Patents
Literature
94 results about "Intellectual property rights protection" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
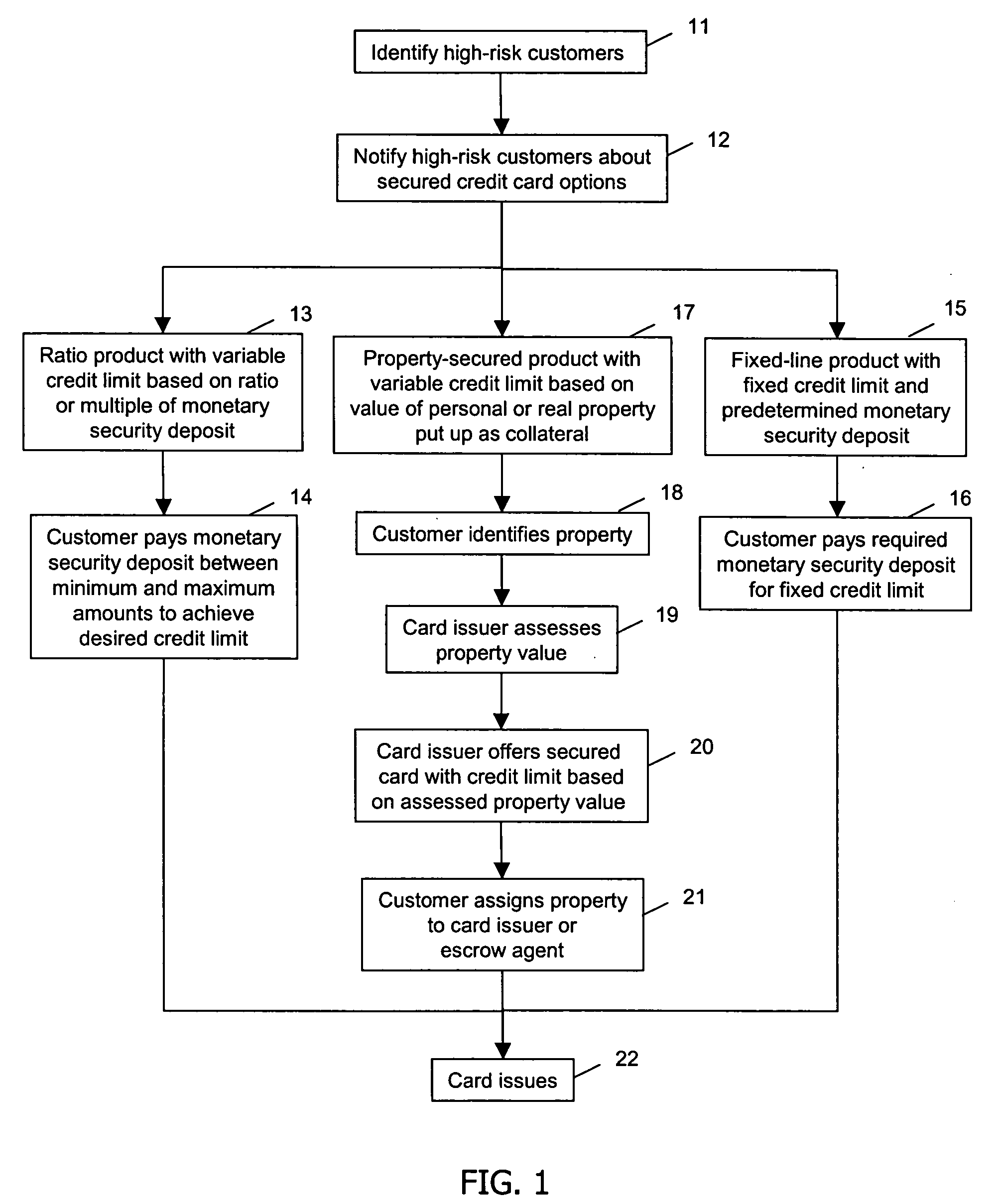
Patent Type
Patent Status
Application Year
Inventor
Intellectual property is a property right that can be protected under federal and state law, including copyrightable works, ideas, discoveries, and inventions.
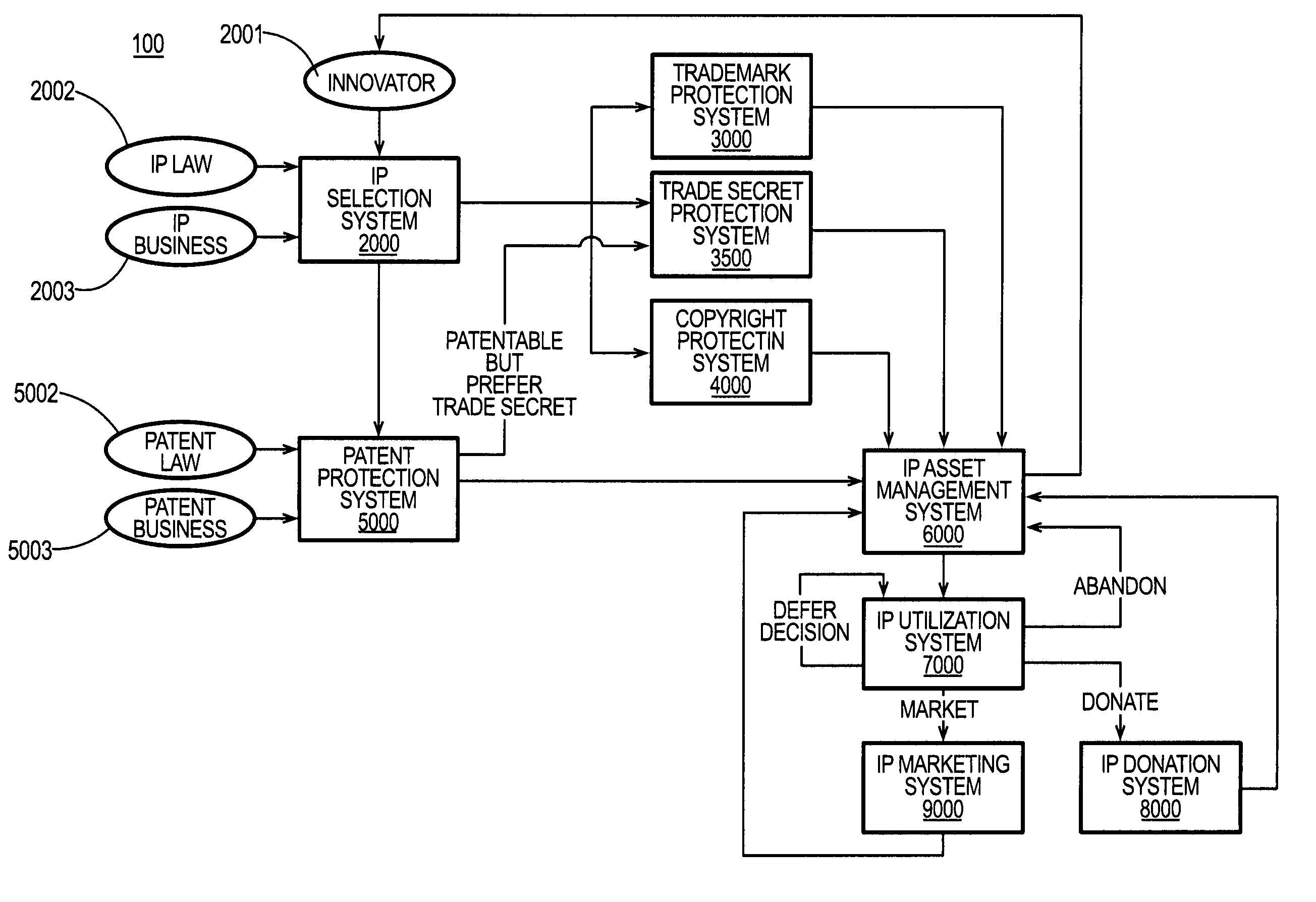
System and method for selecting and protecting intellectual property assets
Owner:BELLSOUTH INTPROP COR
System and method for selecting and protecting intellectual property assets
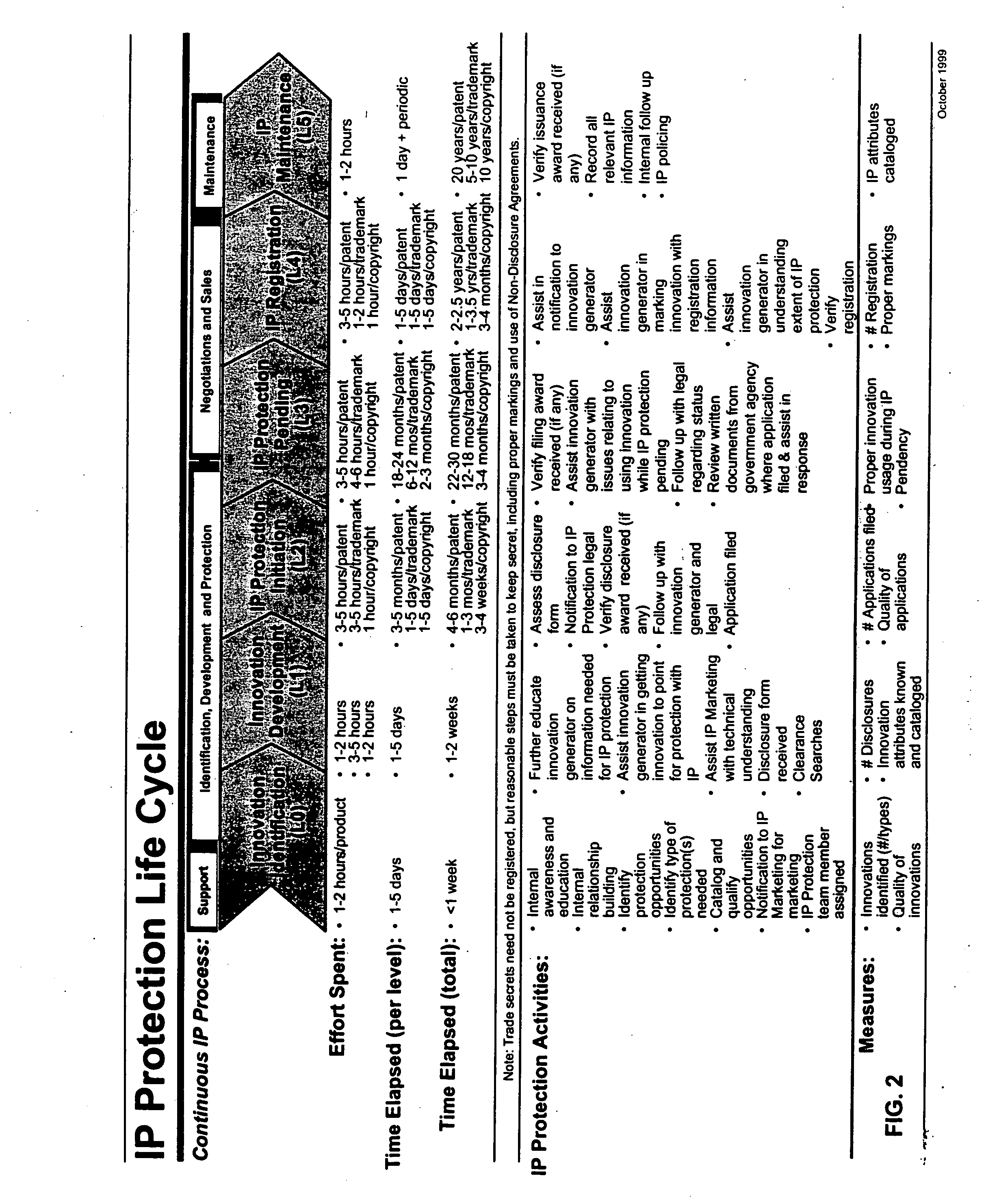
The present invention relates to systems and methods for intellectual property asset selection and protection. In an embodiment, an intellectual property selection system receives from an innovator an innovation submission describing an innovation. An intellectual property protection system receives at least a portion of the innovation submission and manages obtaining an intellectual property legal right related to the innovation. An intellectual property asset management system receives and stores at least one of an innovation description and an intellectual property legal right description, where the innovation description is based at least in part on the at least a portion of the innovation submission and the intellectual property legal right description is based at least in part on the intellectual property legal right.
Owner:AT&T INTPROP I LP
System and method for selecting and protecting intellectual property assets
The present invention relates to systems and methods for intellectual property asset selection and protection. In an embodiment, an intellectual property selection system receives from an innovator an innovation submission describing an innovation. An intellectual property protection system receives at least a portion of the innovation submission and manages obtaining an intellectual property legal right related to the innovation. An intellectual property asset management system receives and stores at least one of an innovation description and an intellectual property legal right description, where the innovation description is based at least in part on the at least a portion of the innovation submission and the intellectual property legal right description is based at least in part on the intellectual property legal right.
Owner:AT&T INTPROP I L P
Digital media resource registering transaction management system and realizing method thereof
InactiveCN101639916AGuarantee normativeReflect the significance of copyright protectionCommerceRelevant informationResource information
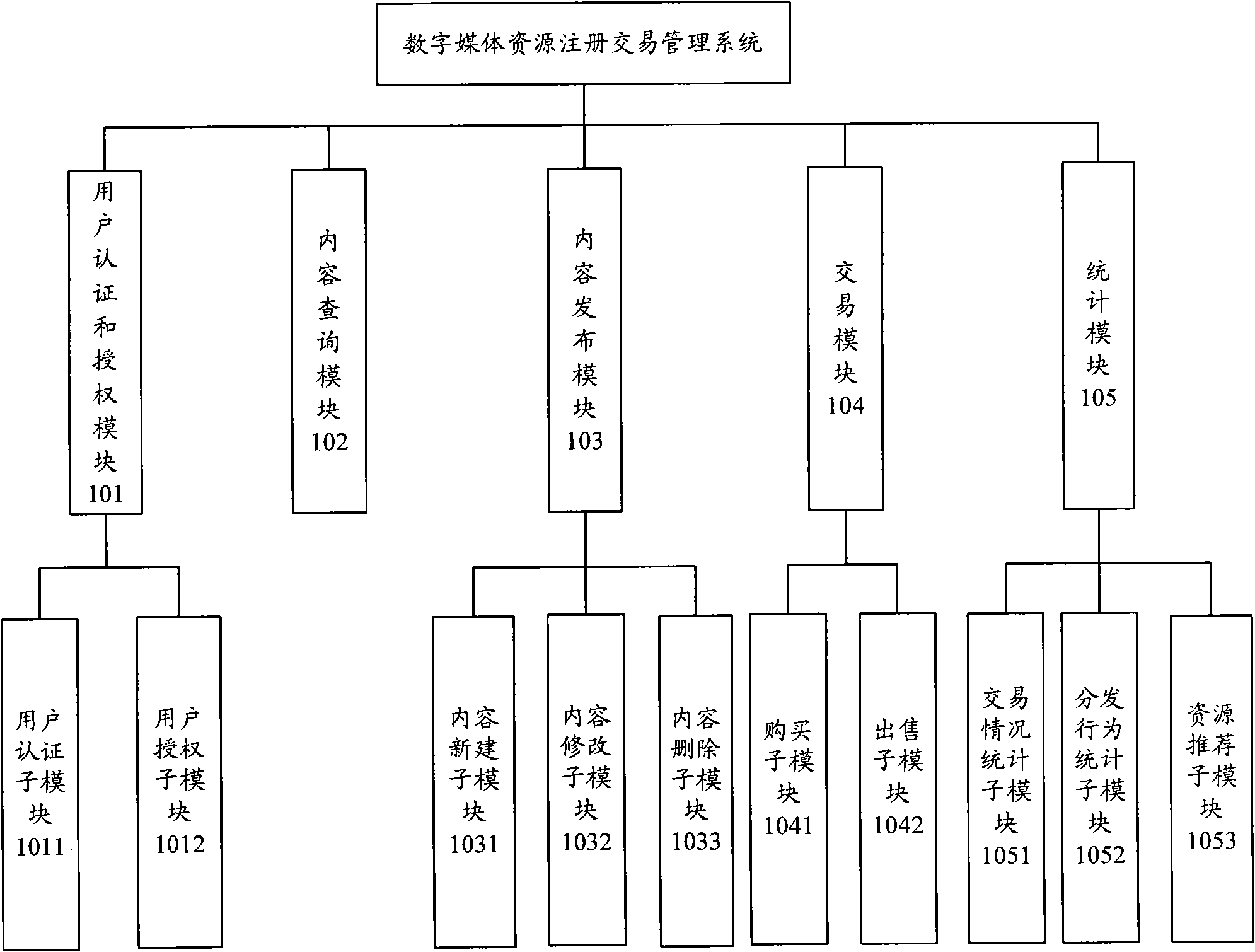
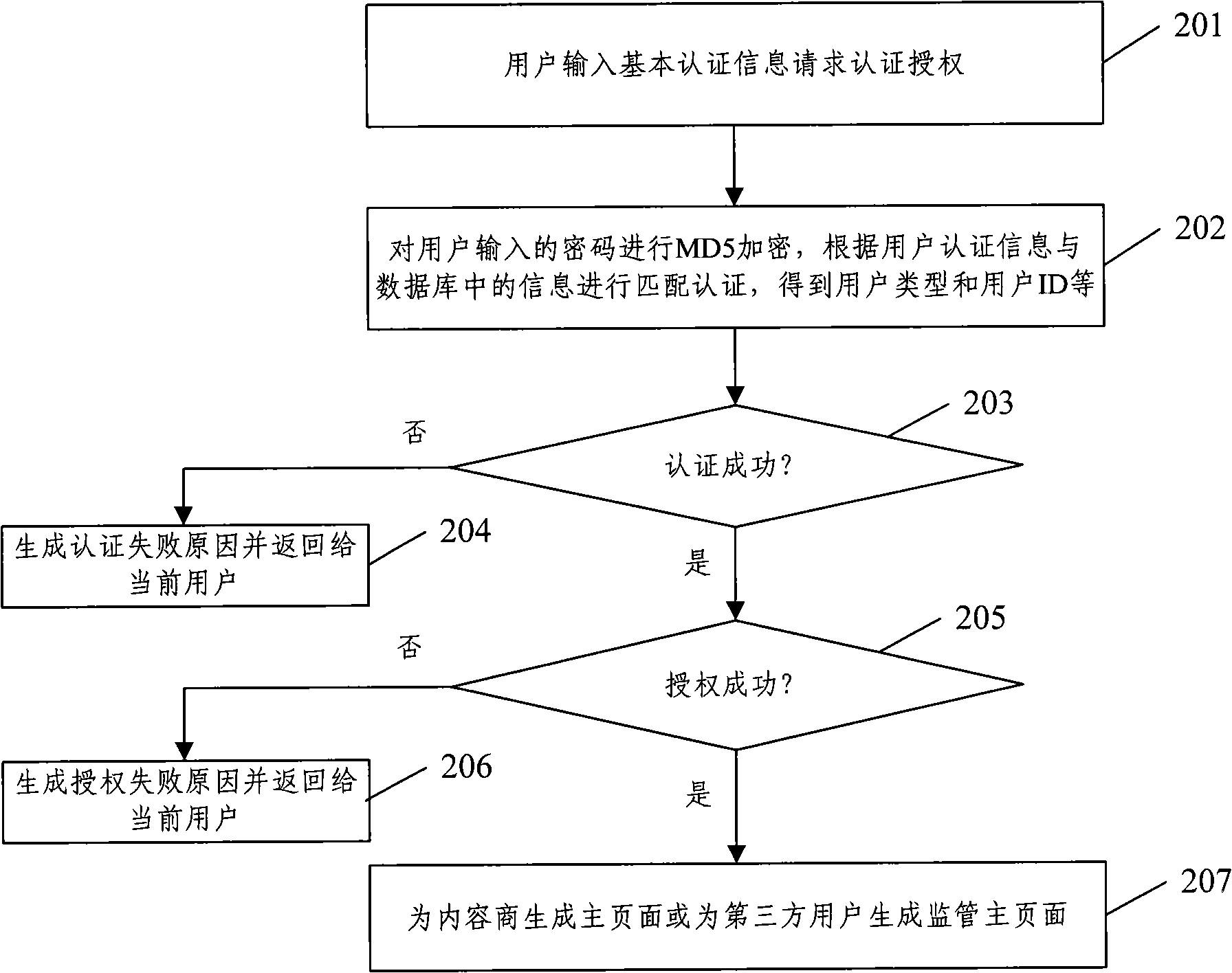
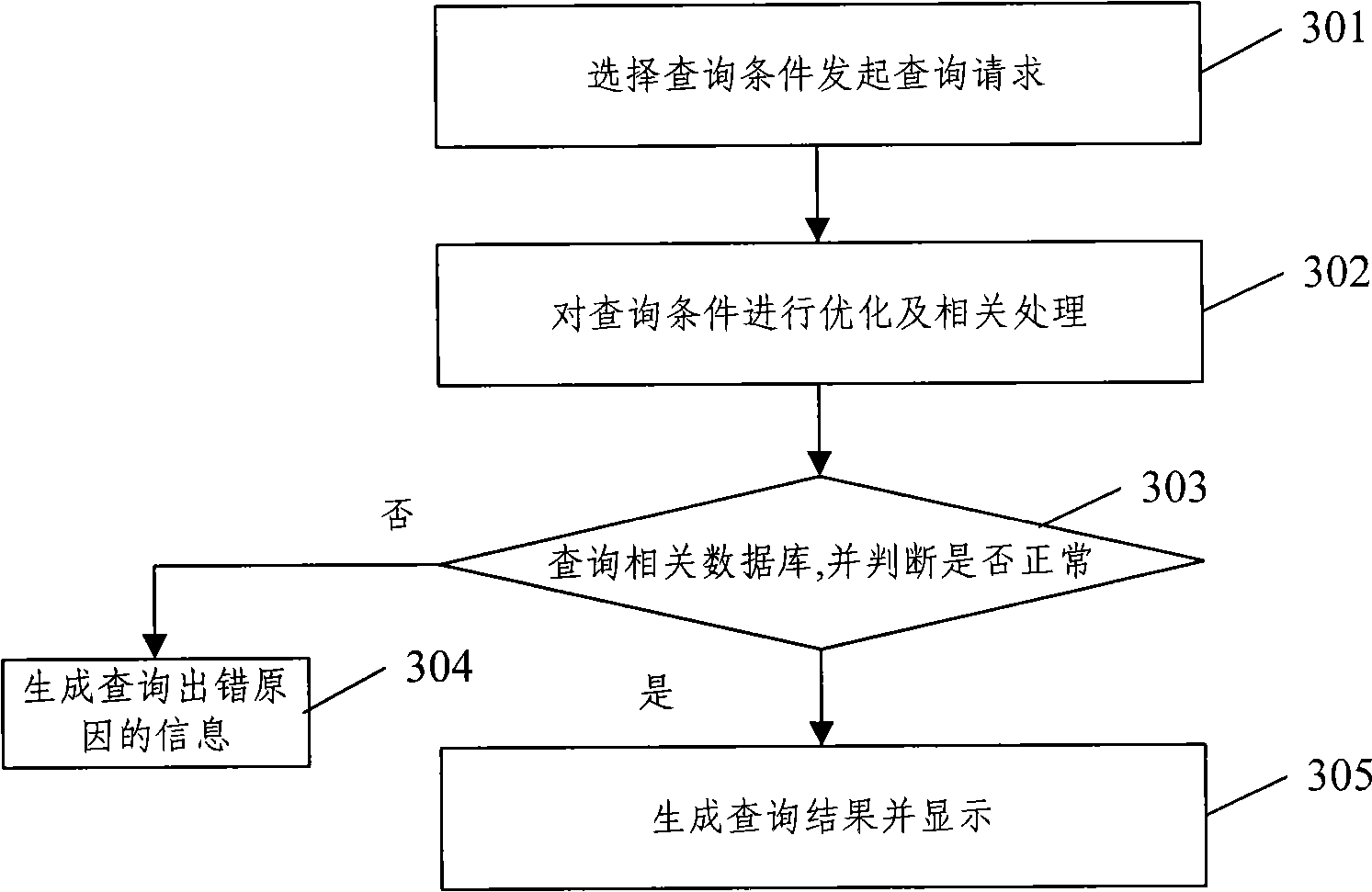
The invention discloses a digital media resource registering transaction management system and a realizing method thereof. The method comprises the following steps that: after being verified through an identification authentication and authorization module, the content dealer logs on the management system, and releases related information of digital media resource to the management system througha content release module; when searching digital media resource information to be purchased through a content searching module, the content dealer purchases the information through a transaction module; in the same way, when searching purchasing information of other content dealers, the content dealer can sell the digital media resource which is required by the opposite side through a dealing module; and the content dealer can carry out statistics for dealing conditions and distribution behaviors of the digital media resource and provide recommendations of hot resources. The management systemand the method can carry out release, deal and the statistics for the digital media resource with copyright among dependable content dealers through internet, and effectively realize intellectual property protection on the digital media resource.
