Program control flow deep confusion method based on labels
A deep and tagged technology, applied in the field of deep obfuscation of program control flow, can solve the problems of in-depth program control flow analysis, poor program performance, program confusion, etc., achieve good obfuscation effect, low overhead, and improve security and privacy effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
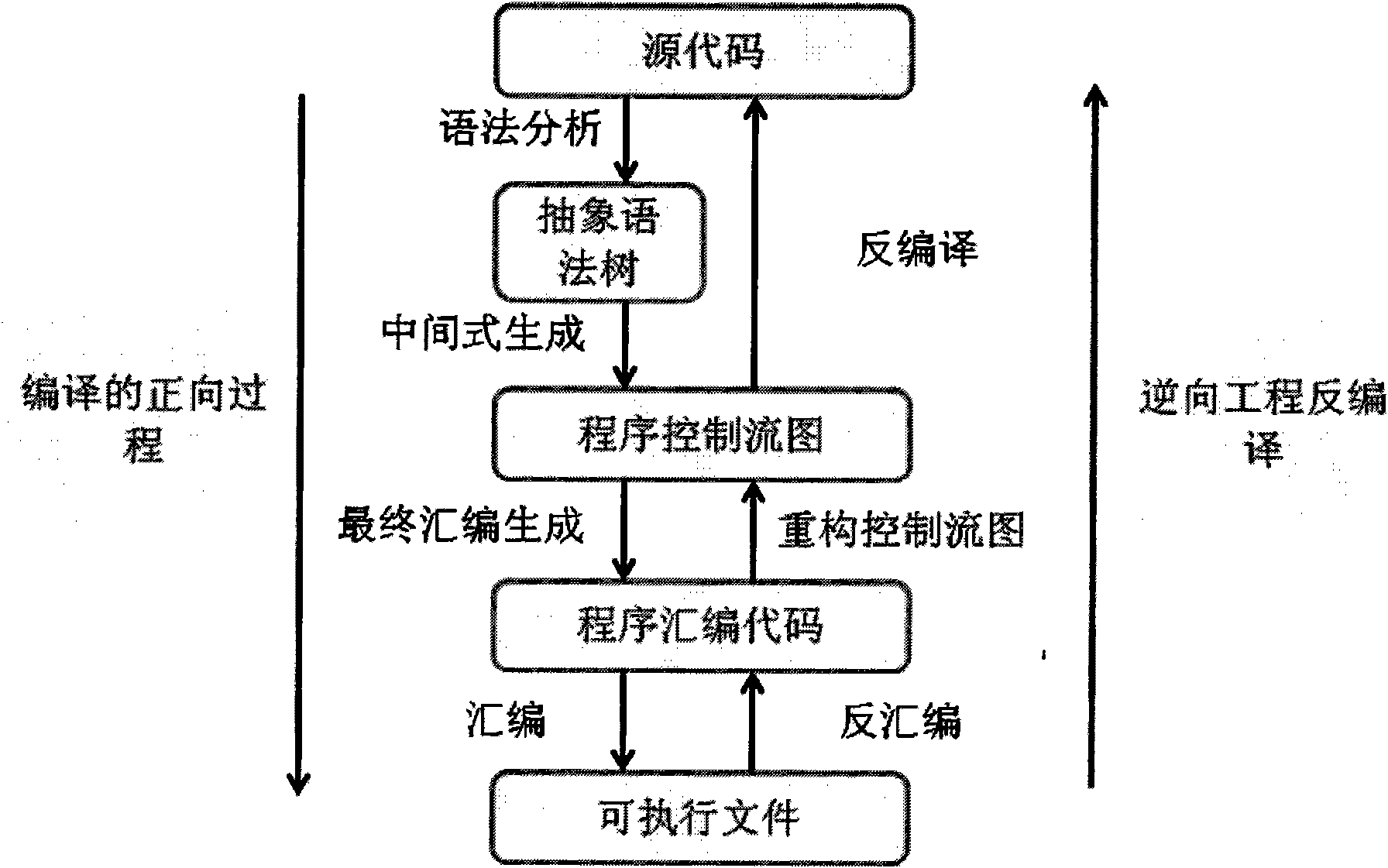
[0016] The present invention will be further described below in conjunction with the accompanying drawings and embodiments.
