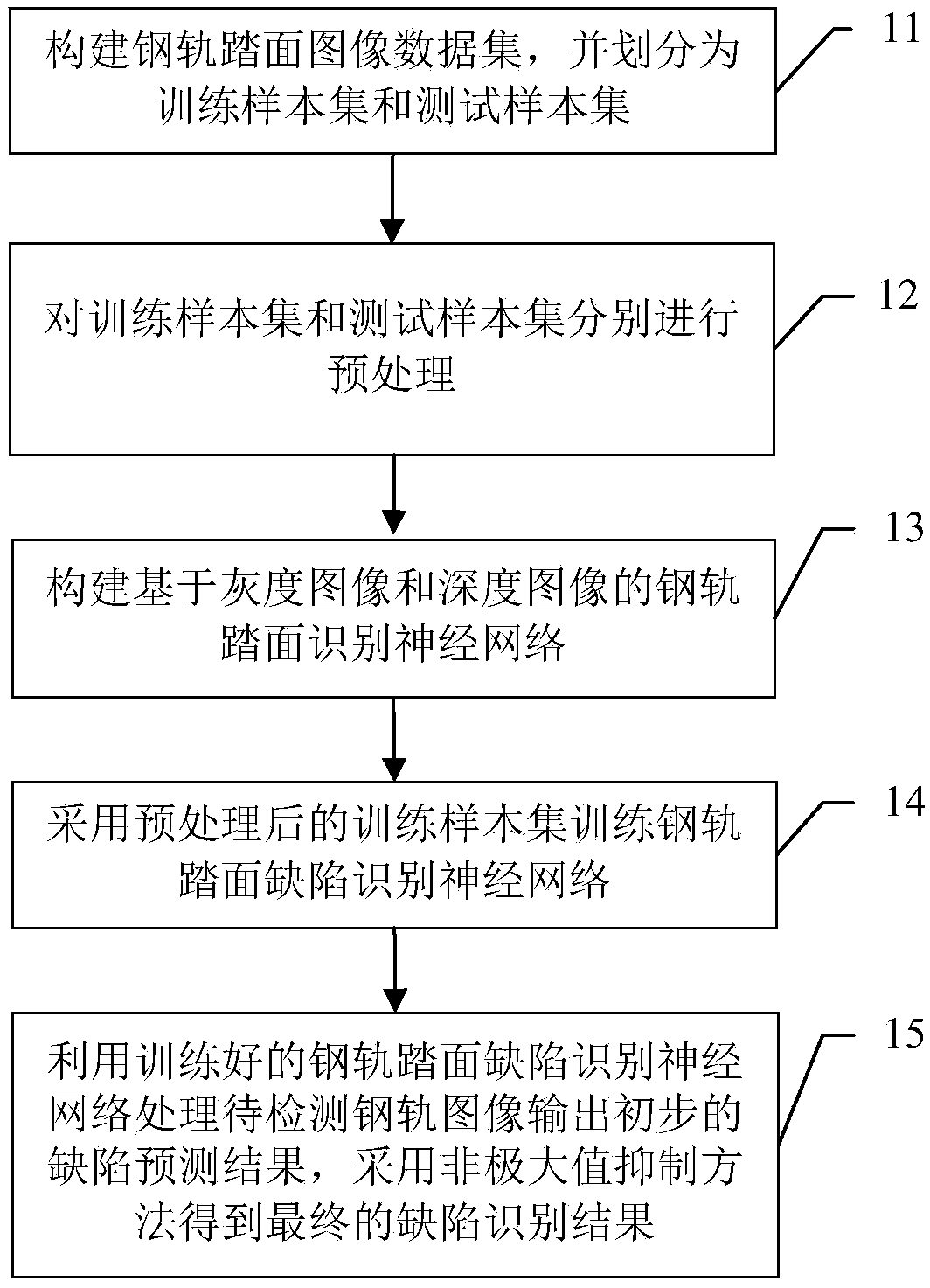
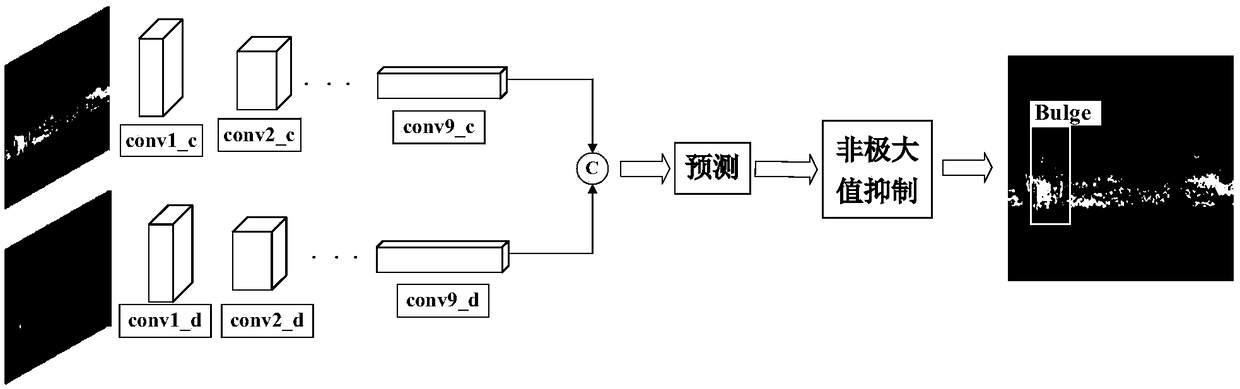
Steel rail tread defect recognition method based on combination of gray image and depth image
InactiveCN108921846ASolving Sparse GradientsReduce false positive rateImage enhancementImage analysisData setTest sample
The invention discloses a steel rail tread defect recognition method based on combination of a gray image and a depth image. The method comprises the steps of establishing a steel rail tread image data set by utilizing a registered gray image and depth image pair of a steel rail tread, dividing the data set into a training sample set and a test sample set, and preprocessing the images of the dataset; performing defect recognition by adopting a special convolutional neural network structure, wherein a front end of the network is provided with two branch structures, which can extract features from the gray image and the depth image of the steel rail tread respectively; fusing feature information of the gray image and the depth image through feature graph connection, and then outputting preliminary prediction results by adopting a prediction module; and finally, screening the preliminary defect prediction results by adopting a non-maximum suppression method to obtain a final steel rail defect recognition result. The method combines two-dimensional and three-dimensional features of the steel rail tread at the same time, has the capability of distinguishing real defects and pseudo-defects, can reduce the misjudgment rate and the missing detection rate, and is especially suitable for defect recognition in a complex environment.