Owner:BEIJING UNIV OF POSTS & TELECOMM
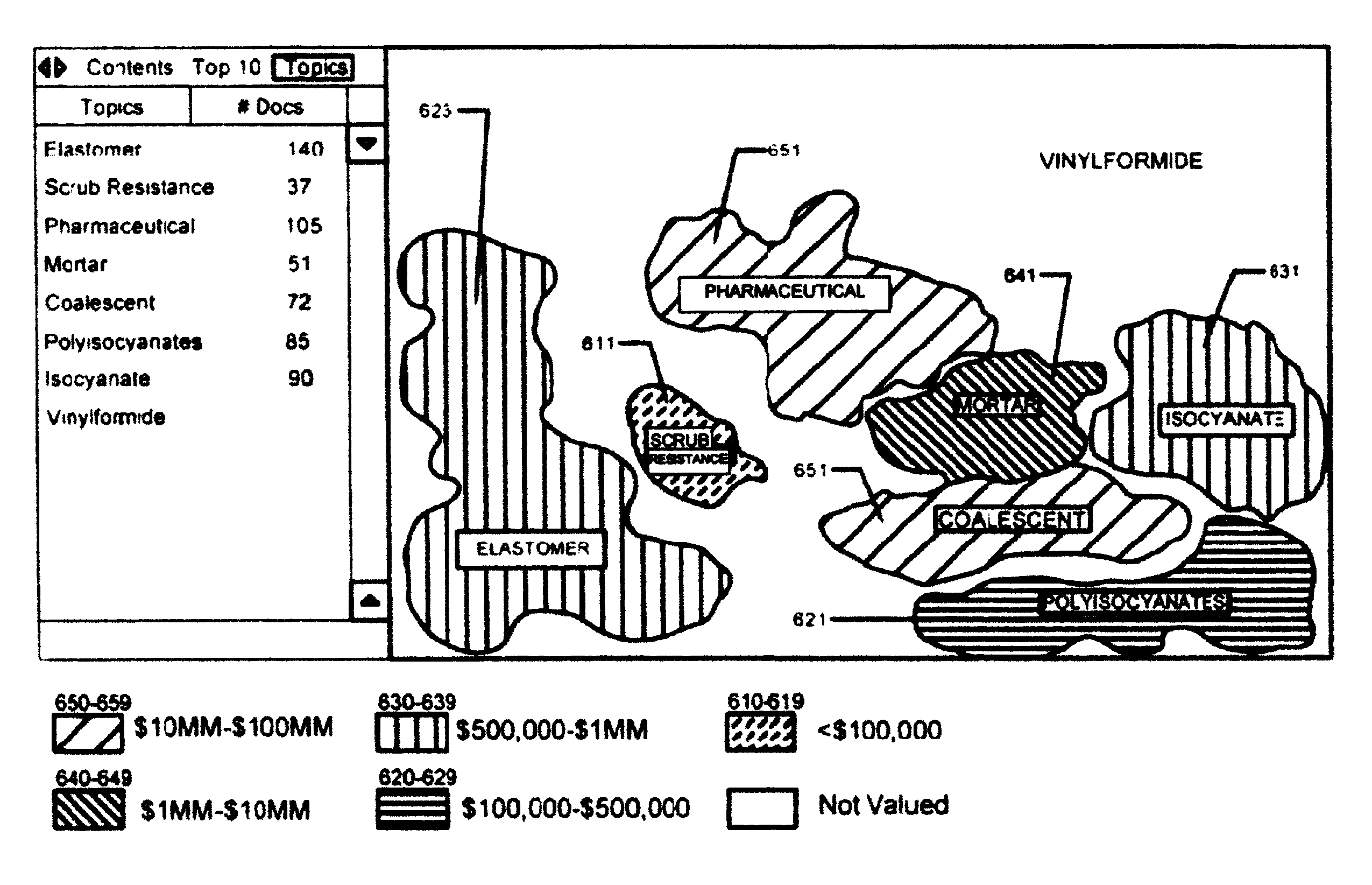
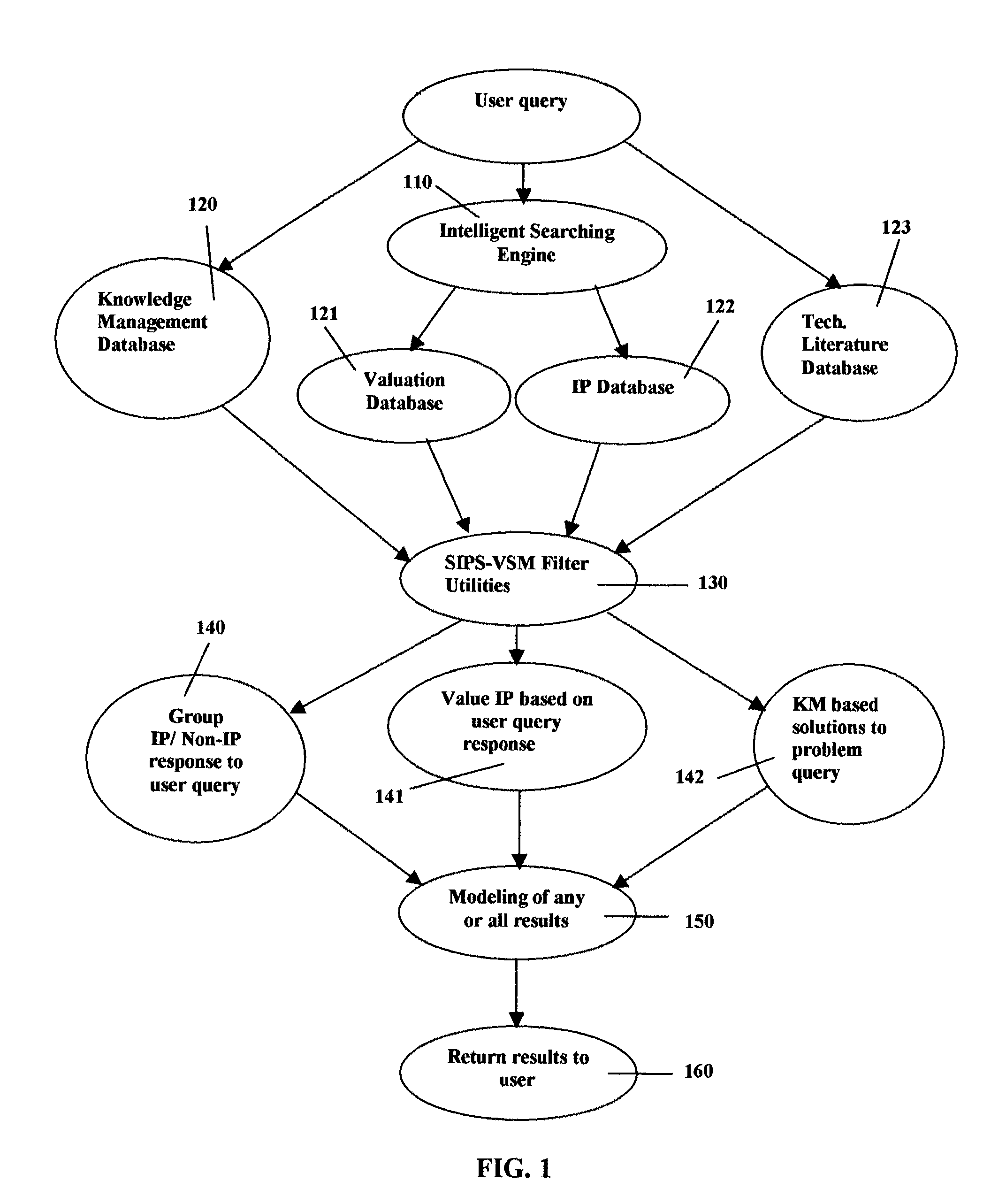
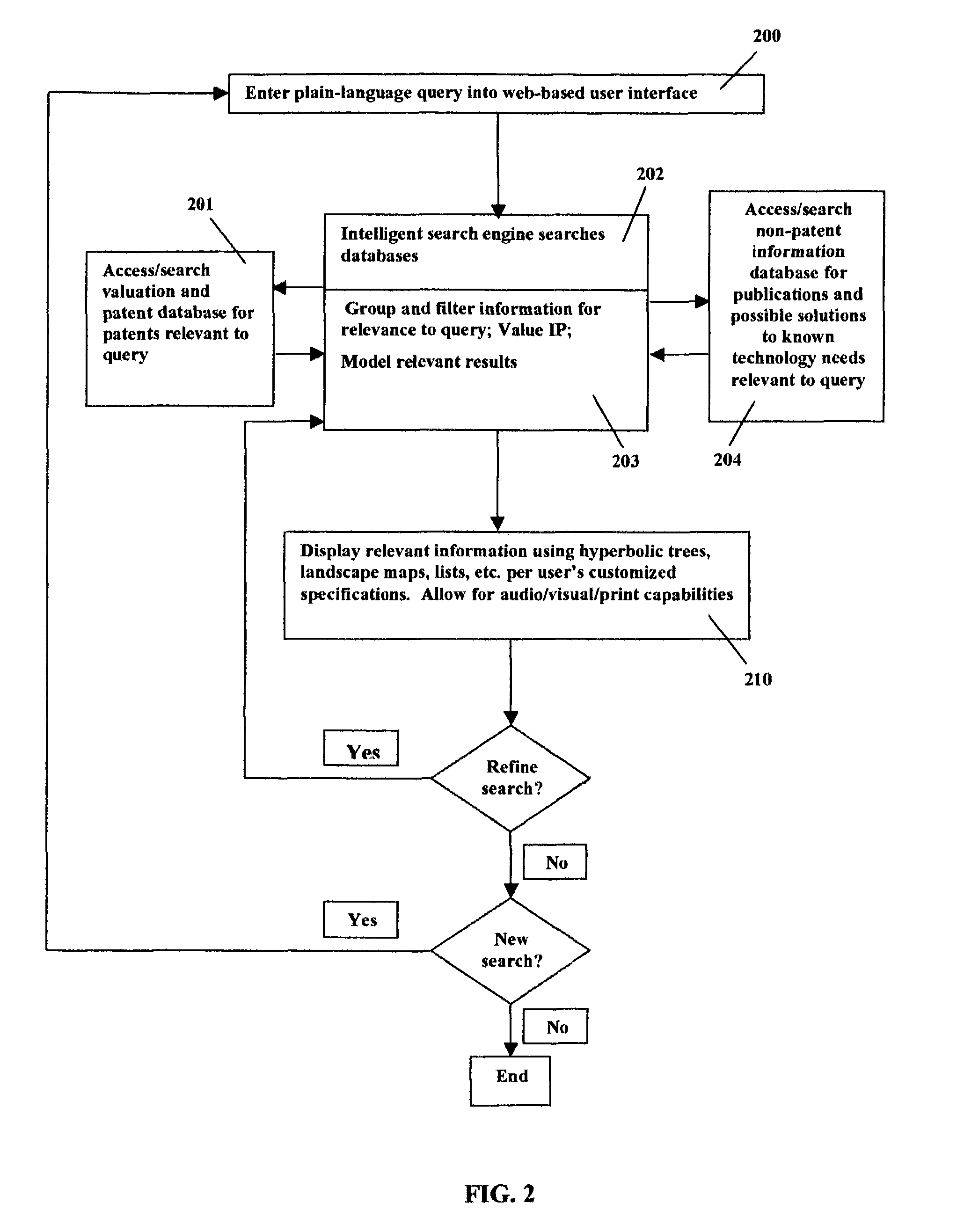
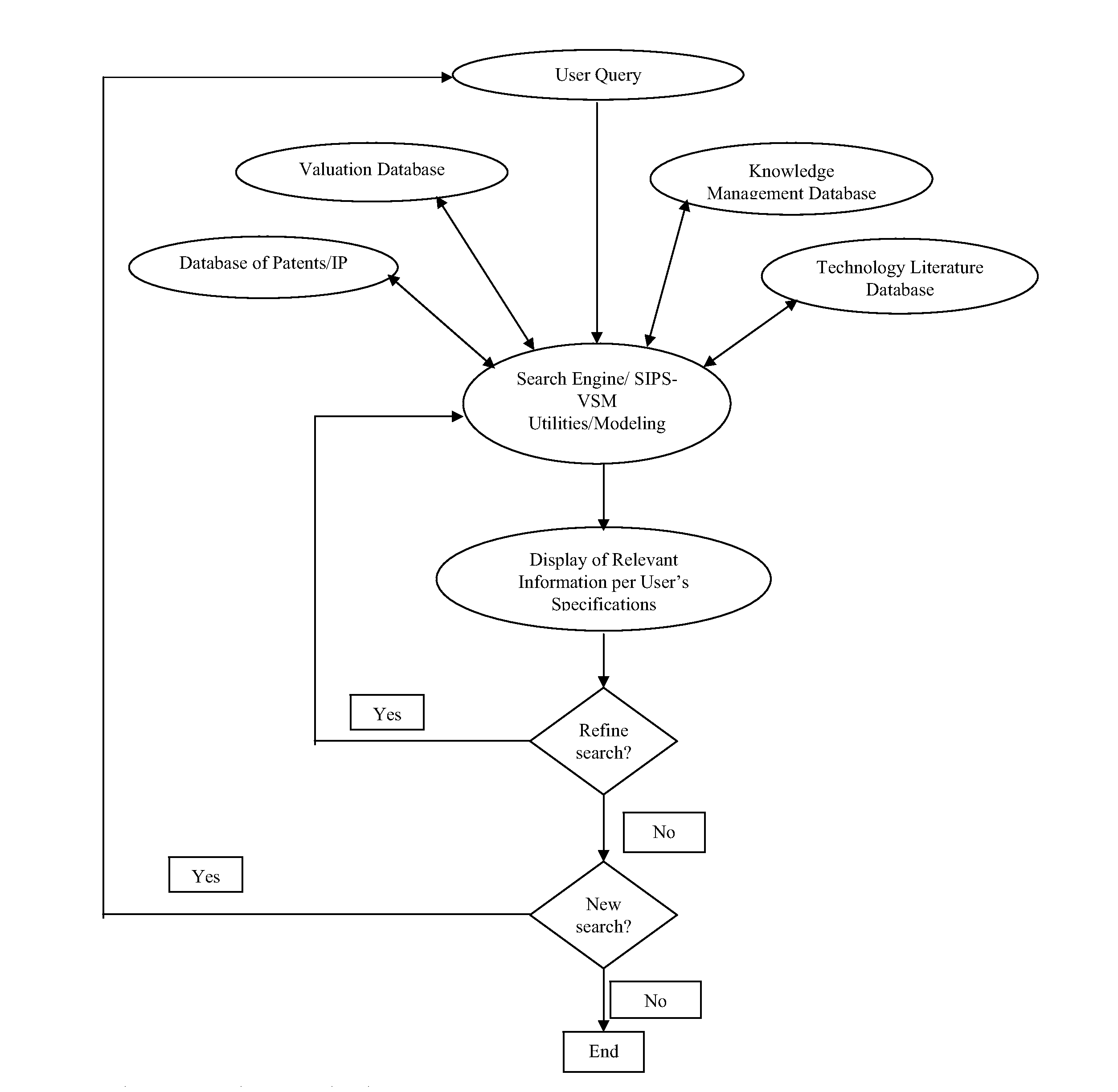
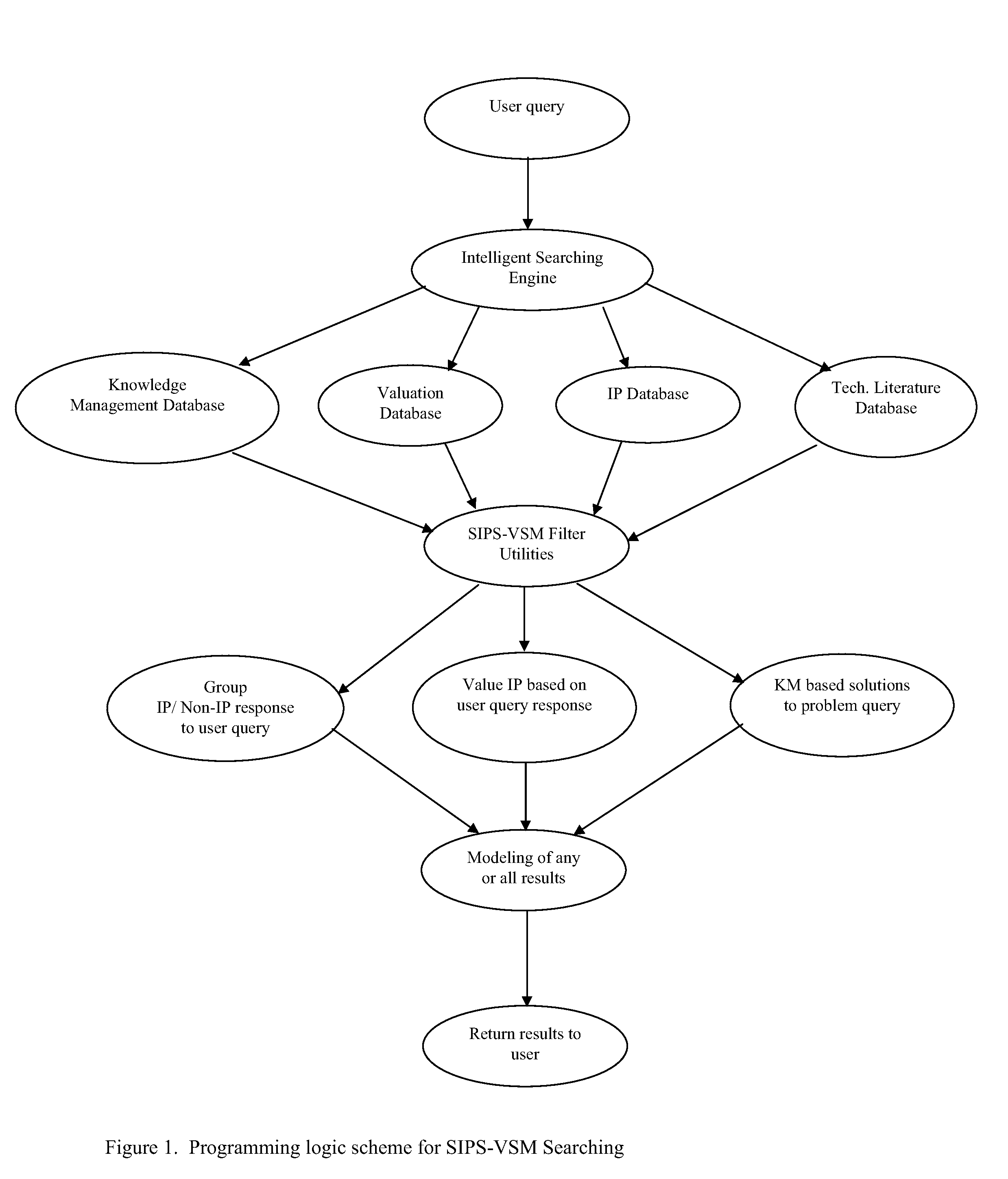
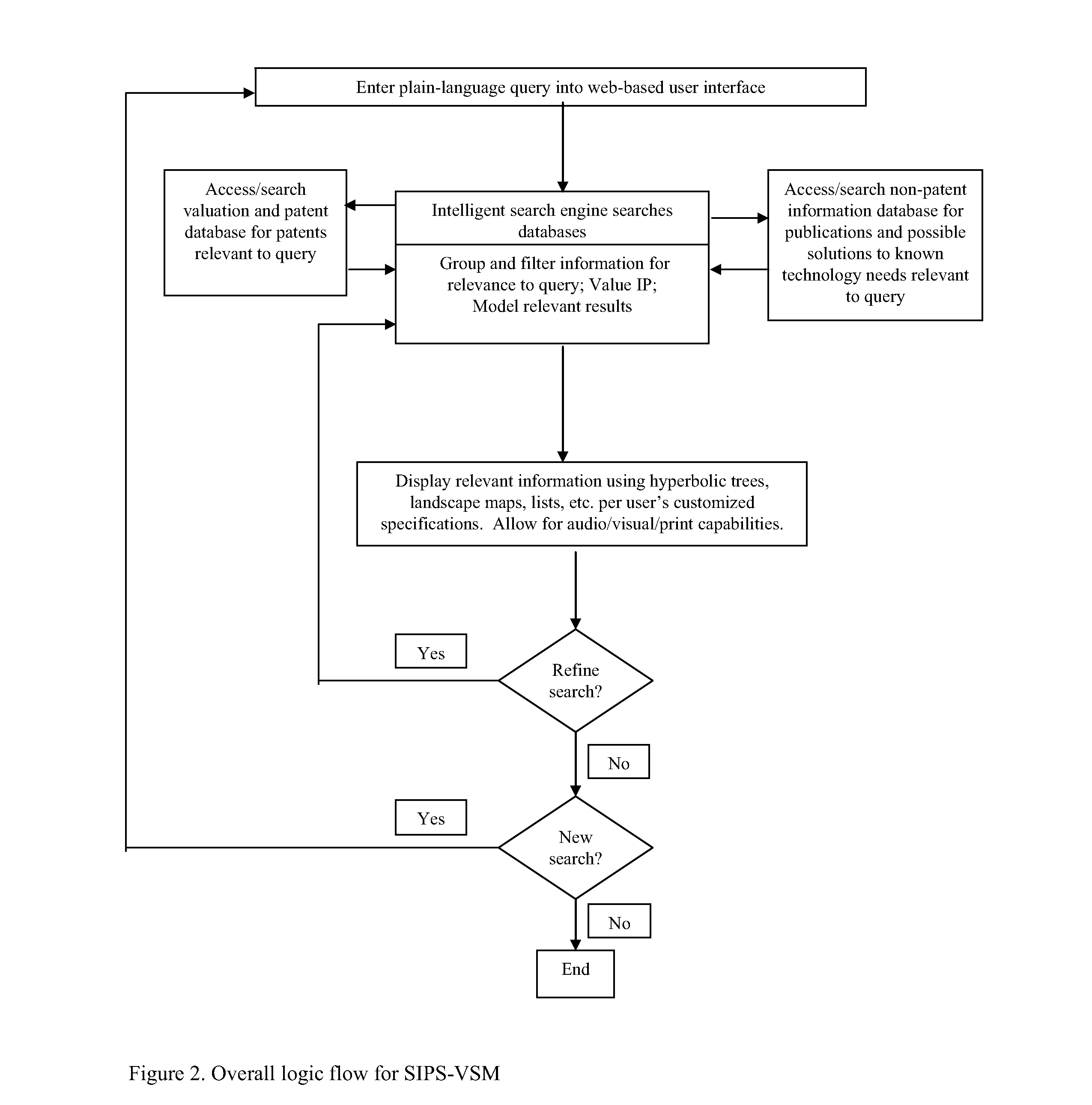
Simultaneous intellectual property search and valuation system and methodology (SIPS-VSM)
ActiveUS8326851B2Easily manipulateEasy to navigateDigital data information retrievalDigital data processing detailsProblem solveData science
A system, method, and computer-based logic flow for a web-enabled tool that allows simultaneous intelligent searching, knowledge management based problem solving, valuation, and modeling of intellectual property and scientific information are described herein. The system accesses databases of intellectual property and scientific information. Additionally, the computer-based logic flow utilizes valuation techniques based on the Black-Sholes Options Pricing model or discounted cash flow methods. The system receives user queries and simultaneously accesses intellectual property, scientific information, knowledge management based problem solving and valuation based algorithm databases. Pertinent information is then categorized, analyzed, disseminated and displayed. The system simultaneously displays intellectual property and valuation information in one model as well as non-intellectual property protected scientific information. Content, value, and direction of current and future specific technology trends can be easily, quickly and accurately accessed based on review of the models and displays associated with that specific technology.
