Dynamic cross-domain access control method based on trust valuation mechanism
An access control and dynamic technology, applied in digital transmission systems, electrical components, transmission systems, etc., to solve problems such as security loopholes, unreasonable authorization, and implementation difficulties
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
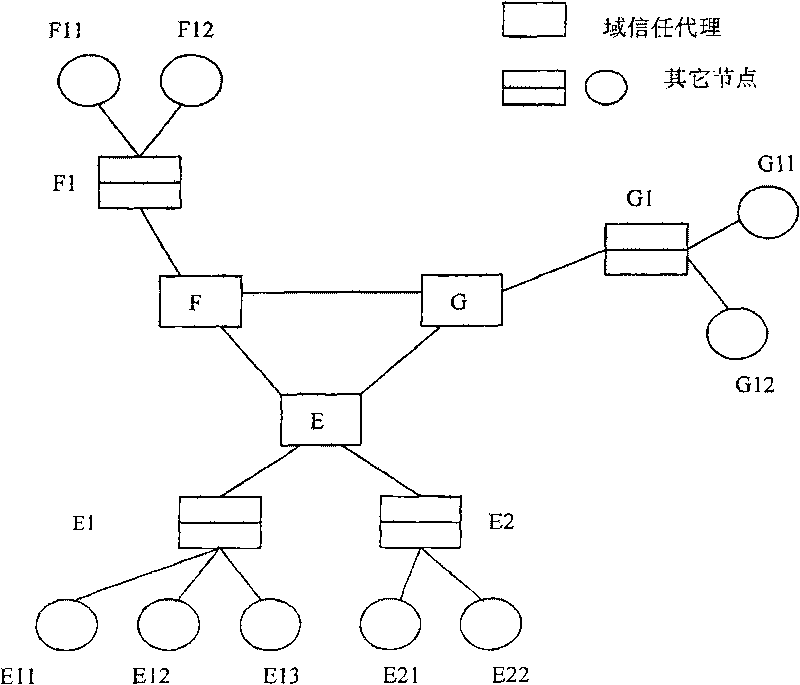
[0167] Example 1: User E11 requests to download the file presentation.ppt:
[0168] First, judge whether the access user E11 is a legal user of the grid. If the user is not a legal user of the grid, the judgment result is returned to the client, and the visit is terminated. If the user is a legal user of the grid, the user submits a request for downloading the file presentation.ppt to the domain trust agent E. The domain trust agent E invokes the entity reputation value table, determines that the user has the right to access this resource, and returns the entities E12 and E22 that have this resource.
[0169] Because entities E12 and E22 with this resource are located in the same domain D as this user E , at this time, the method for determining the trust degree of access control in the domain is called to calculate the trust degree of the user and the entities E12 and E22 respectively, where the trust weight factor β=0.5. The user's trust degree to E12 is greater than its ...
example 2
[0170] Example 2: User E requests to download the file analysis.dll:
[0171] First, it is judged whether the visiting user E is a legal user of the grid. If the user is not a legal user of the grid, the judgment result is returned to the client, and the visit is terminated. If the user is a legal user of the grid, the user submits a request for downloading the file analysis.dll to the domain trust agent. The domain trust agent invokes the entity reputation value table, determines that the user’s entity reputation value is T3, and the role is T3, and determines that the user has the authority to download resources in the grid. According to the user’s request for downloading the file analysis.dll, the domain trust agent, Return all entities F, G that have this resource;
[0172] Since all entities that own this resource are in different domains from this user, the method for determining the trust degree of inter-domain access control is called to calculate user E and domain D...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com