Owner:BEIHANG UNIV
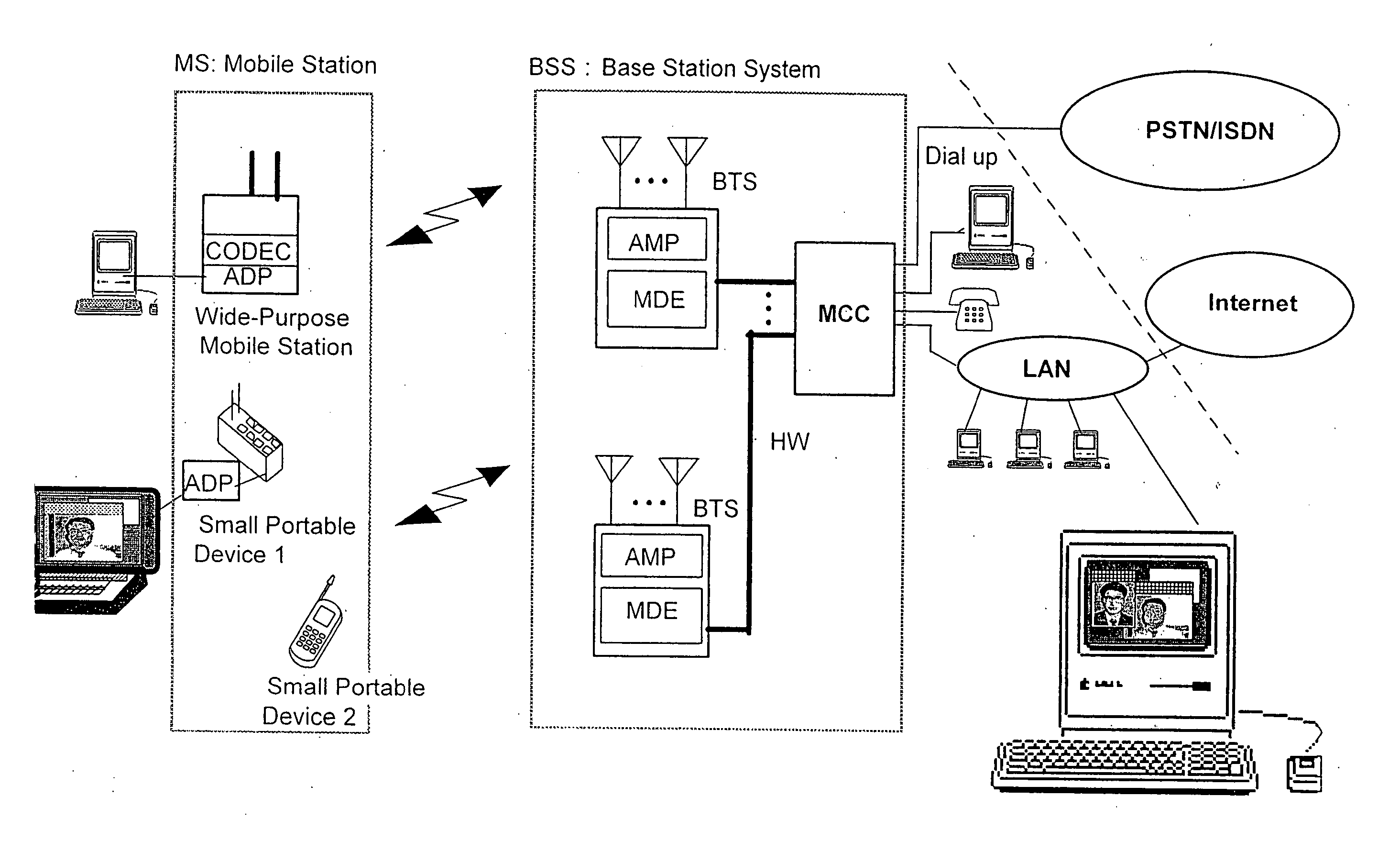
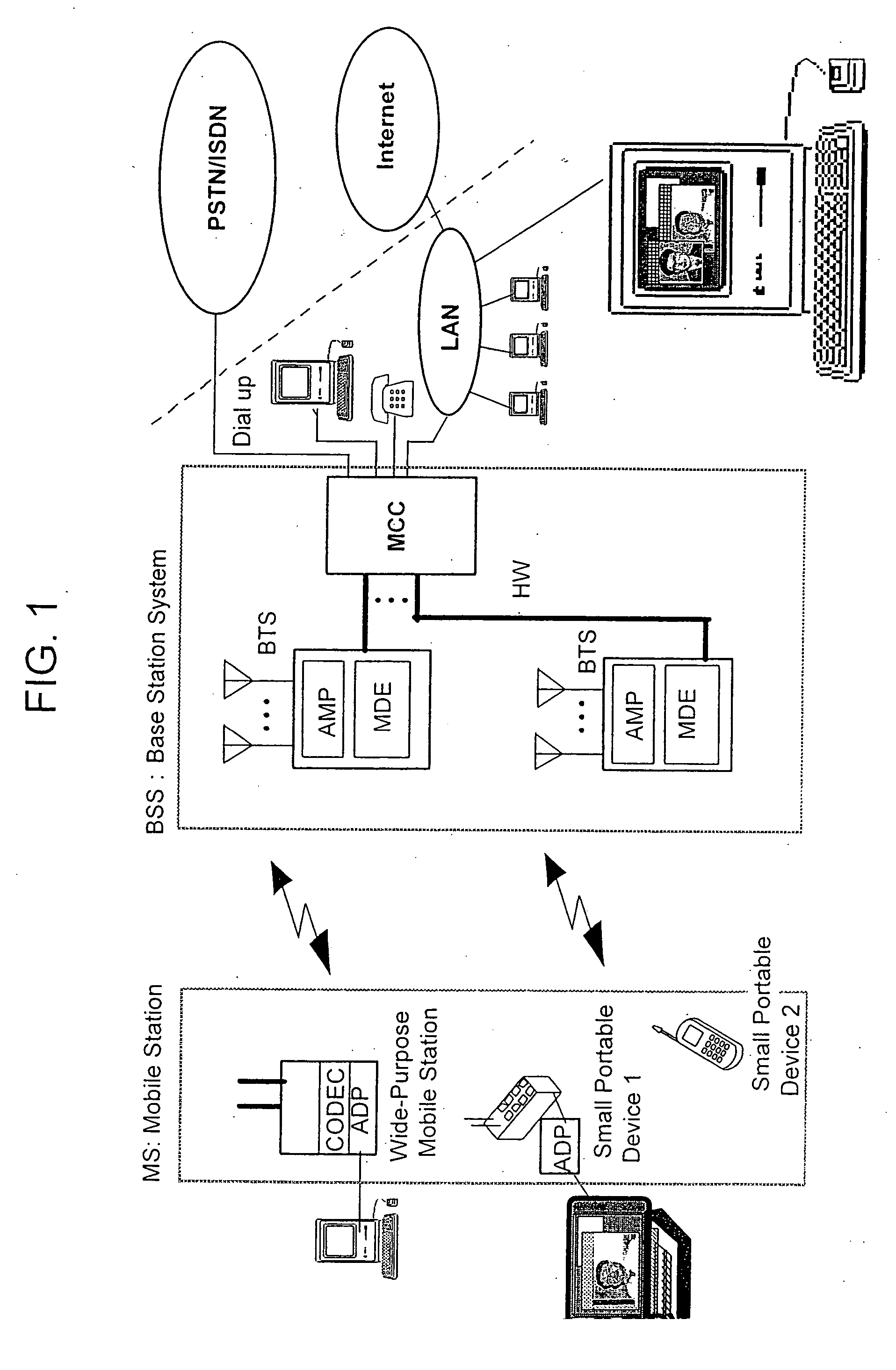
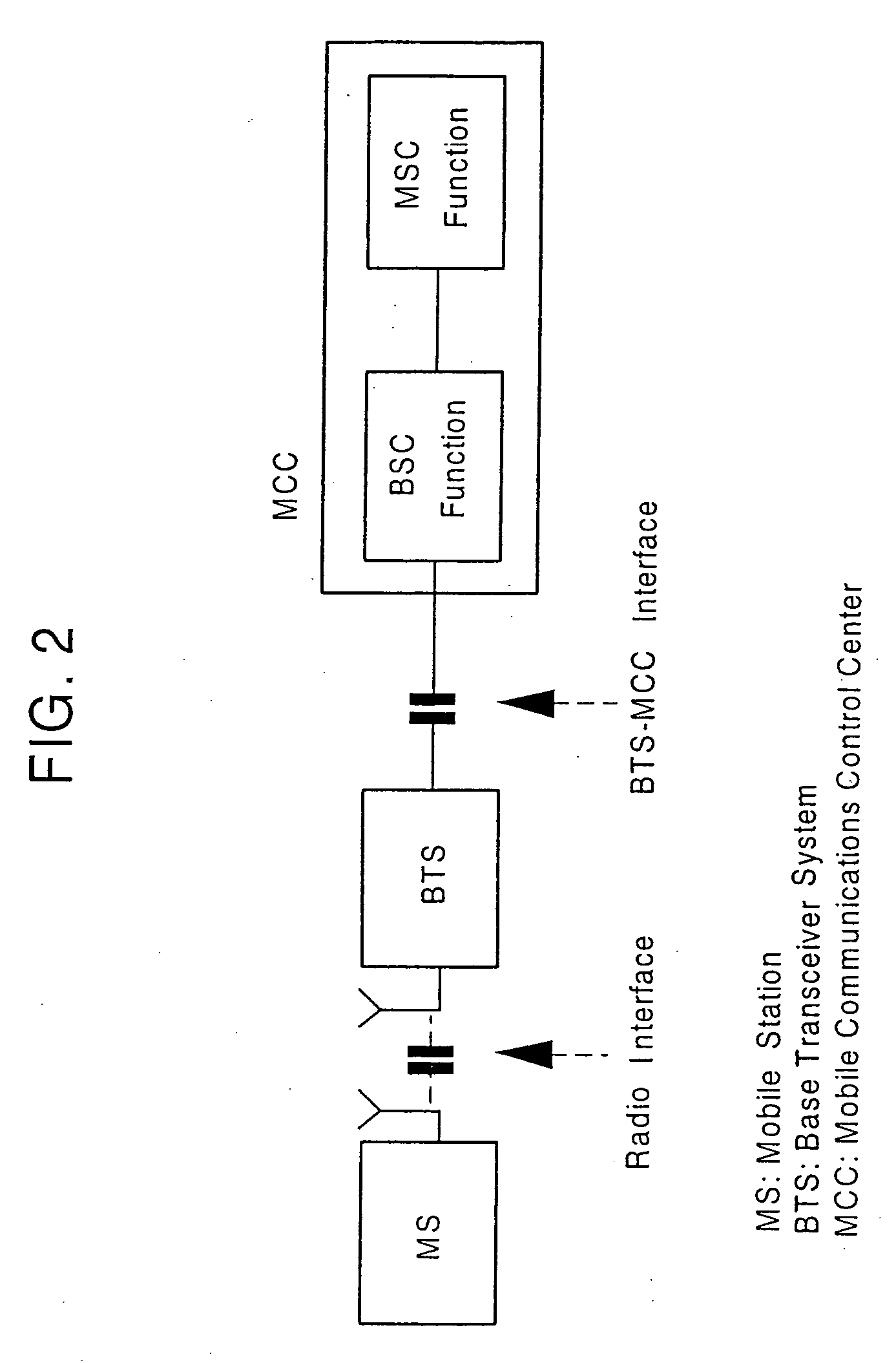
Method and system for mobile communications
InactiveUS20060178167A1Minimize the numberShorten connection delayPower managementSite diversityCommunications systemStart time
When a network pages the temporary user mobile identifier of a mobile station, the mobile station sends a response to the network. Next, the network checks the authenticity of the user using a ciphering key, corresponding to the temporary user mobile identifier and a random number. If the temporary user mobile identifier is authenticated, a normal incoming call acceptance procedure is executed. If the mobile station is authenticated although the temporary user mobile identifier is wrong, the network reassigns a new temporary user mobile identifier to the mobile station and stops the current communication. In communication, the network and the mobile station mutually notify encipherment-onset time and negotiate about encipherment manner with each other. In addition, diversity handover is commenced upon a call attempt. Furthermore, if a branch replacement is necessary, the current branch is replaced by new branches capable of executing the diversity handover. Additionally, when a new call