Owner:EPATENTMANAGER COM
IP protection
ActiveUS20120319246A1Reduces disclosureSemiconductor/solid-state device testing/measurementSolid-state devicesComputer networkIntellectual property rights protection
Owner:RENESAS ELECTRONICS CORP +2
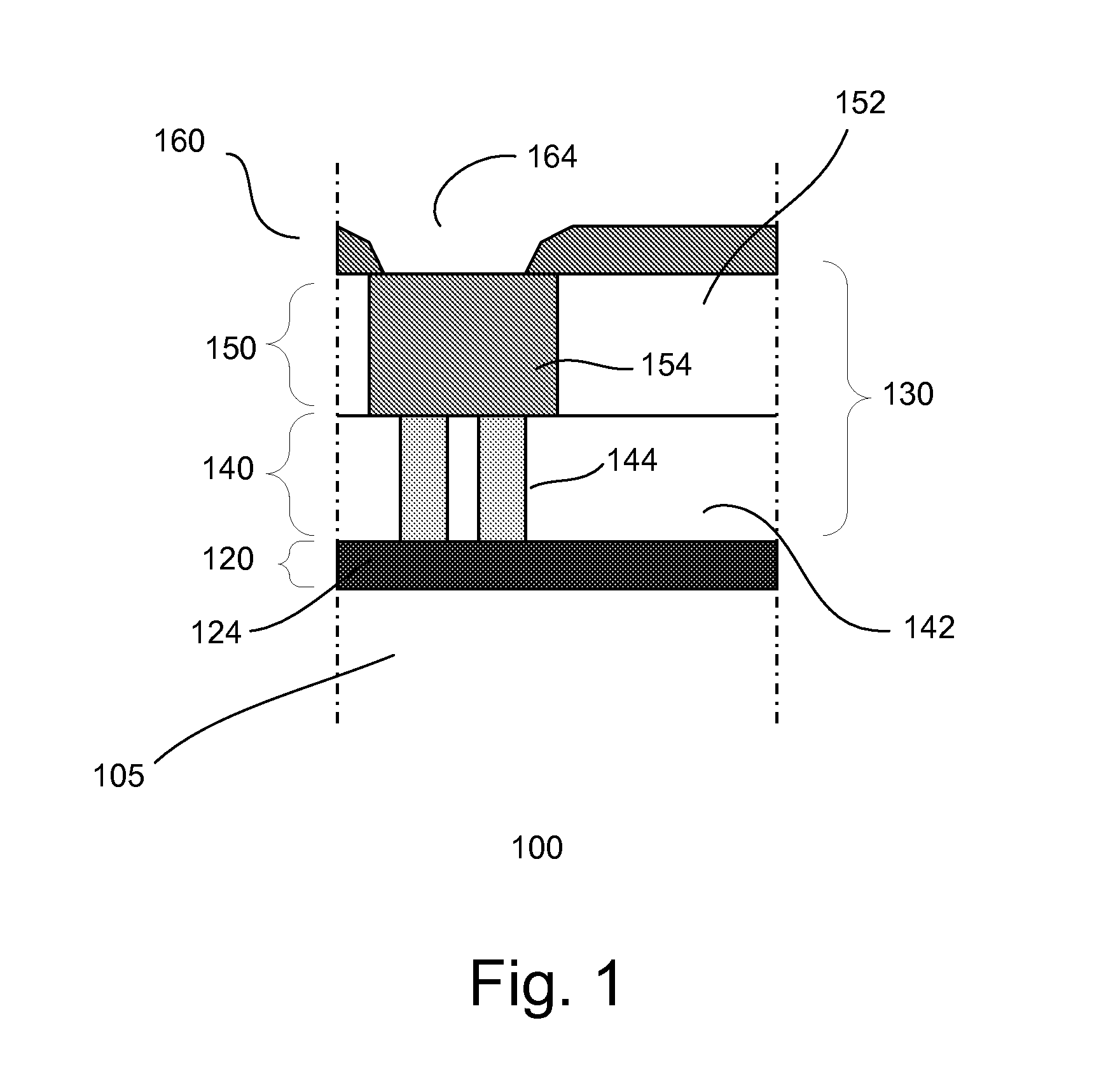
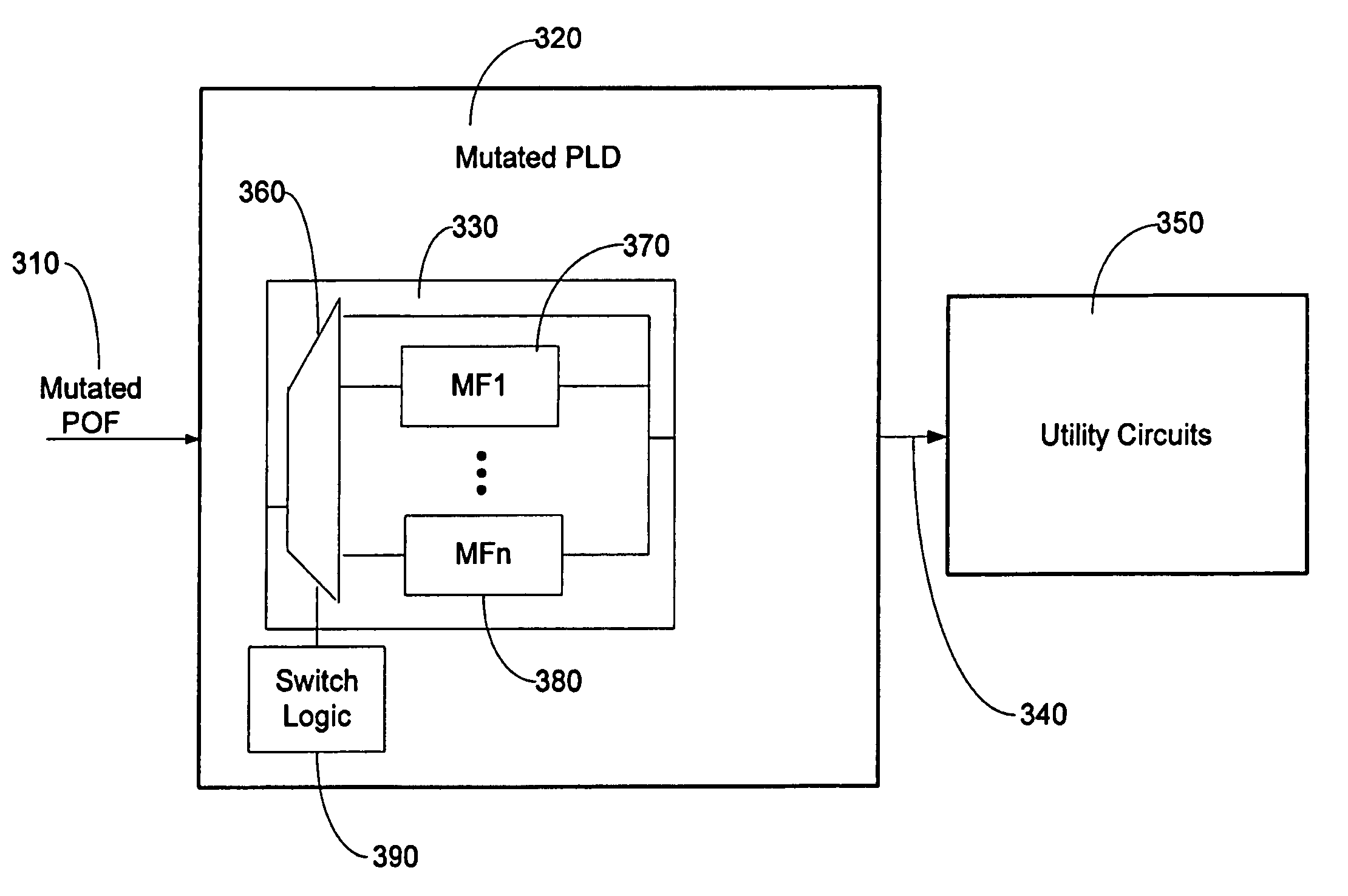
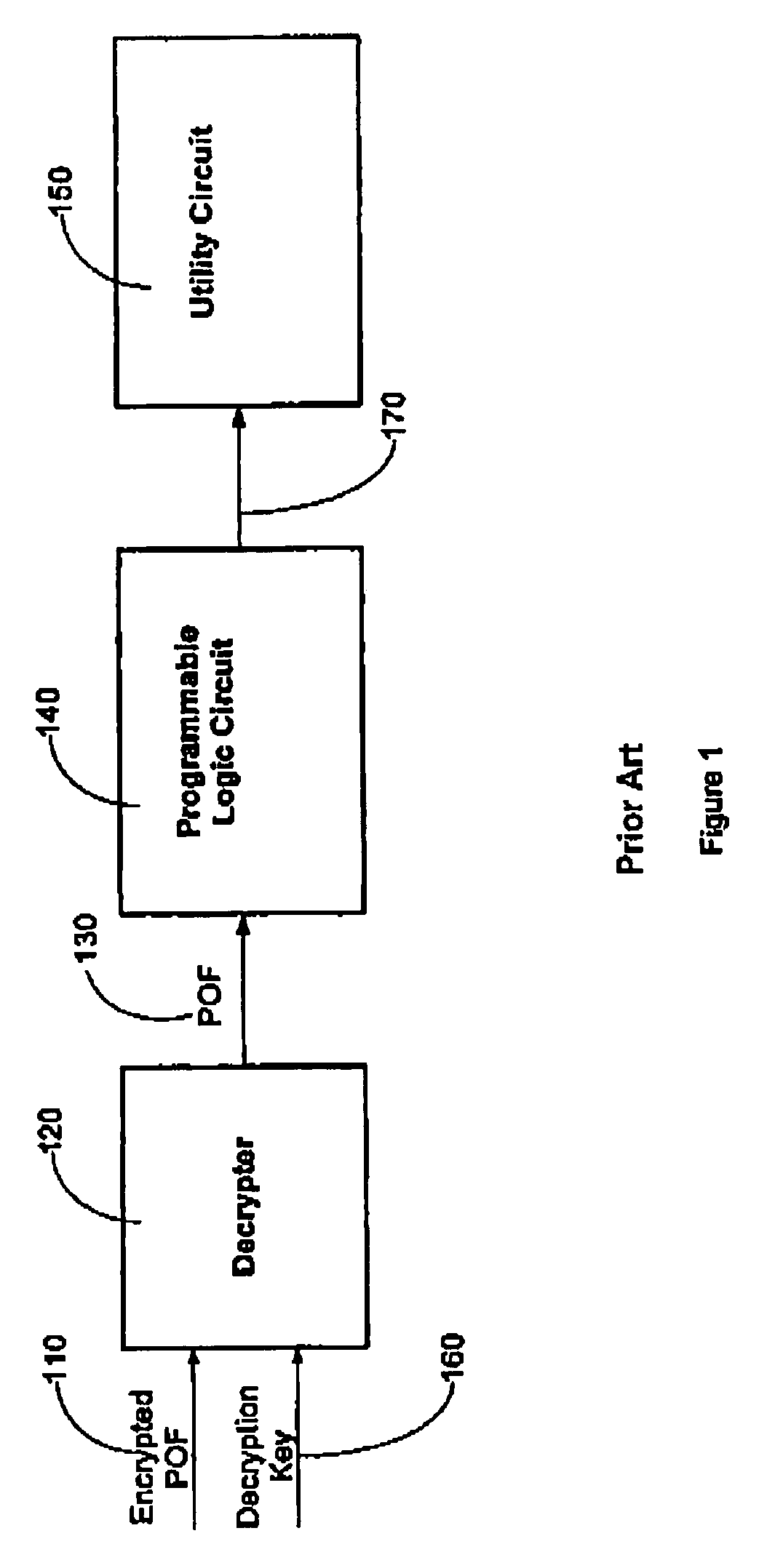
Methods and systems for achieving improved intellectual property protection for programmable logic devices
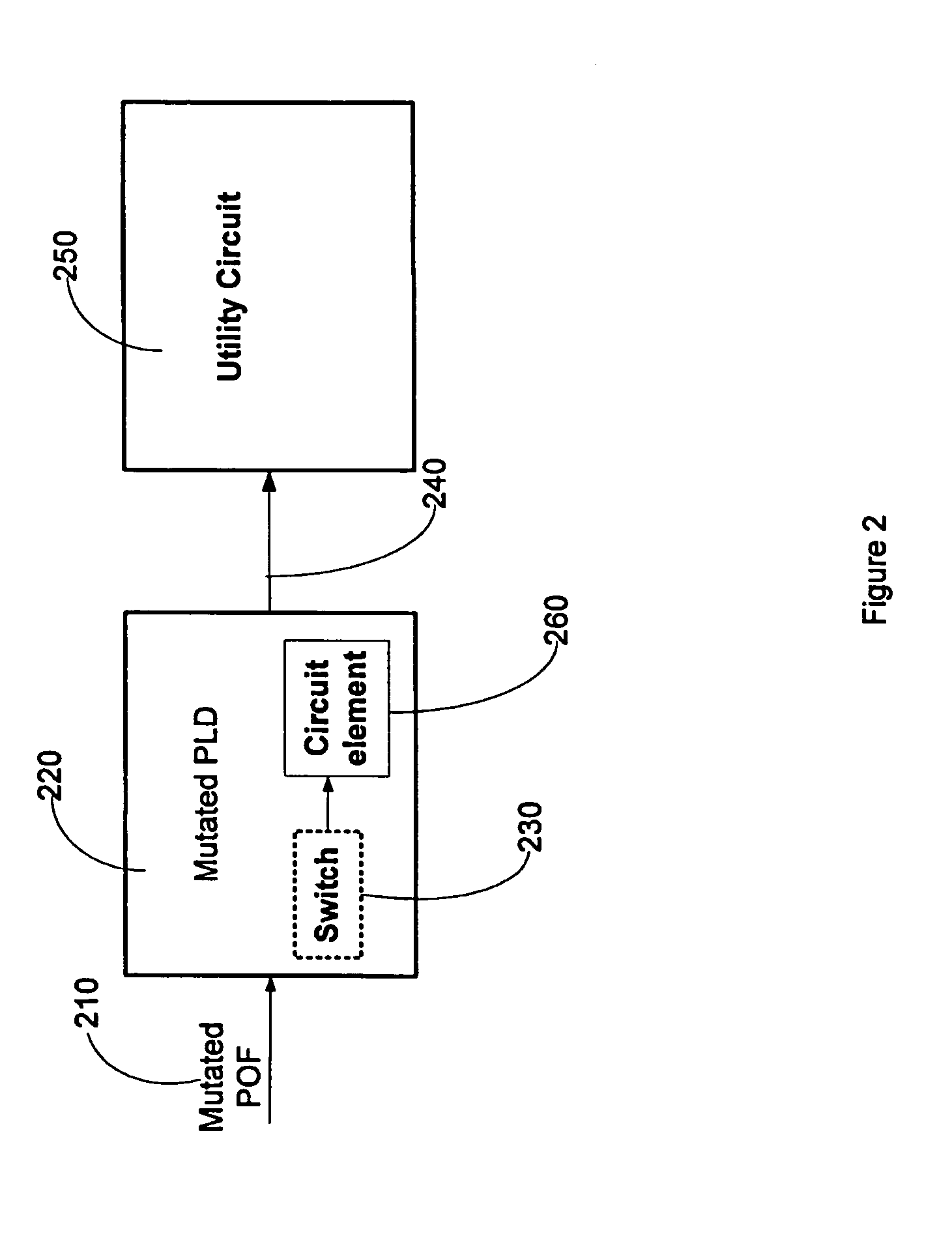
InactiveUS7236007B1Unauthorized memory use protectionHardware monitoringProgrammable logic deviceIntellectual property rights protection
Methods and system for achieving improved copyright protection for programmable logic devices are disclosed. One preferred embodiment comprises a programmable logic device comprising a programmable element programmed by a mutated programming pattern, said mutated programming pattern causing the PLD to generate a mutated output; and a circuit element that translates the mutated output into a normal output.
Owner:ALTERA CORP
Commodity networked gene based brand intellectual property protection platform
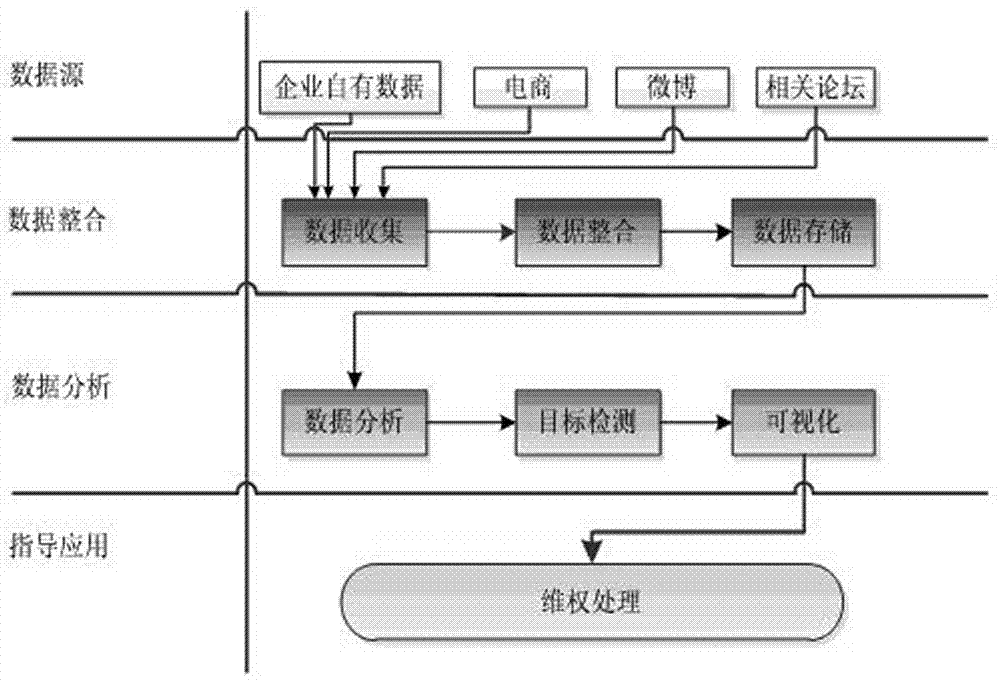
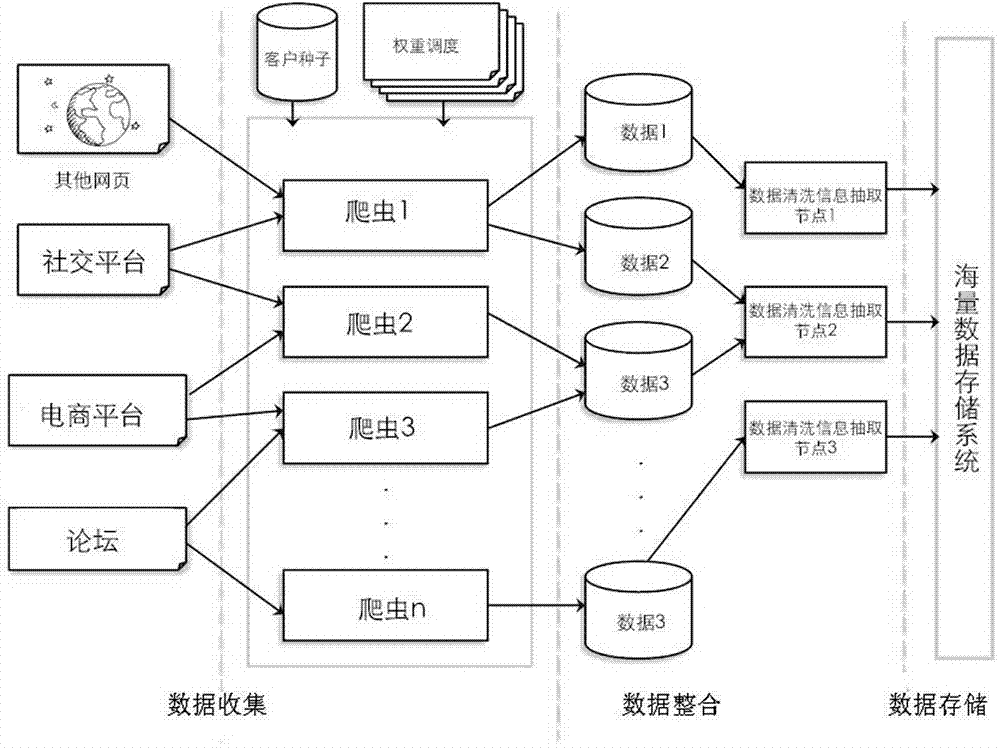
InactiveCN104123659AEasy to handleSave manpower and material resourcesCommerceSpecial data processing applicationsData scrapingMaterial resources
The invention discloses a commodity networked gene based brand intellectual property protection platform comprising a data source module, a data collection module, a data integration module, a data storage module, a data analysis module, an object detection module, a visual module and a data application module. When the data collection module collects data source data, an open-source Hadoop platform is utilized for constructing a distributive whole-network commodity data capturing system; the data analysis module is utilized for structured arrangement of a great number of unstructured commodity comment data; the object detection module is utilized for analysis and detection of suspected infringing commodities by the aid of an established infringing commodity identification model; the visual module is utilized for displaying the analyzed and detected suspected infringing commodities via a visual interface. The commodity networked gene based brand intellectual property protection platform has the advantages that fewer human and material resources can be utilized, a larger-scale market can be handled effectively, and intellectual property maintenance cost is reduced for enterprises, so that economic benefits are increased.
Owner:HANGZHOU YEGOON TECH CO LTD
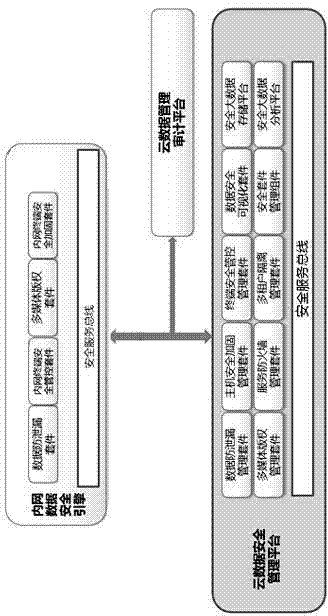
Design method based on intranet data security protection engine
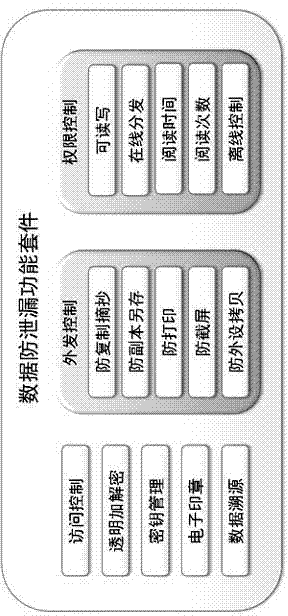
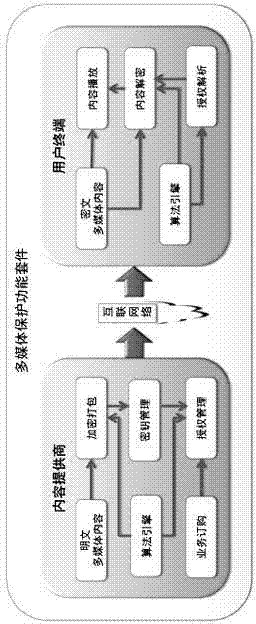
ActiveCN104123508ARealize digital copyright protection functionSolve tracking and positioningDigital data protectionProgram/content distribution protectionData fileSecurity controls
The invention provides a design method based on an intranet data security protection engine. A data file anti-leakage protection package and a multimedia digital right management package are deployed in the intranet data security protection engine, as a result, the multimedia content digital right management function in the intranet environment is achieved, and the effects of authorized accesses, piracy prevention and intellectual property protection of multimedia content are achieved. Through file circulation perception and file leakage perception, all-process tracing and positioning of electronic files are realized, and leakage prevention and unauthorized accesses of the electronic files are realized. In order to facilitate management and configuration of the security packages, dynamic loading management is conducted on all the safety packages in the engine through an intranet terminal security control package, and new security function units can be installed or uninstalled according to real demands of clients at any time. In order to guarantee security of intranet data, mandatory access control over files, progress and services is realized through an intranet terminal security reinforcing package, file process and leakage are perceived, and leakage of classified electronic files are prevented.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
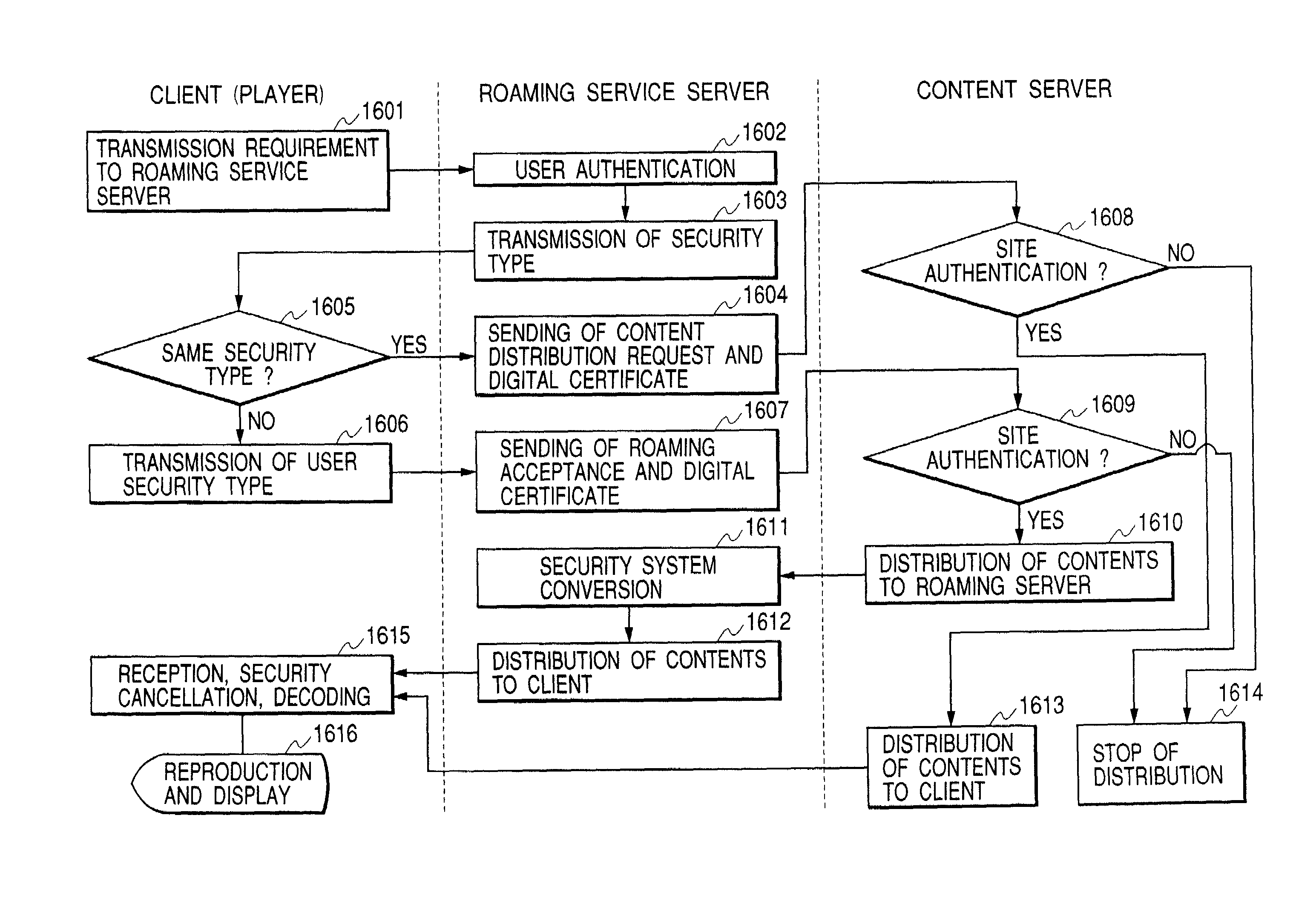
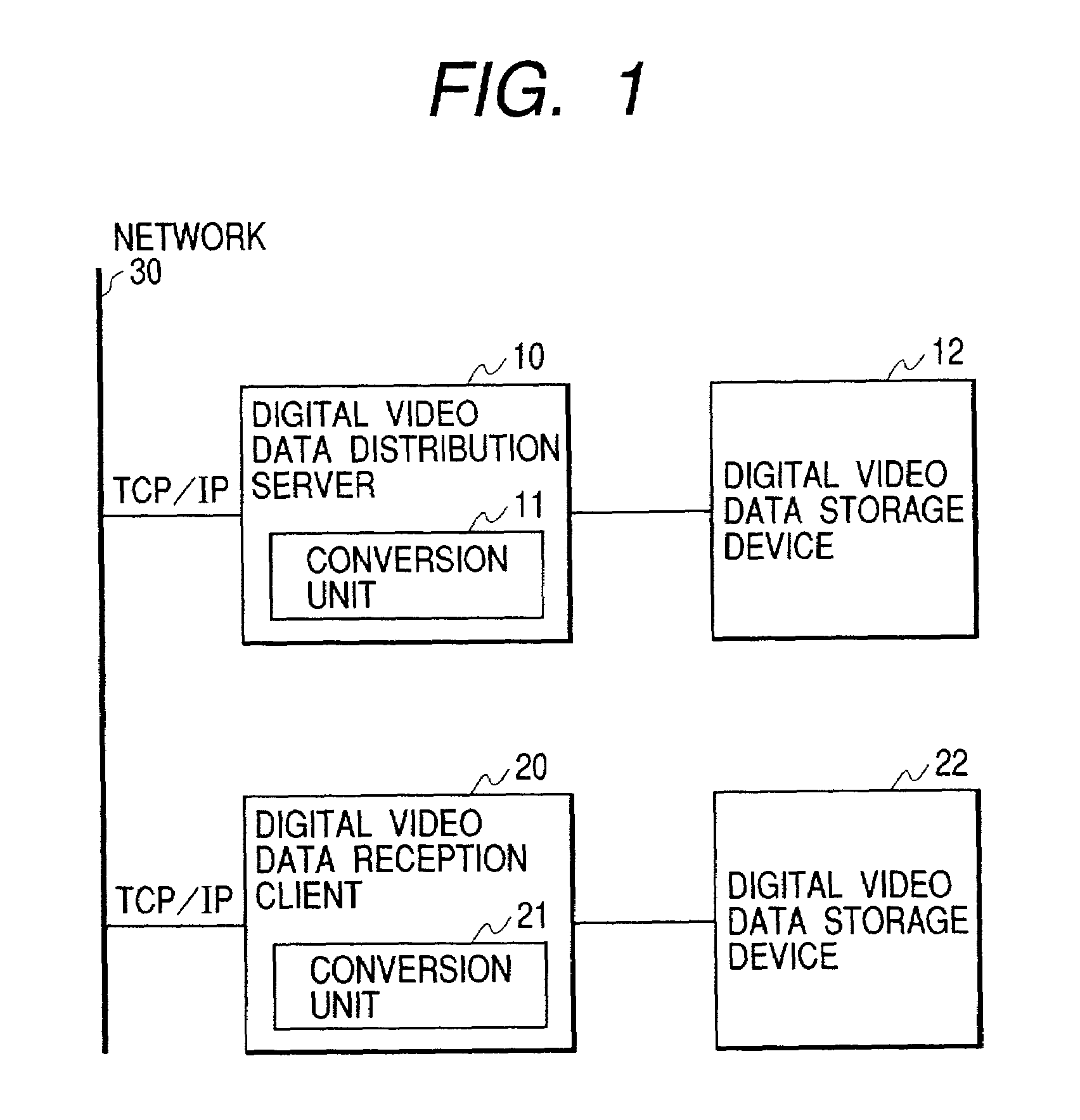
Digital contents distribution system, digital contents distribution method, roaming server, information processor, and information processing method
InactiveUS7177841B2Ensure interoperabilityPulse modulation television signal transmissionData processing applicationsDigital contentDistribution method
A digital contents distribution system including a client, a digital contents server, a roaming server, and a network connected between these terminals. The roaming server includes a receiving section for receiving from the digital contents server a digital content with an intellectual property right protection system protecting the digital content, and a section for converting the intellectual property right protection system of the received digital content into another kind of intellectual property right protection system, and a section for delivering the converted system to the client.
