Authentication random number detection method and SIM (Subscriber Identity Module) card
A detection method and random number technology, applied in authentication random number detection, SIM card field, can solve problems such as production process and process leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
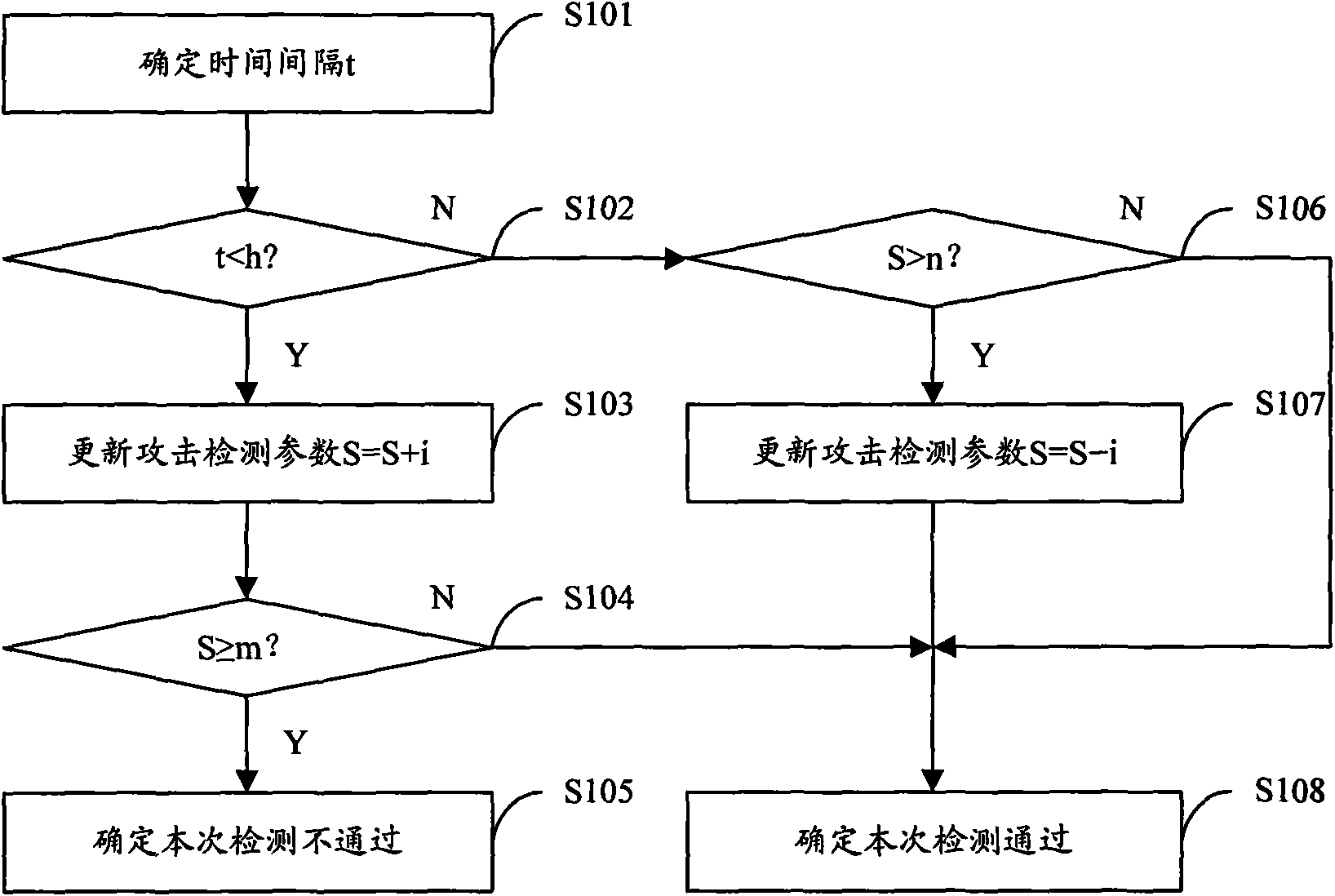
[0034] Embodiment 1 of the present invention provides an authentication random number detection method, such as figure 1 shown, including:
[0035] Step S101, the SIM card determines the time interval t between the received authentication random number sent by the network side this time and the last received authentication random number sent by the network side.
