IC (Integrate Circuit) card access terminal adopting commercial cipher and operation method thereof
A commercial cryptographic algorithm and commercial cryptographic technology, applied in the field of IC card access control terminals, can solve the problems of no key and inability to interpret information, and achieve the effects of easy management, removal of security threats, and security benefits
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
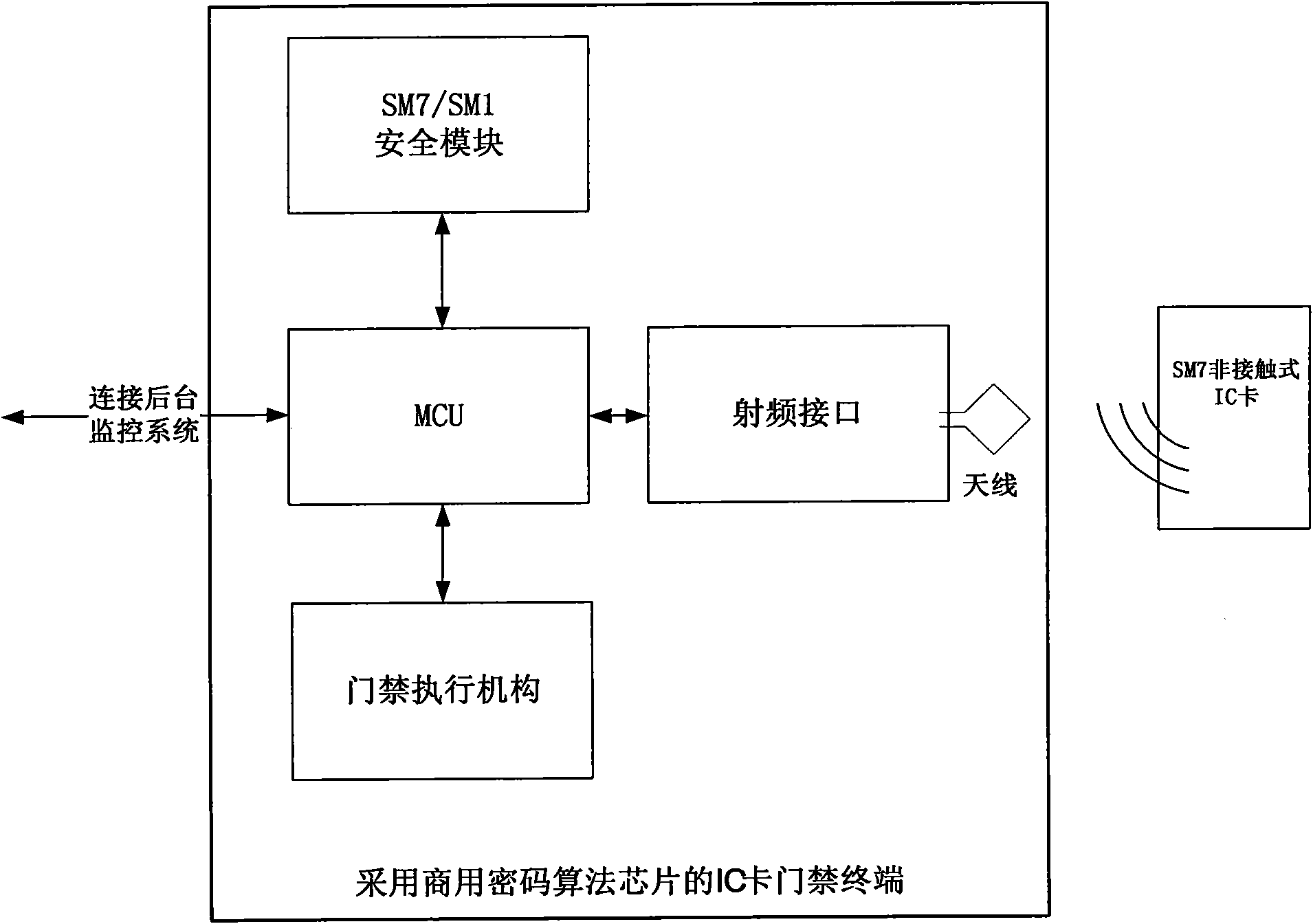
[0047] see figure 1 , the present invention is an IC card access control terminal using a commercial SM7 / SM1 cryptographic module (SAM). MCU is its core component, adopts a 32-bit single-chip microcomputer system, has 512KFalsh / 64KRAM, and has a variety of multi-channel communication interfaces built in. The access control terminal program developed by Shanghai Integrated Communication Equipment Co., Ltd. manages each component of the access control terminal under the control of these programs. The memory in the MCU stores the running program and the latest batch of access control events and alarm information.
[0048] The cryptographic module with commercial cryptographic algorithm is the core of security control in the access control terminal. It contains the 128-bit SM7 block cipher algorithm and SM1 block cipher algorithm designated by the State Cryptography Administration, and stores the system root key. Under the management of MCU, it is responsible for completing SM1 ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com