Owner:CANON KK
Method, apparatus and system for intellectual property protection
InactiveCN101179571ARealize monitoringEasy to downloadData switching networksData informationCommunicator device
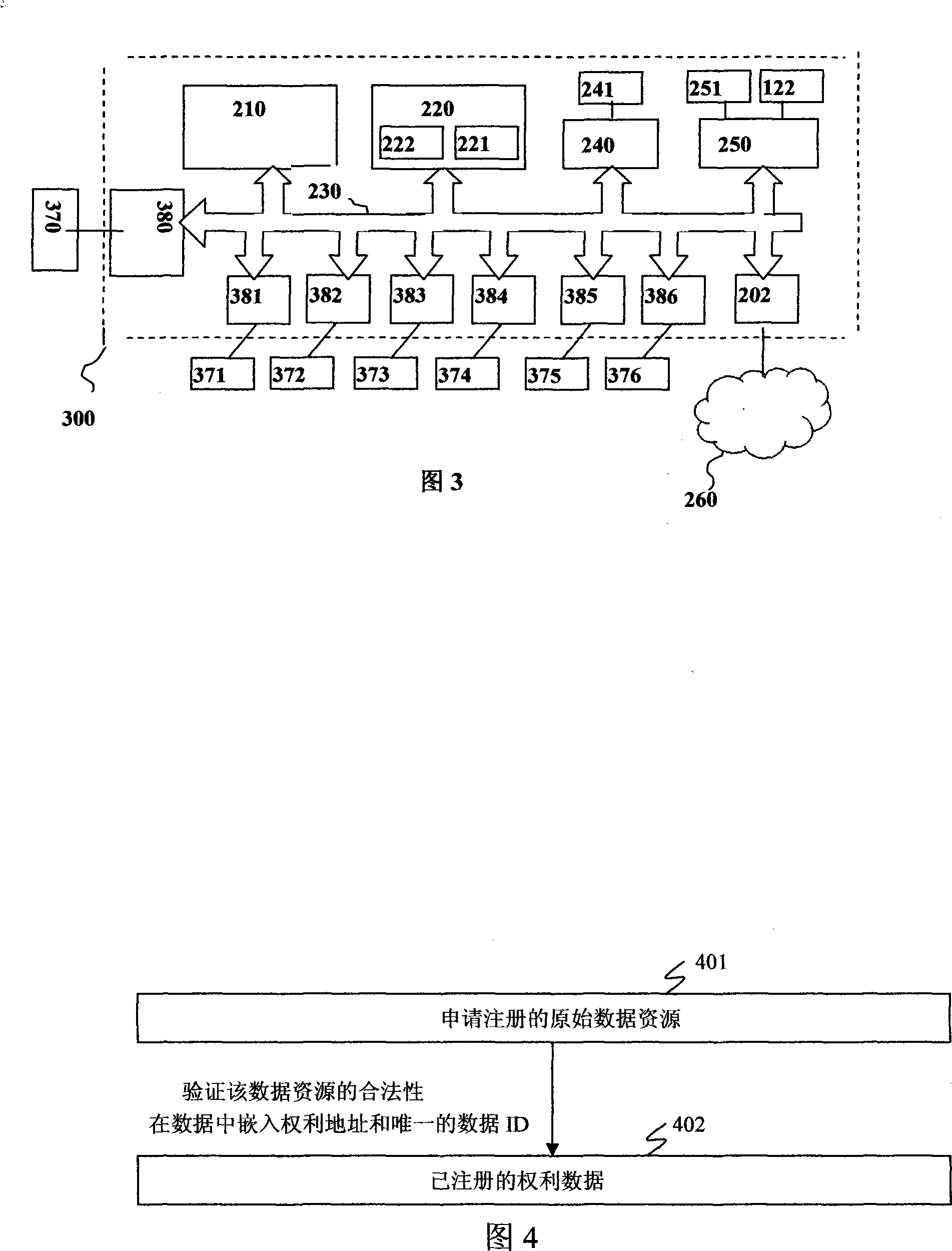
The invention discloses a method, a device and a system relating to the intellectual property protection. The invention discloses a method, a device and a system for embedding the right data information which at least contains the right address and the unique data ID in the data, resulting in a communication device further applying the right data information screening to the transmitted and delivered data when transmitting and delivering the data, and resulting in the host which processes and stores the data screening the right data information and processing the corresponding data.
Owner:张建中
Safe two-dimensional code manufacture method and decoding method, and safe two-dimensional code identifier
ActiveCN105550730AFix security issuesSolve defects such as anti-copyingRecord carriers used with machinesDecoding methodsProgramming language
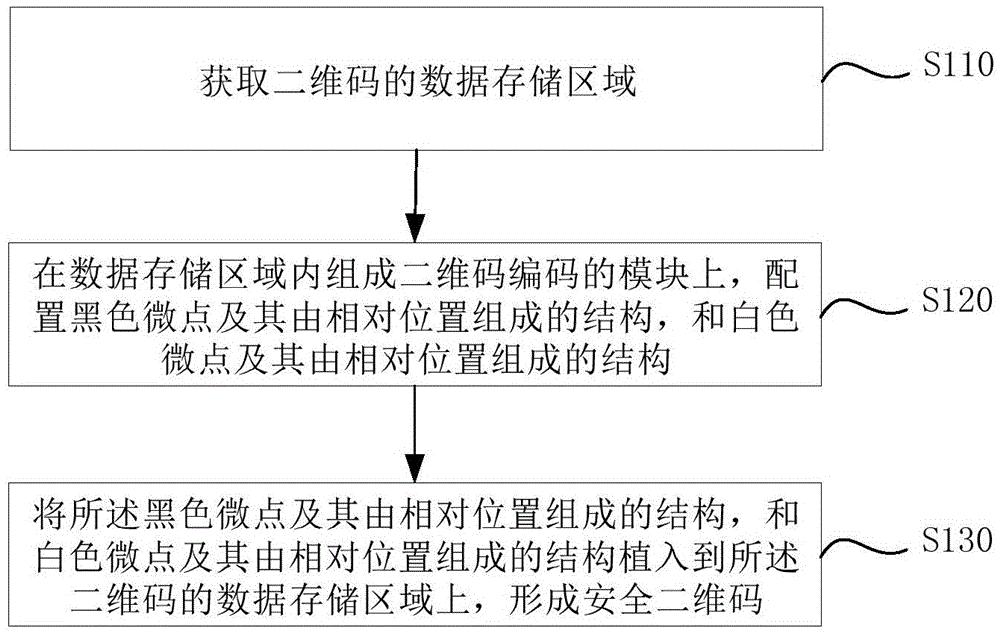
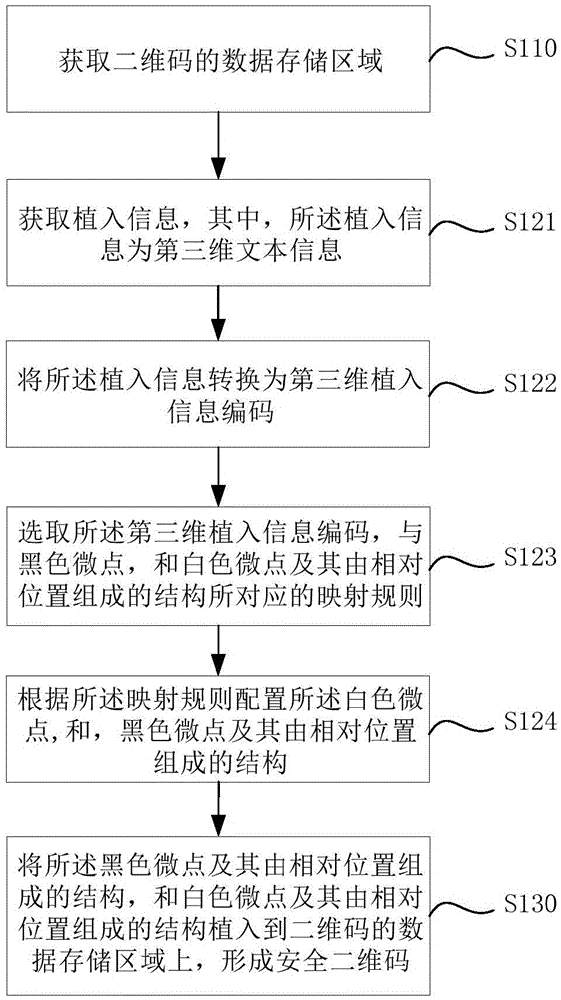
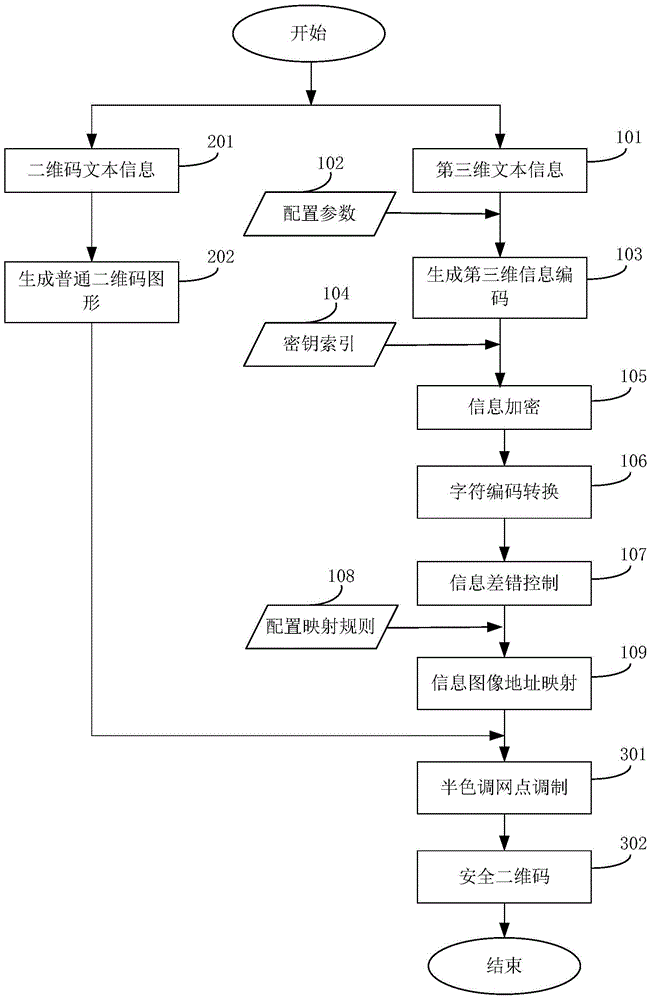
The embodiment of the invention discloses a safe two-dimensional code manufacture method and decoding method, and a safe two-dimensional code identifier. The safe two-dimensional code manufacture method comprises the following steps: according to a two-dimensional code coding rule, obtaining a data storage area of a two-dimensional code, implanting a plurality of black and white microdots and a structure, which is formed by the relative positions of the microdots, of the black and white microdots into the data storage area, wherein the black and white microdots and the structure represent implanted information; and implanting the black and white microdots and the structure into the storage area of the two-dimensional code to form a safe two-dimensional code. The scheme solves the defects of low safety, replicability and the like of the common two-dimensional code. The safe two-dimensional code provided by the invention and a safe two-dimensional code identifier which uses the safe two-dimensional code can be widely applied to various information service systems including intellectual property protection, object authentication, anti-counterfeiting traceability and the like.
Owner:北京兆信信息技术股份有限公司
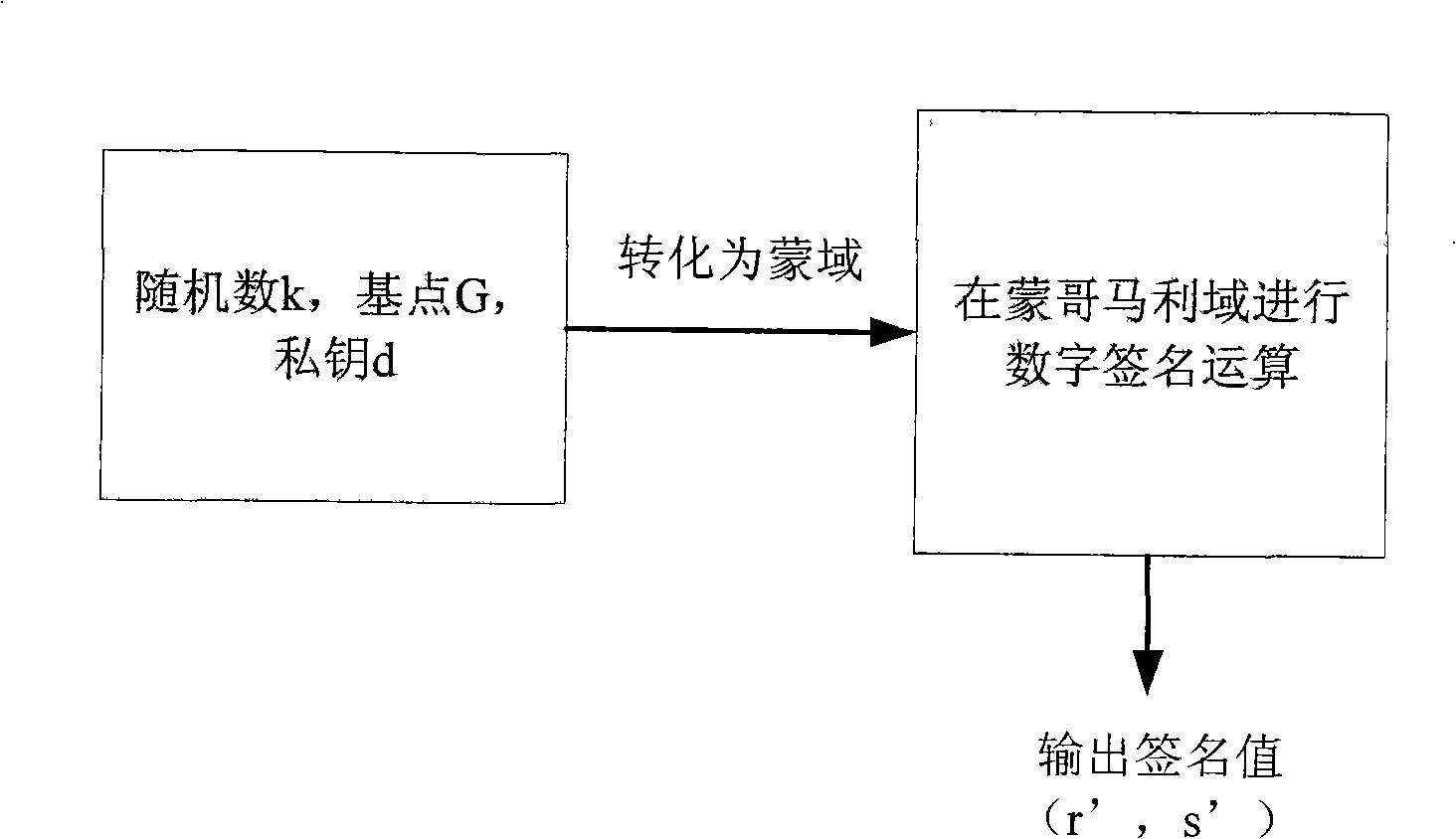
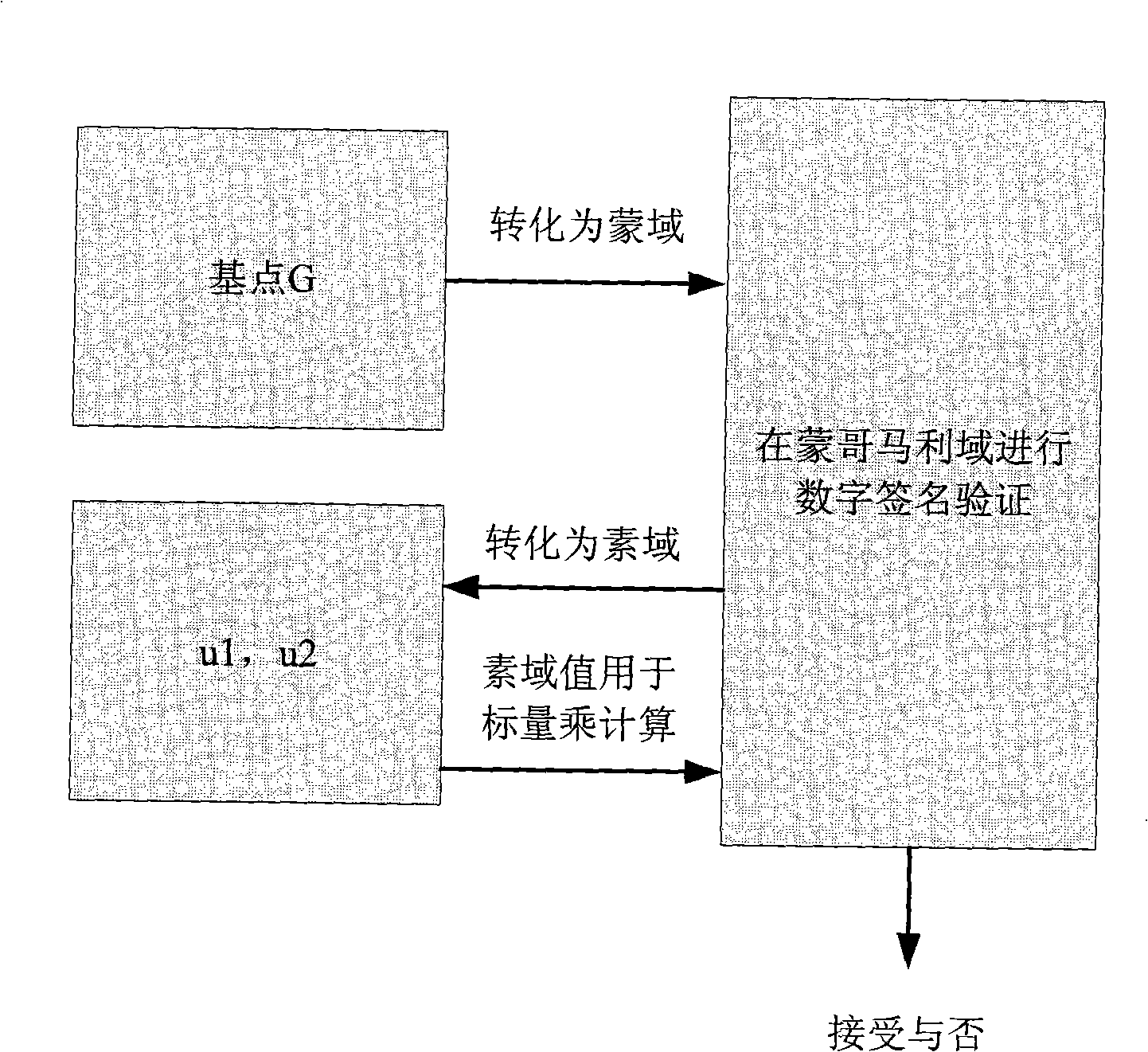
Digital signature scheme based on ECC
The invention discloses a digital signature proposal based on ECC. Scalar multiplication of an elliptic curve, point addition and Montgomery field modulo algorithm, etc. are usedfor realizing fast digital signature and signature verification. In the proposal, a method for replacement is adopted for treating random numbers which do not meet requirements, thus preventing the process for generating the random numbers again; the methods such as the replacement, interception and zeroizing are adopted to treat hash values, thus preventing frequent switch between large prime field and Montgomery field; the operations of signature and verification are basically in the Montgomery field, thus preventing time-consuming operation of modulo reduction. The digital signature proposal can be used in environments such as e-business, content protection interface, banking system, military communication, and intellectual property right protection, etc.
Owner:SICHUAN PANOVASIC TECH
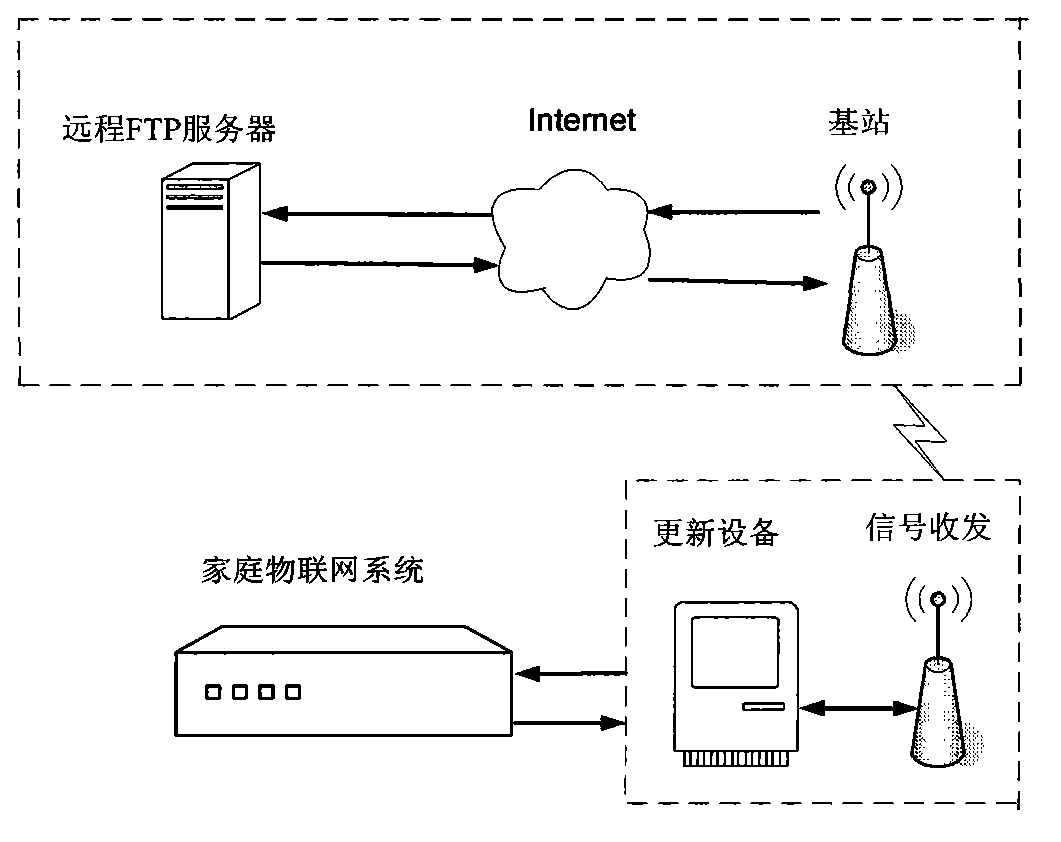
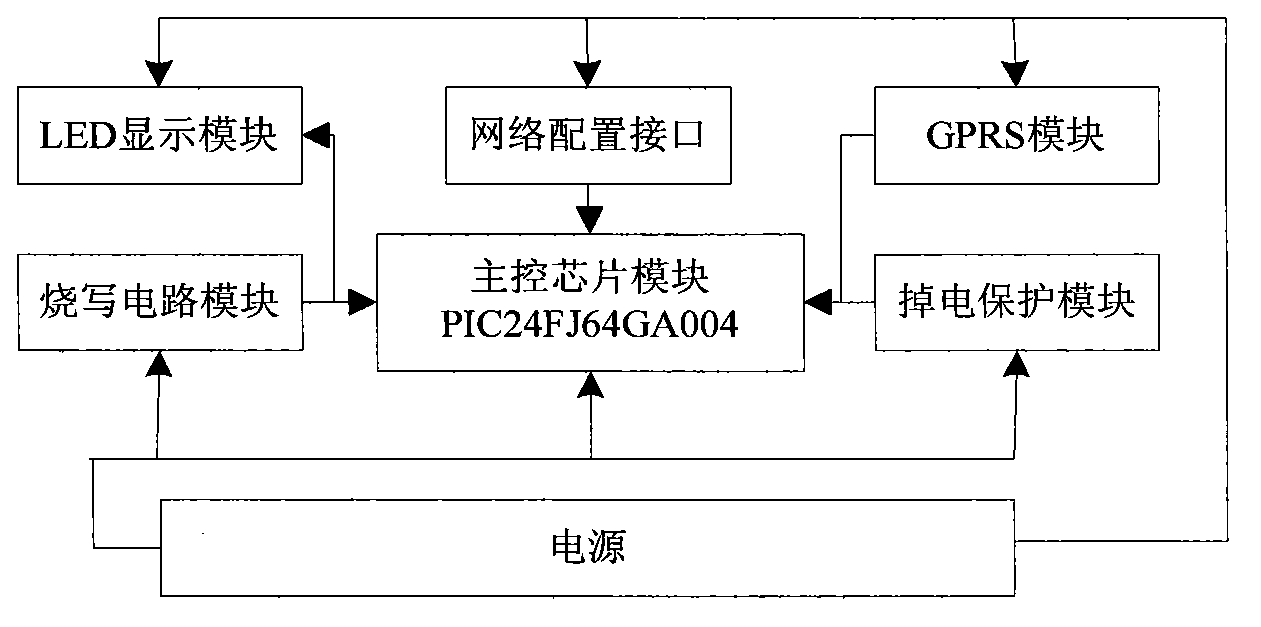
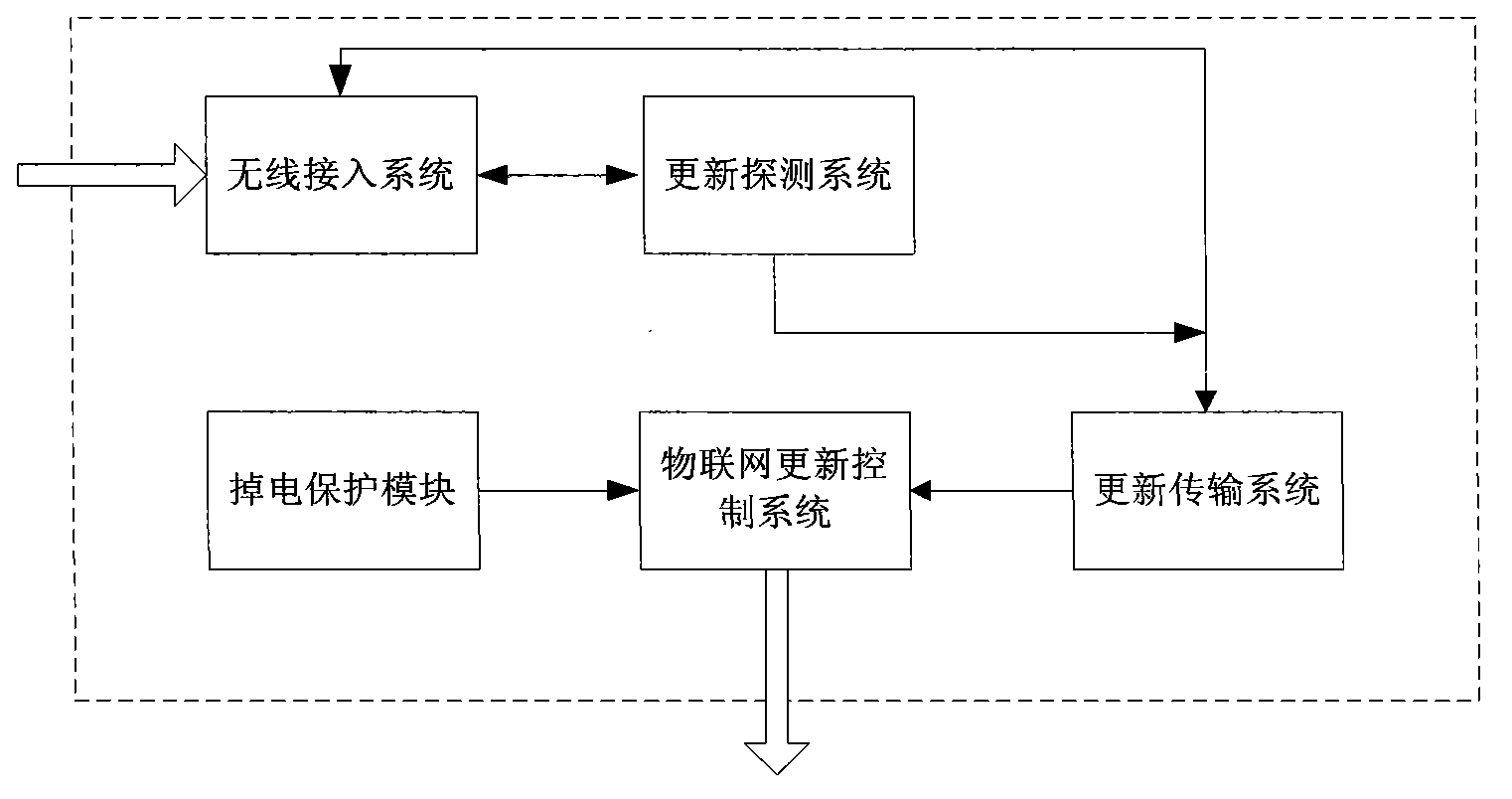
Automatic long-distance updating system and method for family Internet of Things system
InactiveCN103227813ANo regional restrictionsSmartProgram loading/initiatingTransmissionGeneral Packet Radio ServiceThe Internet
The invention discloses an automatic long-distance updating system and an automatic long-distance updating method for a family Internet of Things system. The automatic long-distance updating system comprises a main control chip module, a general packet radio service (GPRS) module, a network configuration interface module, a programming circuit module, a power down protection module and a light-emitting diode (LED) module. The invention mainly solves the problem of implementation of long-distance automatic updating of a firmware control system under the Internet of Things application environment. The technology is realized by automatically finding updating program without manual intervention so as to realize real-time automatic wireless updating, and has high operability and usability. In addition, the invention takes the intellectual property protective function of software into consideration, so information can be automatically eliminated after outage.