[0036] Step S102, judging whether the time interval t determined in step S101 is less than the set time threshold h, if yes, proceed to step S103, otherwise, proceed to step S106.
[0037] This step may also be to judge whether the time interval t is less than or equal to the set time threshold h, if yes, go to step S103, otherwise, go to step S106.
[0038] Step S103 , adding the set change value i to the attack detection parameter S to obtain an updated attack detection parameter S, that is, S=S+i.
[0039]Step S104 , judging whether the updated attack detection parameter S obtained after executing step S103 is g...
Embodiment 2
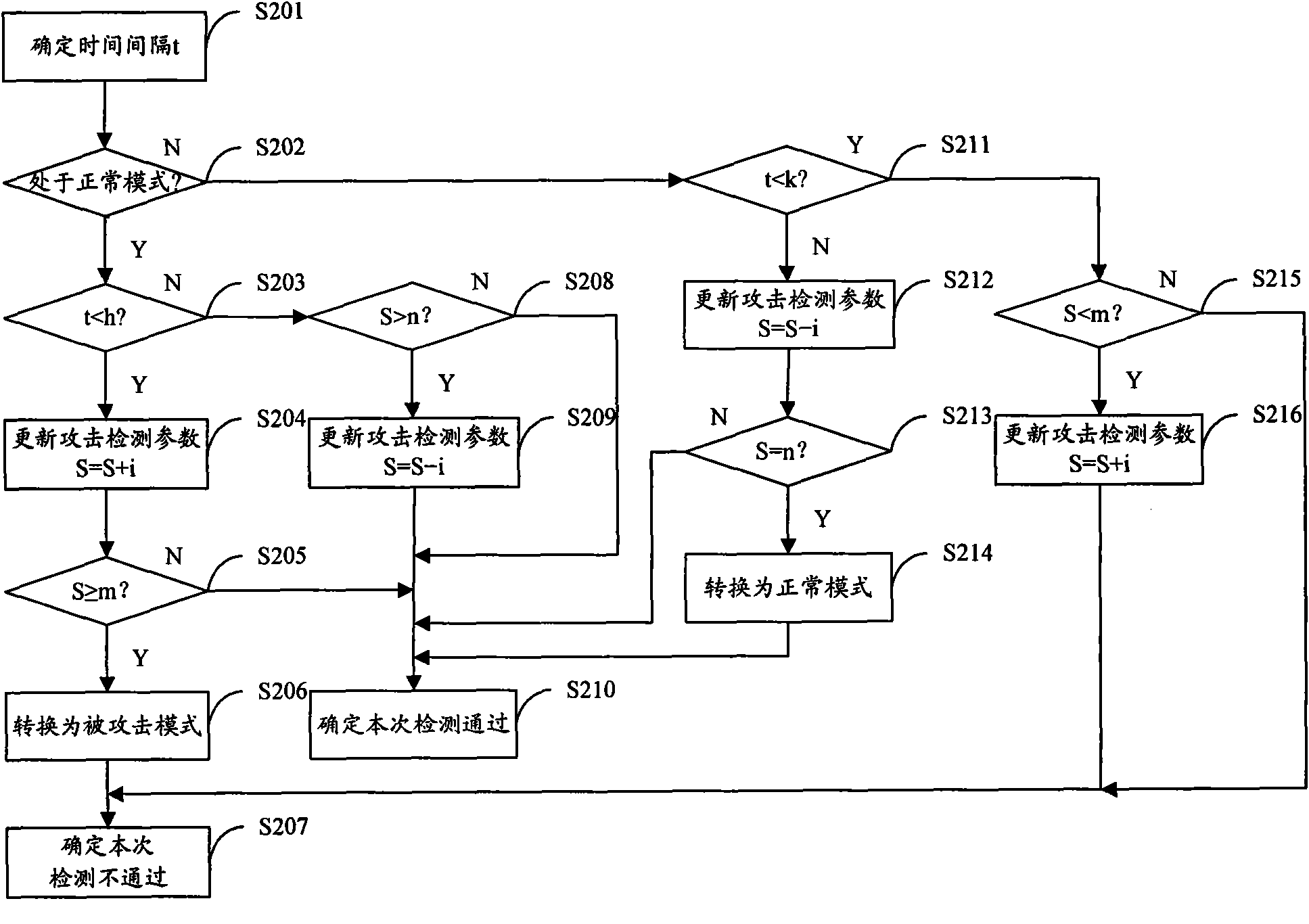
[0063] Embodiment 2 of the present invention provides an authentication random number detection method, such as figure 2 shown, including:
[0064] Step S201, the SIM card determines the time interval t between the received authentication random number sent by the network side this time and the last received authentication random number sent by the network side.