occurs to or from the mobile station capable of treating a plurality of calls simultaneously, the mobile station uses the same branch structure and the same communication frequency band for all of calls. Additionally, when a new call occurs to or from the mobile station capable of treating a plurality of calls simultaneously, a branch structure and a communication frequency band, which can continue all of the calls, are selected and used. Therefore, the mobile communications system is suitable for transmission of various sorts of data in accordance with the development of multimedia.
Owner:KOKUSA ELECTRIC CO LTD
Wire for welding
InactiveUS6337144B1Increase the number ofElectric discharge heatingSynthetic resin layered productsUnsaturated hydrocarbonCarbon steel
A welding wire of the type consists of a plated or uncovered solid wire and a flux-cored wire for carbon steel or stainless steel, wherein one or more of hydrocarbon compounds selected from the group consisting of saturated or unsaturated hydrocarbon compounds, which have from 5 to 12 carbon atoms and a linear or branched structure, and hydrocarbon compounds having a cyclic structure are deposited on a wire surface. A lubricating oil and / or lubricating particles are chemically combined with a wire surface through the one or more hydrocarbon compounds. The total amount of the hydrocarbon compounds, and a lubricating oil and / or lubricating particles deposited on the wire surface is in the range of 0.1 to 5 g per 10 kg of the wire.
Owner:KOBE STEEL LTD
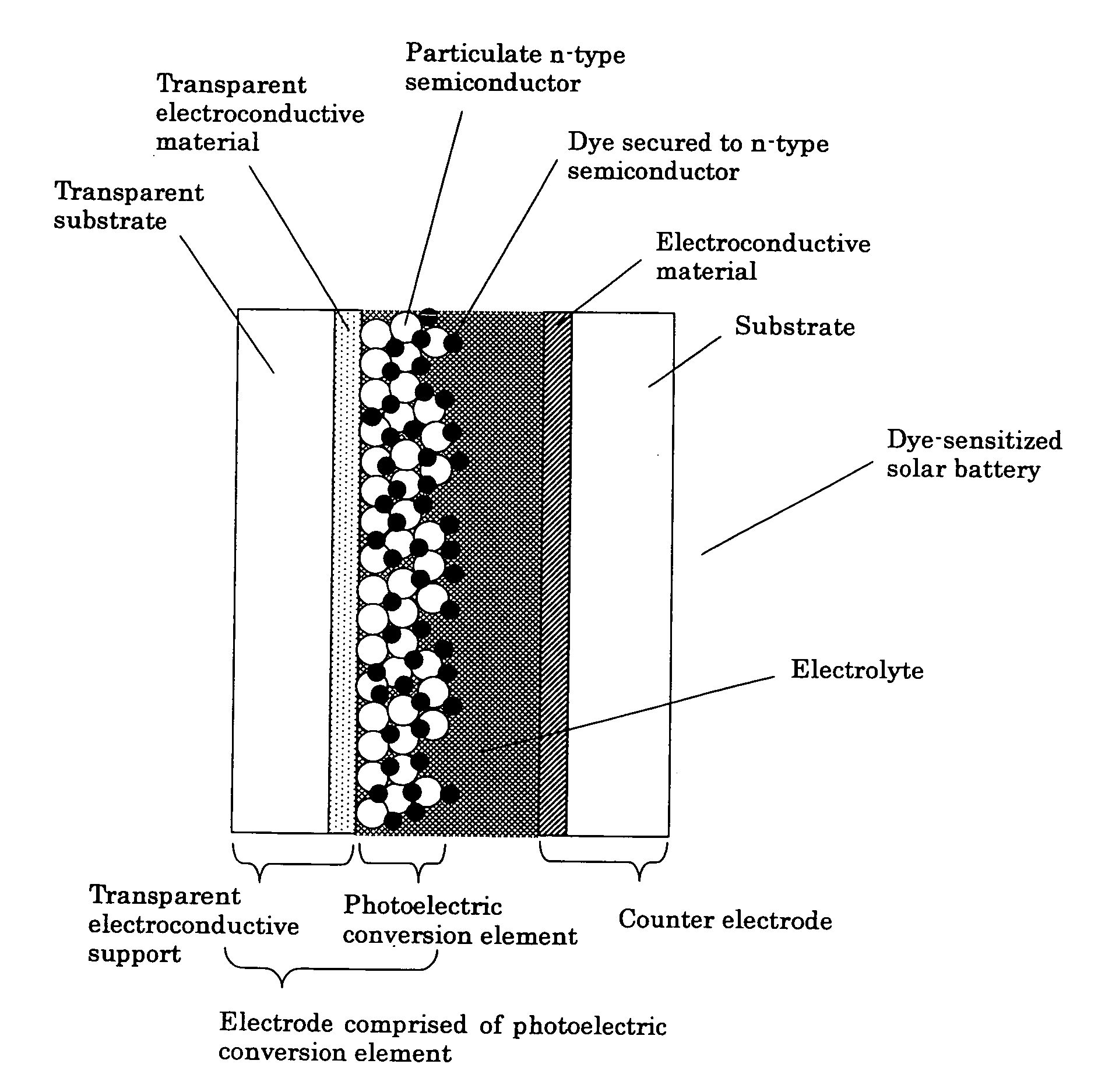
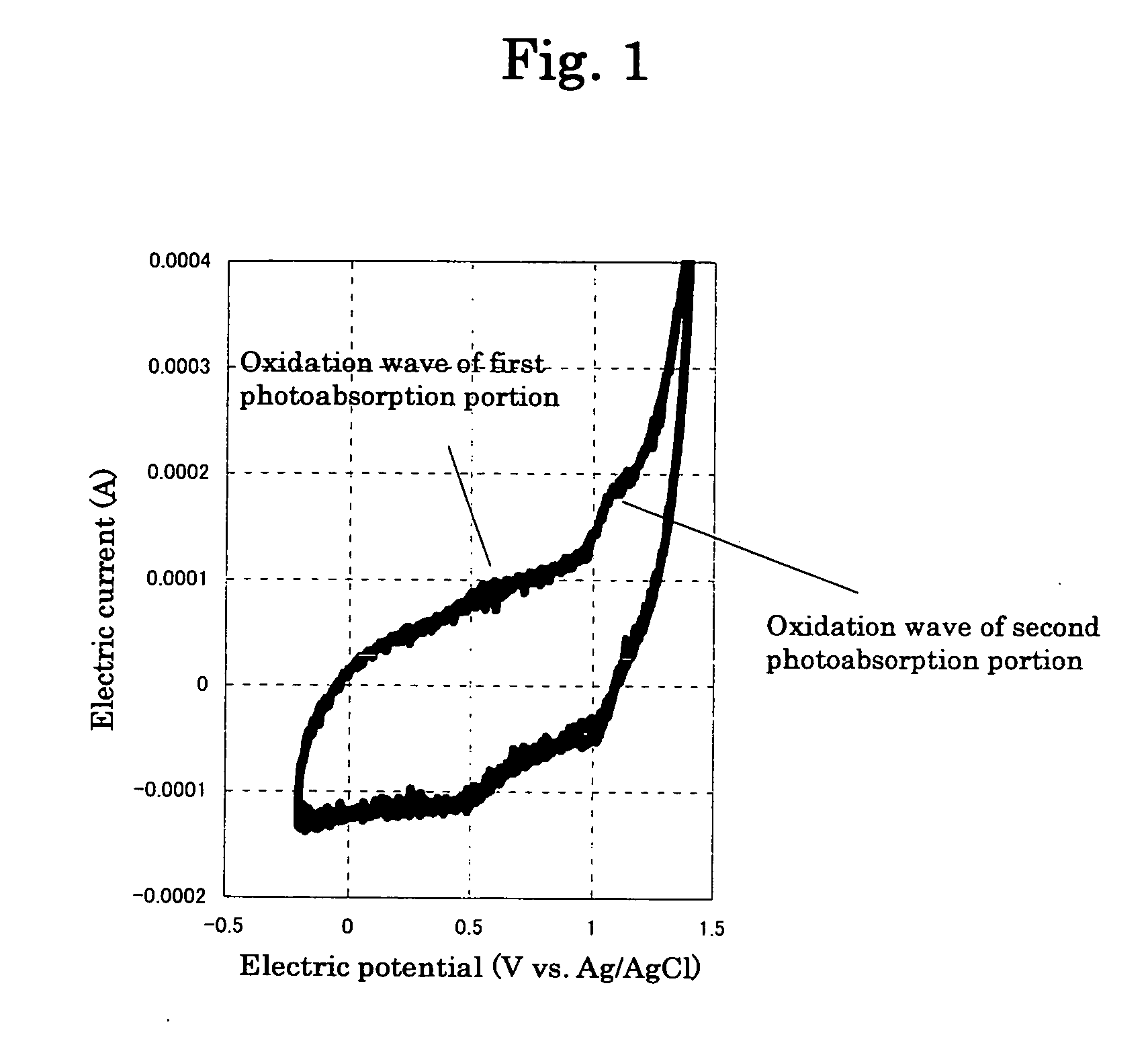
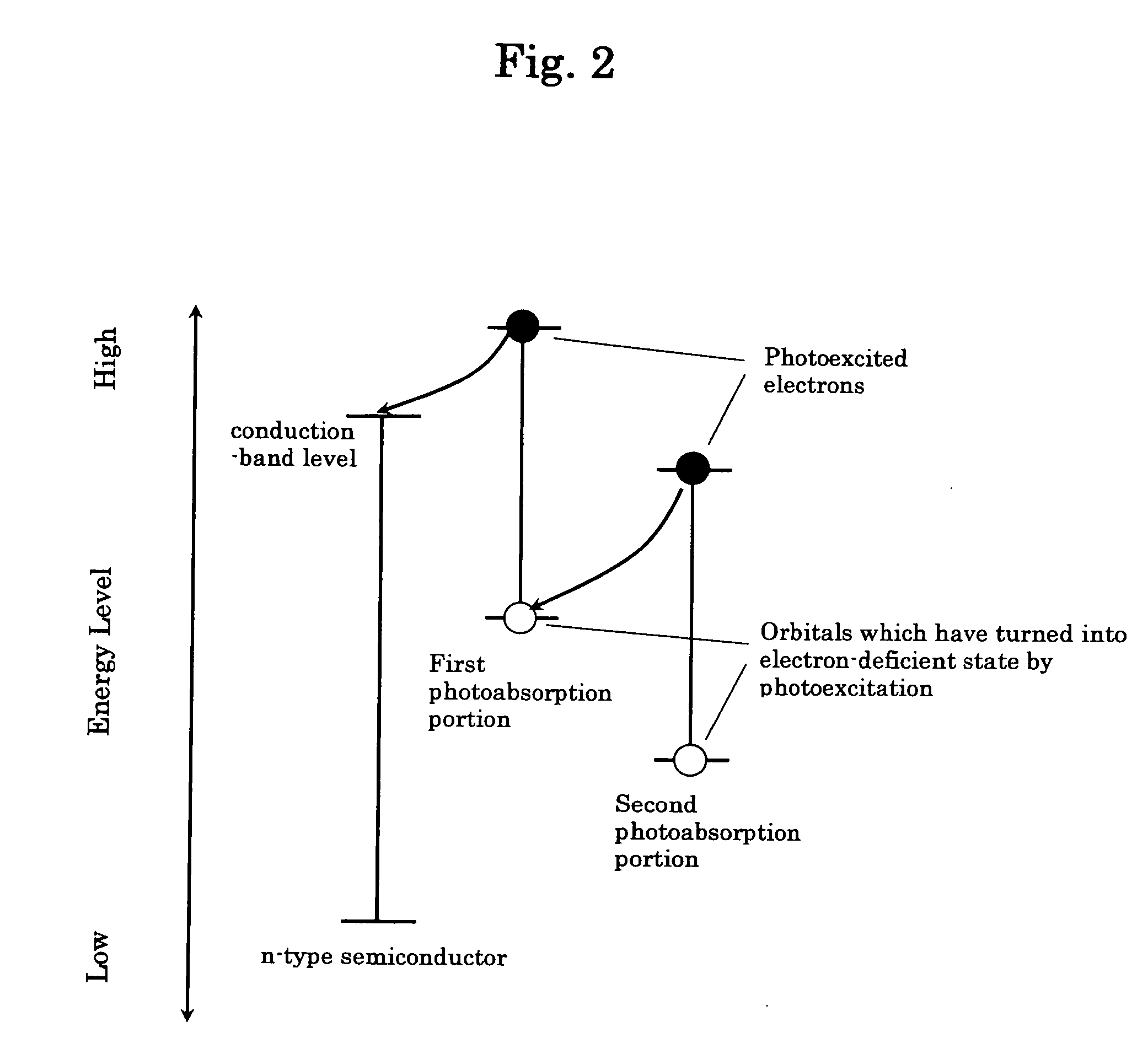
Photoelectric conversion element
InactiveUS20060237059A1Improve photoelectric conversion performanceImprove efficiencyLight-sensitive devicesSolid-state devicesPhotoelectric conversionSemiconductor
A photoelectric conversion element having a composite dye and an n-type semiconductor, the composite dye having a plurality of component dyes which have different excitation levels and which are chemically bonded to each other to form a straight chain or branched structure for transferring an electron therethrough, wherein the straight chain or branched structure is, at one end thereof, secured to the n-type semiconductor and has, at least at one other end thereof, a free end, wherein, in the straight chain or branched structure, the plurality of component dyes are arranged in an order such that the excitation levels of the plurality of component dyes are decreased as viewed from the one end of the structure toward the at least one other end of the structure.