Owner:CHONGQING COLLEGE OF ELECTRONICS ENG
Method, apparatus and information unit for establishing, analyzing and affirming article identity information
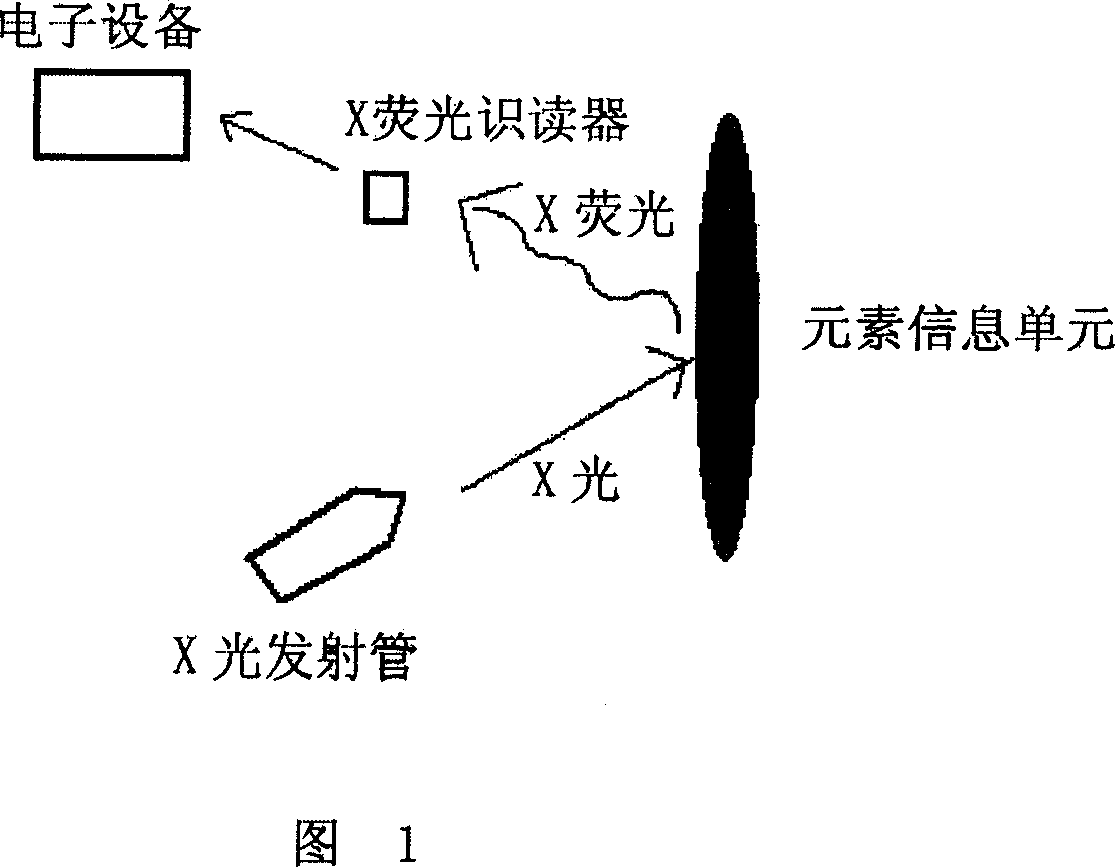
InactiveCN101078731AWon't breakAvoid breakingMaterial analysis using wave/particle radiationCharacter and pattern recognitionLogistics managementComputerized system
The invention discloses a method for building, analyzing and confirming goods identity information. Goods element in itself and setting element set on goods are sued as goods element information unit. As reading device reads the element information unit goods identity information can be built, analyzed and confirmed. The invention also provides the reading device realizing said method, the computer system connected with the reading device and said element information unit. The invention can be applied almost all materials conveniently. It can be used in goods identity authentication, safety authentication, insignia / evidence authentication, bank bill / voucher authentication, intellectual property protection, remote management, information management, duty decision, duty trace, commodities fleeing prevention, logistics monitoring, asset preservation, analysis and statistic, tort early-warning, supervision check, government procurement, door-forbidden management, file transfer and judicature basis.
Owner:TRUE PROD ID TECH BEIJING
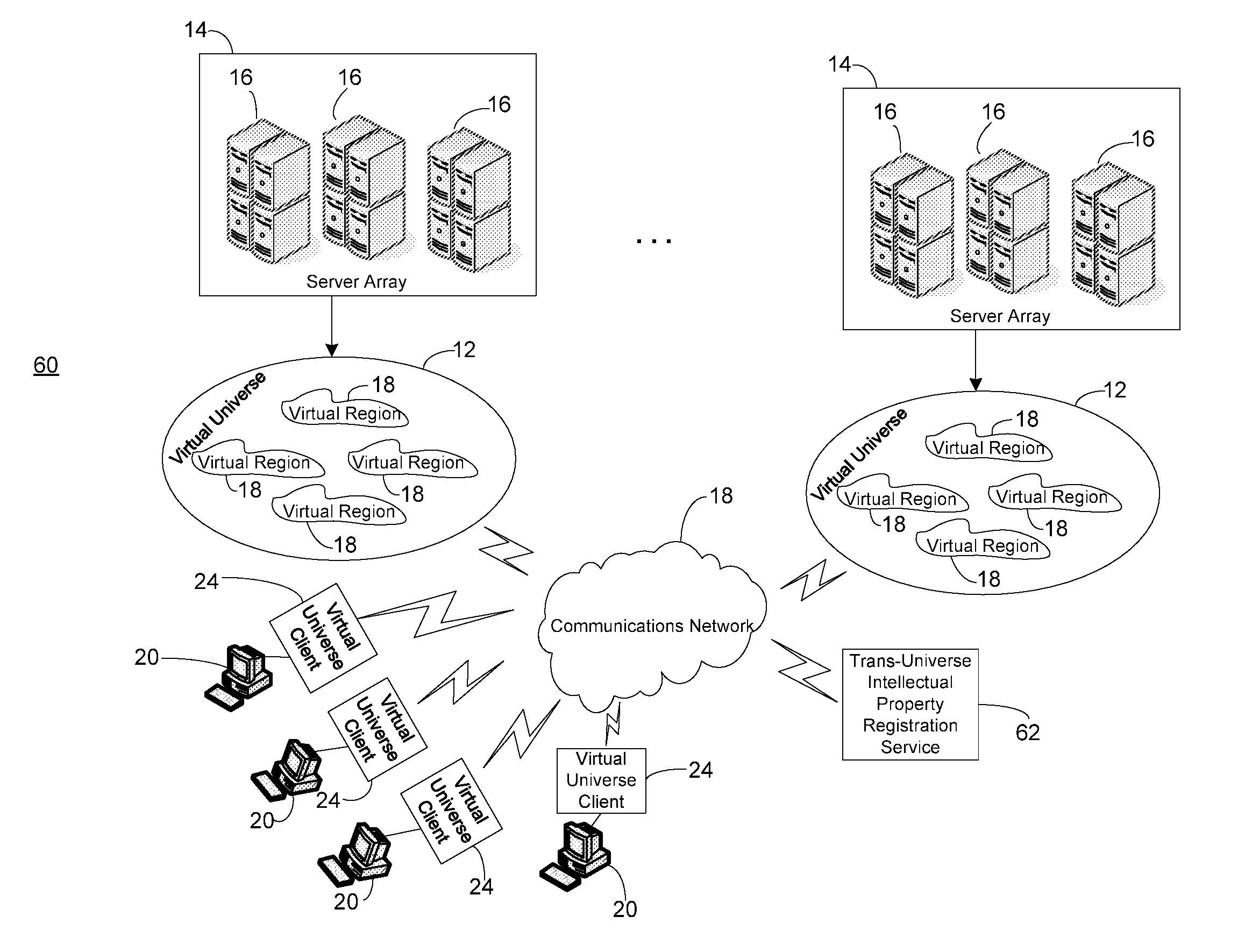
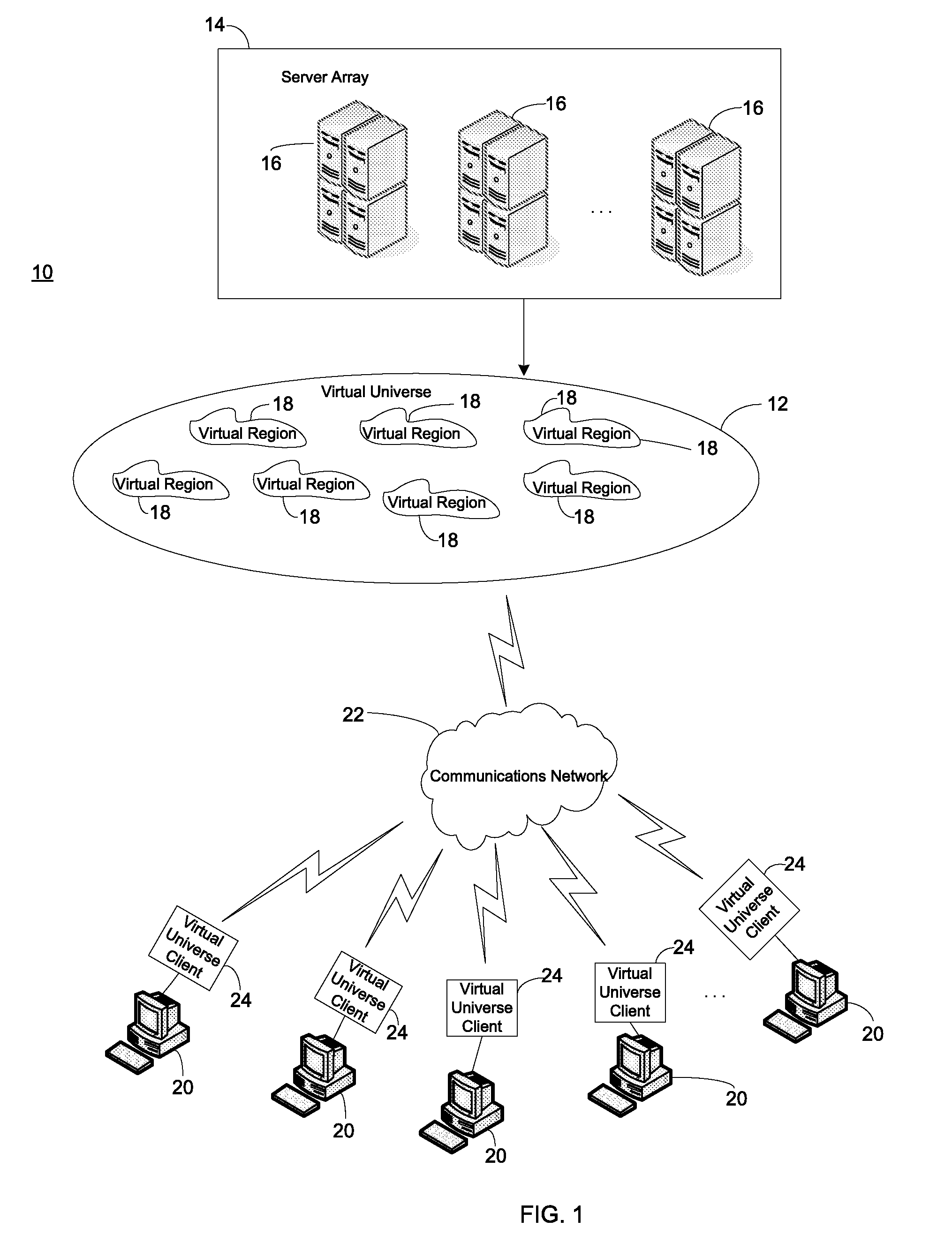
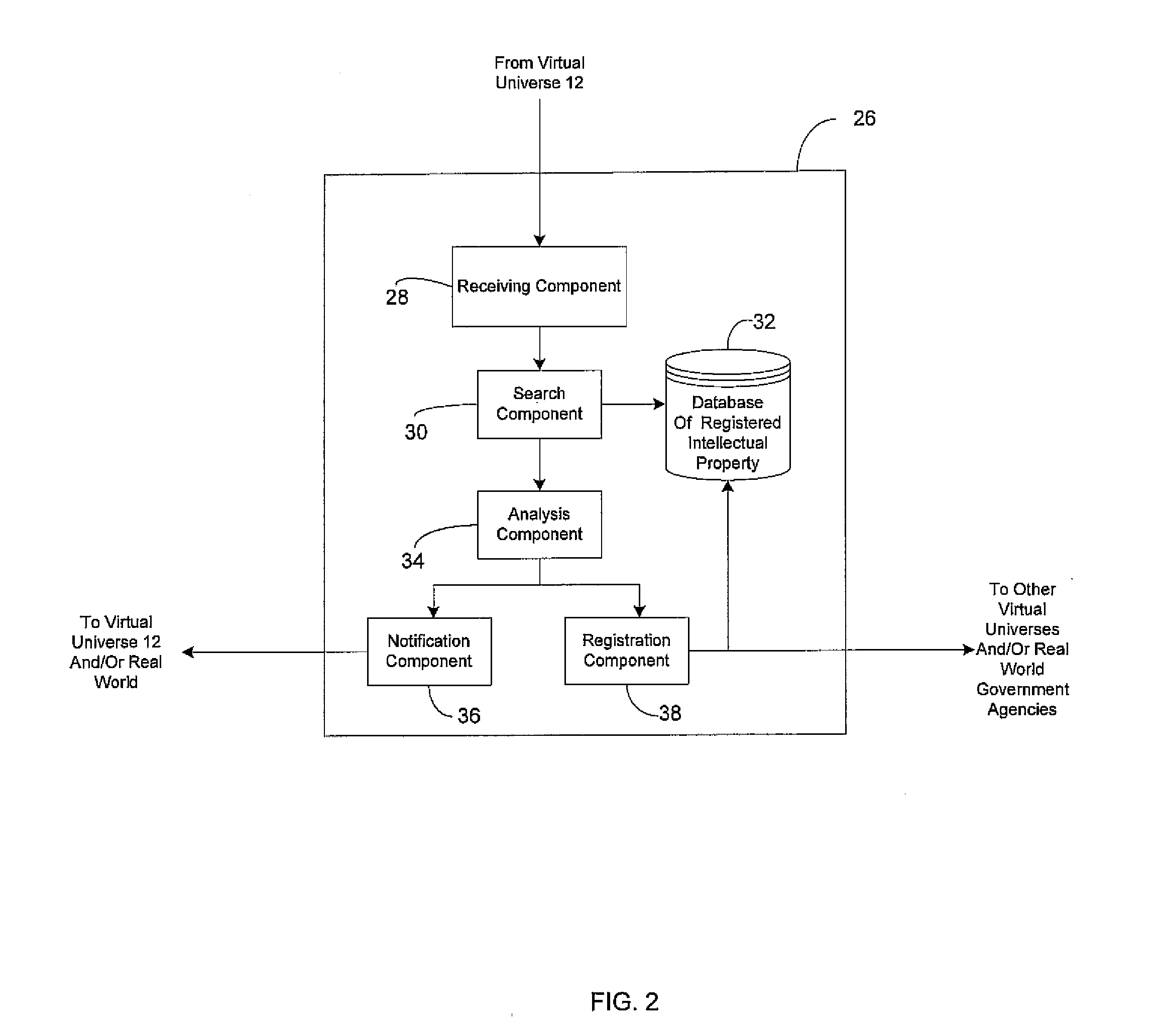
Intellectual property protection for content created within a virtual universe
An approach that protects intellectual property rights in content created by users of a virtual universe is described. In one embodiment, there is an intellectual property rights protection tool for use in a virtual universe. A receiving component is configured to receive a request to protect intellectual property rights in content created by a user of the virtual universe. A database is configured to store content created by users of the virtual universe that have intellectual property rights therein. A search component is configured to search the database for content created by users of the virtual universe that have intellectual property rights therein that is similar to the content created by the user. An analysis component is configured to determine whether any preexisting intellectual property rights in content stored in the database precludes intellectual property protection of the content created by the user.
Owner:IBM CORP
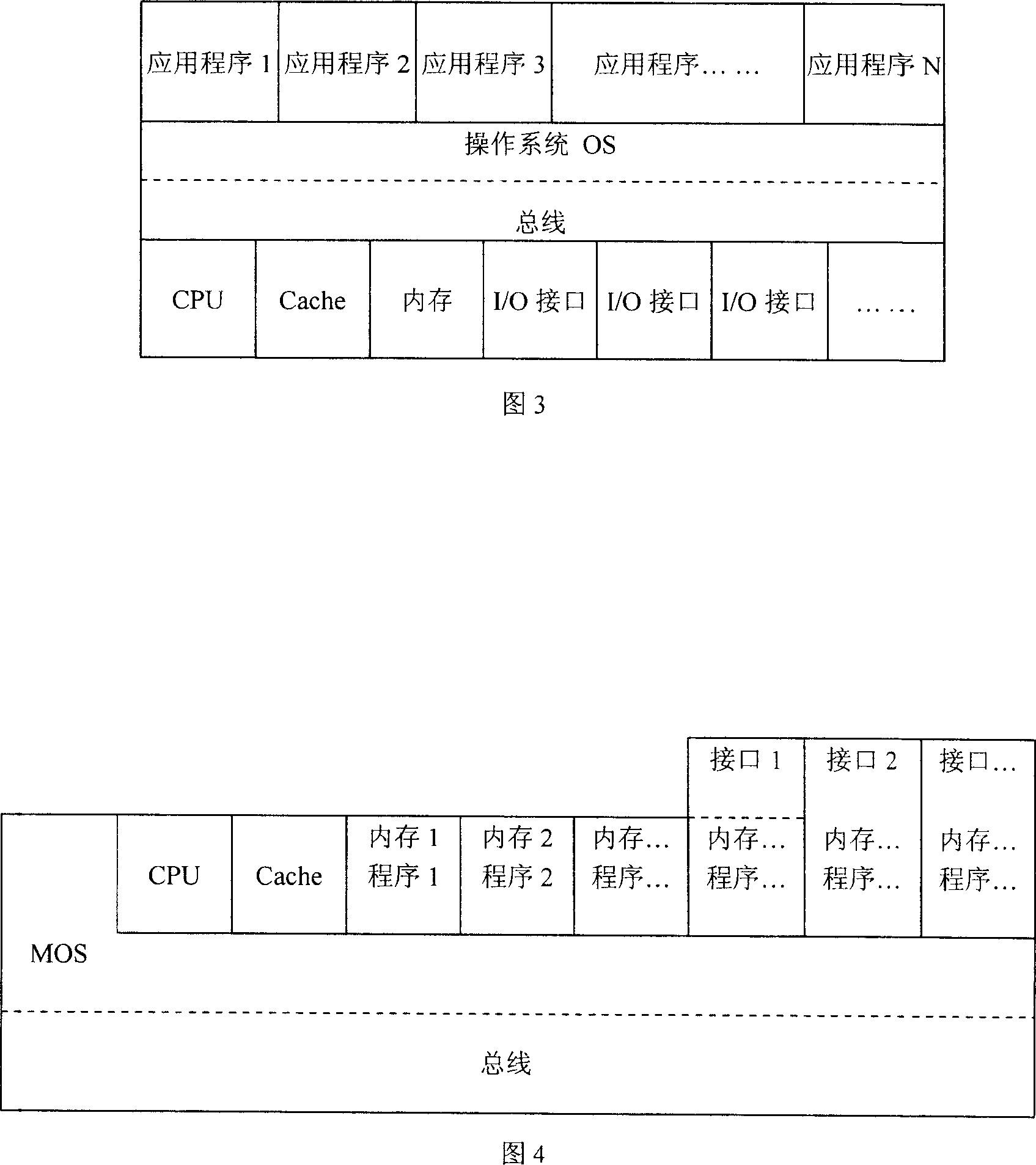
Block-model computer and operating system
InactiveCN101071409AGeneral purpose stored program computerProgram loading/initiatingComputer usersOperational system
The invention involves a new type of general computer - building blocks computers (NewCs) and the operating system (MOS), which is based on a new concept of the foundation, and can be used in all areas of social life. Building blocks of all computer hardware, software and interfaces have been designed and manufactured in the form of a module - building blocks, it theoretically has unlimited capacity for expansion. According to choose people use building blocks. Then they will be combined into fitness and computer user needs. Its operating system (MOS) is a multi-tasking real-time operating system, which will logically link these building blocks, and the control and operation of the computer operation, all of the features of the computer. Building blocks in the structure of computers and PC completely different, it efficient, uses broad, low investment, high security, to protection of intellectual property rights, breaking Intel hardware and Microsoft software monopoly status, and enhance China in the field of international computer status.
Owner:曲卫晶
Big data-based source code comprehensive evaluation platform
ActiveCN108710564ASolve cloneResolve detectionReverse engineeringSoftware testing/debuggingData displayComputer cluster
Owner:苏州棱镜七彩信息科技有限公司
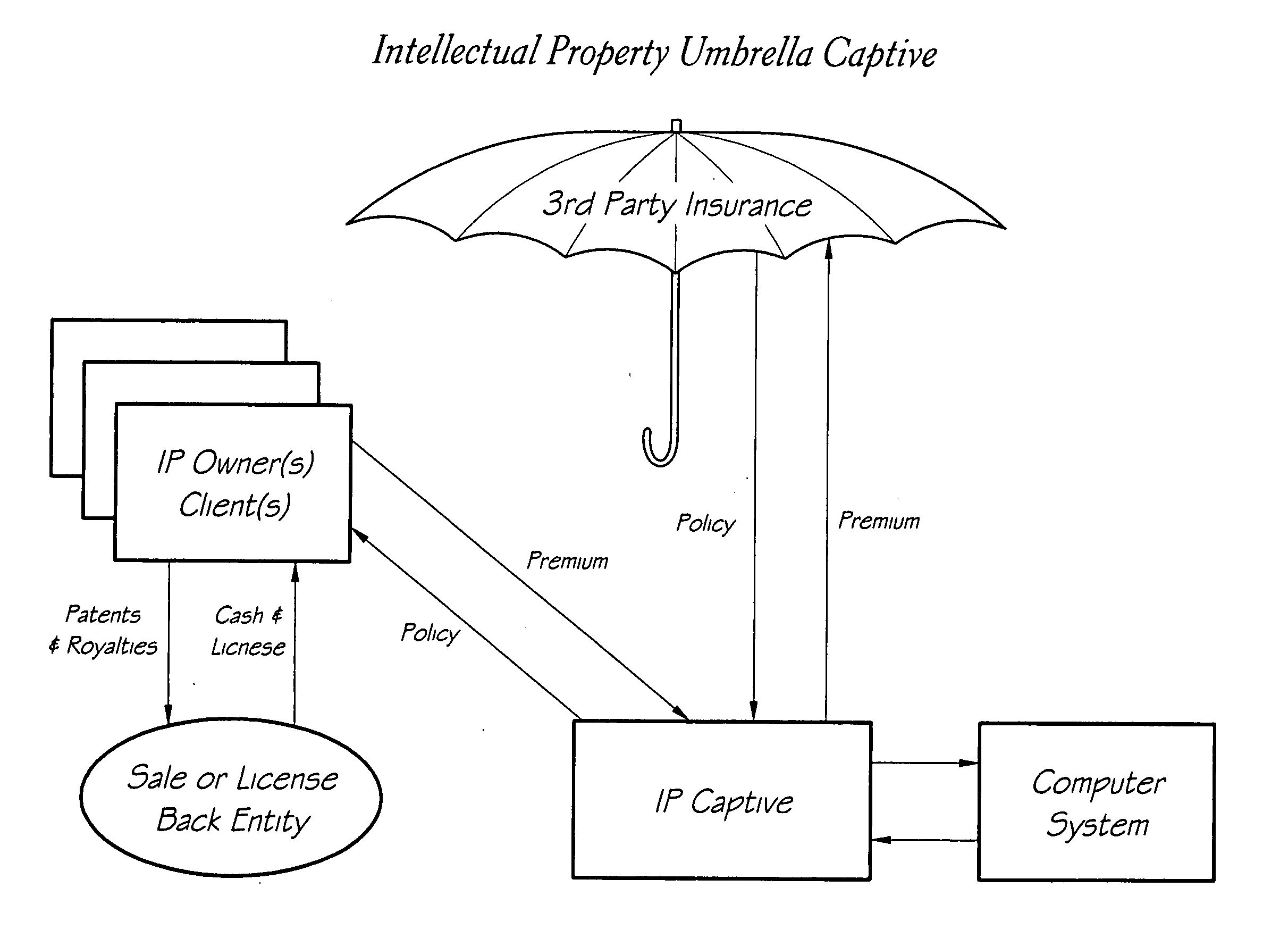
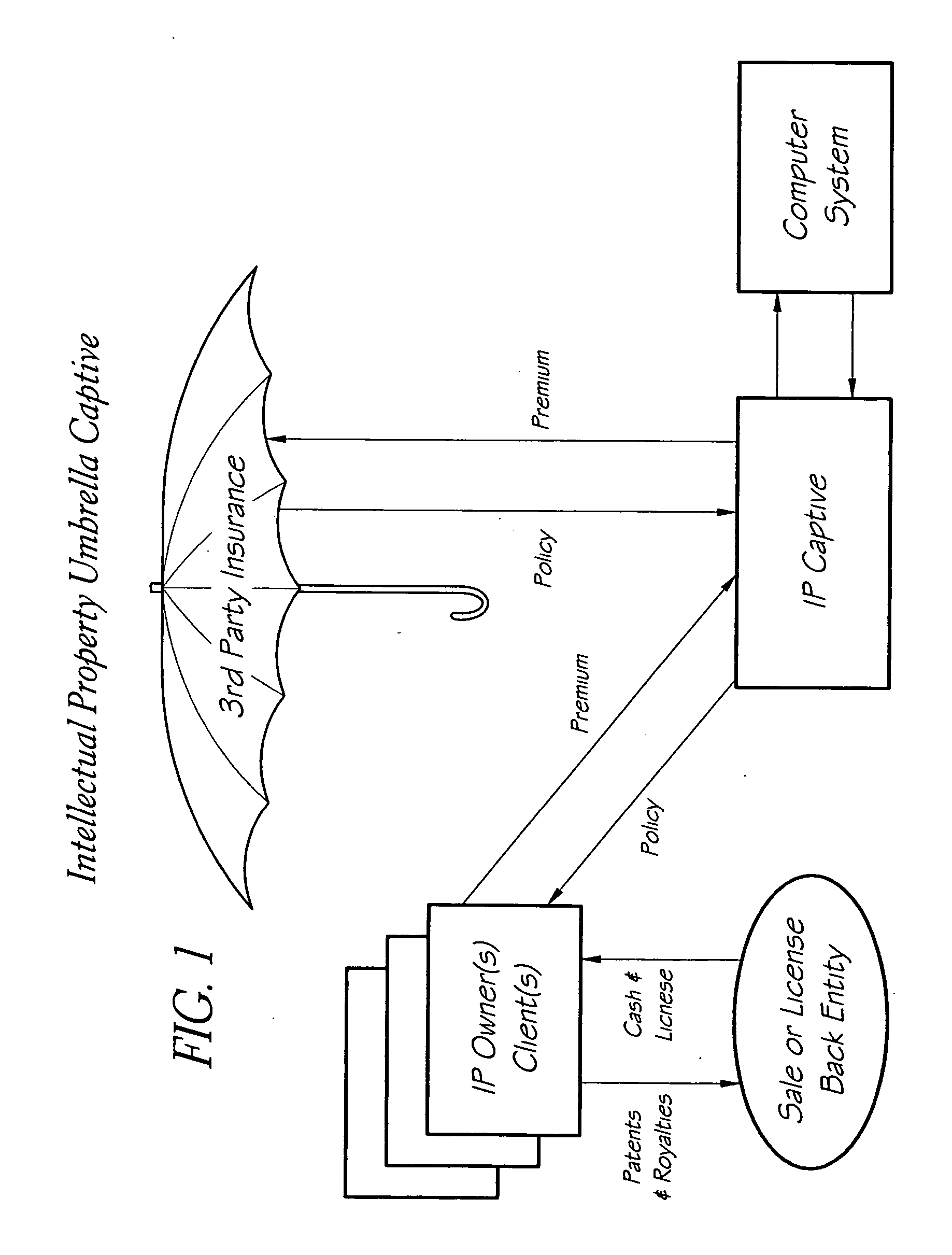
Intellectual property umbrella captive insurer
One embodiment of the invention is a proactive intellectual property (IP) risk management tool, such as an intellectual property umbrella captive (IPUC). In some embodiments, execution of the IPUC includes an initial assessment of the IP Value-at-Risk (Phase I); creation and funding of the required structure (Phase II); and implementation of the necessary process and control elements to manage the identified risks (Phase III). Coincident with formation, patent Sale / License-Back (“S / LB”) options as well as reinsurance or umbrella insurance policies preferably exist to enhance or accelerate execution.
