Data sharing and access control method based on Xen
A technology for data sharing and access control, applied in the direction of input/output to record carriers, etc., can solve problems such as inappropriateness, limited data volume, data sharing flexibility and security risks, and achieve easy implementation, high security, and guaranteed safety effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0024] The present invention will be further described below in conjunction with the accompanying drawings.
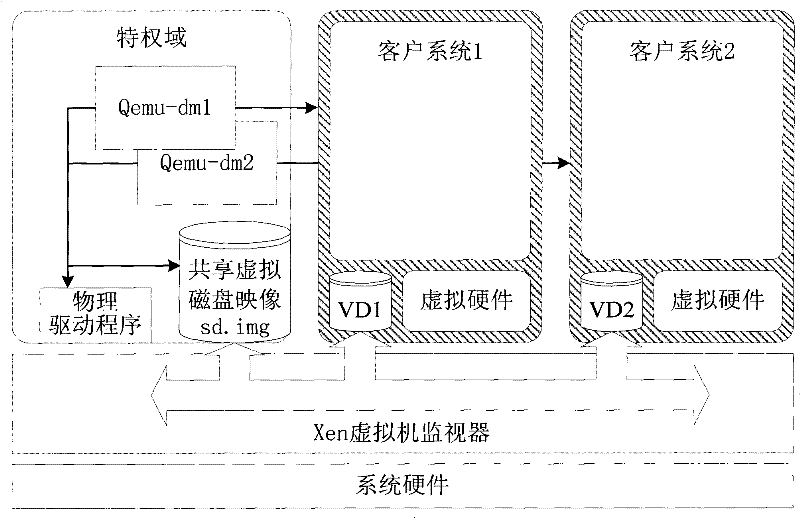
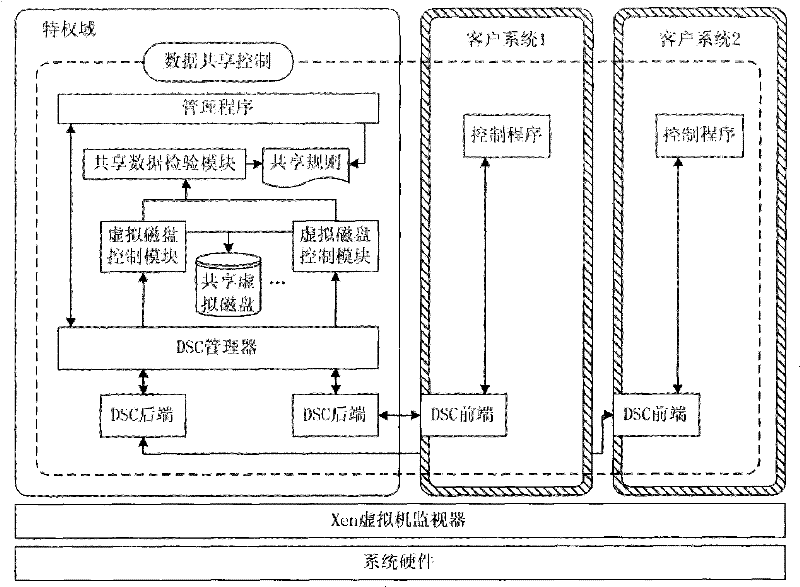
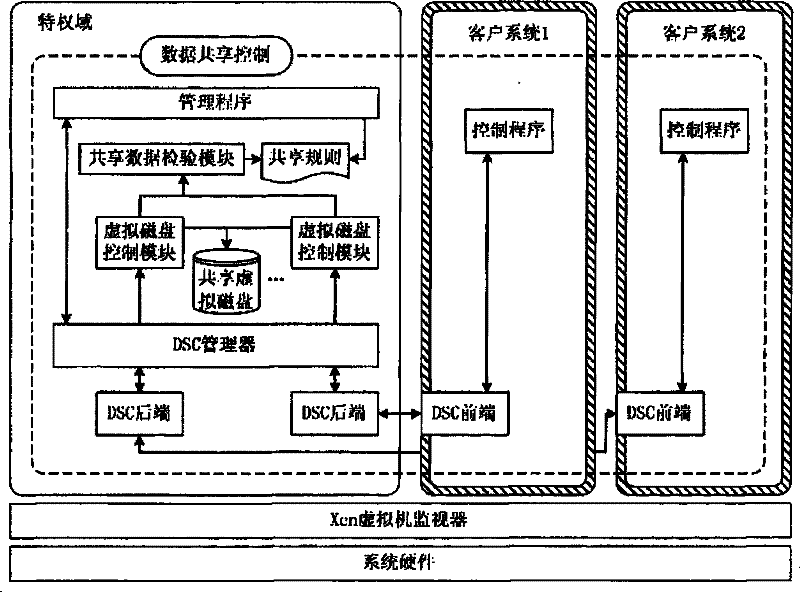
[0025] Such as figure 1 As shown, the basic framework of the present invention is that a plurality of client systems have the same image file existing in the host system as its virtual disk, that is, the data sharing system; figure 2 All modules of the invention shown: client system, data sharing system, access control module, virtual disk control module.
[0026] The data sharing system is the basic condition for the implementation of the present invention, and is composed of multiple configured full virtualization client systems and disk image files that exist in Domain0 (i.e. the Xen host system). Each client system includes not only the necessary disks for system operation, but also the disks provided by this machine as the owner to share data with other client systems, and the disks that this machine serves as sharers to share data with other client systems.
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com