Owner:ASAHI KASEI KK
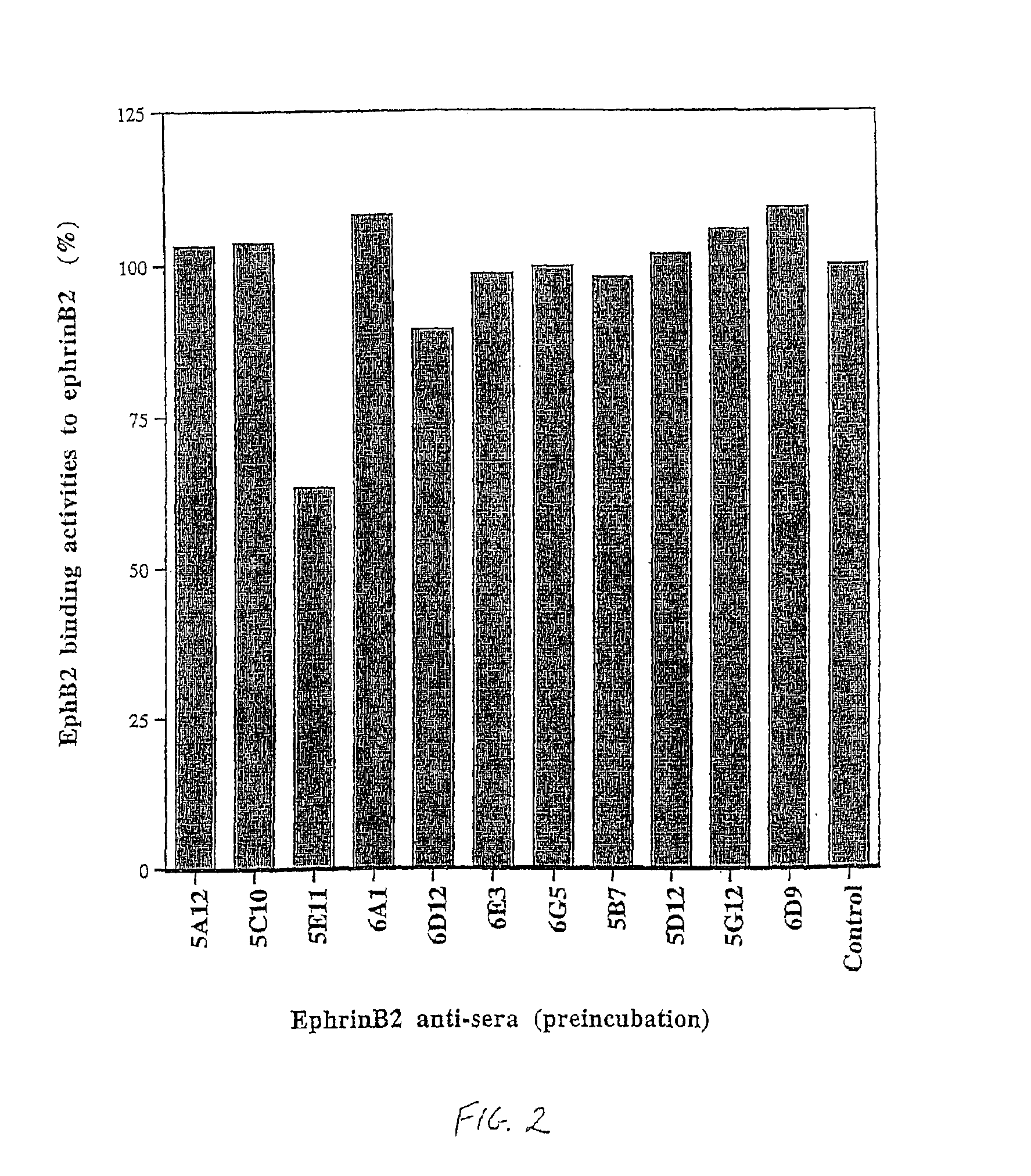
Artery- and vein-specific proteins and uses therefor
InactiveUS6887674B1Enhancing and inhibiting effectCompounds screening/testingPeptide/protein ingredientsBlood vesselReceptor for activated C kinase 1
Arterial and venous endothelial cells are molecularly distinct from the earliest stages of angiogenesis. This distinction is revealed by expression on arterial cells of a transmembrane ligand, called EphrinB2 whose receptor EphB4 is expressed on venous cells. Targeted disruption of the EphrinB2 gene prevents the remodeling of veins from a capillary plexus into properly branched structures. Moreover, it also disrupts the remodeling of arteries, suggesting that reciprocal interactions between pre-specified arterial and venous endothelial cells are necessary for angiogenesis. This distinction can be used to advantage in methods to alter angiogenesis, methods to assess the effect of drugs on artery cells and vein cells, and methods to identify and isolate artery cells and vein cells, for example.
Owner:CALIFORNIA INST OF TECH
High fused mass strength polypropylene containing long branched chain structure and preparing method thereof
The invention relates to a high fused mass strength polypropylene contained long-chain branch and the preparation method thereof. The high fused mass strength polypropylene resin is prepared by polypropylene grafted object, amine or alcohols compound as well as antioxidant and heat stabilizer, etc. The invention adopts a melting and continuously extrusion method with a reaction-type double screw extruder to prepare the high fused mass strength polypropylene, and uses supercritical carbon dioxide to assist the extrusion, which can lower the extrusion temperature, reduce the degradation of polymer and meanwhile greatly strengthen the pervasion of molecule, so as to further promote the reaction. In the reaction process, as chain extender, amine and alcohols compound react with special functional group of polypropylene grafted object, link linearity polypropylene molecular chain, consequently produce novel polypropylene that each grafted point includes two long-chain branch structures and of which the melt flow rate is adjustable. The novel polypropylene is characterized by non-gelatin and strain hardening. The product shows great advantages over a plurality of aspects like color, mechanical property and workability, therefore, the product is suitable for application areas of blowing, thermo-forming, blown film, extrusion and coating, etc.
Owner:ZHEJIANG UNIV
Medical image processing apparatus and method, and computer readable recording medium on which is recorded program for the same
ActiveUS20110243403A1Improve diagnostic accuracyImprove efficiencyImage enhancementImage analysisImaging processingComputer graphics (images)
Extracting a branch structure and a surrounding structure area in which a surrounding structure of the branch structure exists from a three-dimensional medical image, setting an attention branch structure in the branch structure, estimating an attention surrounding structure area functionally associated with the attention branch structure from the surrounding structure area based on the branch structure, obtaining an evaluation value in the attention surrounding structure area, and generating a mapped image which is an image generated by mapping the evaluation value in the attention surrounding structure area to a morphological image representing morphology of at least one of the attention branch structure and the attention surrounding structure area.
