Method for filtering and monitoring behavior of program
A technology for filtering programs and monitoring programs, applied in the field of computer security, can solve problems such as large manpower, high cost, and difficulty in promotion, and achieve the effects of reducing interference, reducing processing capacity, and improving accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
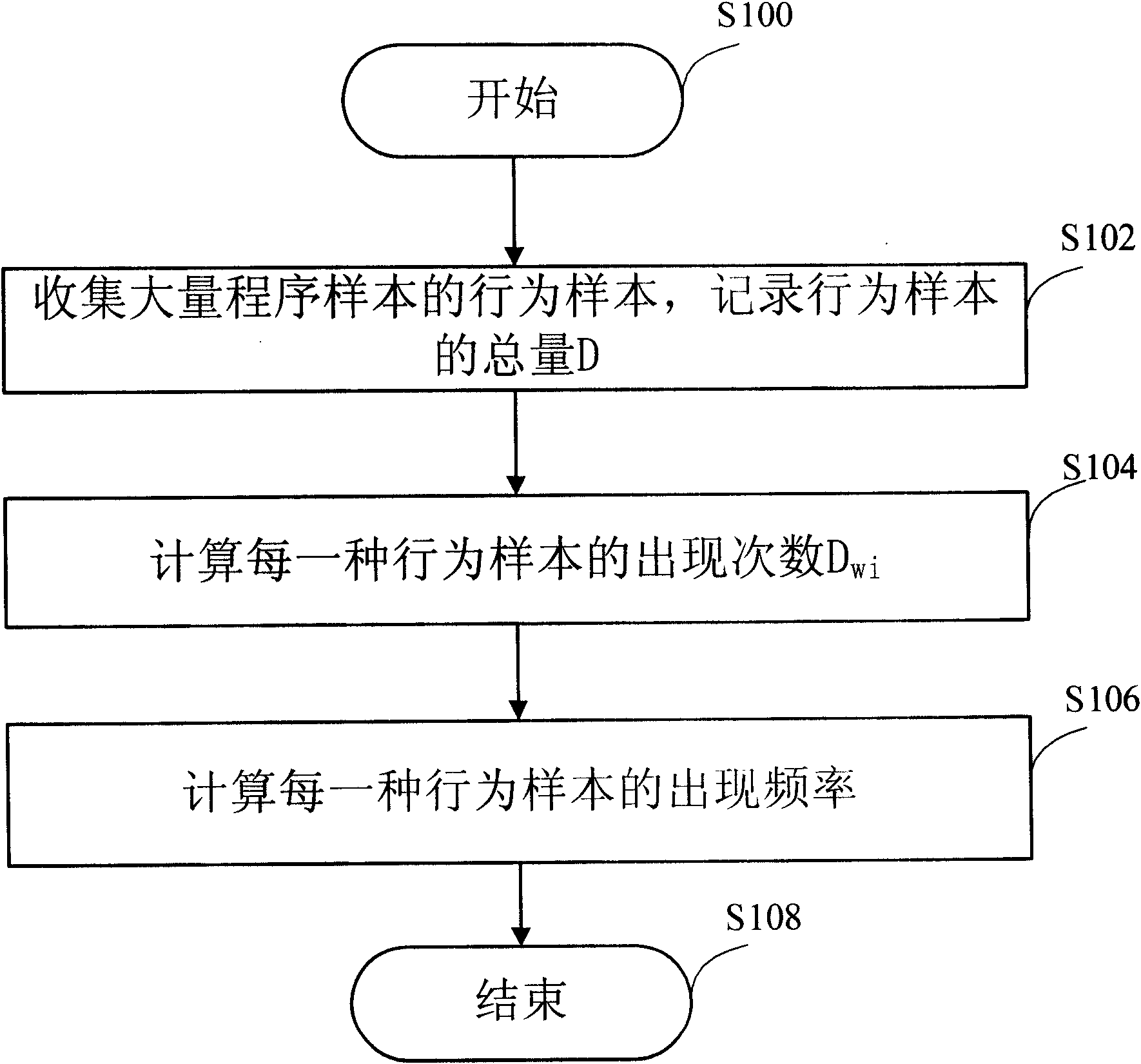
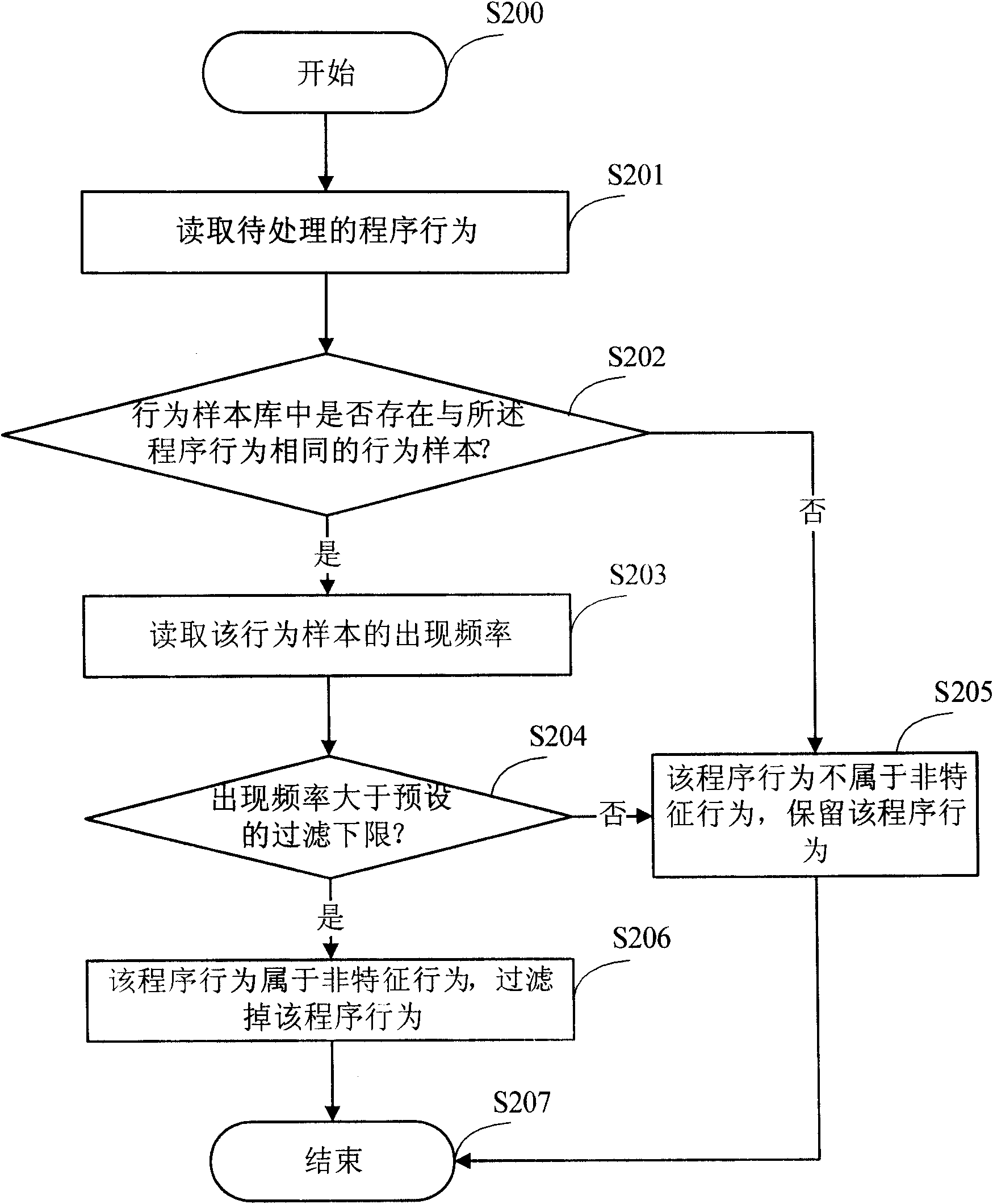
[0030] figure 1 Is a flowchart of constructing a behavior sample library in an embodiment of the present invention, figure 2 Is app figure 1 The flow chart of the behavior sample library for filtering the behavior of the program is shown.
[0031] Such as figure 1 As shown, after starting step S100, in step S102, the behaviors of a large number of program samples are collected to obtain a large number of behavior samples, and the total amount D of the collected behavior samples is recorded. According to statistical principles, the larger the sample size, the closer to the true value the statistical results obtained. Therefore, in the process of constructing the behavior sample library, it is preferable to collect as many behavior samples of the program samples as possible. Those skilled in the art should be aware that, with the existing technology, the behavior of a large number of program samples can be collected by means of setting intercept points, such as file read and wri...
