CDMA port-to-port encryption communication system and key distribution method thereof
An encrypted communication system and key distribution technology, which is applied in the key distribution field of CDMA end-to-end encrypted communication, can solve the problems of key management and identity authentication limitations, to ensure security, reduce security risks, and improve communication safety effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0022] All features disclosed in this specification, or steps in all methods or processes disclosed, may be combined in any manner, except for mutually exclusive features and / or steps.
[0023] Any feature disclosed in this specification (including any appended claims, abstract and drawings), unless expressly stated otherwise, may be replaced by alternative features which are equivalent or serve a similar purpose. That is, unless expressly stated otherwise, each feature is one example only of a series of equivalent or similar features.
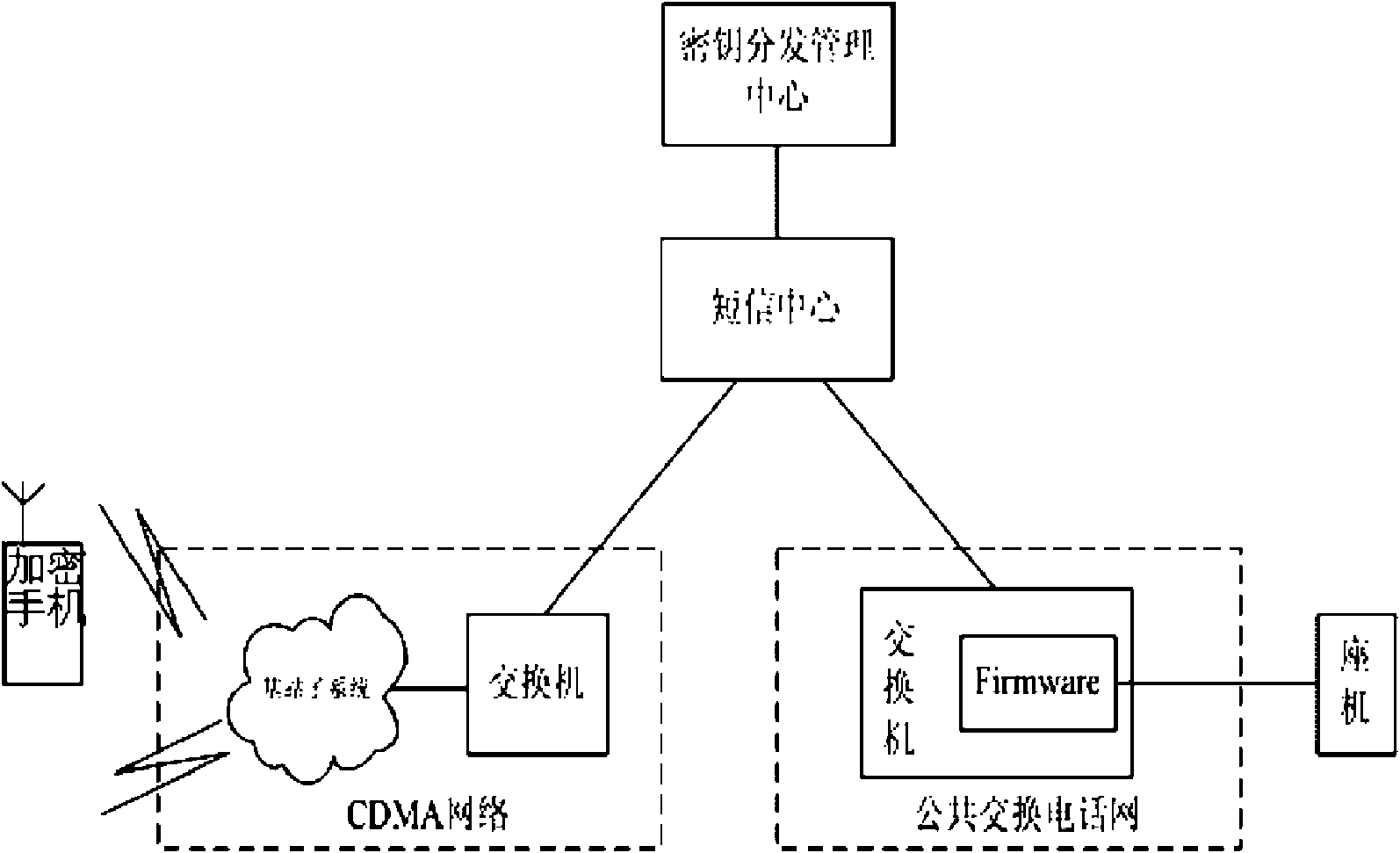
[0024] The system structure of this embodiment sees appendix figure 1 As shown, the key distribution management center server is deployed in a higher security domain in the CDMA communication network, and the short message center is connected to the key distribution management center server.