Owner:FUJIFILM CORP
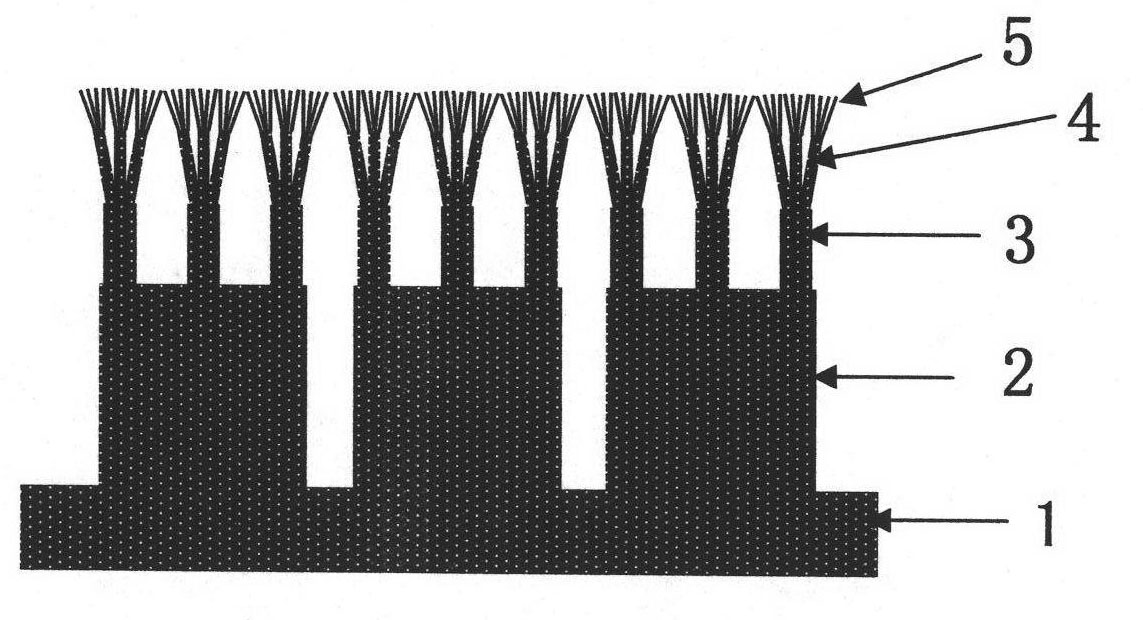
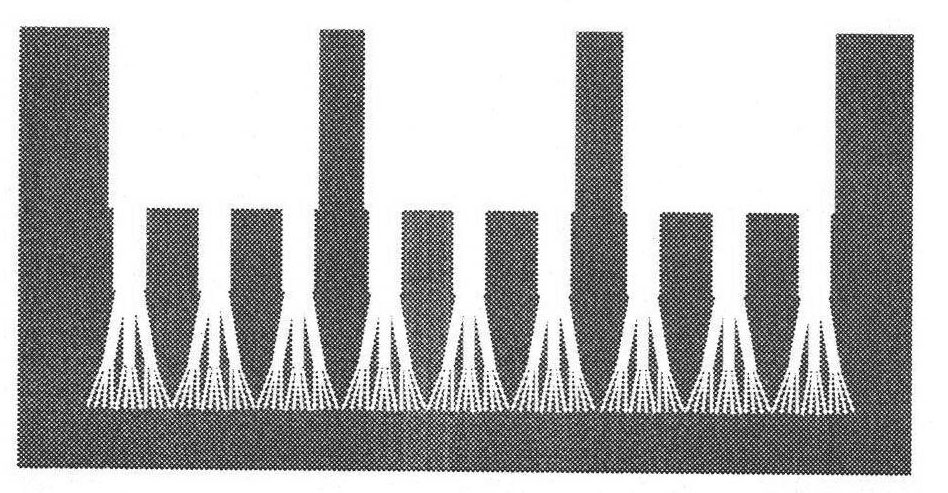
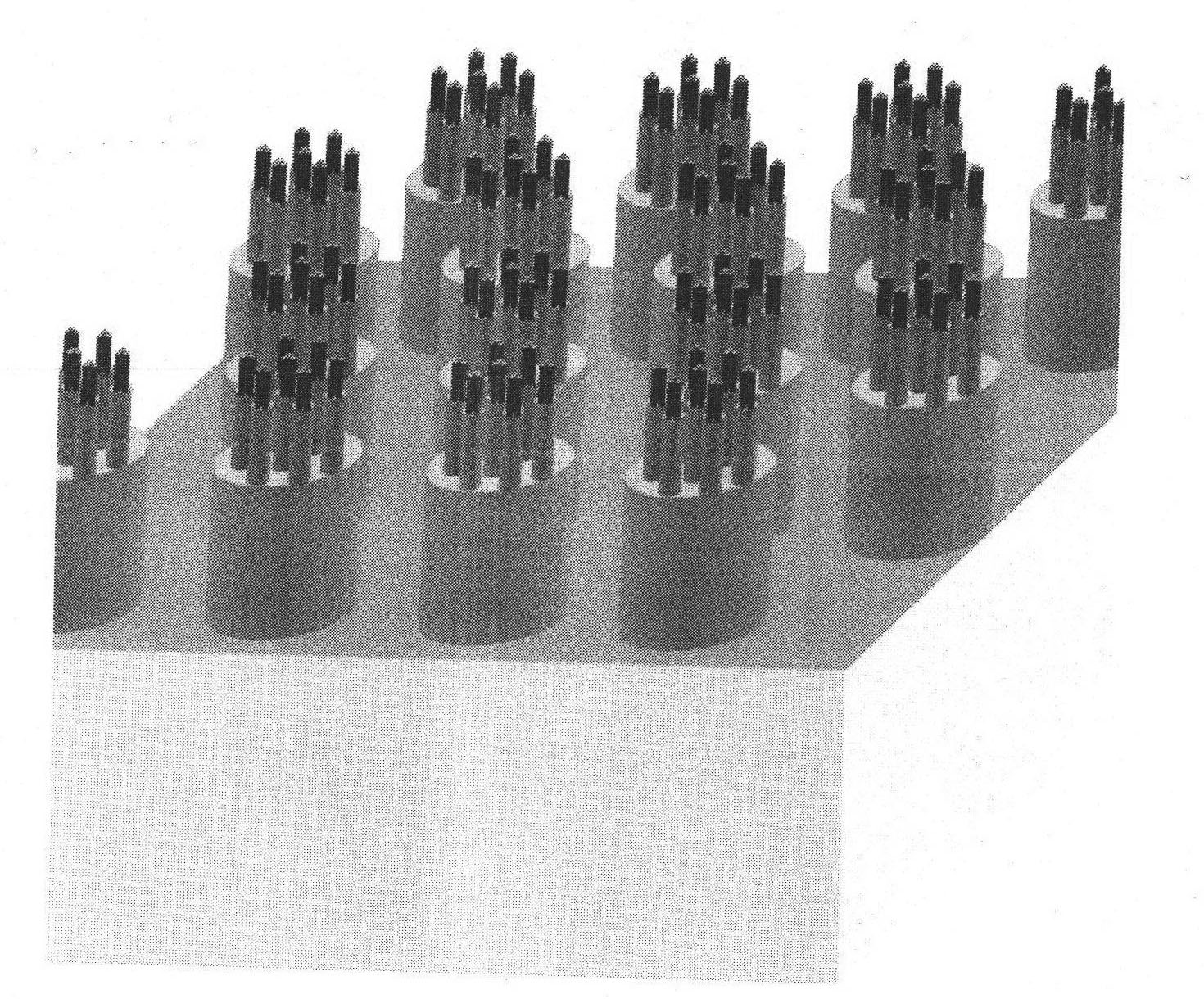
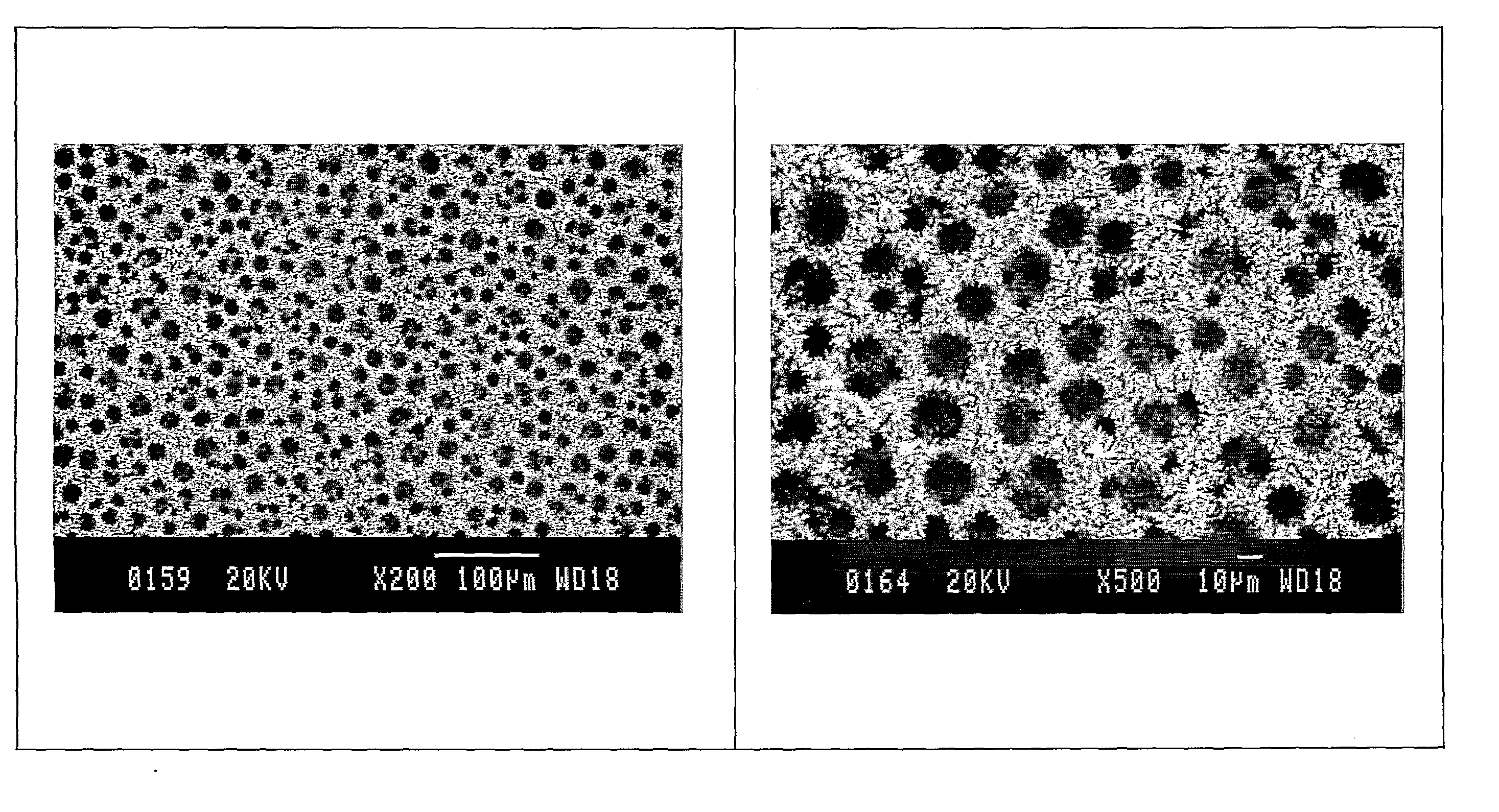
Cross-scale biomimetic micro-nano branch structure array and preparation method thereof
InactiveCN101774528AAchieving cross-scale integrationSolution controllableAnodisationNanostructure manufactureMicro nanoElectrochemical anodization
The invention discloses a cross-scale biomimetic micro-nano branch structure array and a preparation method thereof, which relate to the field of micro-nano materials and robots, particularly relate to a biomimetic adhesive material and a preparation method thereof and also relate to an electrochemical anodic oxidation process. The cross-scale biomimetic micro-nano branch structure array consists of a substrate and a micro-nano multilevel branch structure array, wherein the micro-nano multilevel branch structure array at least comprises a primary micron cylindrical structure array and a branch micro-nano cylindrical structure array. The preparation method thereof comprises the following steps of: firstly, etching an aluminum template with an argon ion beam to obtain an aluminum template with a primary micron hole array; secondly, preparing a micro-nano branch structure array in a definite point and direction on the template array by an electrochemical anodic oxidation process; thirdly, performing film extrusion and curing on the template by a polymer replica method; and finally, removing the template for forming to obtain the desired micro-nano structure array to form a biomimetic dry adhesive material. The cross-scale biomimetic micro-nano branch structure array and the preparation method thereof use electric characteristics to effectively solve the control problem of from micron to nanometer cross-scale branch structure arrays and have a great significance for the development of biomimetic adhesive materials and related dry biomimetic robots.
Owner:HEFEI INSTITUTES OF PHYSICAL SCIENCE - CHINESE ACAD OF SCI
Porous Layer
InactiveUS20100044018A1Improve conductivity stabilityImprove mechanical stabilityLayered productsPretreated surfacesSurface layerPorous layer
