Method and device for protecting user privacy
A user and privacy technology, applied in computer security devices, internal/peripheral computer component protection, instruments, etc., can solve problems such as user privacy threats
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0016] At present, the operation of the widely used computer operating system can be divided into user mode and kernel mode. In the user mode, processing requests from external user programs, etc., is equivalent to the third ring (Ring 3) in the computer three-ring protection model, which has the lowest authority level. In the kernel mode, execute system kernel component functions, and finally respond to external user program requests through the execution of system kernel functions, etc. This corresponds to the zeroth ring (Ring 0) in the computer's three-ring protection model, which has the highest authority level .
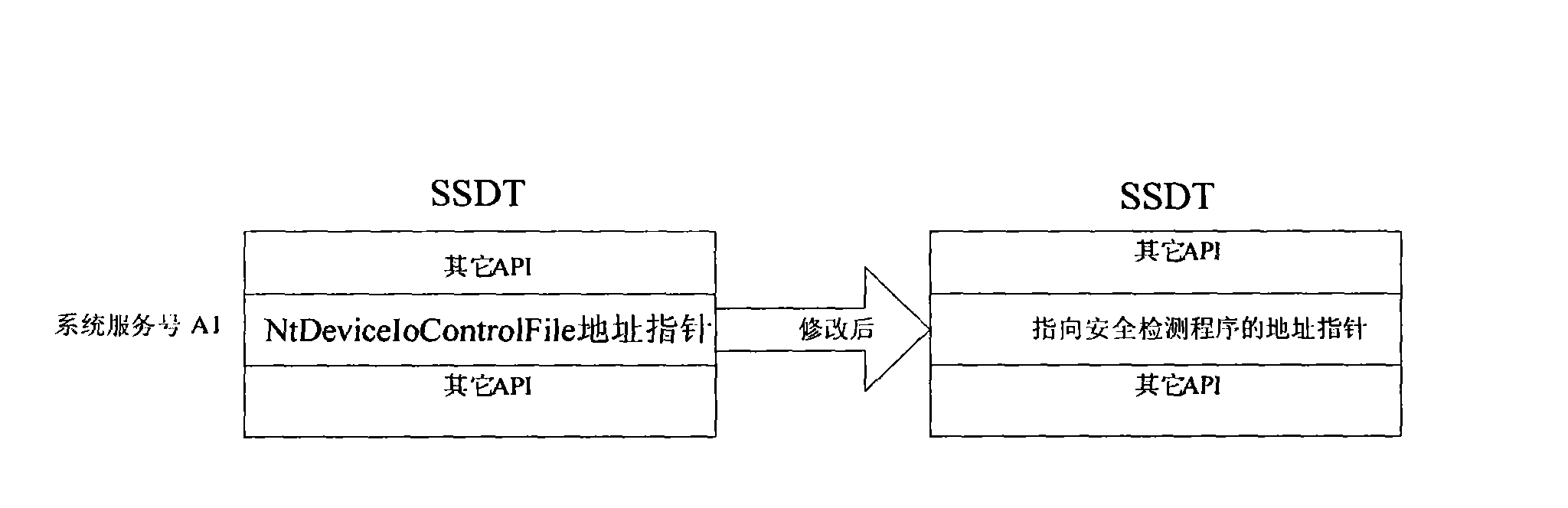
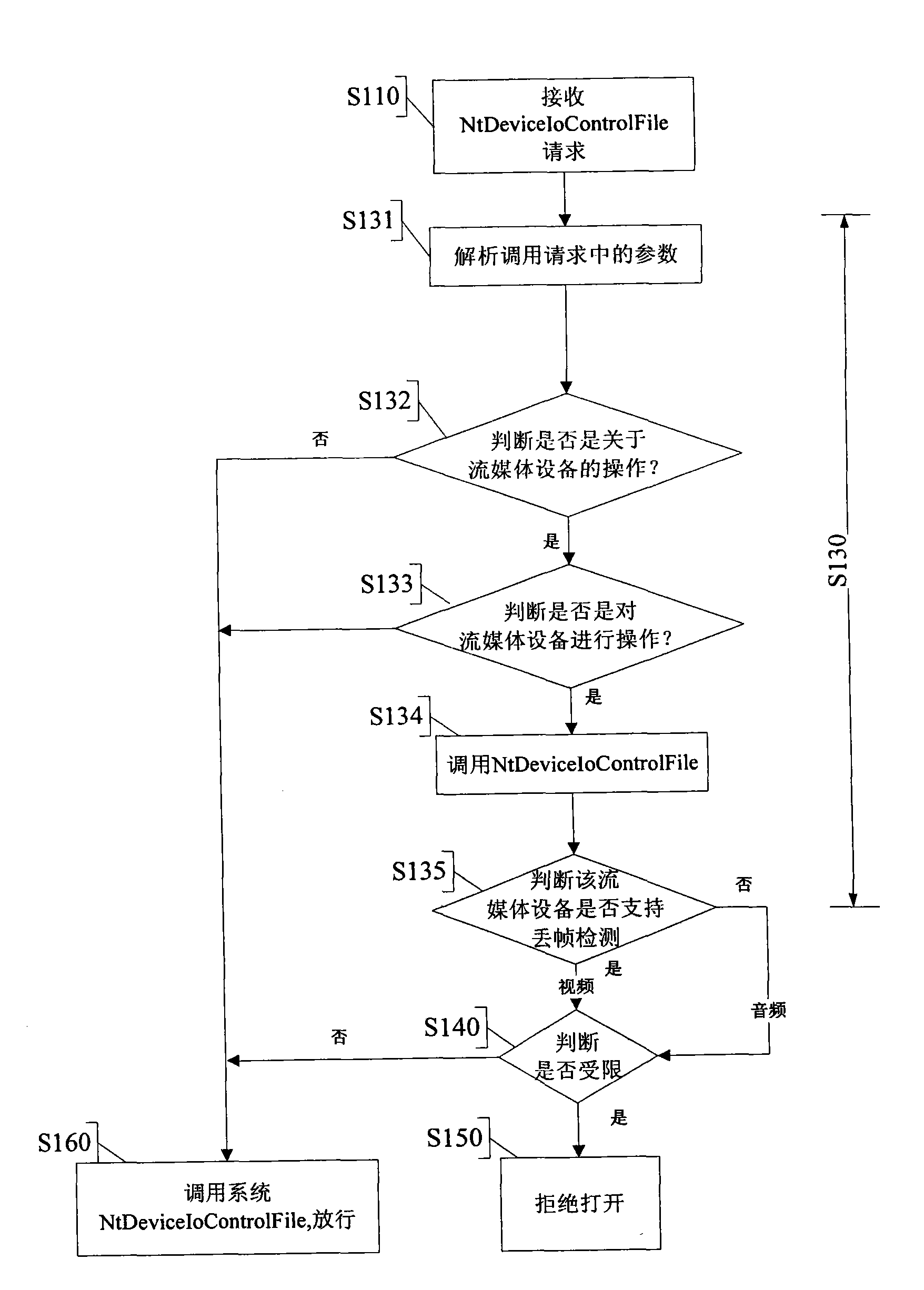
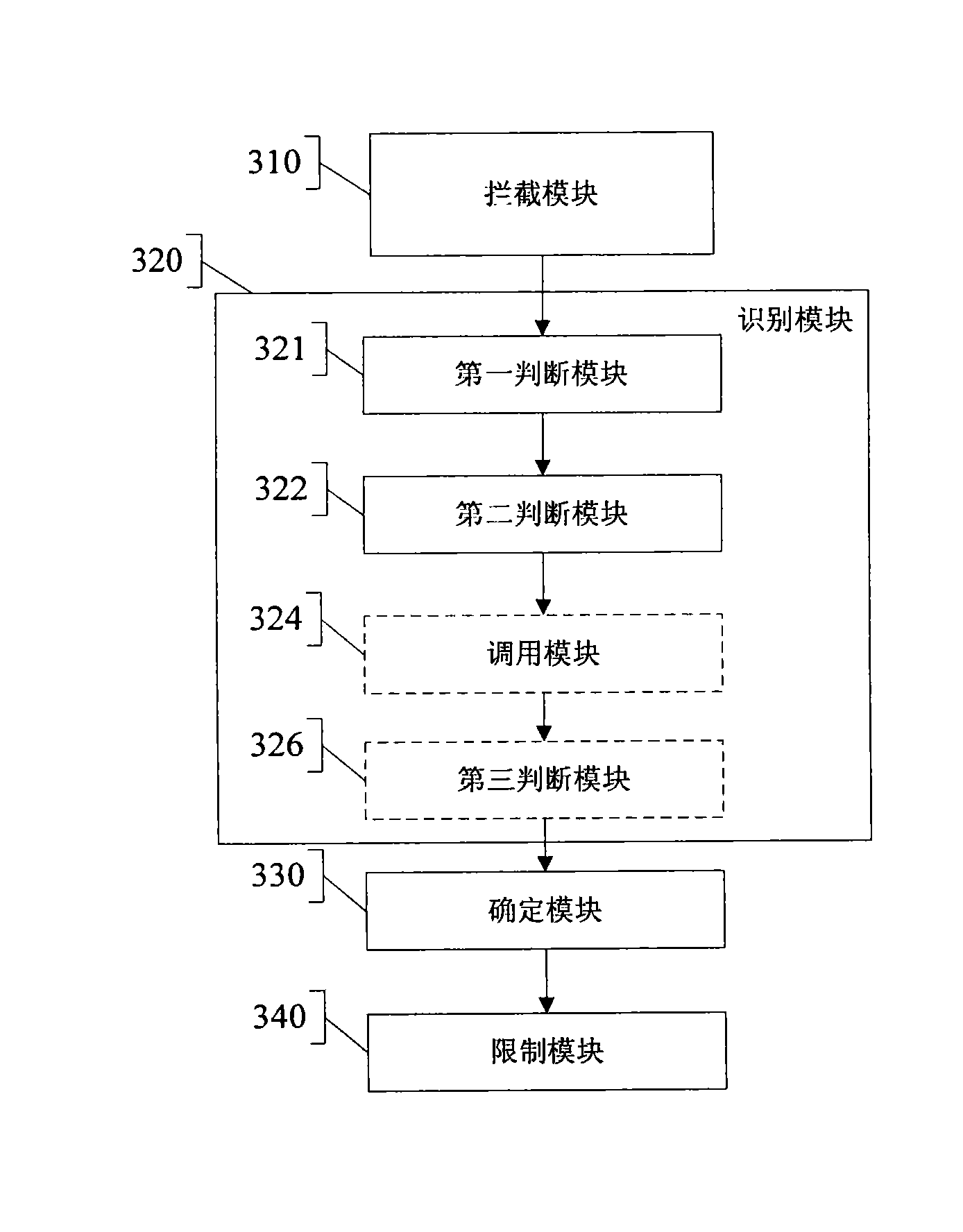
[0017] Through the analysis of the system, an embodiment of the present invention proposes: by hooking the system service description table (SSDT table), in the system kernel mode, intercepting the user program to open the streaming media device (such as a camera or a microphone) Actions to achieve controlled access to streaming media devices in the highest autho...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com