Owner:OCEAN TOMO
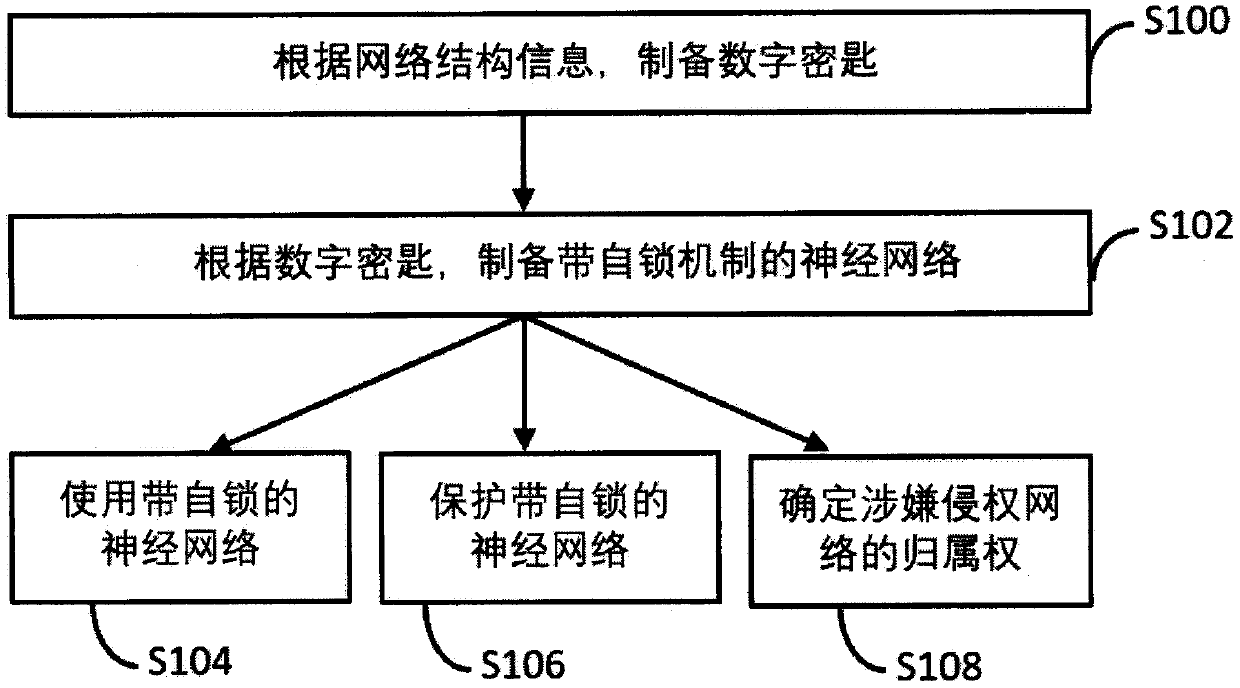
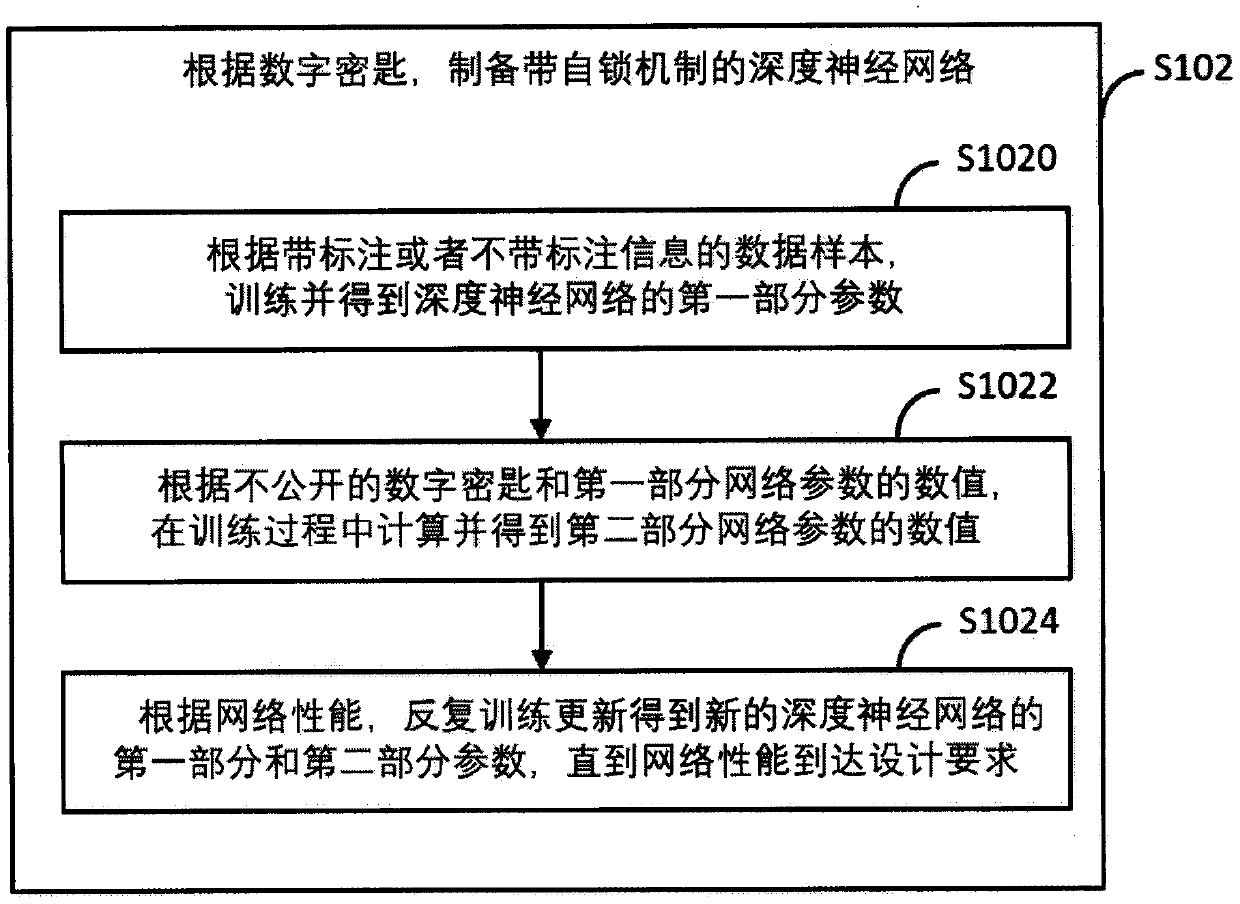
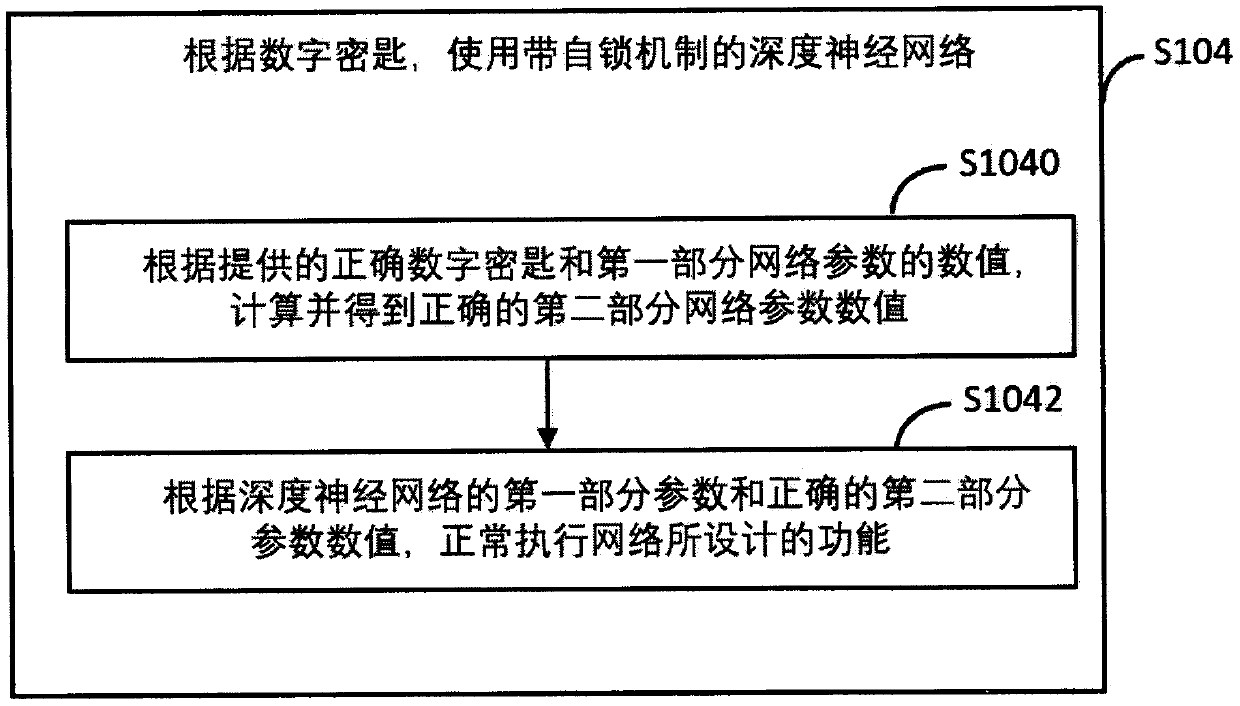
Intellectual property protection method and system for deep neural network and terminal
ActiveCN109919303AData processing applicationsNeural architecturesLocking mechanismProtection mechanism
The invention belongs to the field of artificial intelligence. Through a skillfully designed self-locking mechanism, the intellectual property of any deep neural network is protected, and an illegal infringement behavior is stopped in time. The self-locking mechanism comprises two core processes: firstly, when a neural network is trained, a specific digital key is used for locking processing; Andsecondly, when the neural network is used, the processed neural network can play a normal role only by key matching. In terms of the timeliness and the right protection cost of right protection, the self-locking mechanism provided by the invention has obvious advantages that a pirate network without key matching cannot play a normal function and cannot compete with a legal authorized network. Dueto the fact that a stealer cannot benefit from the motivation machine, infringement does not exist. On the contrary, a traditional digital watermark protection mechanism can only prove the ownership of the neural network, rights protection must pass legal ways, the timeliness is poor, and the cost is high.
Owner:FANDWORK TECH NANJING CO LTD
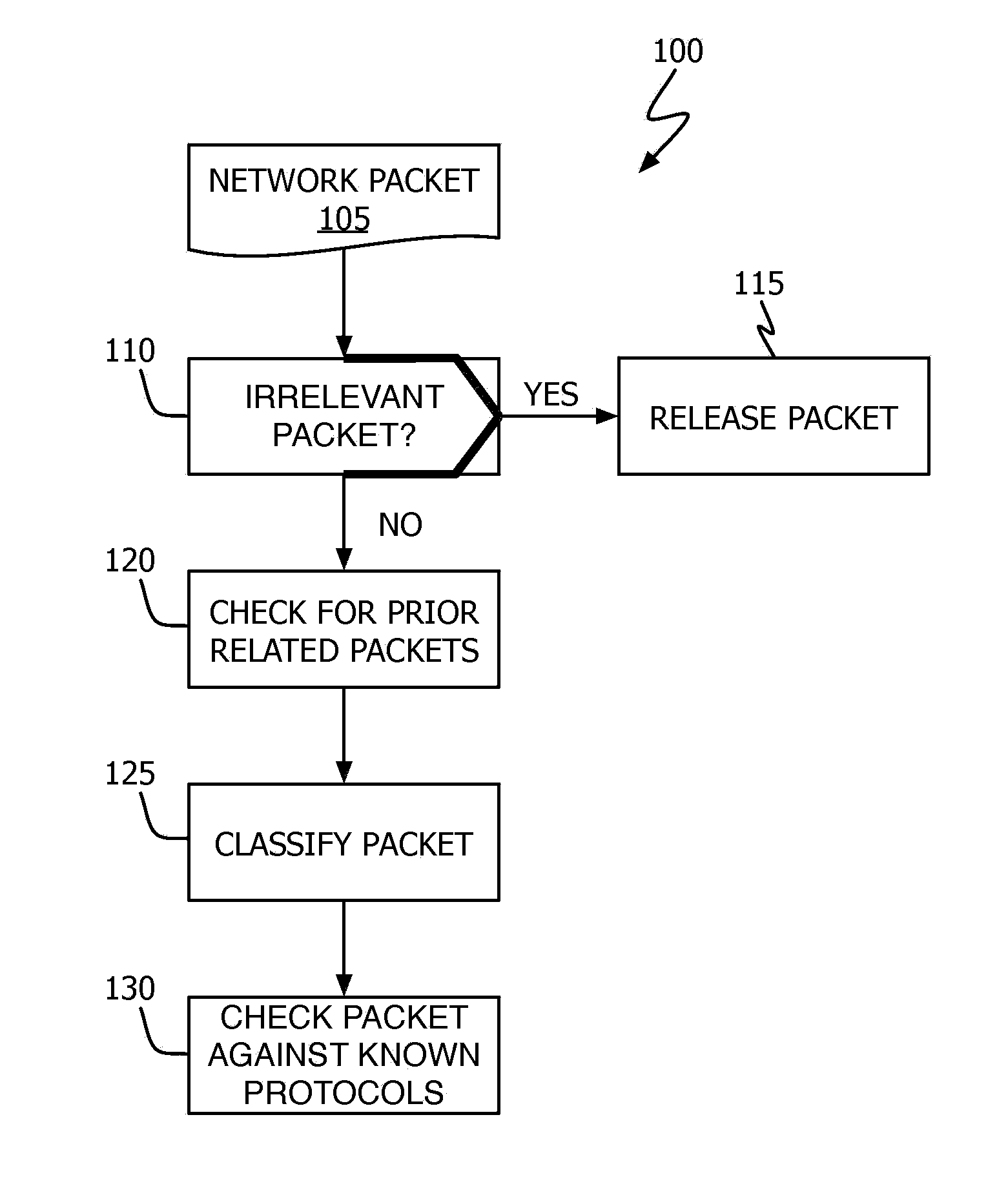
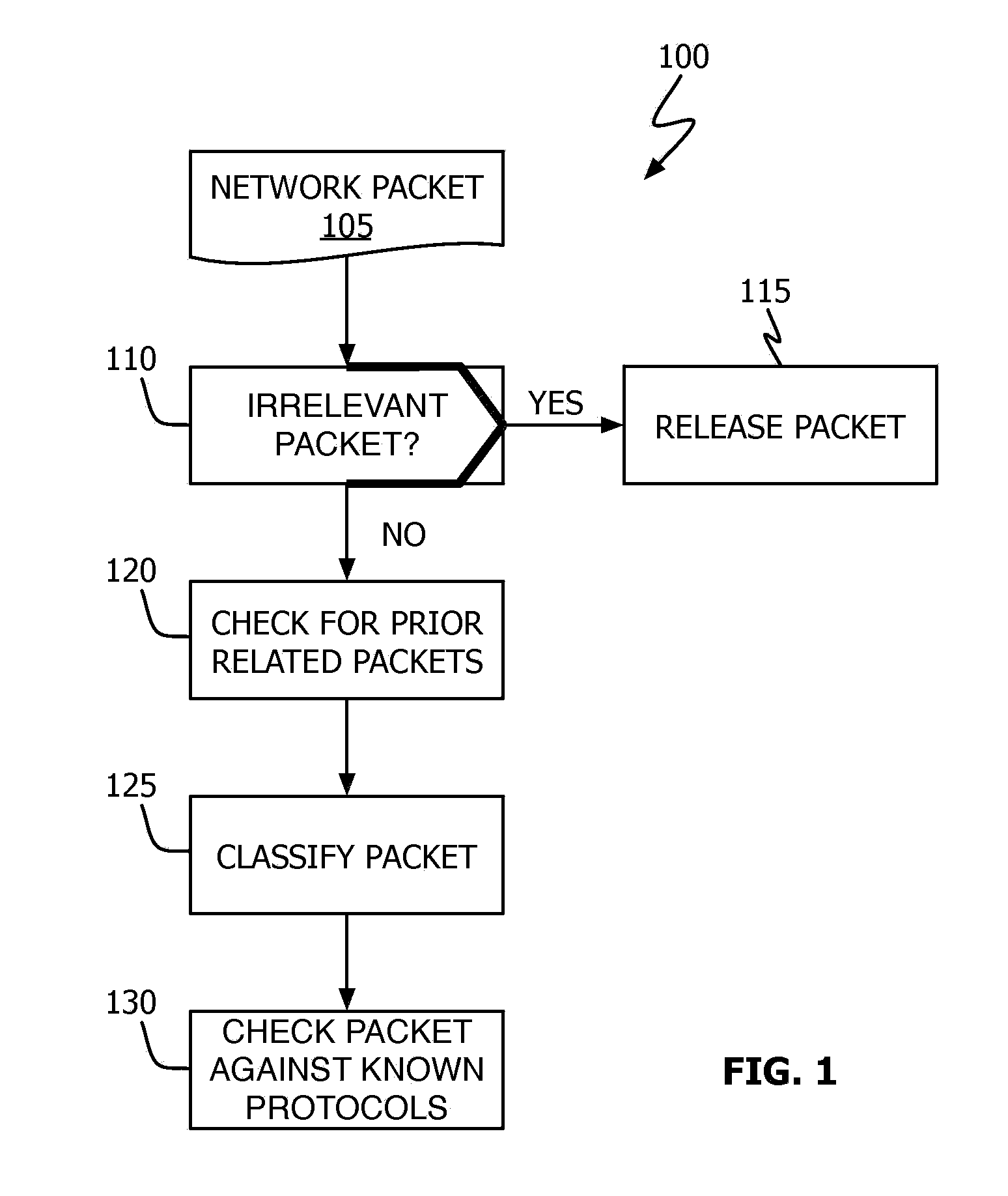
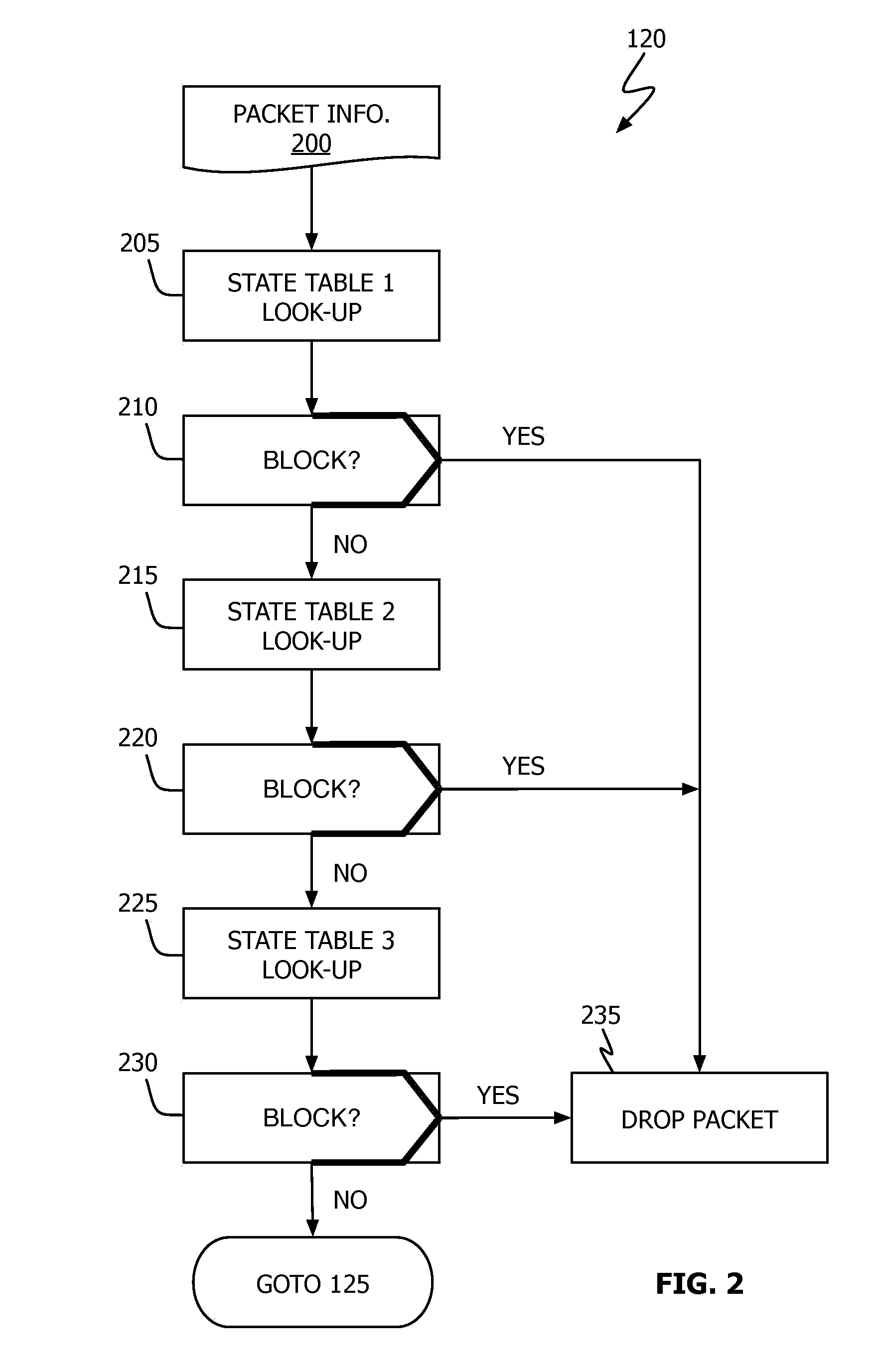
Network Monitoring And Intellectual Property Protection Device, System, And Method
A method and device for detecting and halting specified peer-to-peer (“P2P”) and / or Internet Relay Chat (“IRC”) communication sessions based on a priori defined templates is described. Network packets are intercepted and inspected for patterns (defined by the templates) that identify them as definitely, likely or not being associated with one of the specified P2P and / or IRC protocols. Those packets identified as definitely belonging to one of the specified protocols are prevented from reaching their target destination. Those packets identified as only likely belonging to one of the specified protocols are permitted to continue toward their target destination after select information about the particular session / packet is recorded for later use. Those packets identified as not belonging to one of the specified protocols are permitted to continue to their target destination.
Owner:FAHMY SAFWAT F
Method for protecting online education and teaching video property rights by using block chain technology
PendingCN112307440AGuaranteed privacyUniqueness guaranteedDatabase distribution/replicationDigital data protectionInternet privacyEngineering
The invention relates to the technical field of intellectual property protection, and discloses a method for protecting online education and teaching video property rights by using a block chain technology, which comprises the following steps: S1, sending an online education and teaching video registration request to a block node; s2, performing hash operation on the online education and teachingvideo data through a block chain, uploading and registering an obtained hash operation value, and generating a platform signature; according to the invention, hash operation is carried out on different contents, the obtained hash value results are generally different, and then the platform signature is generated by utilizing the hash value obtained by the hash operation and the private key, so that the uniqueness and authenticity of the signature can be ensured; by adopting the steps 7 and 8, when infringement occurs, infringement evidences can be found out in time, infringement events can besolved rapidly and timely, losses of all people are reduced, continuous improvement of teaching video quality is facilitated through protection of online education teaching video intellectual propertyrights by the block chain technology, and the motivation of developers is stimulated.