Embodiment 2
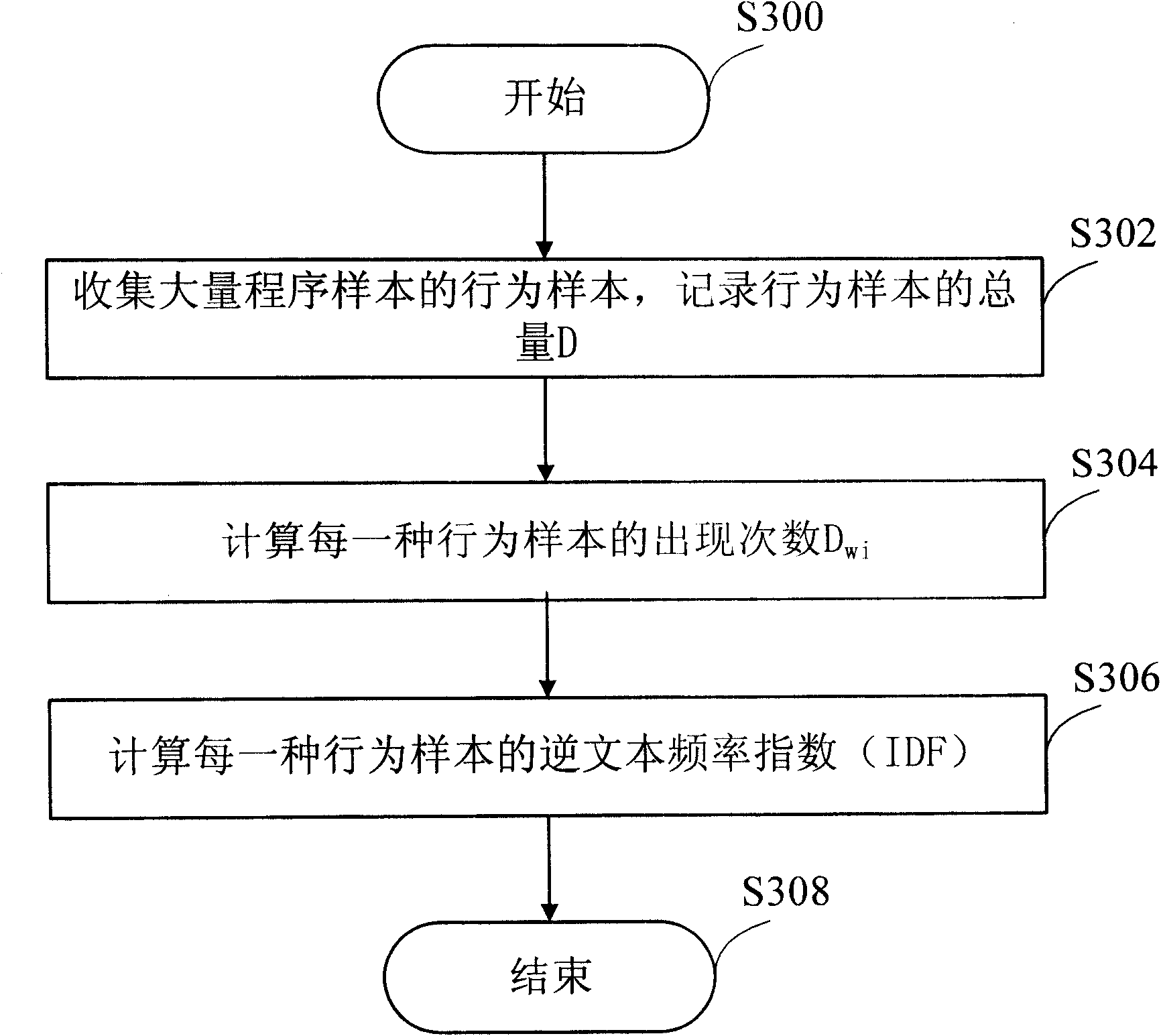
[0043] image 3 Is a flowchart of constructing a behavior sample library in another embodiment of the present invention; Figure 4 Is app image 3 The flow chart of the behavior sample library for filtering the behavior of the program is shown.
[0044] image 3 The flow of the construction behavior sample library shown and figure 1 The construction process shown is similar. More specifically, image 3 The steps S300 to S304 shown are and figure 1 The steps S100 to S104 shown are the same. They are the starting step, collecting a large number of behavior samples and recording the total amount D of behavior samples, and calculating the number of occurrences D of each behavior sample. wi .
[0045] Next, in step S306, the inverse text frequency index (IDF) of each behavior sample is calculated. As mentioned above, the inverse text frequency index is recognized as an important parameter for measuring relevance and value. The inverse text frequency index IDF(i) of the i-th behavio...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com