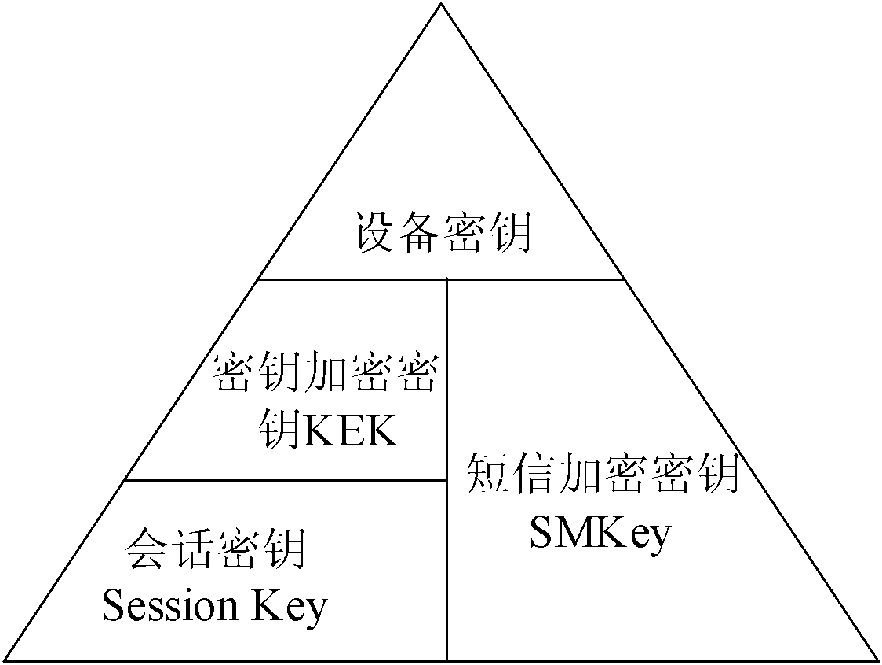
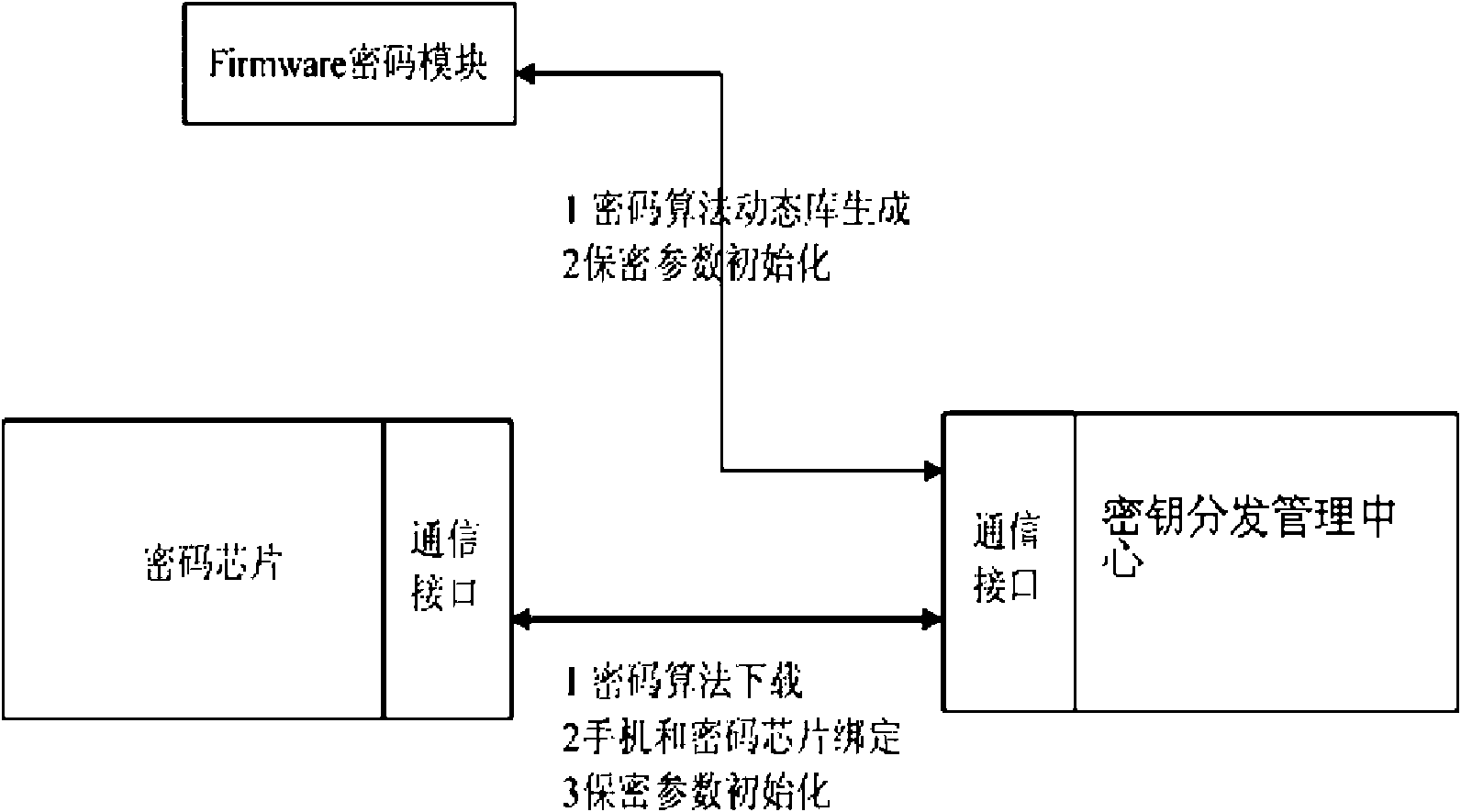
[0025] The three-tier management structure of key distribution is as follows: figure 2 As shown, the specific distribution method is as follows:
[...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com