Owner:YUNNAN NORMAL UNIV
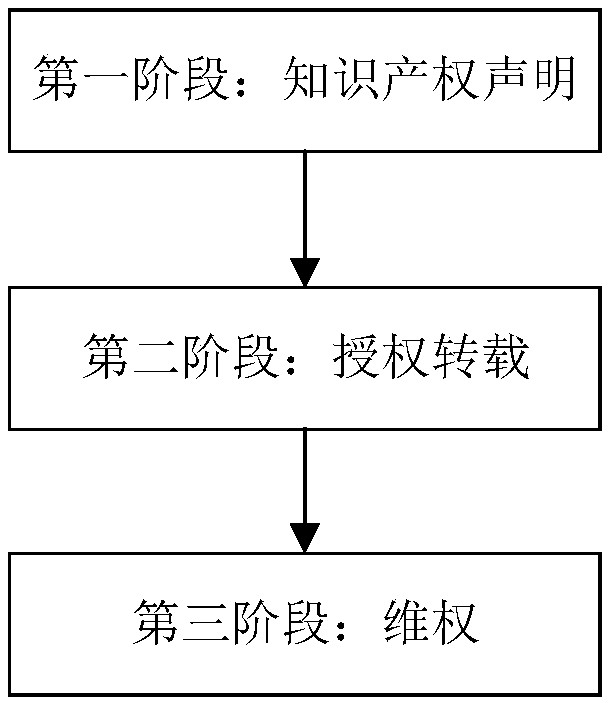
Block chain-based Internet essay intellectual property protection method
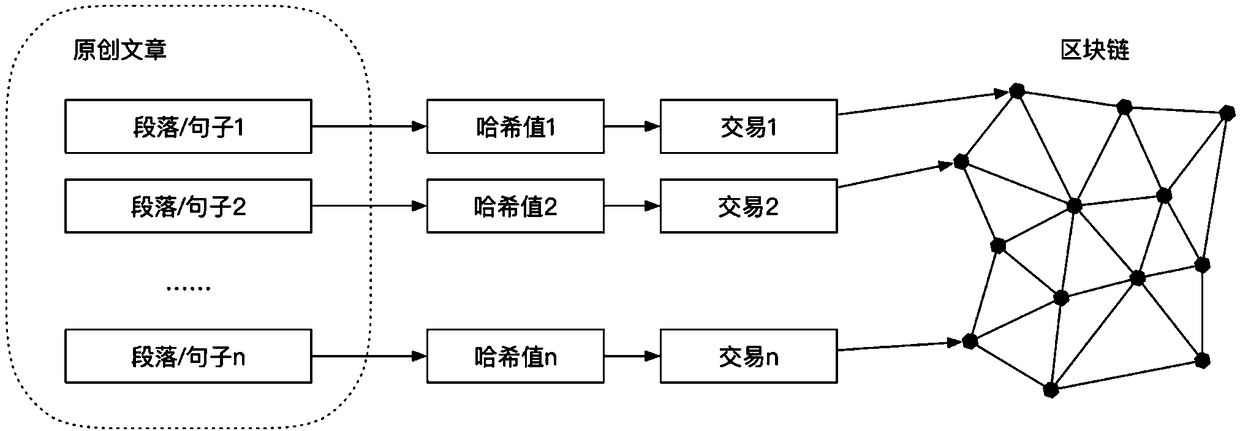
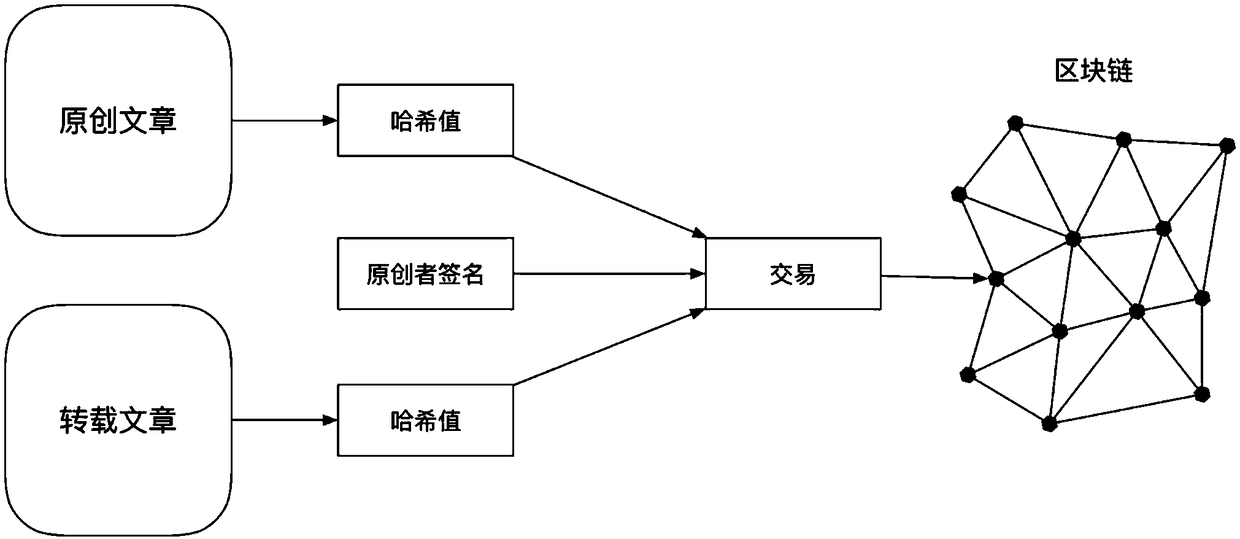
InactiveCN108881244ASolve plagiarismEasy maintenanceFinanceTransmissionArray data structureGranularity
The invention belongs to the field of intellectual property protection, and provides a block chain-based Internet essay intellectual property protection method for solving the technical problems thatin existing Internet essay intellectual property protection, whether or not the work is infringed is difficult to detect, and quantization on the plagiarism degree is in deficiency. The block chain-based Internet essay intellectual property protection method comprises the following steps of intellectual property rights stating in the first stage; reprinting authorization in the second stage; and rights protection in the third stage. According to the method, the granularity of Internet essay intellectual property protection can be set, an original author of an Internet essay can state the Internet essay intellectual property in a fine granularity mode, after it is discovered that the Internet essay is infringed, illegal reprinted content is subjected to Hash processing by a server and thencompared with a Hash value array of the original article to obtain a reprinting proportion value, and then the plagiarism degree is quantized; and accordingly, the original author can more conveniently protect the rights of the original author according to the infringing degree of an infringer, and the protection effort on the network essay intellectual property is increased.
Owner:NAT UNIV OF DEFENSE TECH
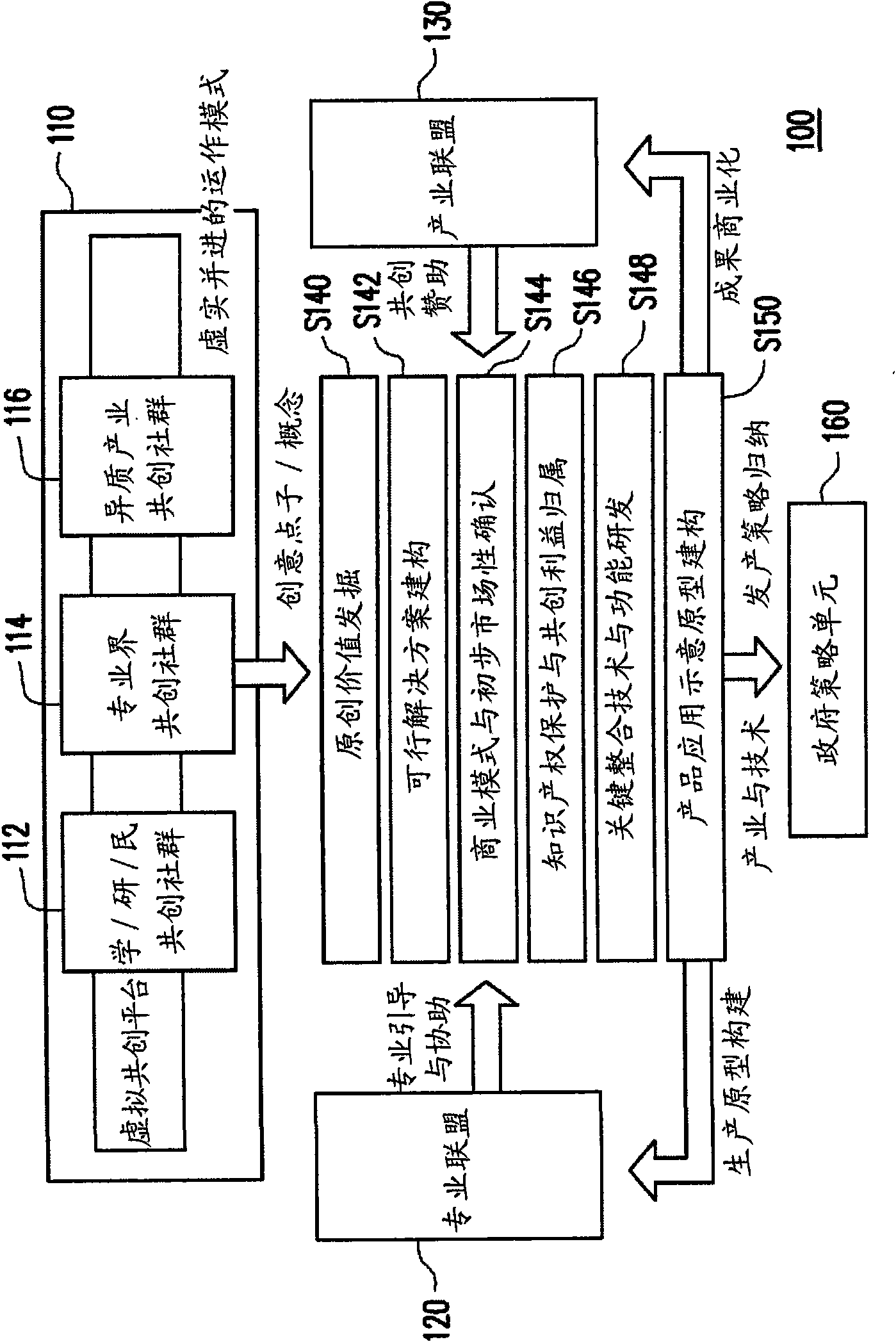
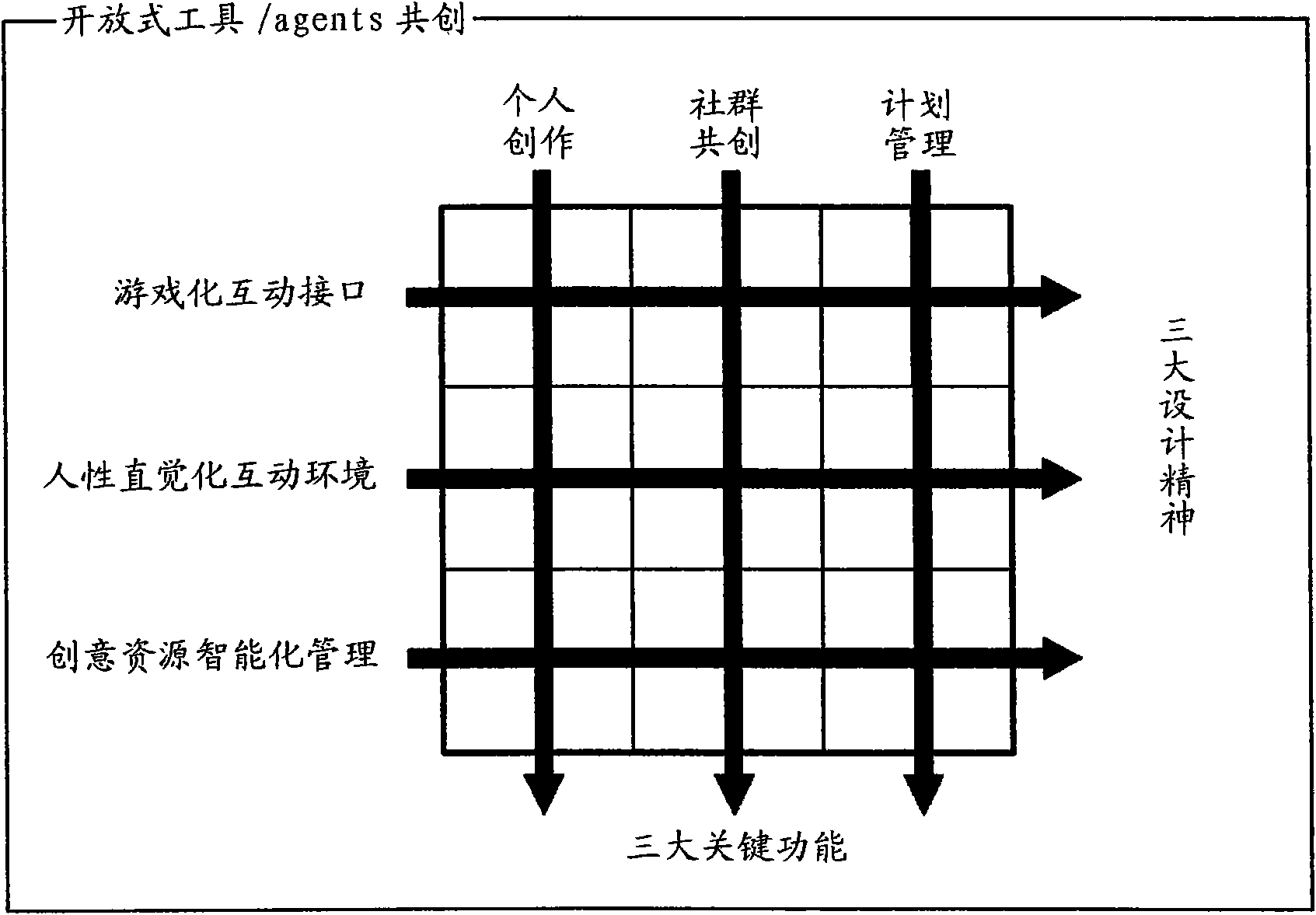
Open type innovation co-creation platform capable of simultaneously carrying out deficiency and excess and operation method thereof
The invention discloses an open type innovation co-creation platform capable of simultaneously carrying out deficiency and excess and an operation method thereof. The open type innovation co-creation platform comprises an operation module capable of simultaneously carrying out deficiency and excess, a professional association and a business association. In the operation mode of simultaneously carrying out the deficiency and excess, the idea and conception of creative idea are generated. The professional association provides professional guidance or assistance to obtain the feedback built by a production model. In addition, the business association raises requirements and sponsorship so as to obtain the feedback of a commercialized result. The raised innovative ideas and conceptions explore innovative values under the guidance or assistance provided by the professional association, and a feasible solution is found and is built. After the determination of a commercial mode and preliminary marketability, the discussion on intellectual property protection or mutual benefit affiliation is carried out. The further development on key integrated technology and function development is carried out, then production implementation demonstration is displayed, and the model product is convenient to be in line with business or technical plans.
Owner:IND TECH RES INST
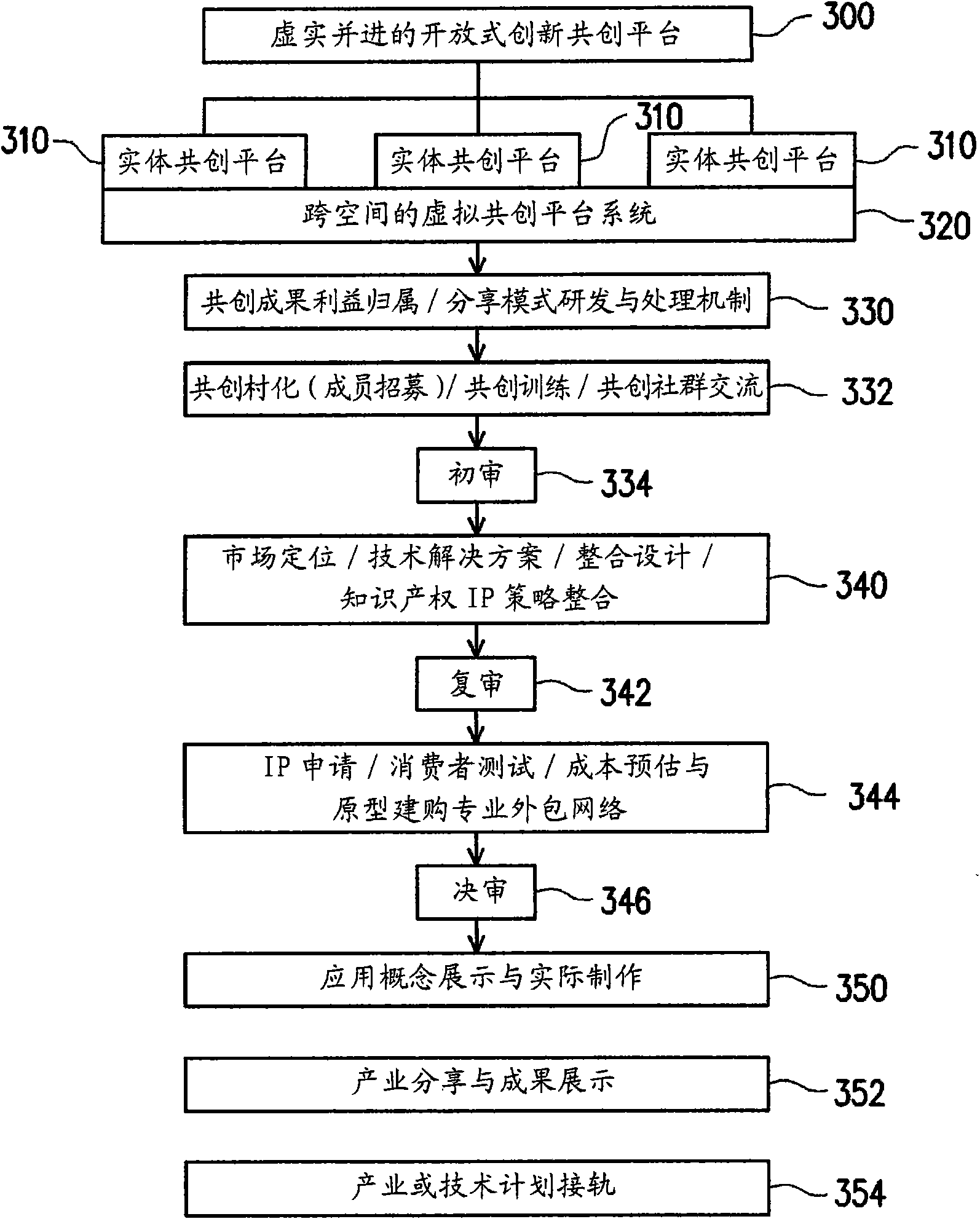
Industrial cloud platform-based creativity conversion system and method
InactiveCN107578213AShorten the development cycleShorten the production cycleOffice automationSoftware systemInformation transfer
The invention discloses an industrial cloud platform-based creativity conversion method in the field of software systems. The method comprises the following steps of: creativity collection: collectingcreativities of creators through a creator service forum and sending the creativities to a collaborative research and development forum; collaborative research and development: researching and developing the received creativities in the collaborative research and development forum, carrying out intellectual property protection on the obtained achievement, and consigning the achievement to a collaborative manufacture forum; and collaborative manufacture: converting the obtained achievement in the collaborative manufacture forum and finally popularizing and applying the converted achievement. The method is capable of overcoming the defect that the traditional marketing, design, manufacture and verification processes in the manufacturing industry are long in time consumption, slow in information transfer and weak in mass participation, enhancing the design and production ability and efficiency, and enabling the product quality to obtain best guarantee, and can be used in the enterprise production, research, development and management.
Owner:NINGXIA KOCEL MOLD
Distributed technology transfer department
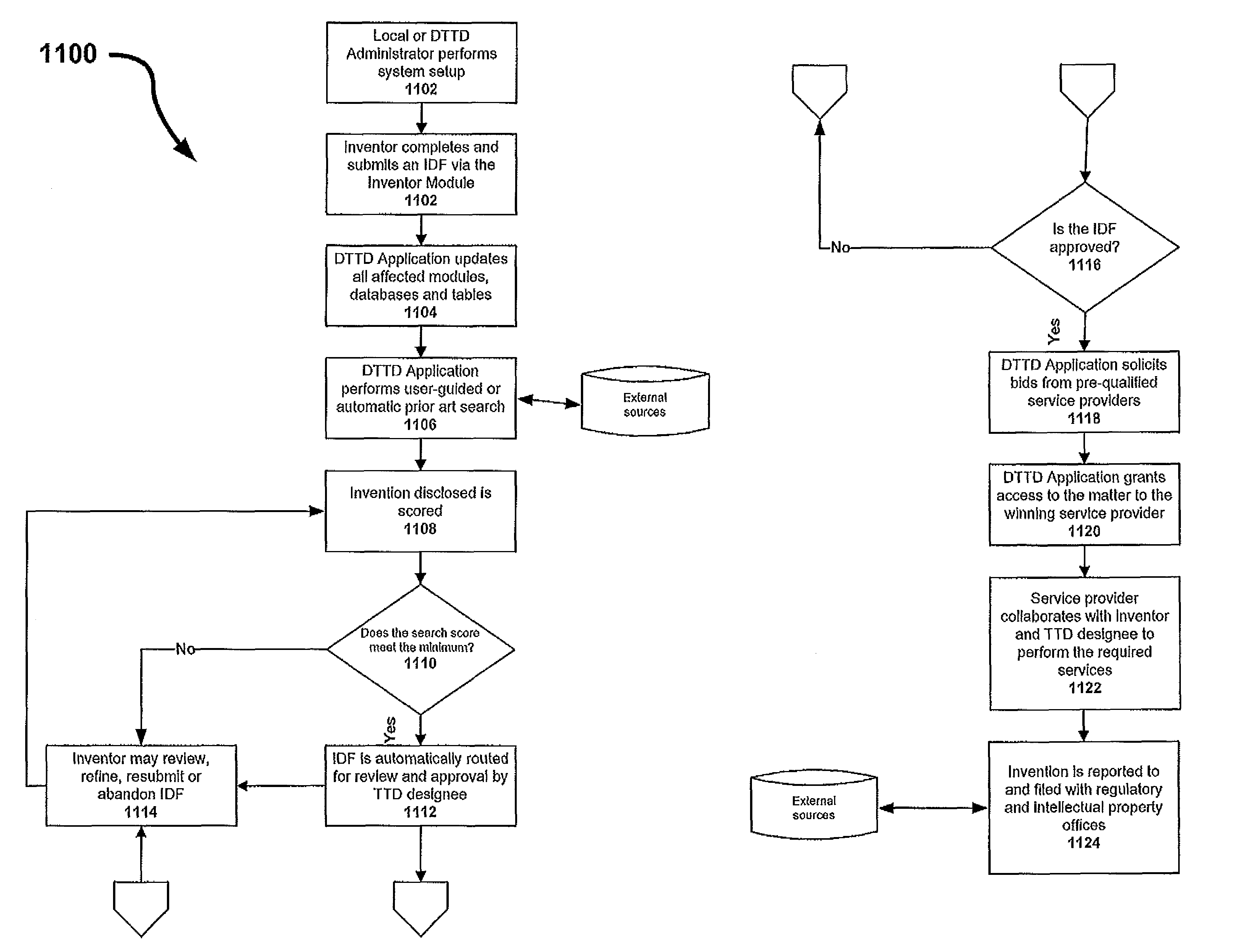
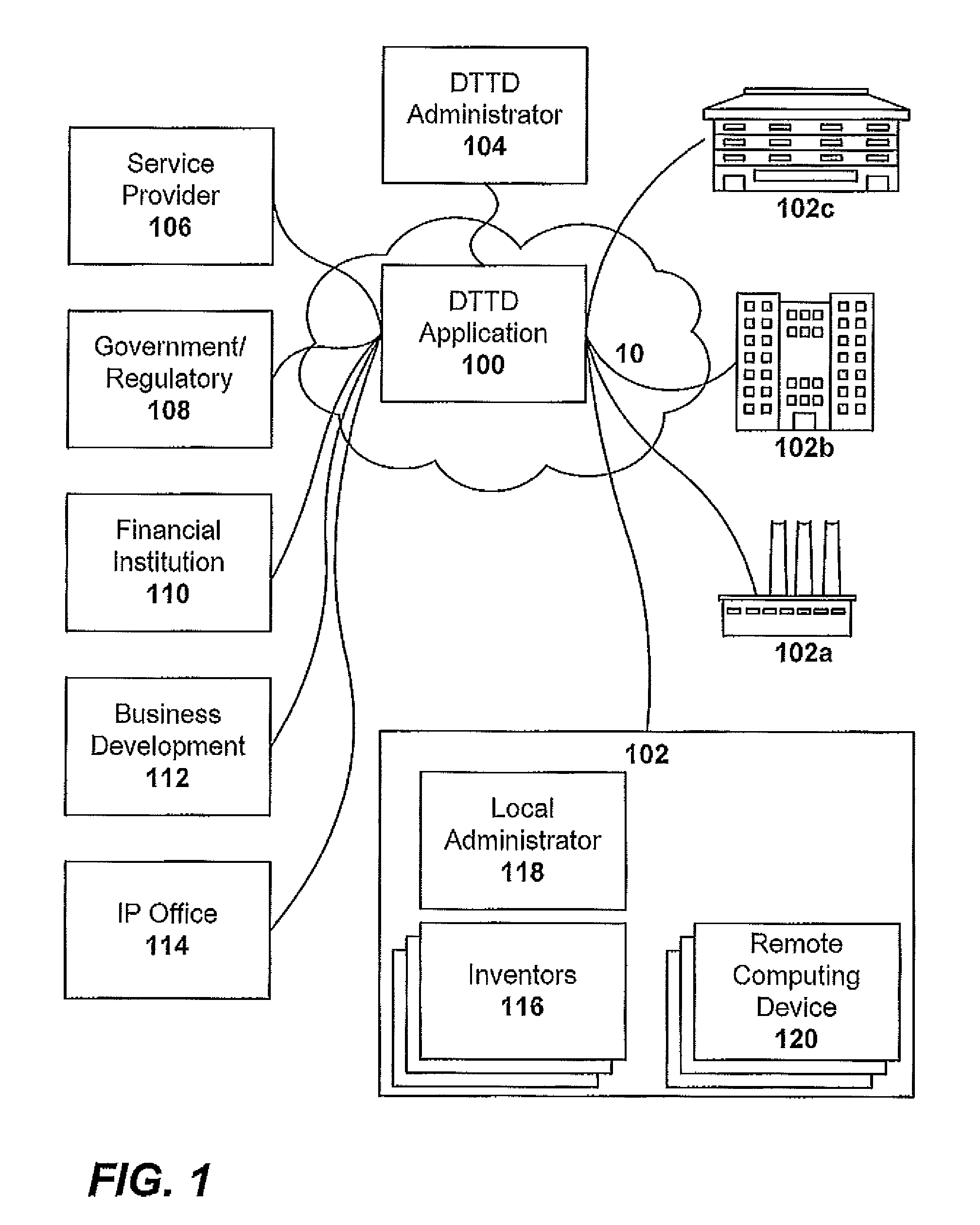
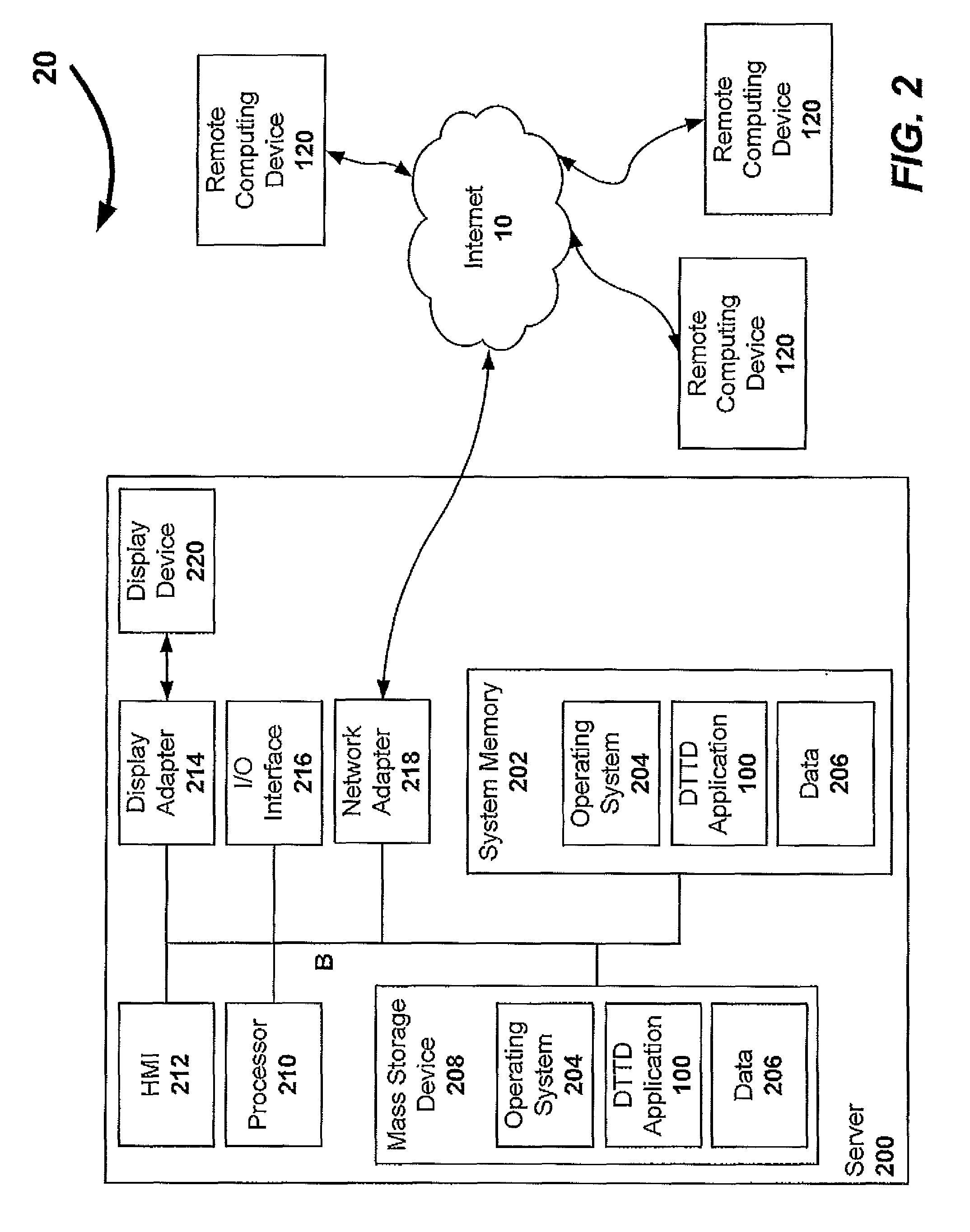
ActiveUS8117131B2Enhanced interactionNeed can be addressedOffice automationService provisionApplication software
An online, and therefore distributed, technology transfer department accessible by multiple inventive entities is provided. The systems and methods of the invention provide a comprehensive interface to a remote application that collects information related to inventions, ranks the inventions, solicits approval for pursuing intellectual property protection, funding, financing, commercializing or otherwise exploiting the invention, solicits bids from a stable of service providers, manages the award of contracts to provide services, facilitates collaboration between users internal and external to the inventive entities and between different entities, implements security protocols, and reports government funded inventions to the appropriate regulatory agencies, and manages intellectual property portfolios. Each inventive entity may specify the level of control to be retained to utilize the distributed technology office application as a supplement for or as a substitute for full time technology transfer personnel.
