Method and device for restricting remote access of switcher
A remote access and switch technology, applied in the field of network data communication, can solve problems such as waste of computing resources, achieve fast search speed, flexible implementation, and reduce CPU traffic
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
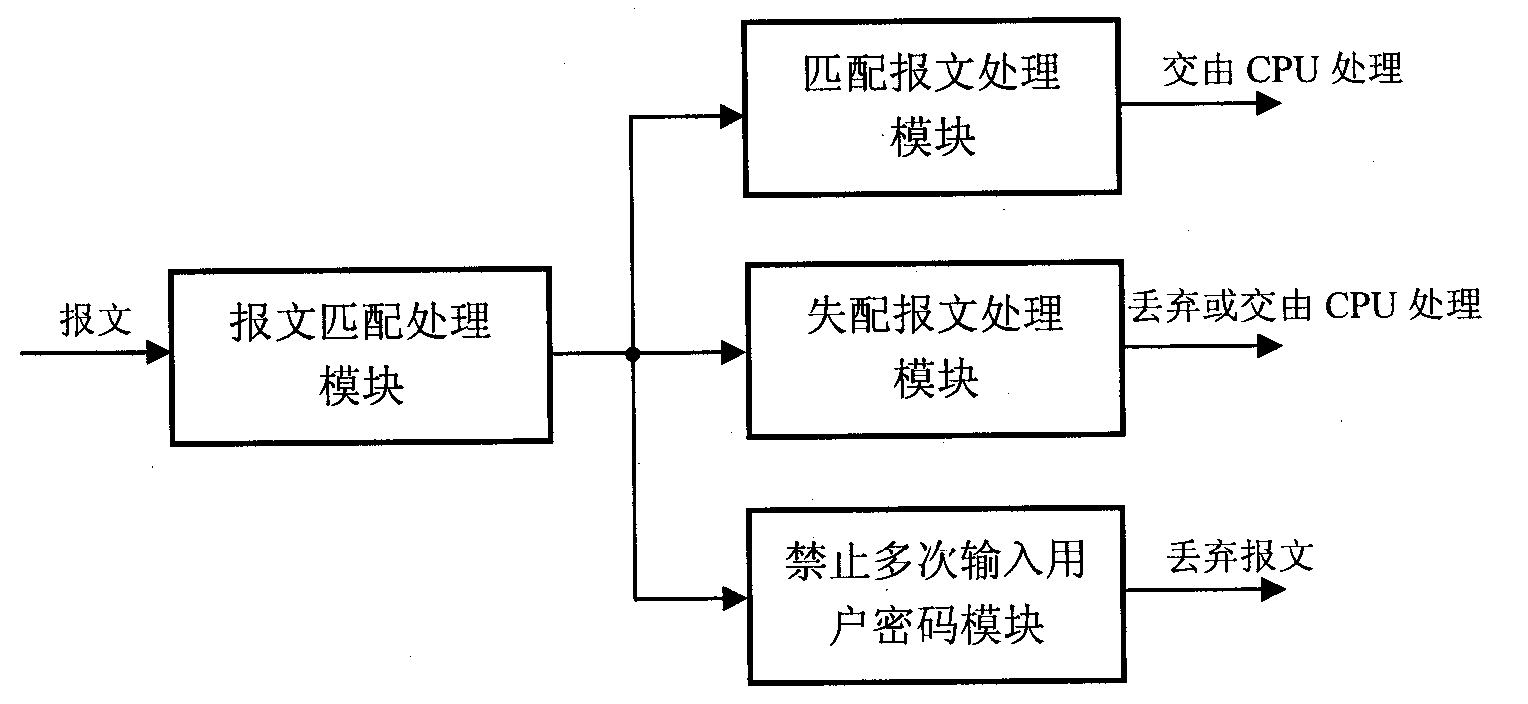
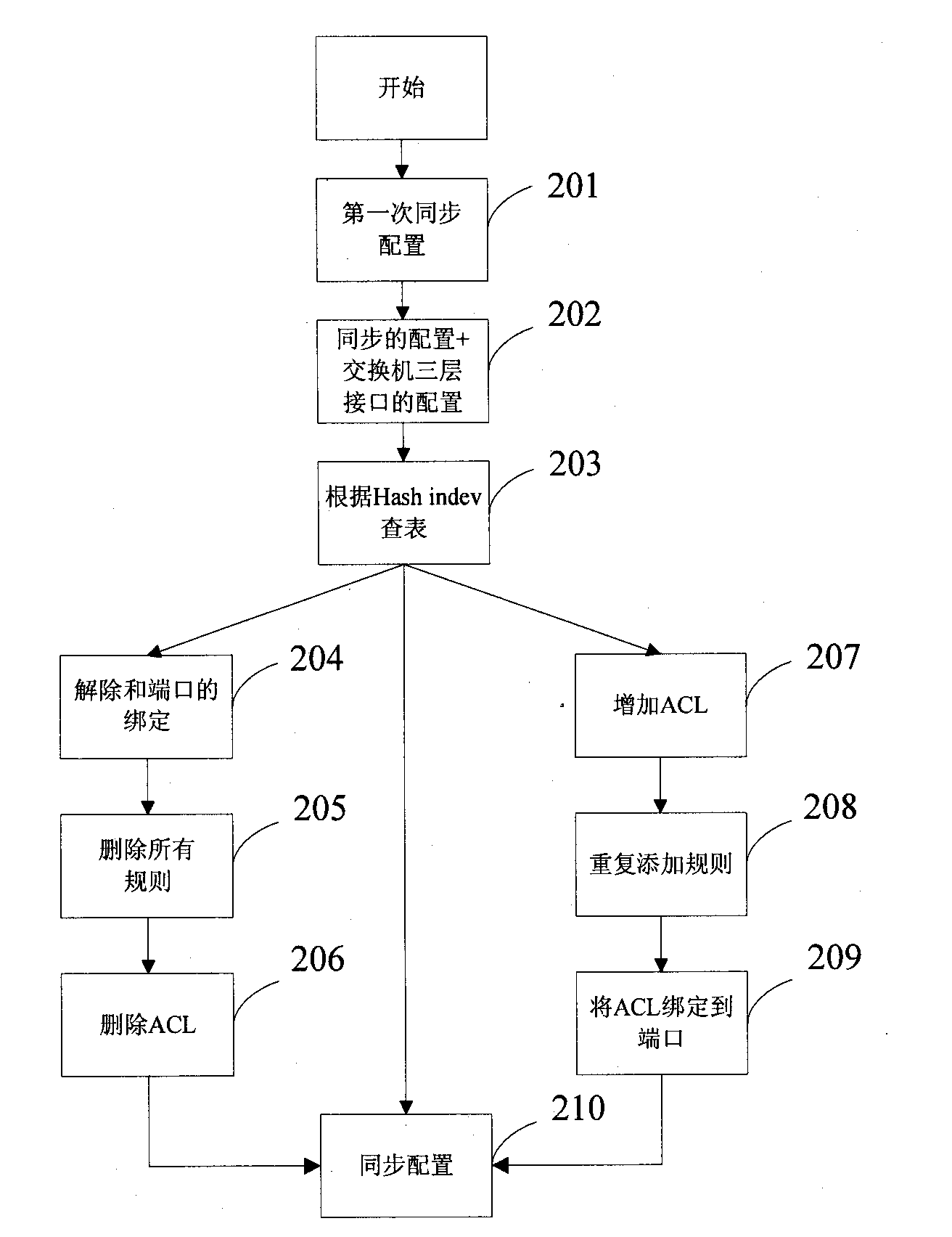
[0033] figure 1 The device for restricting the remote access of the switch by the global ACL of the present invention is shown, including:
[0034] The matching processing module is used to use the first ACL of the switch to perform matching processing on the data packet message received by the predetermined port of the switch;
