Cloned subscriber identity module card test method and system
A user identification module, card detection technology, applied in network data management, security devices, electrical components, etc., can solve the problems of consuming a lot of manpower and energy, loss of operators and mobile users, etc., and achieve the effect of saving labor costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
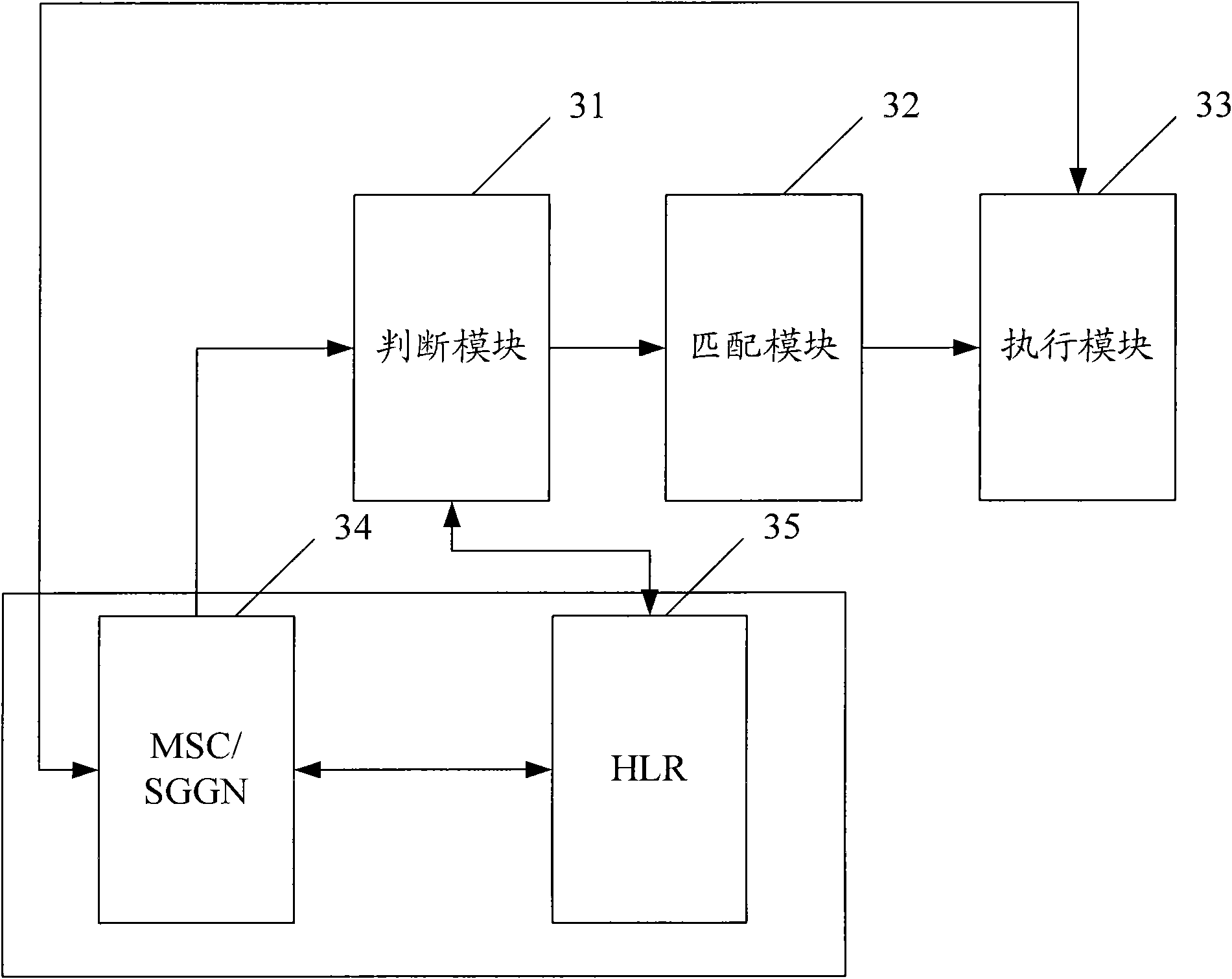
Image
Examples
Embodiment Construction
[0025] The present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments.
