Encrypting/decrypting system and encrypting/decrypting method for interactive network television
A network TV and encryption system technology, applied in the field of encryption/decryption system of interactive network TV, can solve problems such as algorithm security and intellectual property barriers, low strength of scrambling algorithm, inability to effectively resist violent attacks, etc., to provide security Sexuality and normativeness, resistance to violent attacks, and high computing efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0063] The above and other technical features and advantages of the present invention will be described in more detail below in conjunction with the accompanying drawings.
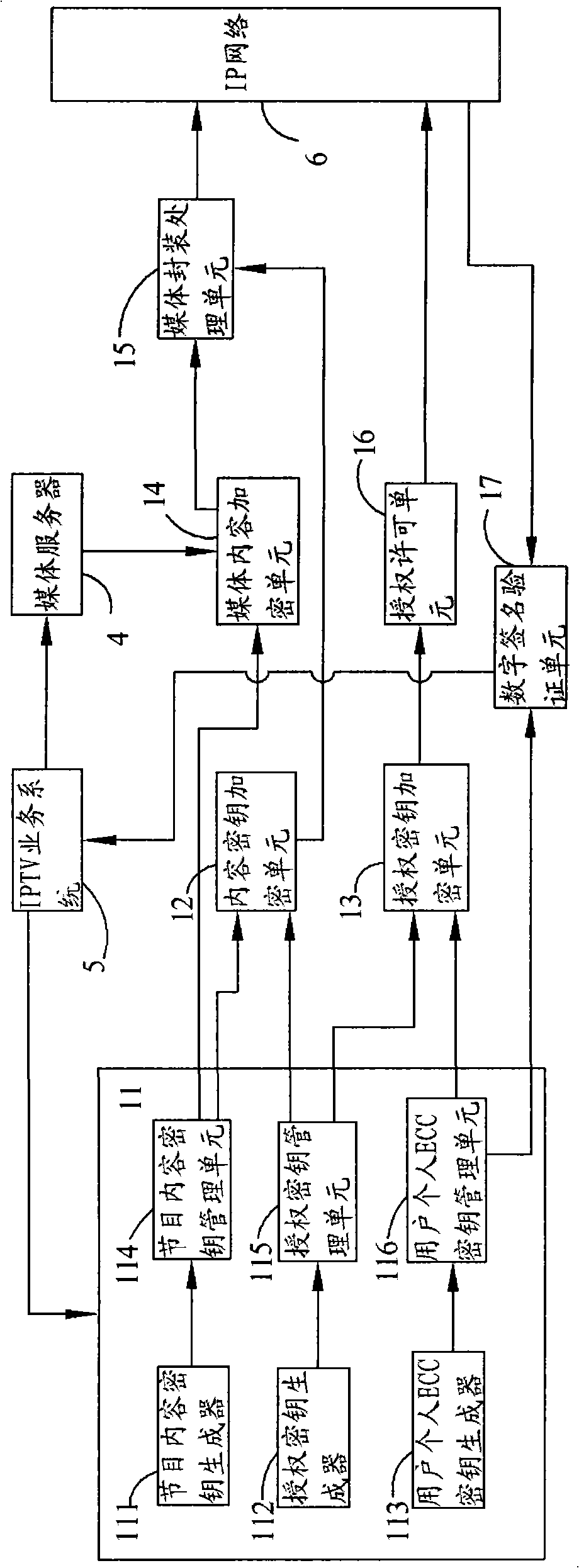
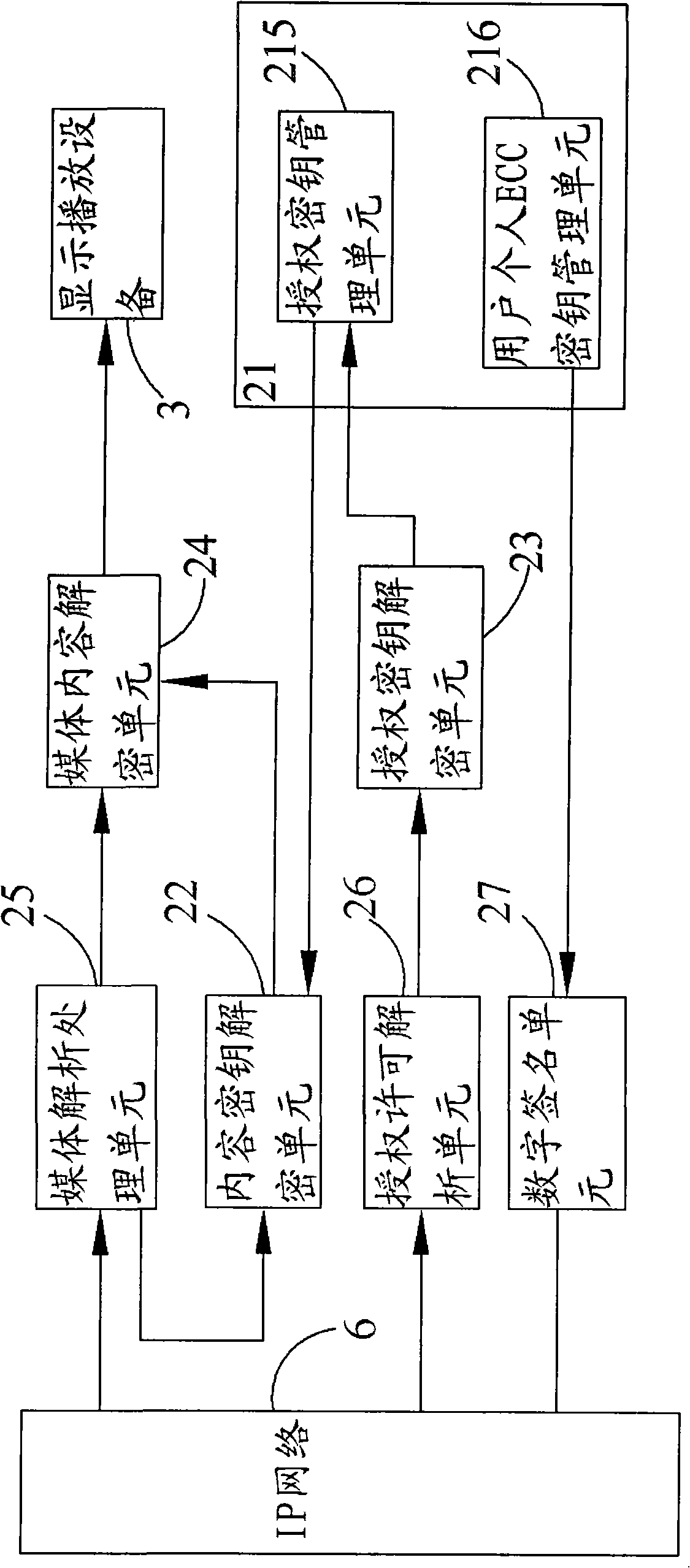
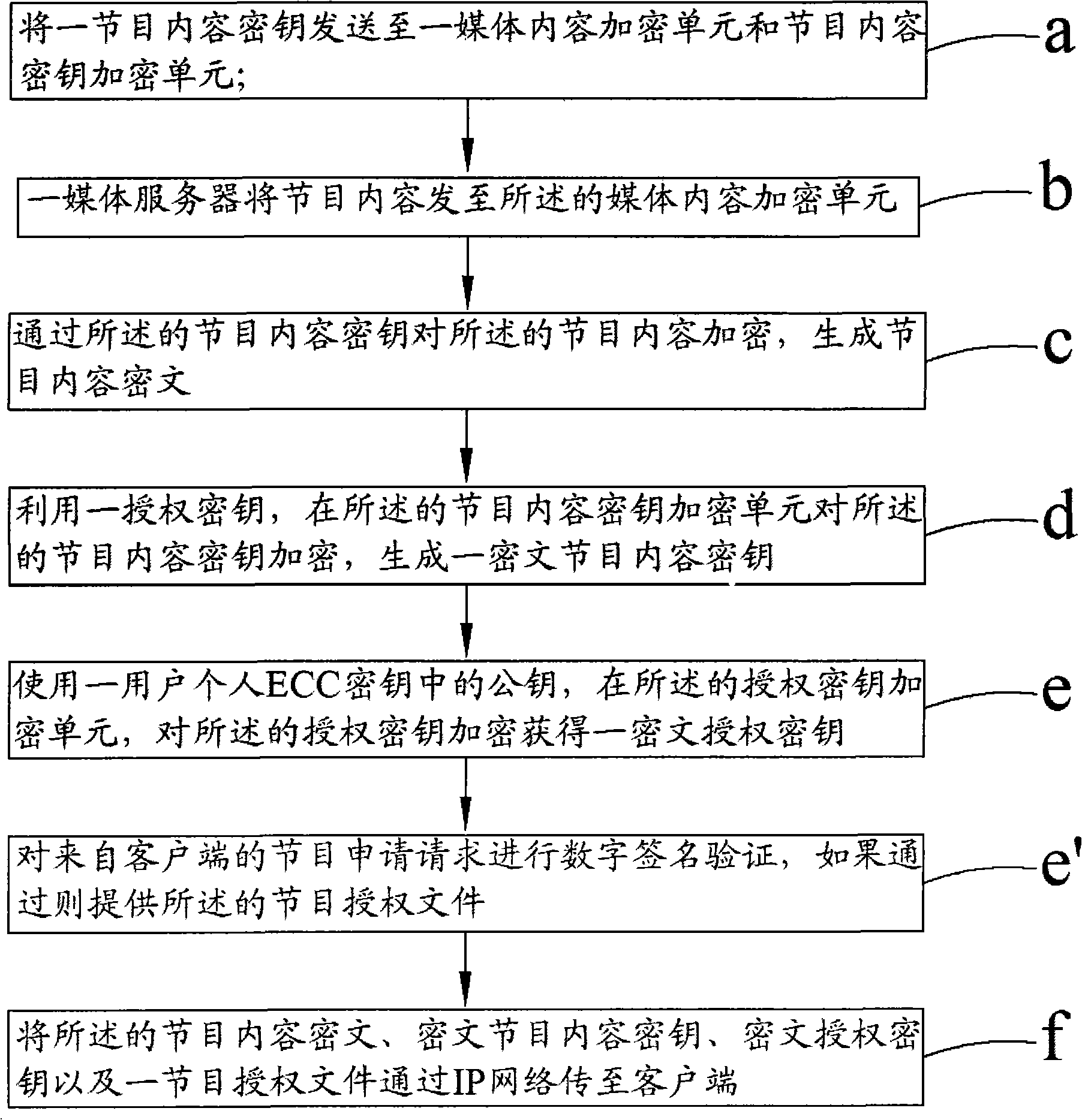
[0064] For the encryption and decryption system of interactive IP TV, we use the encryption algorithm approved by the national encryption management department, and adopt a secure three-layer key system, namely: program content key, authorization key, user's personal ECC key pair, As well as mature identity authentication technology, the security protection of the business system can not only solve the identity authentication problem of the system, but also realize the security protection of on-demand and live broadcast services. The symmetric block cipher algorithm (SM1) of the Cipher Administration is used, with a key length of 128bit, used to encrypt and decrypt program content.
[0065] The authorization key is used in conjunction with the symmetric block cipher algorithm (SM1) of the State Cryptograph...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com