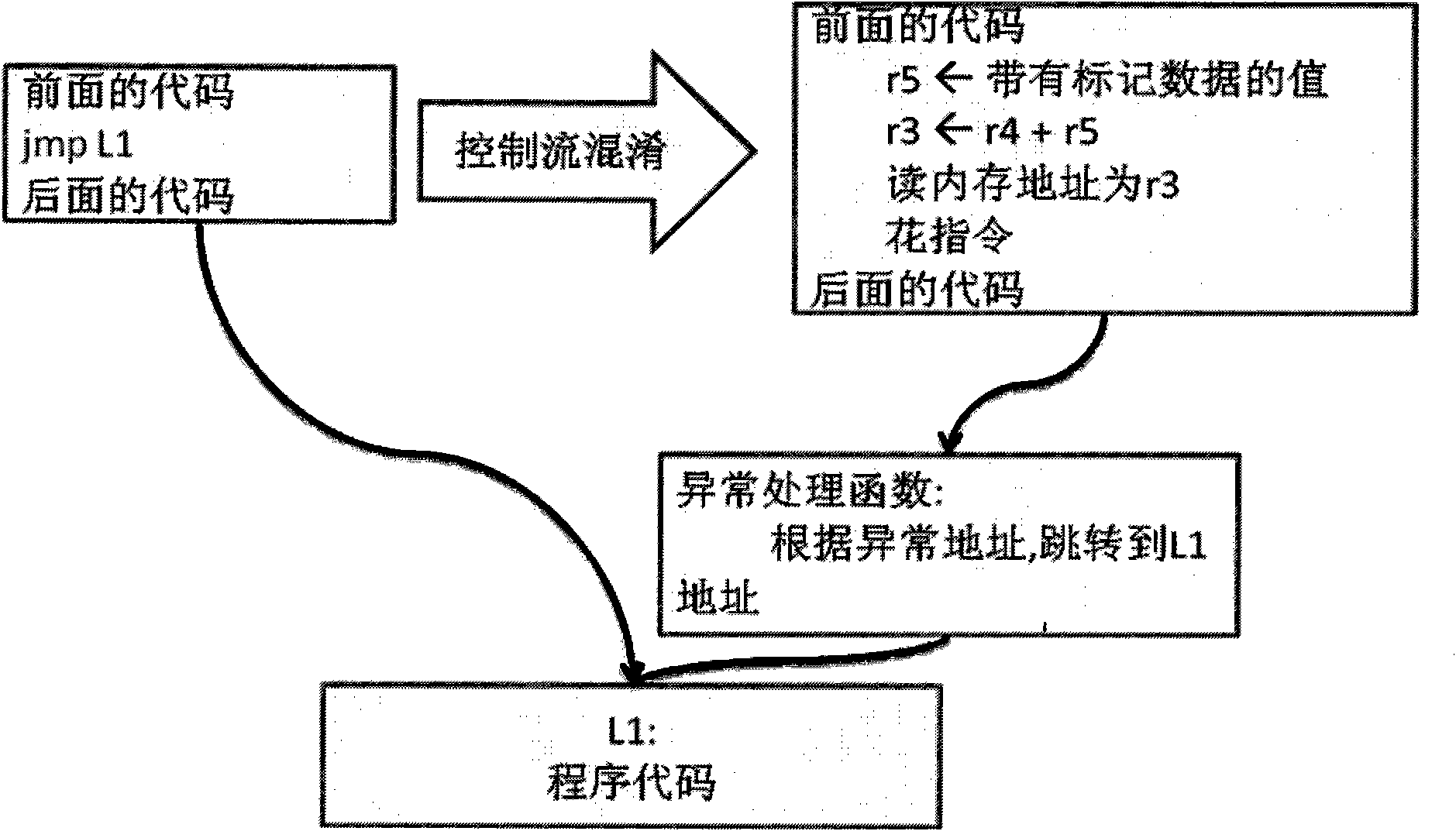
[0017] Such as image 3 As shown, an unconditional jump instruction is confused with the program instruction on the right. The semantics of the original program is to jump the processor's PC value to the address of L1. The obfuscated program instructions actually complete the same function, let's analyze its execution process in detail.
[0018] First, during the execution of the program, a data with a mark is assigned to the register R5, and then R5 propagates the mark to R3 along with the execution of the program. We can see that R3 is also a marked register. Then, as mentioned above in the summary of the invention, there will be a difference in CPU processing between marked data and unmarked data. R3, the marked data, is used as a memory address for reading, and will An exception will occur. At this time, because of the exception, the program wil...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com