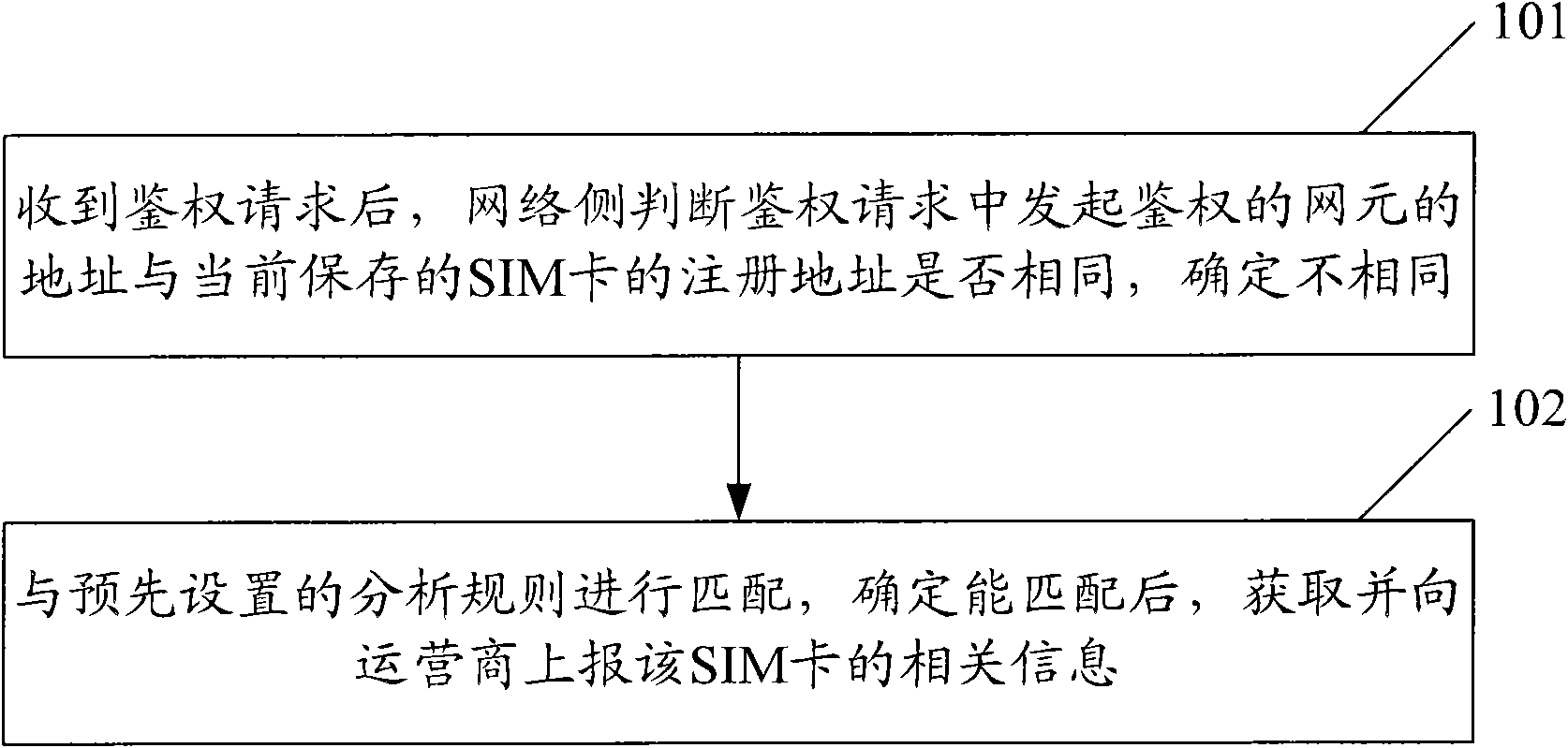
[0026] The detection method of cloning SIM card of the present invention, as figure 1 shown, including the following steps:
[0027] Step 101: After receiving the authentication request, the network side judges whether the address of the network element initiating the authentication in the authentication request is the same as the registered address of the currently saved SIM card, and if it is determined that they are not the same, execute step 102;