[0035] The matching data packet message processing module is used to hand over the matching data packet message whose content of the data packet message is exactly the same as the field configured in the first ACL to be processed by the switch CPU;
[0036] Mismatched data packet message processing module, used to send the mismatched data packet message whose content of the data packet message is different from the field configured in the first ACL to the global ACL effective on all ports of the switch for discarding or send it to the switch CPU processing.
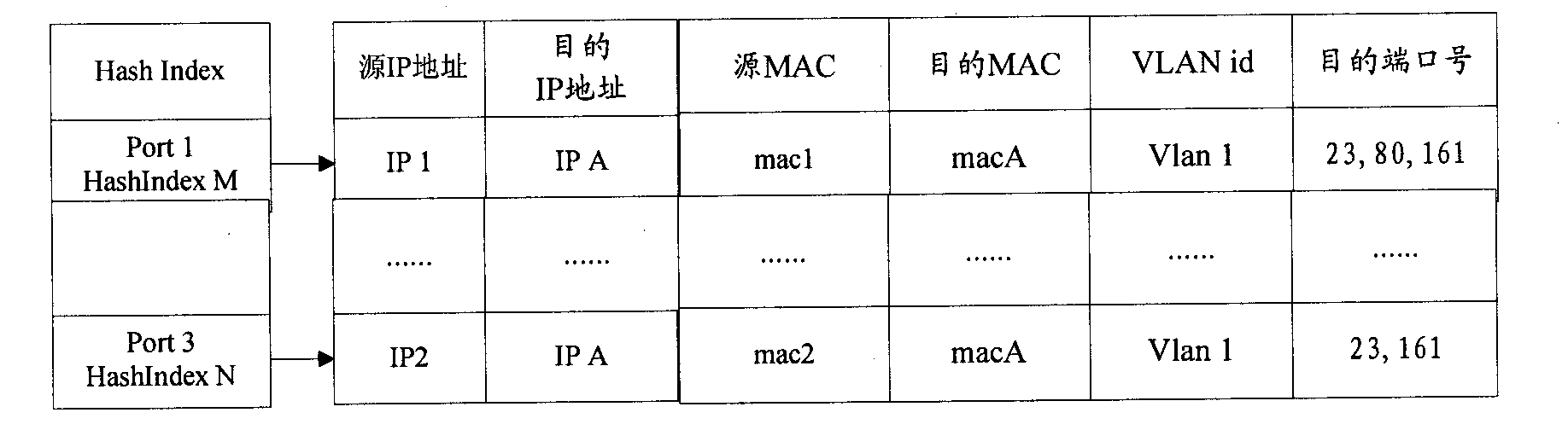
[0037] The first ACL and the global ACL are saved in the Hash storage table of the switch, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com