Large-scale DDoS (Distributed Denial of Service) attack defense system and method based on two-level linkage mechanism
A large-scale, mechanism-based technology, applied in the field of network security, can solve problems such as difficult customer DDoS attack protection, high-level cleaning system deployment, and difficult deployment of protection strategies, so as to reduce deployment costs, improve cleaning accuracy, and improve large-scale DDoS attacks The effect of defense
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0027] The present invention will be described more fully hereinafter with reference to the accompanying drawings, in which exemplary embodiments of the invention are illustrated.
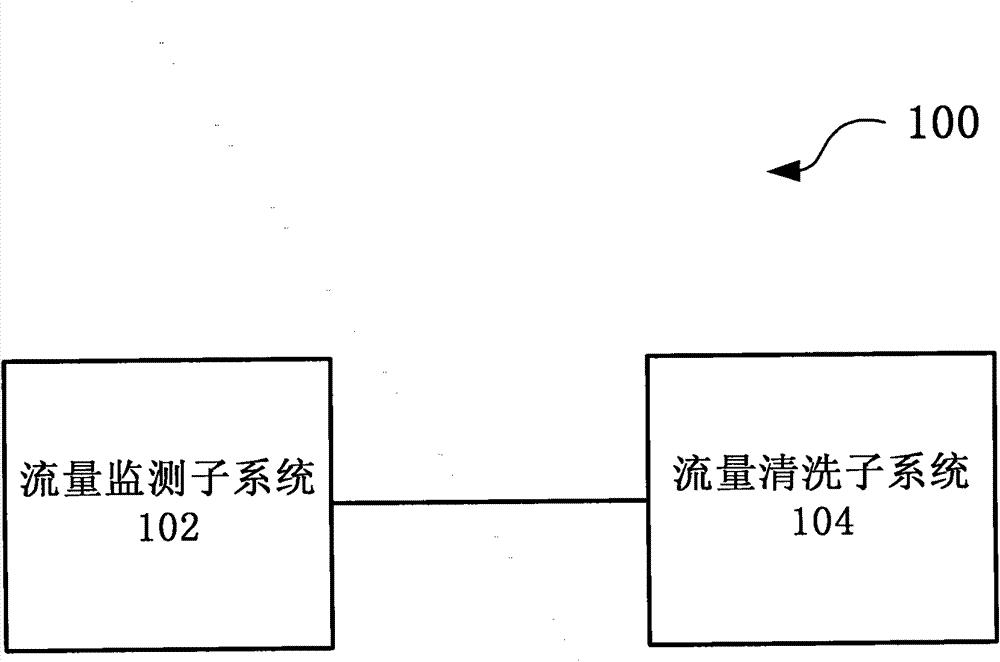