Owner:FLORIDA A&M UNIVERSITY
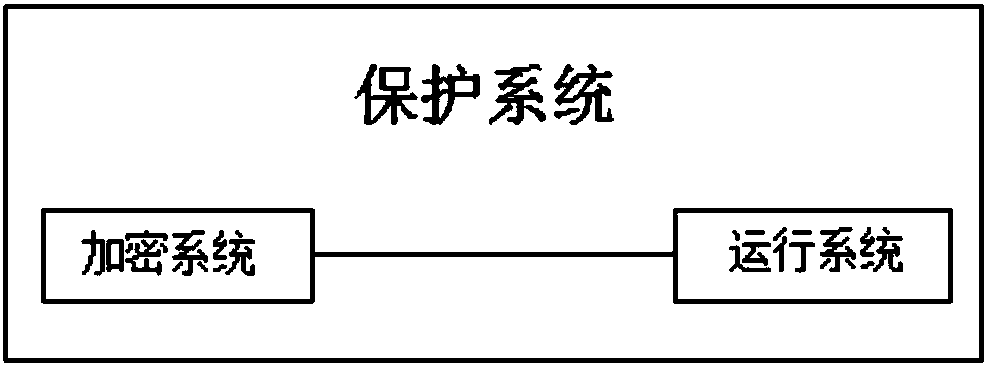
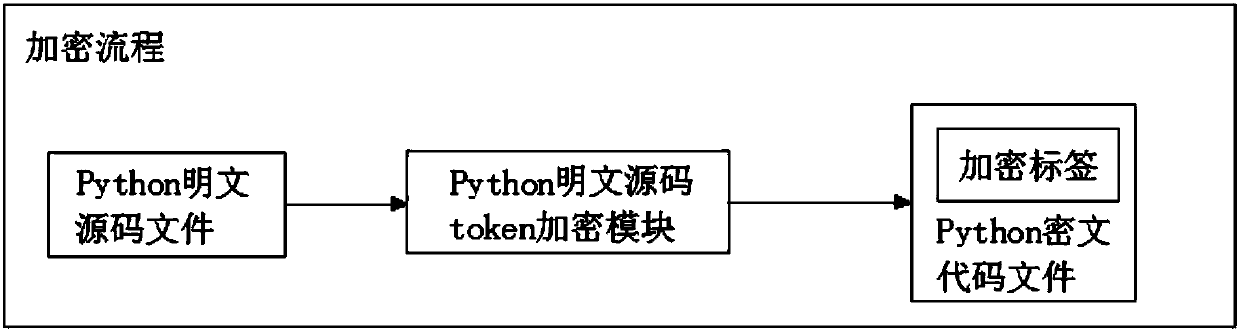
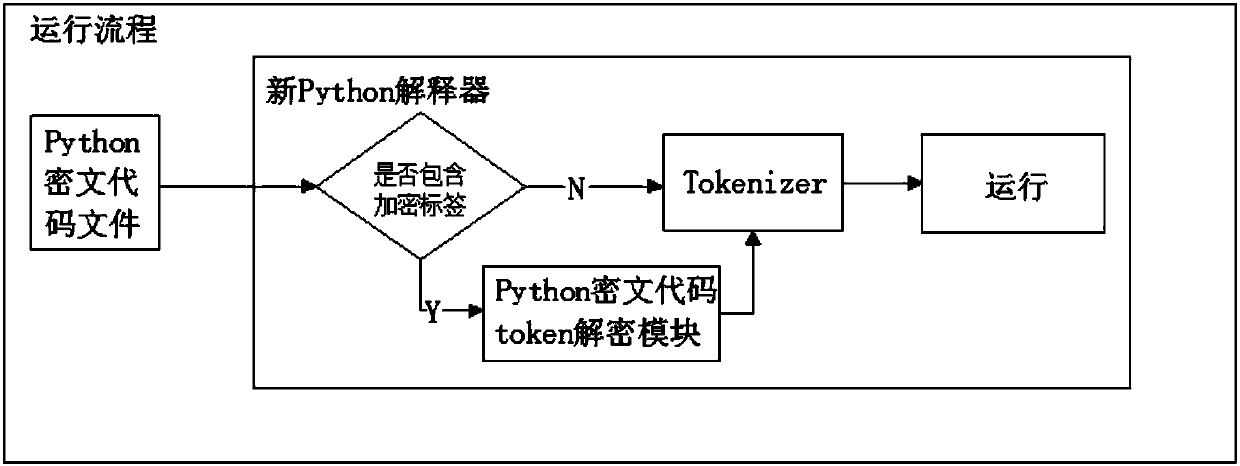
System for protecting intellectual properties through encrypting Python plaintext source code tokens
ActiveCN107808101AEffective protectionKey distribution for secure communicationData processing applicationsPlaintextSource code file
The invention discloses a system for protecting intellectual properties through encrypting Python plaintext source code tokens. The system comprises an encryption system and an operation system, wherein the encryption system comprises a Python plaintext source code token encryption module which is used for encrypting Python plaintext source code files through a self-defined symmetric private key encryption algorithm; the operation system comprises a new Python interpreter which is used for decrypting the Python cyphertext source code files; a Python cyphertext code token decryption operation module is added in the new Python interpreter; and the new Python interpreter is obtained from a Python protogenic interpreter through the Python cyphertext code token decryption operation module. Thesystem is capable of effectively preventing Python files from being changed, read and analyzed, so as to achieve the aim of protecting intellectual properties.
Owner:上海金途信息科技有限公司
Simultaneous Intellectual Property Search and Valuation System and Methodology (SIPS-VSM)
InactiveUS20140143269A1Digital data information retrievalDigital data processing detailsLibrary scienceProblem solve
A system, method, and computer-based logic flow is presented for a web-enabled tool allowing simultaneous intelligent searching, knowledge management based problem solving, valuation, and modeling of intellectual property and scientific information. The system accesses databases containing intellectual property and scientific information. Additionally, the computer-based logic flow utilizes valuation techniques. The system receives user queries and can simultaneously and automatically access an intellectual property database, a scientific information database, a knowledge management based problem solving database, and a valuation based algorithm database to categorize, analyze, and disseminate pertinent information resulting in modeling and displaying the results. The invention also allows for the simultaneous display of intellectual property and valuation information in one model as well as the non-intellectual property protected scientific information. The user can easily, quickly, and accurately obtain information vital to determining the content, value, and direction of current and future specific technology trends.
Owner:GRUNE GUERRY L +2
Apparatus and method of protecting user's privacy information and intellectual property against denial of information attack
InactiveUS20070136139A1Prevent leakagePrevent inflowDigital computer detailsPayment architectureNetwork Access ControlProtection system
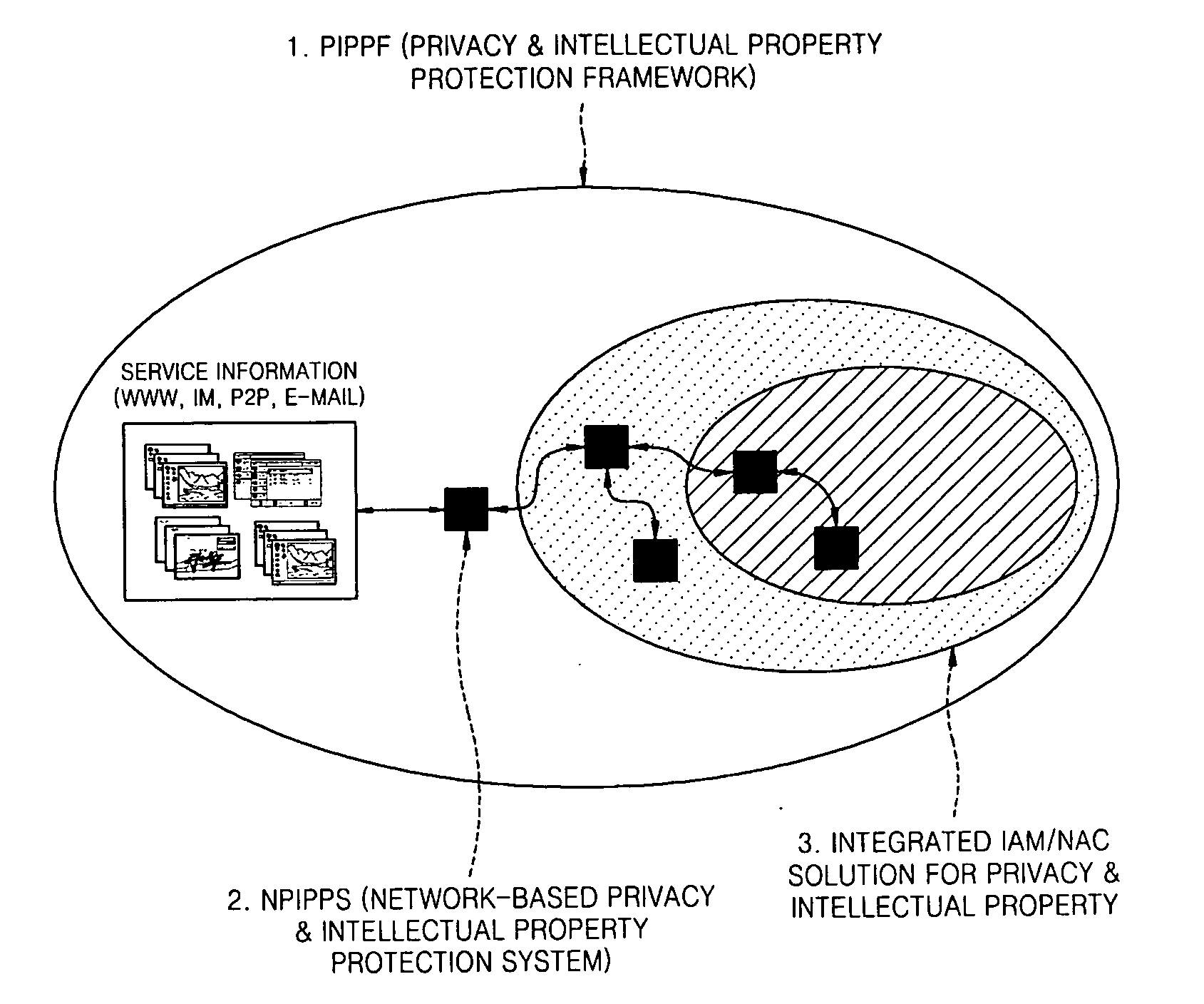
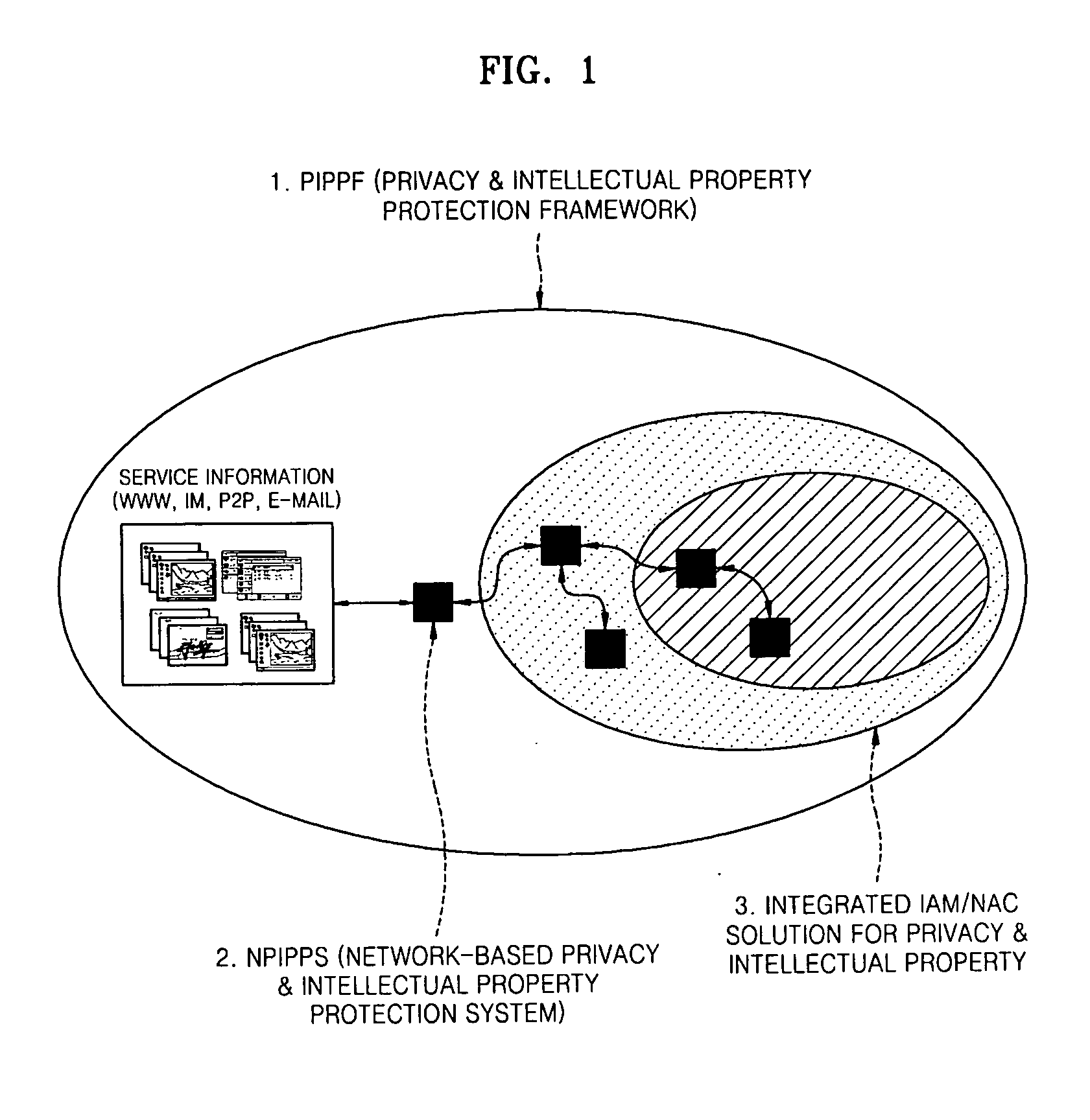
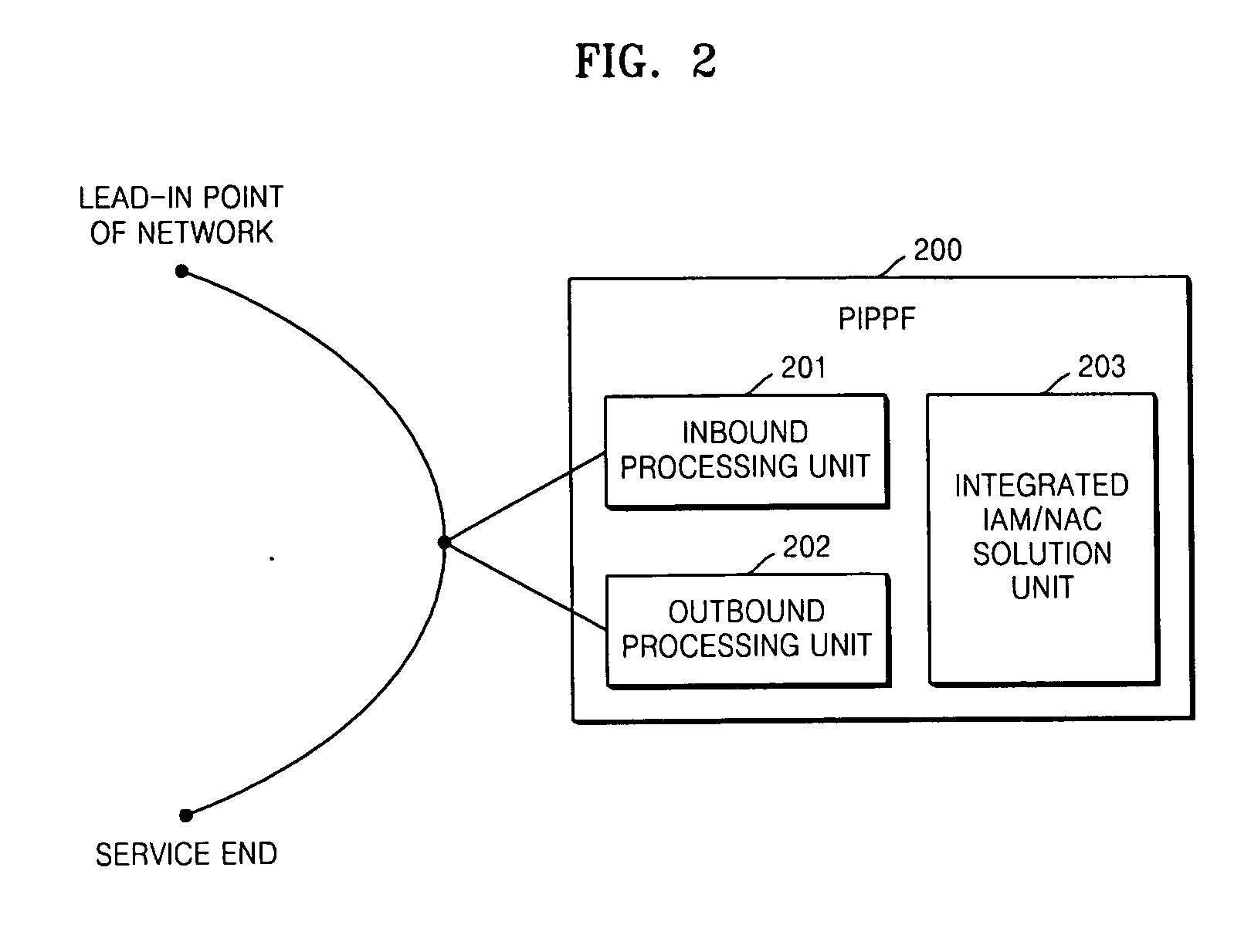
Provided are an apparatus and method of protecting a user's privacy information and corporate intellectual property against a denial-of-information (DoI) attack, and more particularly, a privacy & intellectual property protection framework (PIPPF) and a network-based privacy & intellectual property protection system (NPIPPS). The PIPPF includes the NPIPPS and an integrated identity access and management (IAM) / network access control (NAC) solution. The NPIPPS monitors inbound and outbound contents at the network level and prevents the leakage of important information. In addition, the integrated IAM / NAC solution prevents abnormal user activity within a network and unauthorized use of information.
Owner:ELECTRONICS & TELECOMM RES INST
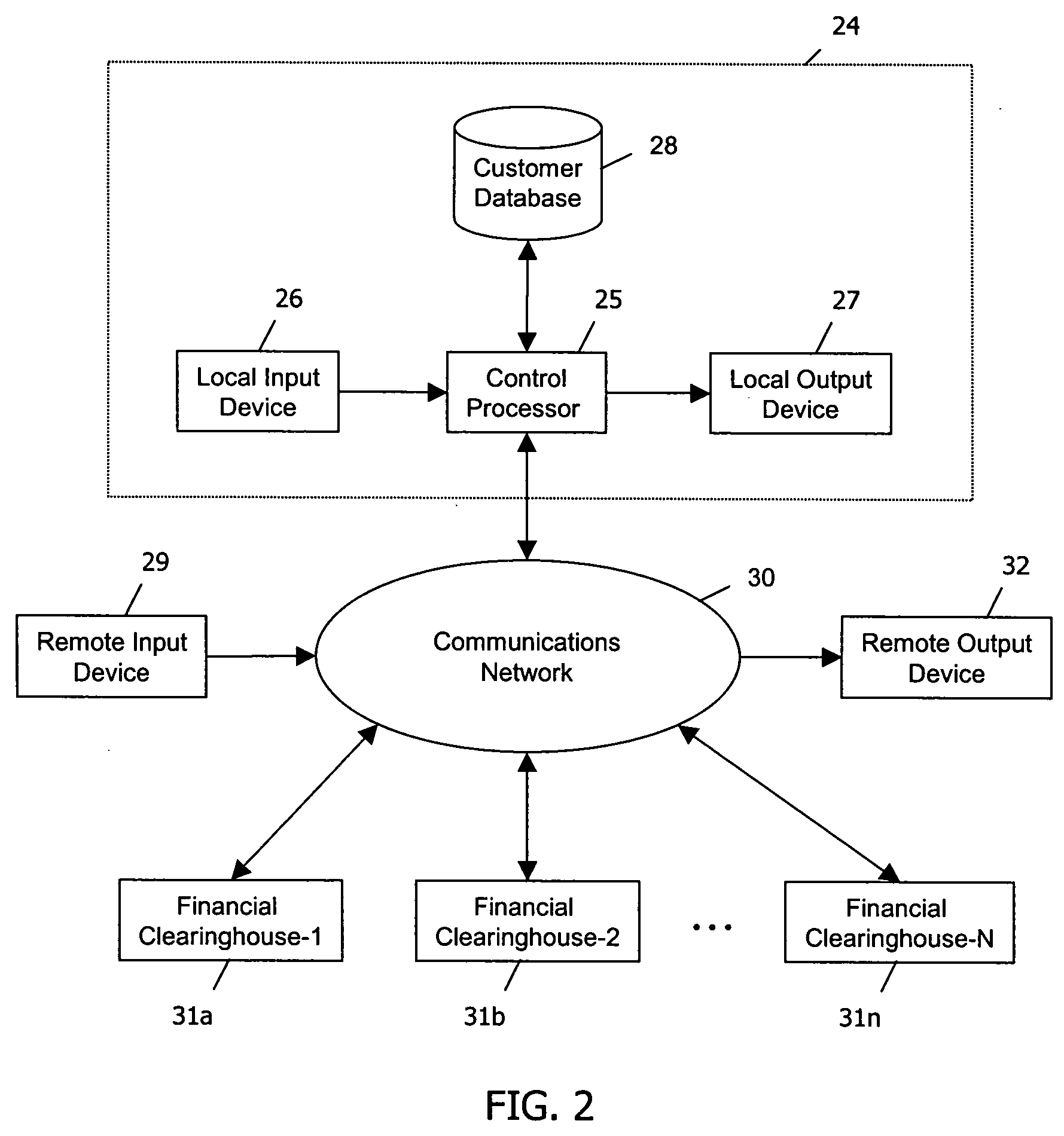
System and method for providing property-secured credit card products
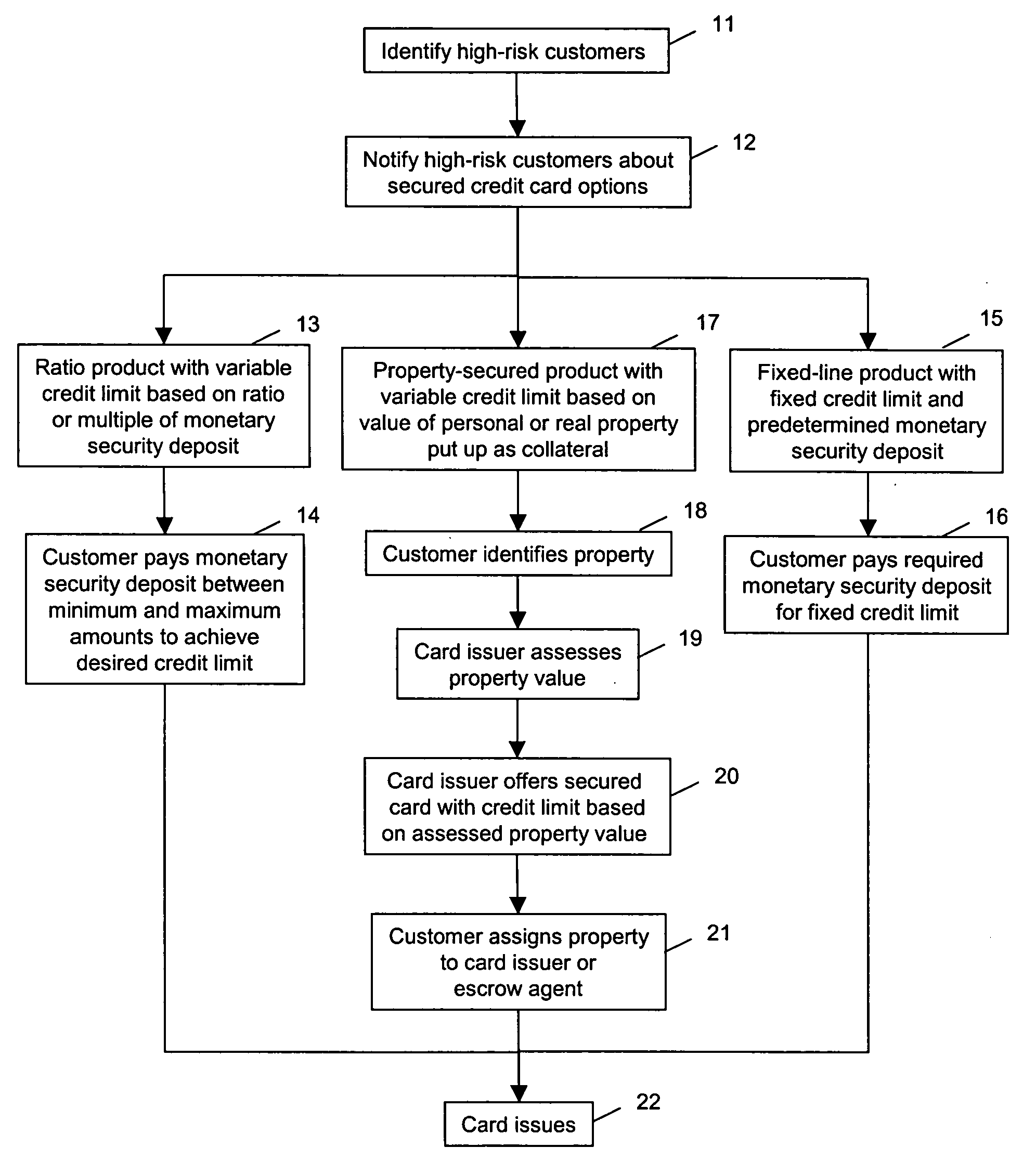
A system, method, and computer program product provides credit card products secured with personal property, real property, or intellectual property to minimize risk to credit card issuers while making secured credit card products available to customers who currently cannot obtain such a card. The customer identifies customer property to be utilized as collateral in exchange for the secured credit card product. A market value of the collateral property is assessed, and the card issuer determines a credit limit based on the assessed market value. The card issuer offers the secured credit card product with the determined credit limit, and receives in response, an assignment of ownership of the customer's collateral property. The card issuer provides the secured credit card product in response to receiving the assignment of ownership. The assignment and the property may be held by an escrow agent.
Owner:SMITH STEVEN W
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com