Network security incident association analysis system
A network security and event correlation technology, applied in the field of network security event correlation analysis system, can solve problems such as inability to produce synergistic effects, and achieve long-term management effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] The present invention is described in detail below in conjunction with accompanying drawing:
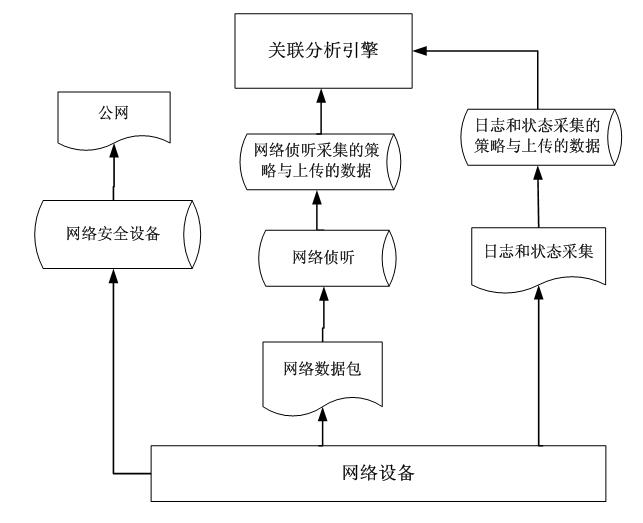
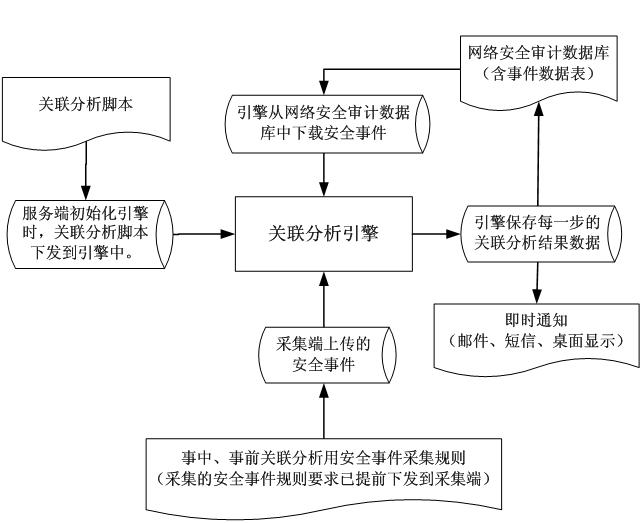
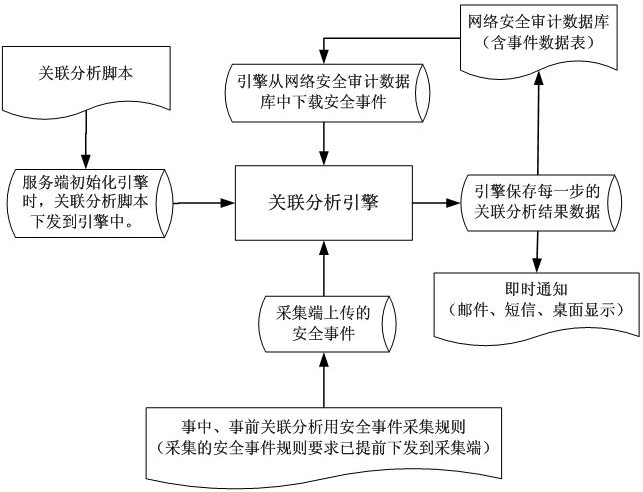
[0029] The network security event correlation analysis system of the present invention includes four layers: a network security event collection layer, a communication network layer, a correlation analysis layer and a management display layer.
[0030] The network security event collection layer is the most basic part of the system, such as figure 1 It is a principle diagram of collecting network security events of the present invention. It is installed next to the core switching equipment of the network system on site at each key monitoring point of the computer network. It includes status collection equipment, log collection equipment, and network data packet collection equipment. Install status collection equipment, log collection equipment, and network data packet collection equipment on site. After relevant configuration, the data of network security events can be obtain...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com