Method and system for detecting abnormal service behaviors
A business system and anomaly detection technology, applied in the field of information security, can solve the problems of underreporting of attack behavior, inability to formulate reasonable security configuration rules, and cumbersome security configuration rules, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0042] The implementation of the present invention will be described in detail below in conjunction with the accompanying drawings and examples, so as to fully understand and implement the process of how to apply technical means to solve technical problems and achieve technical effects in the present invention.
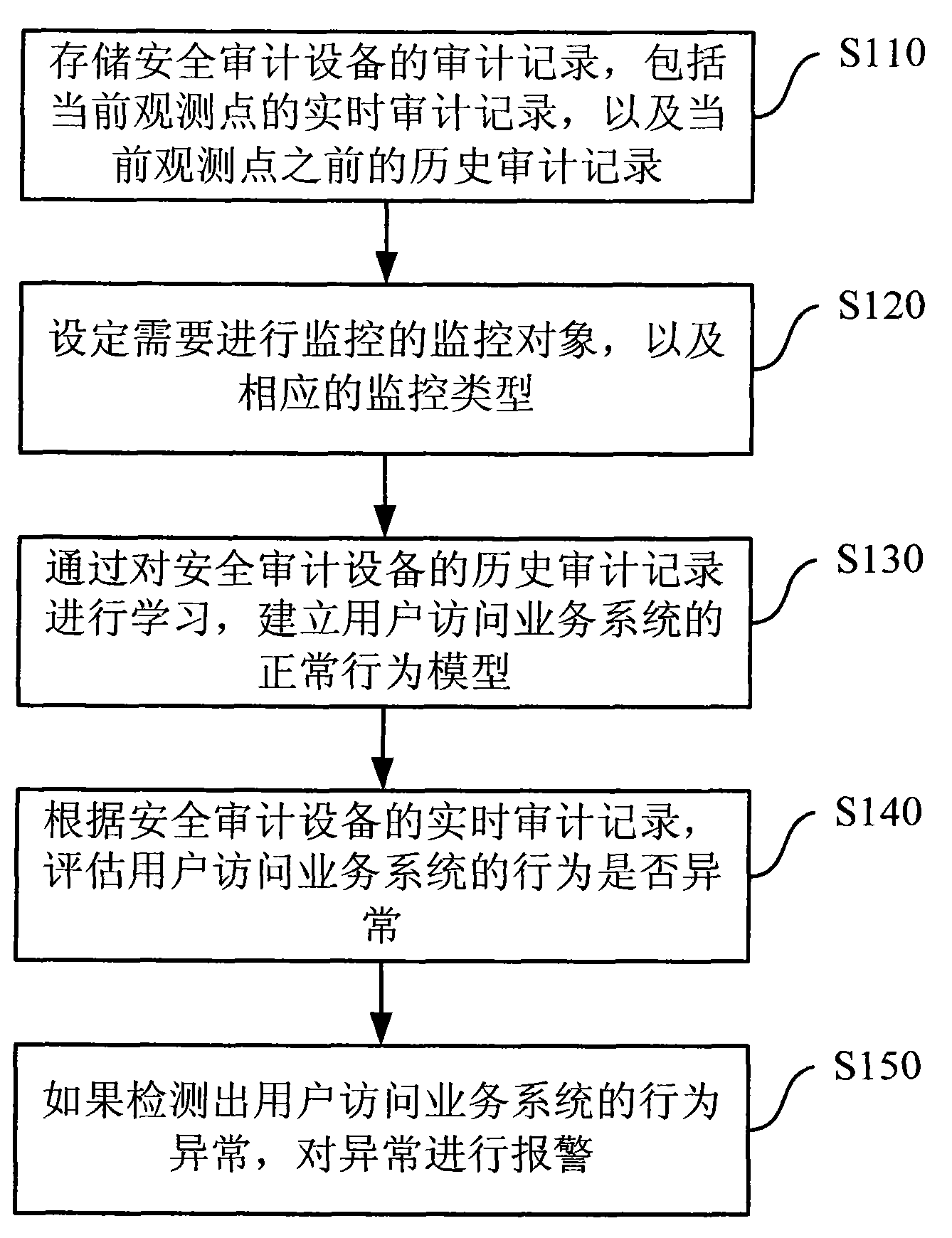
[0043] figure 1 It is a schematic flowchart of an embodiment of a method for detecting abnormal business behavior in the present invention. Such as figure 1 As shown, the method embodiment mainly includes the following steps:
[0044]Step S110, storing the audit records of the security audit equipment, including the real-time audit records of the current observation point, and the historical audit records before the current observation point;
[0045] Step S120, setting the monitoring object to be monitored and the corresponding monitoring type of the monitoring object;
[0046] The monitoring objects include database table names, and corresponding operation types ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com