Information safety protecting method, information safety protecting device and server device
A technology of information security and protective devices, applied in the field of information security, can solve problems such as antivirus software upgrades, and achieve the effect of protecting information security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
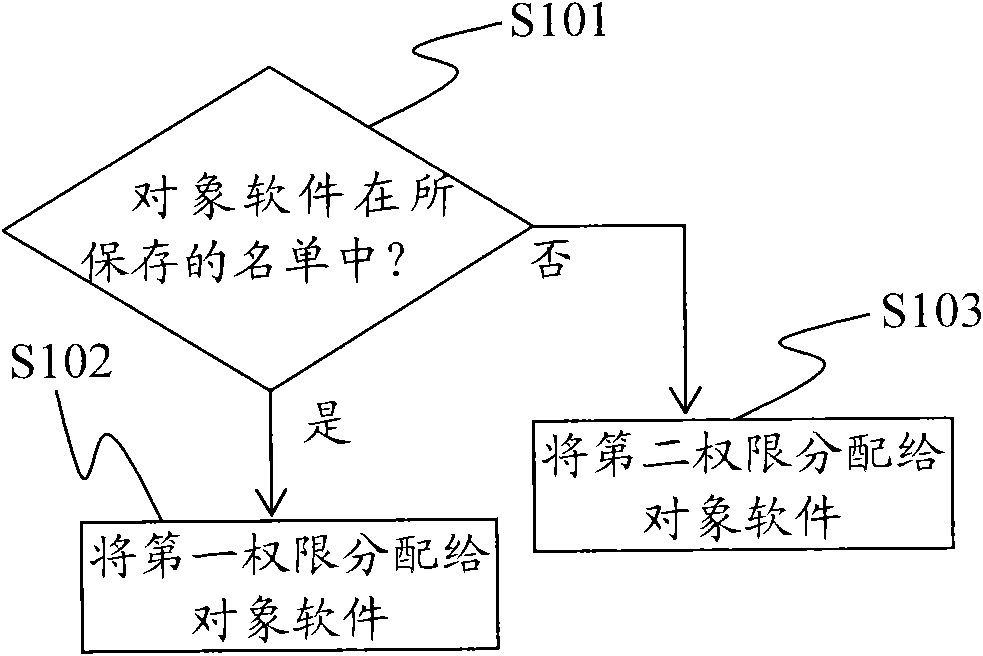
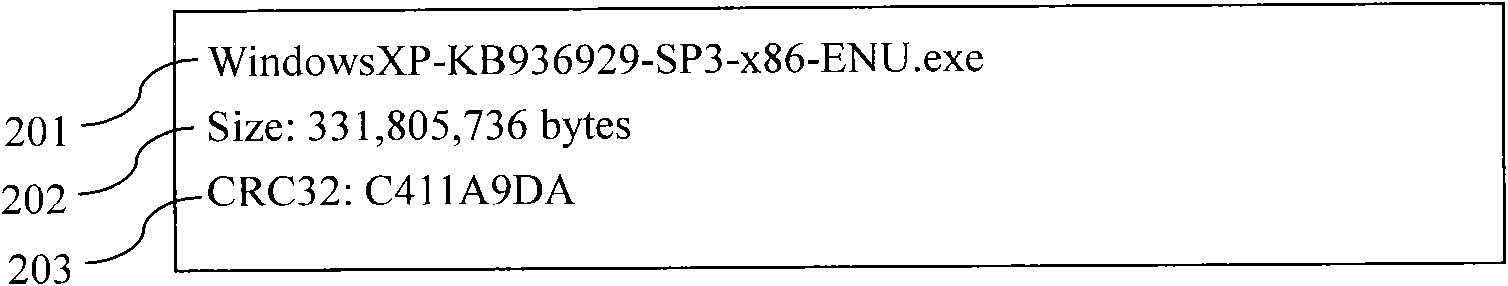
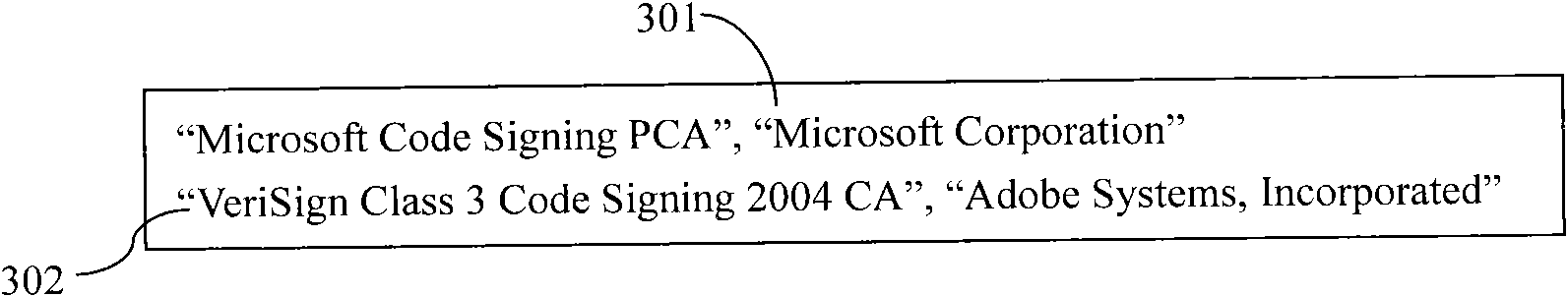
[0025] The present invention uses a software list different from the "black list" of the prior art to assign a higher first authority to software in the software list, and assign a lower second authority to software not in the software list. So that the software not in the software list will not cause harm to the system. Since it is impossible for newly-emerged virus software or rogue software to be in the saved software list, it is impossible for the newly-appeared virus software or rogue software to be assigned higher authority, so it will not cause harm to the system and effectively protects the system. System information security.
[0026] Exemplary embodiments of the present invention will be described below with reference to the accompanying drawings.
[0027] figure 1 It is a flowchart showing the general processing of the information security protection method of the present invention.
[0028] The information security protection method of the present invention is i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com