Method and device for detecting Trojans by analyzing network behaviors
A Trojan horse program and behavior technology, applied in the field of network security, can solve problems such as undetectable, achieve good compatibility and adaptability, and good detection effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
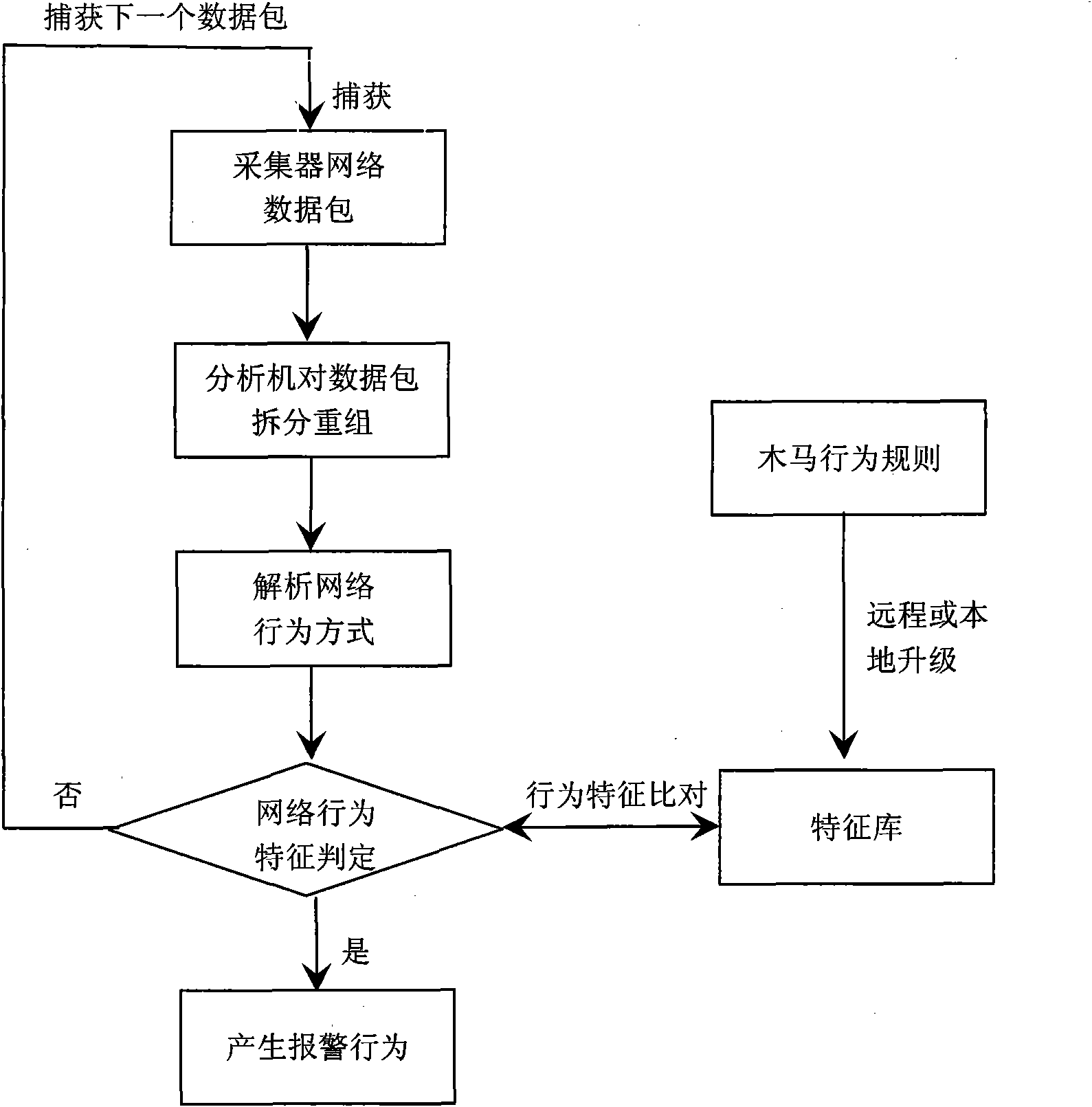
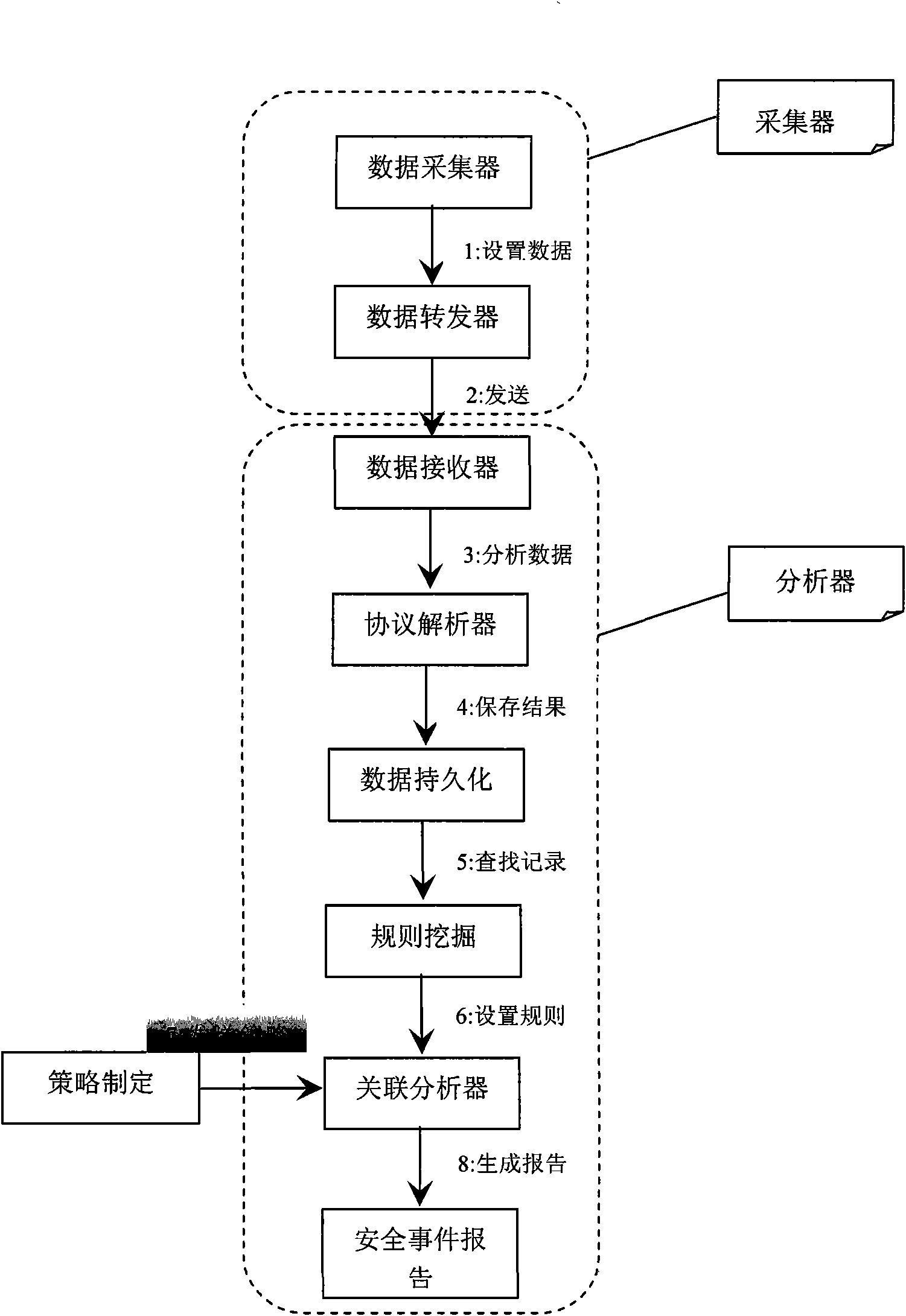
[0043] The present invention will be further illustrated by the following application examples.