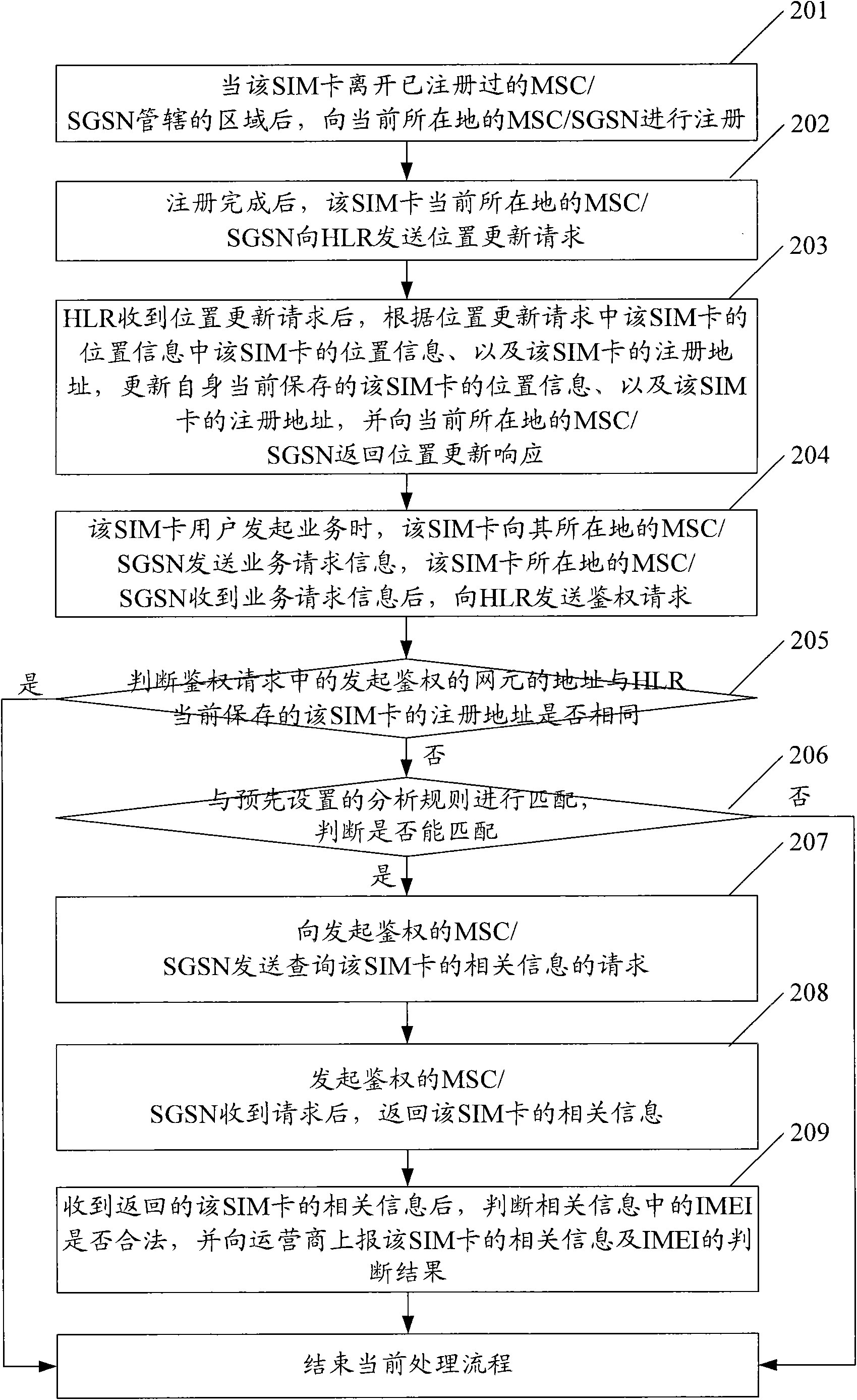
[0028] Here, the timing of receiving the authentication request is: when the SIM card initiates a service, the Mobile Switching Center (MSC) / Serving General Packet Radio Node (SGSN) at the SIM card location sends the authentication request to the Home Location Register (HLR); The network side includes network equipment such as MSC / SGSN and HLR. Wherein, the service initiated by the SI...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com