Novel unwanted code detecting method based on characteristics of function call relationship graph
A function call relationship, malicious code detection technology, applied in electrical digital data processing, instrument, platform integrity maintenance, etc., can solve the problem that users cannot deal with security threats in time, reduce detection effect, and local characteristics are not fixed.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment
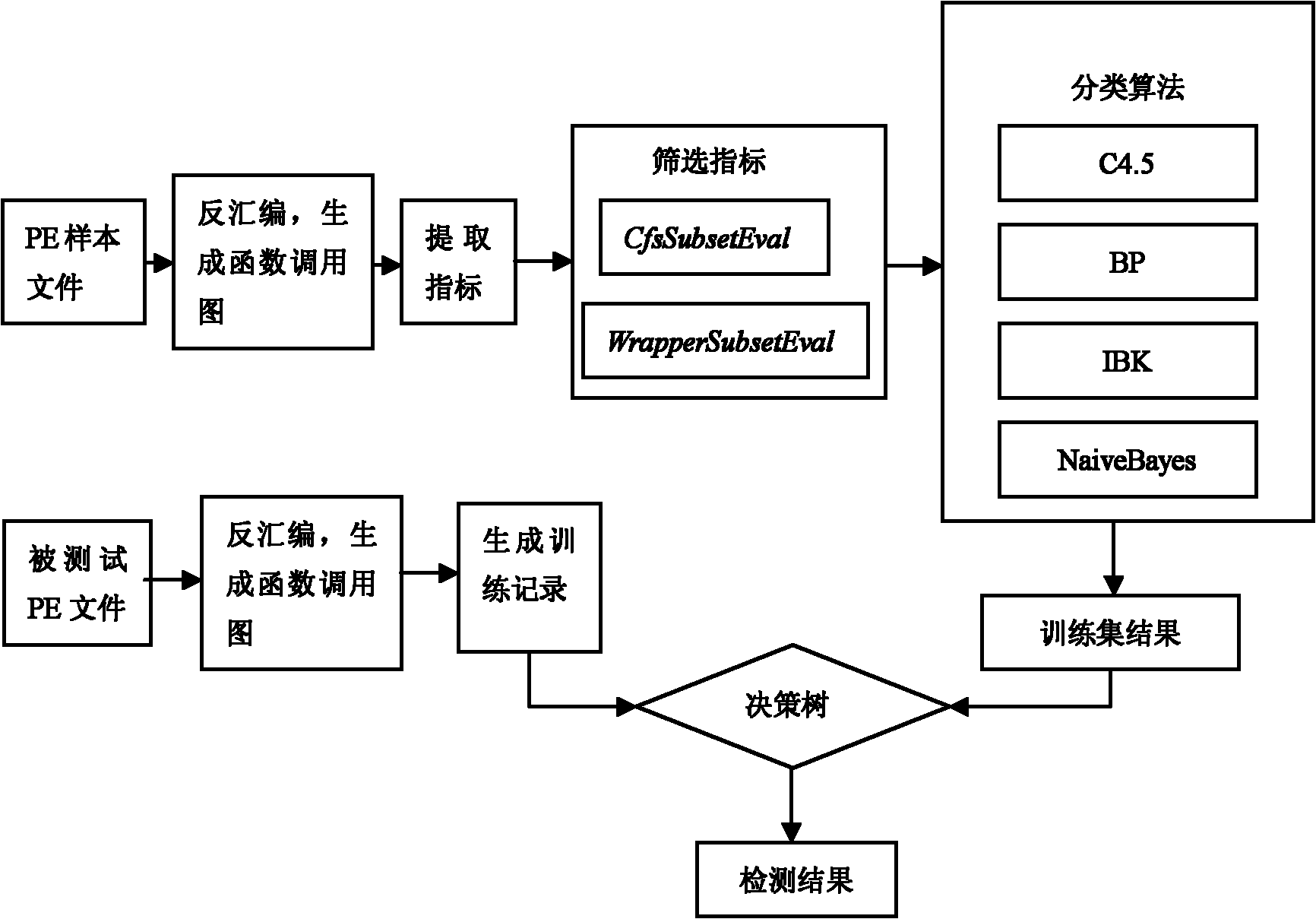
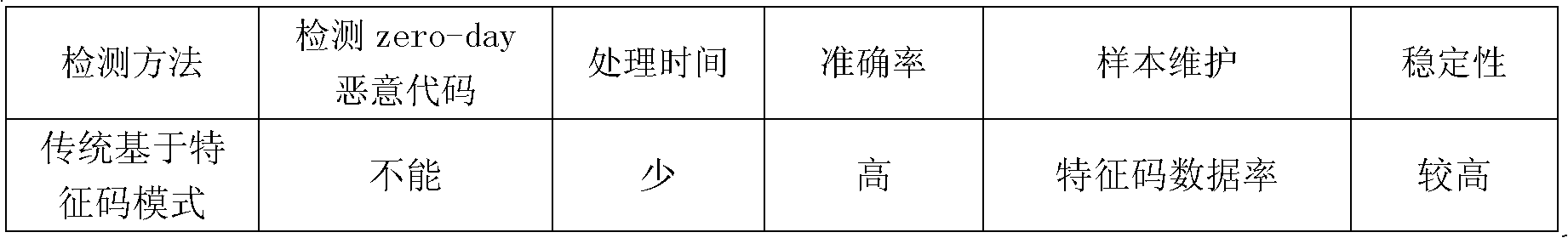
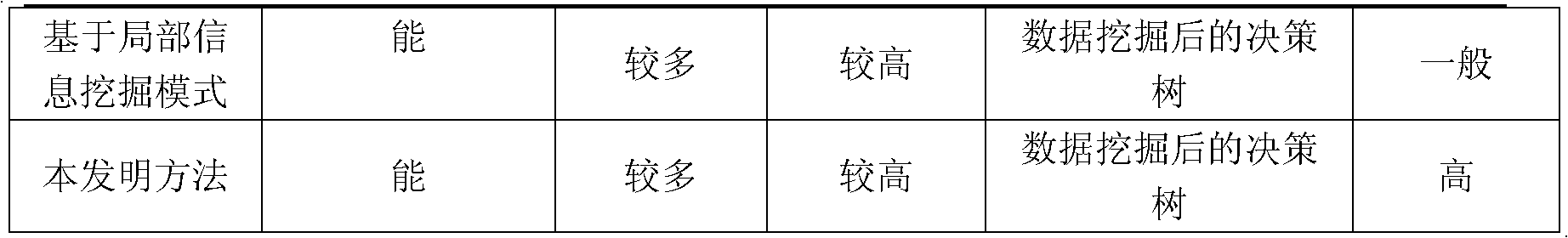
[0154] Brief information on the experimental datasets employed in the method of the present invention is described in Table 2. The normal files of the experimental data set are the system files and applications in Windows XP sp3 collected in the laboratory; the malicious codes are some virus files downloaded from the Malfease datasets website. The process of sample file processing includes disassembly, generating a function call graph, extracting graph feature indicators from it, and saving these data in arff type files. In the verification process of the method of the present invention, 10 fold cross-validation is adopted, and different classification algorithms are used in the testing process.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com