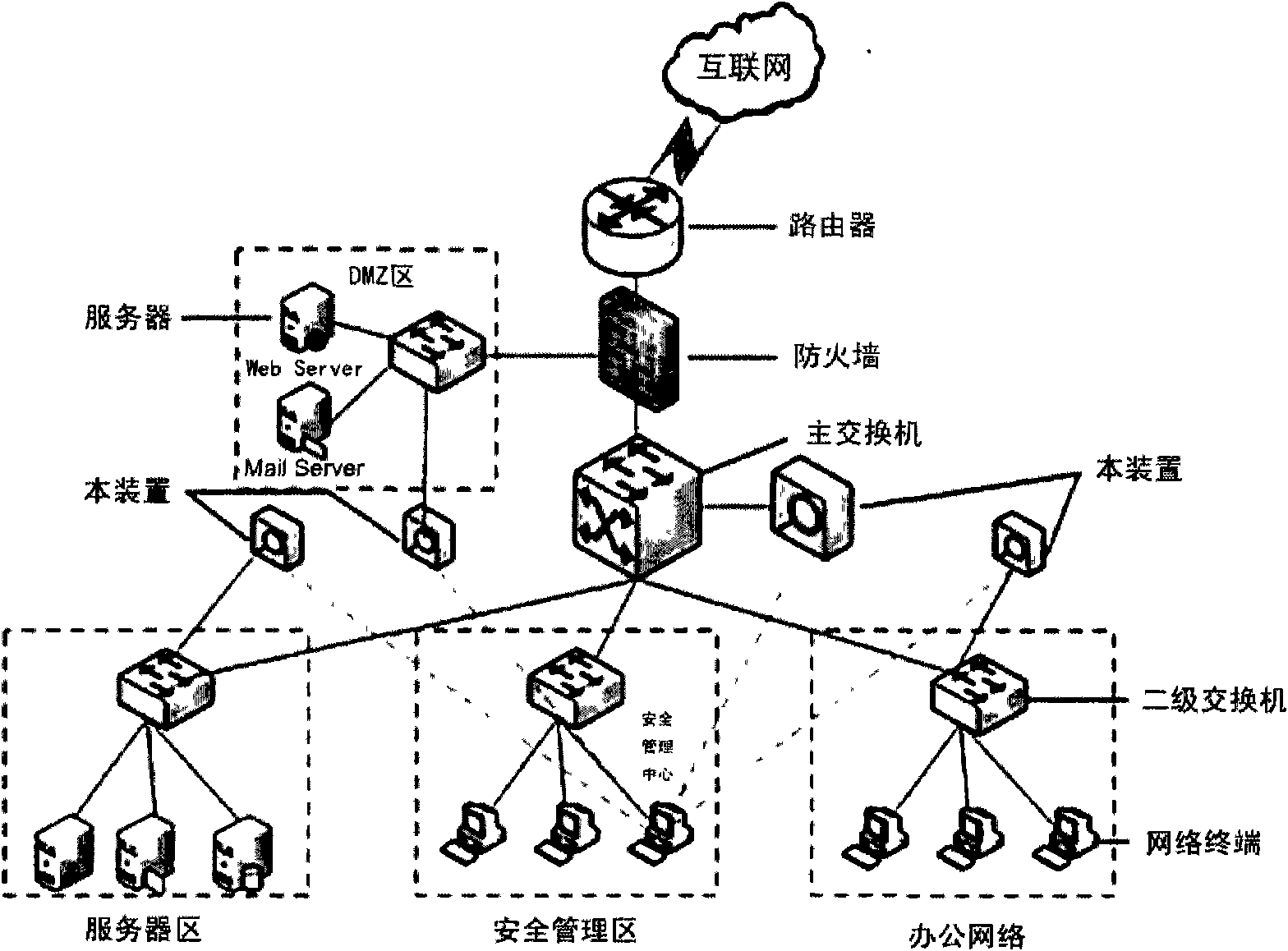
[0044] attached image 3 It is a schematic diagram of an application example of the present invention, and the device shown in the figure is the device described in the present invention.
[0045] The device (system) of the present invention adopts a bypass connection mode to access the network, is deployed at the entrance and exit of the network, and conducts comprehensive monitoring of all information flows in and out of the Internet in the entire network. The bypass connection mode can reduce the single point of failure and ensure the availability of the system.
[0046] Multiple monitoring is realized by deploying the device (system) of the present invention in multiple key network segments (such as security management area, DMZ area, server area and office area). Use the system security center to centrally manage multiple network detectors, which is convenient for centraliz...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com