[0028] figure 1 A schematic structural diagram of a large-scale DDoS attack defense system based on a two-level linkage mechanism provided by an embodiment of the present invention is shown.
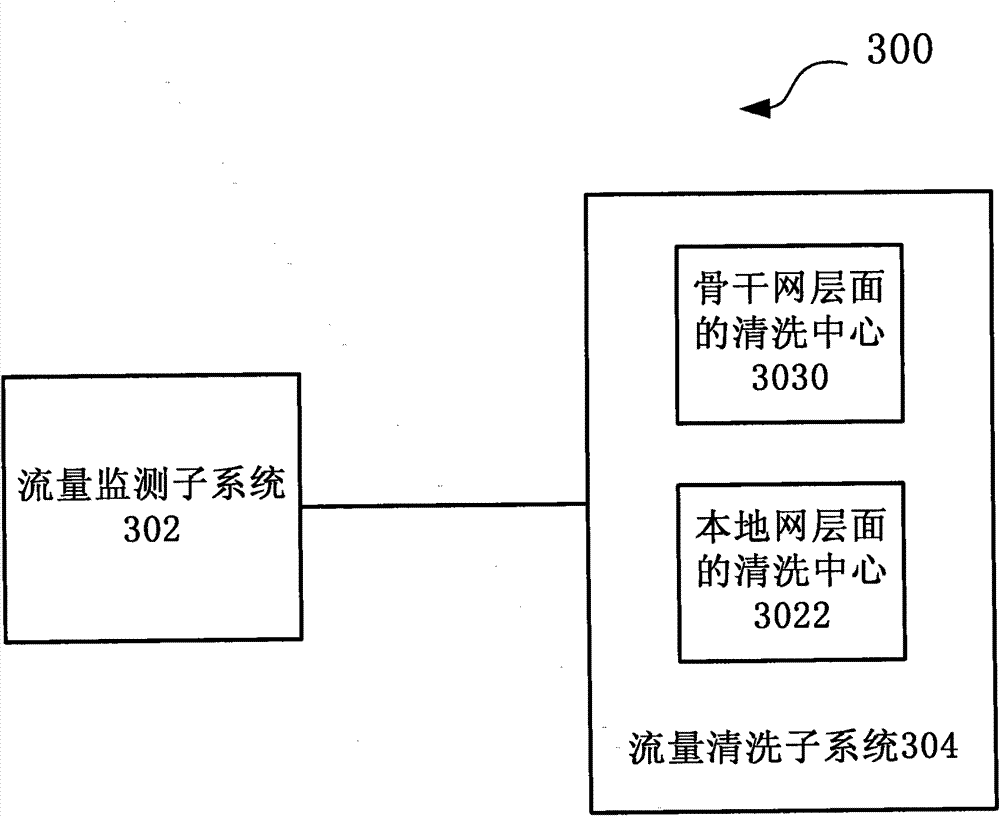
[0029] Such as figure 1 As shown, the large-scale DDoS attack defense system 100 based on the two-level linkage mechanism includes a traffic monitoring subsystem 102 and a traffic cleaning subsystem 104, wherein
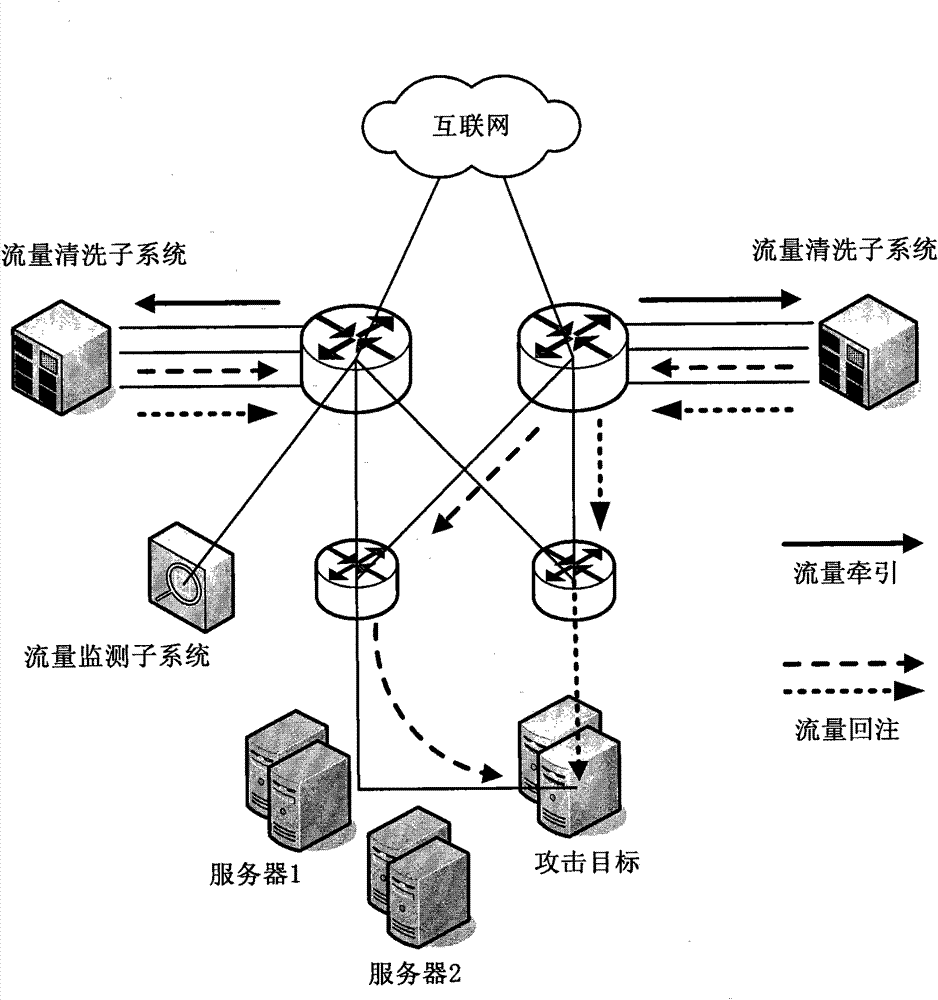
[0030] The traffic monitoring subsystem 102 is used to monitor the traffic of the entire network in real time, and after searching and confirming the DDoS attack behavior, send an alarm message triggering the cleaning operation to the traffic cleaning subsystem, and draw the abnormal traffic of the DDoS attack behavior to the traffic cleaning subsystem. For example, the traffic monitoring subsyst...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com