Heat exchange device with a boiling surface comprising porous surface layer arranged on a solid substrate, the porous surface layer comprises a porous wall structure defining and separating macro-pores that are interconnected in the general direction normal to the surface of the substrate and have a diameter greater than 5 μm and less than 1000 μm wherein the diameter of the pores gradually increases with distance from the substrate wherein the porous wall structure is a continuous branched structure.
Owner:DANFOSS AS
Oily makeup cosmetics
The present invention is to provide oily makeup cosmetics which comprises an oligo ester obtained from (a) an aliphatic acid or a hydroxy aliphatic acid having 8 to 30 carbon atoms (straight or branched, saturated or unsaturated), (b) a straight or branched dibasic acid having 12 to 36 carbon atoms, and (c) glycerol or a glycerol condensate, and a hydrocarbon having a branched structure.
Owner:KANEBO COSMETICS INC +1
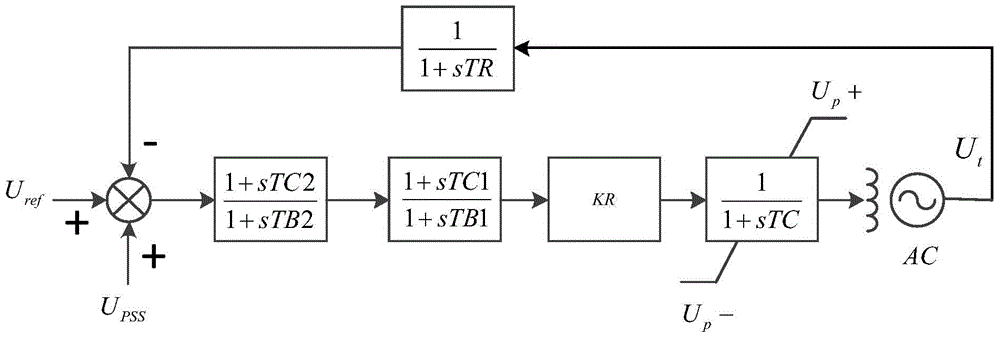
Design method for power system stabilizer capable of suppressing ultra-low frequency oscillation
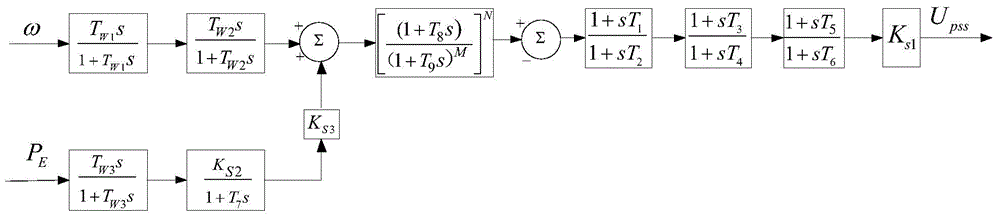
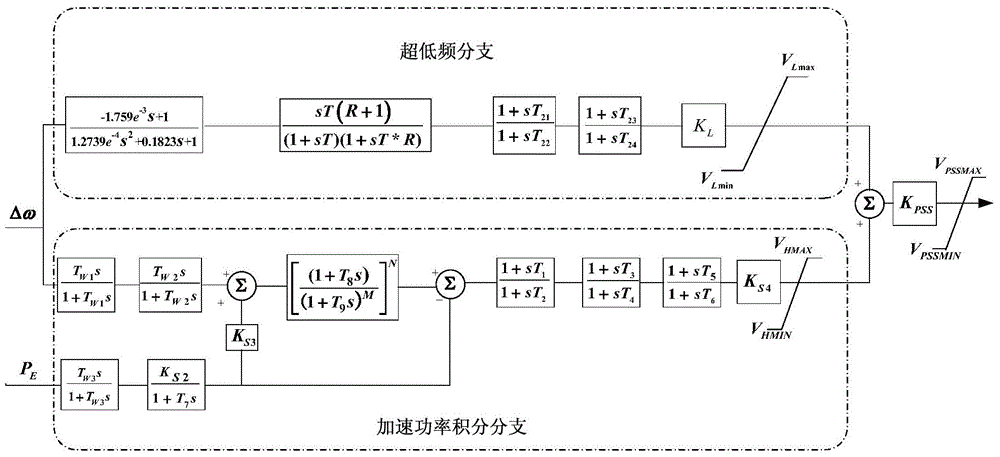
ActiveCN103956755AStrong independenceSolve the problem of insufficient dampingPower oscillations reduction/preventionAngular velocityEngineering
The invention provides a design method for a power system stabilizer capable of suppressing ultra-low frequency oscillation. The design method comprises the steps that the operating frequency of the power system stabilizer is divided into an ultra-low frequency band with rotor angular velocity deviation delta omega as input signals and a medium-high frequency band with acceleration power deviation integral as input signals; the input signals of the ultra-low frequency band are screened and subjected to phase compensation; the input signals of the medium-high frequency band are obtained and subjected to phase compensation. According to the design method for the power system stabilizer capable of suppressing ultra-low frequency oscillation, two parallel branch structures are adopted and compensate for different frequency domain ranges respectively, the parameters of the two parallel branch structures are greatly independent with respect to setting, and the problem that an existing PSS is insufficient in damping within an ultra-low frequency domain is solved by means of adding ultra-low frequency branches.