[0065] Step S202, judging whether the current detection mode of the SIM card is the normal mode or the attacked mode, if it is the normal mode, go to step S203, and if it is the attacked mode, go to step S211.
[0066] Step S203, judging whether the time interval t determined in step S201 is less than the first set time threshold h, if yes, proceed to step S204, otherwise, proceed to step S208.
[0067] This step may also be to judge whether the time interval t is less than or equal to the first set time threshold h, if yes, go to step S204, otherwise, go to step S208.
[0068] Step S204 , adding the set change va...
Embodiment 3
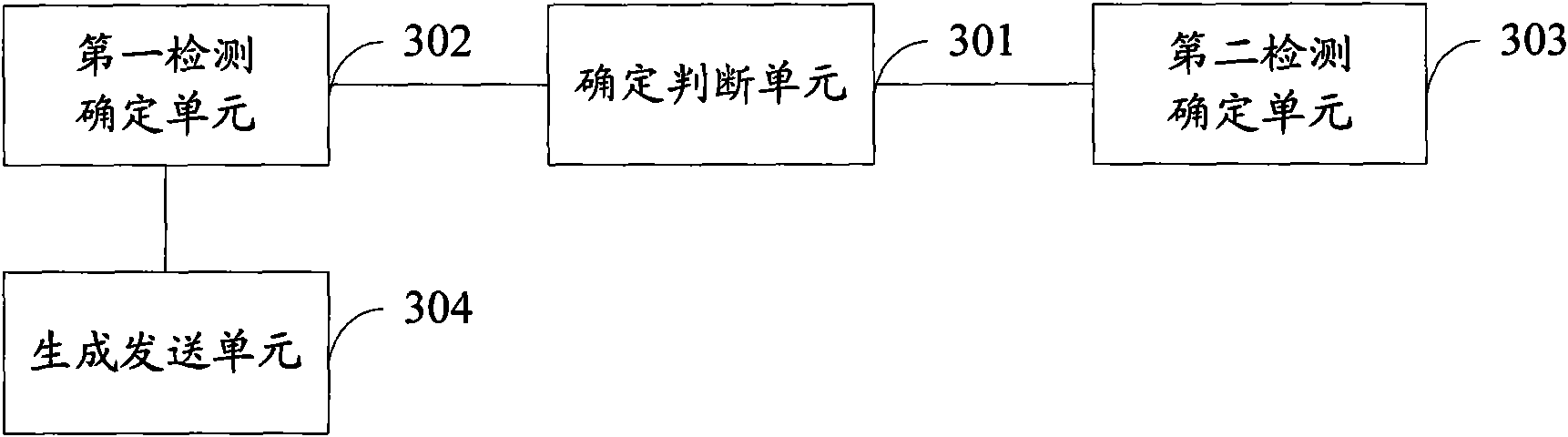
[0091] Based on the same inventive concept, according to the authentication random number detection method provided by the first embodiment of the present invention, the third embodiment of the present invention also provides a SIM card, the schematic diagram of which is as follows image 3 As shown, it includes: a determination judgment unit 301, a first detection determination unit 302 and a second detection determination unit 303;
[0092] The determination and judgment unit 301 is configured to determine the time interval between receiving the authentication random number sent by the network side this time and last time; and judge whether the time interval is less than the set time threshold, and if so, notify the above-mentioned first detection and determination Unit 302, otherwise, notify the above-mentioned second detection determination unit 303;
[0093] The above-mentioned first detection determination unit 302 is configured to add the attack detection parameter to t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com