Owner:STATE GRID CORP OF CHINA +1
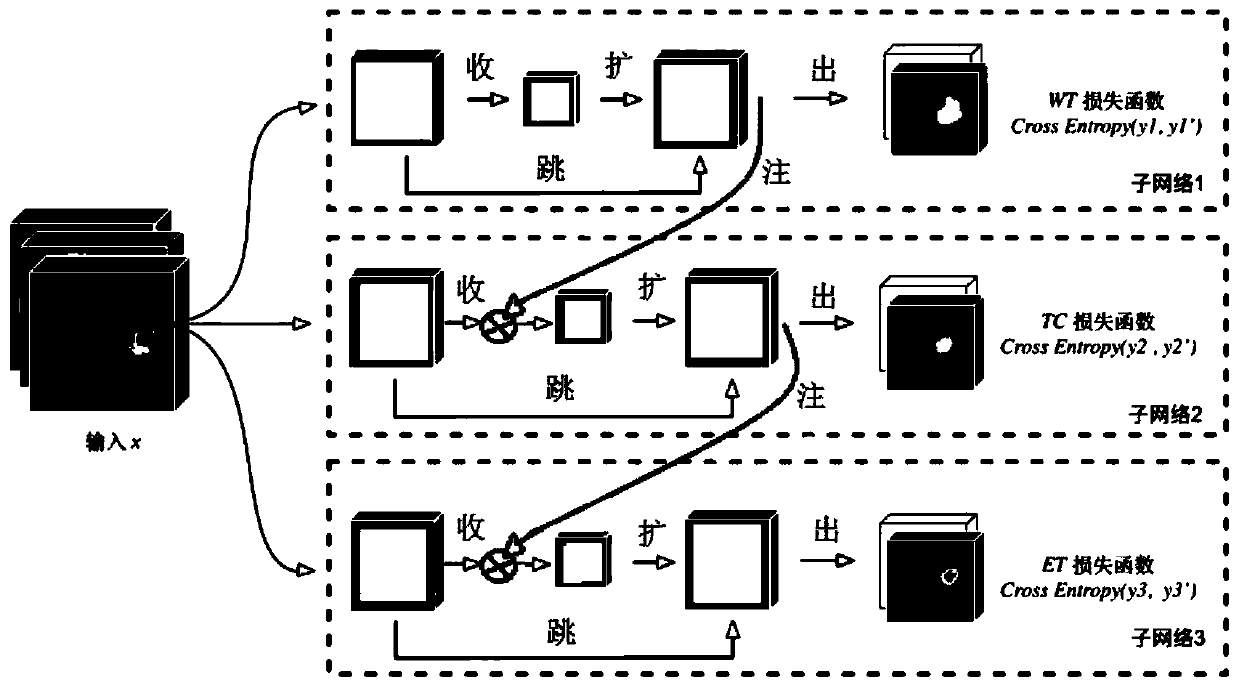
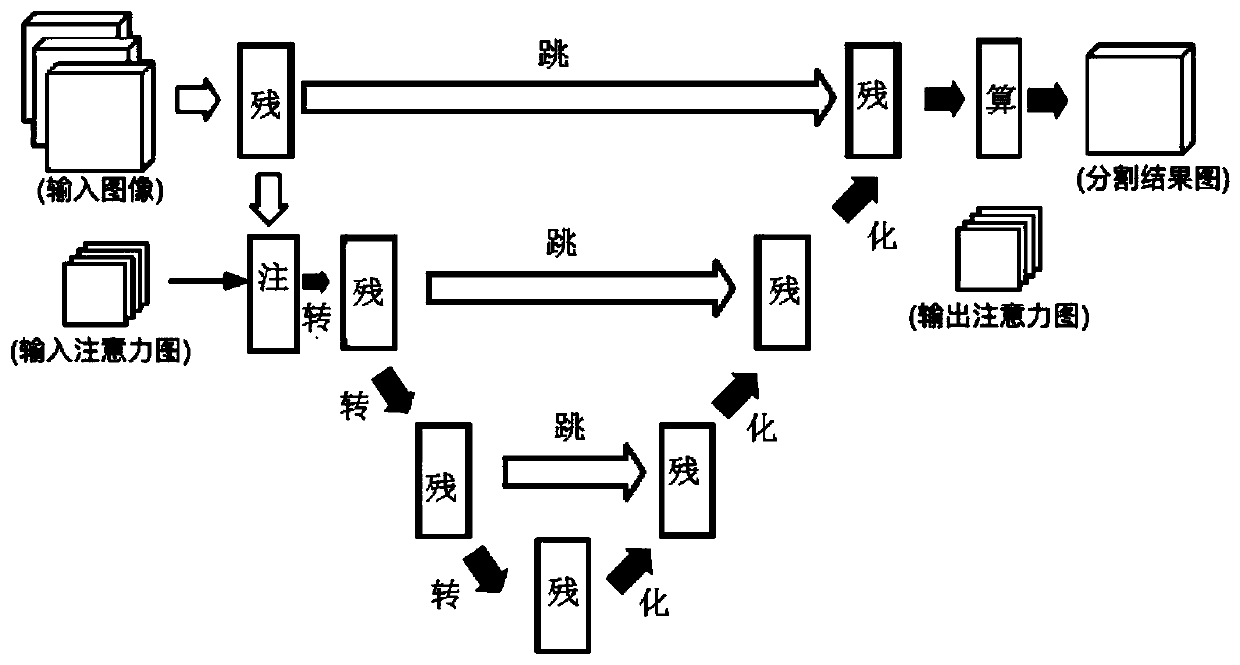
End-to-end tumor segmentation method based on multi-attention mechanism
ActiveCN109754404AImprove segmentationEasy to splitImage analysisNeural architectures3d imageBrain tumor
The invention relates to an end-to-end tumor segmentation method based on a multi-attention mechanism. The method mainly comprises a backbone network part and an attention module part, the backbone network comprises three sub-networks, and the three sub-networks are composed of improved 3D Resinual U-net composition; and the attention module is composed of a specially designed double-branch structure. The method can make up the defect of low training efficiency in the prior art; defect of poor segmentation precision, converting the multi-class segmentation problem of a plurality of tumor sub-regions into a plurality of two-class segmentation tasks. The attention mechanism takes the segmentation result of the tumor peripheral edema region as a soft attention and adds the soft attention intothe segmentation subtask for the tumor core part, and the segmentation result of the tumor core part is also added into the segmentation subtask for the enhancement region in the tumor core through the attention mechanism. The method is suitable for segmentation of 3D images of tumor lesion tissues with similar hierarchical structures including brain tumors, including MRI images, CT images and the like, and a more accurate segmentation result can be provided.
Owner:SHENZHEN GRADUATE SCHOOL TSINGHUA UNIV
Colloidal silica containing silica secondary particles having bent structure and/or branched structure, and method for producing same
ActiveUS20110163262A1Improve polishing rateLarge aspect ratioSilicaOther chemical processesColloidal silicaColloid
This invention provides a dense, high-purity colloidal silica containing silica secondary particles having a branched and / or bent structure, and a production method thereof. Specifically, this invention provides a method for producing a colloidal silica, comprising the steps of 1) preparing a mother liquid containing an alkali catalyst and water, and having a pH of 9 to 12; and 2) adding a hydrolysis liquid obtained by hydrolysis of an alkyl silicate to the mother liquid, wherein the step of adding the hydrolysis liquid to the mother liquid sequentially comprises A) step 1 of adding the hydrolysis liquid until the pH of the resulting liquid mixture becomes less than 7; B) step 2 of adding an aqueous alkali solution until the pH of the liquid mixture becomes 7 or more; and C) step 3 of adding the hydrolysis liquid while maintaining the pH of the liquid mixture at 7 or more, and a colloidal silica containing silica secondary particles having a branched and / or bent structure, obtained by this method.
Owner:FUSO CHEM
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com