Concealed channel identification method
A covert channel and identification technology, applied in the direction of security communication devices, digital transmission systems, electrical components, etc., can solve problems such as state explosion, achieve low false alarm rate and false negative rate, reduce system analysis complexity, and reduce complexity Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0040] Below in conjunction with accompanying drawing, the present invention will be further described through embodiment, but the scope of the present invention is not limited in any way.
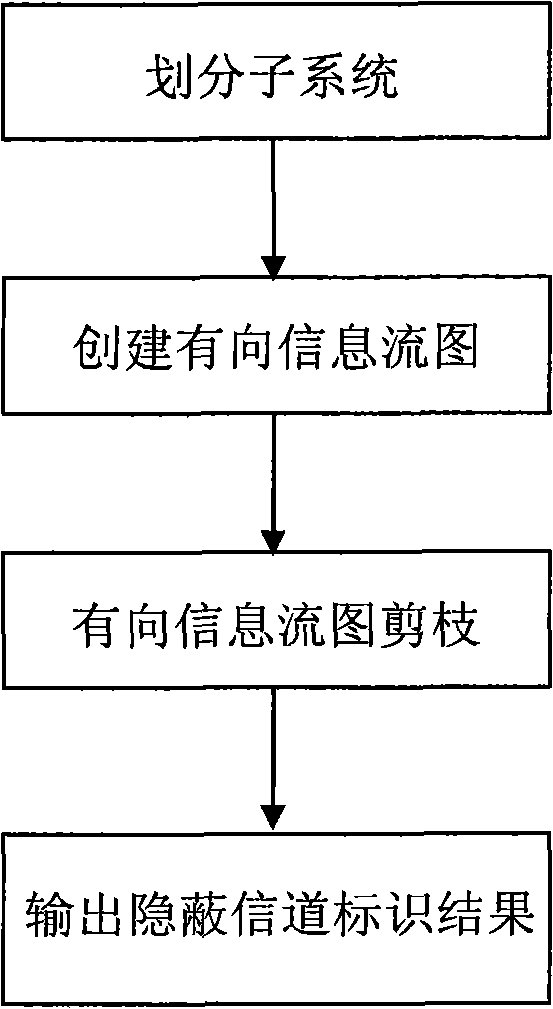
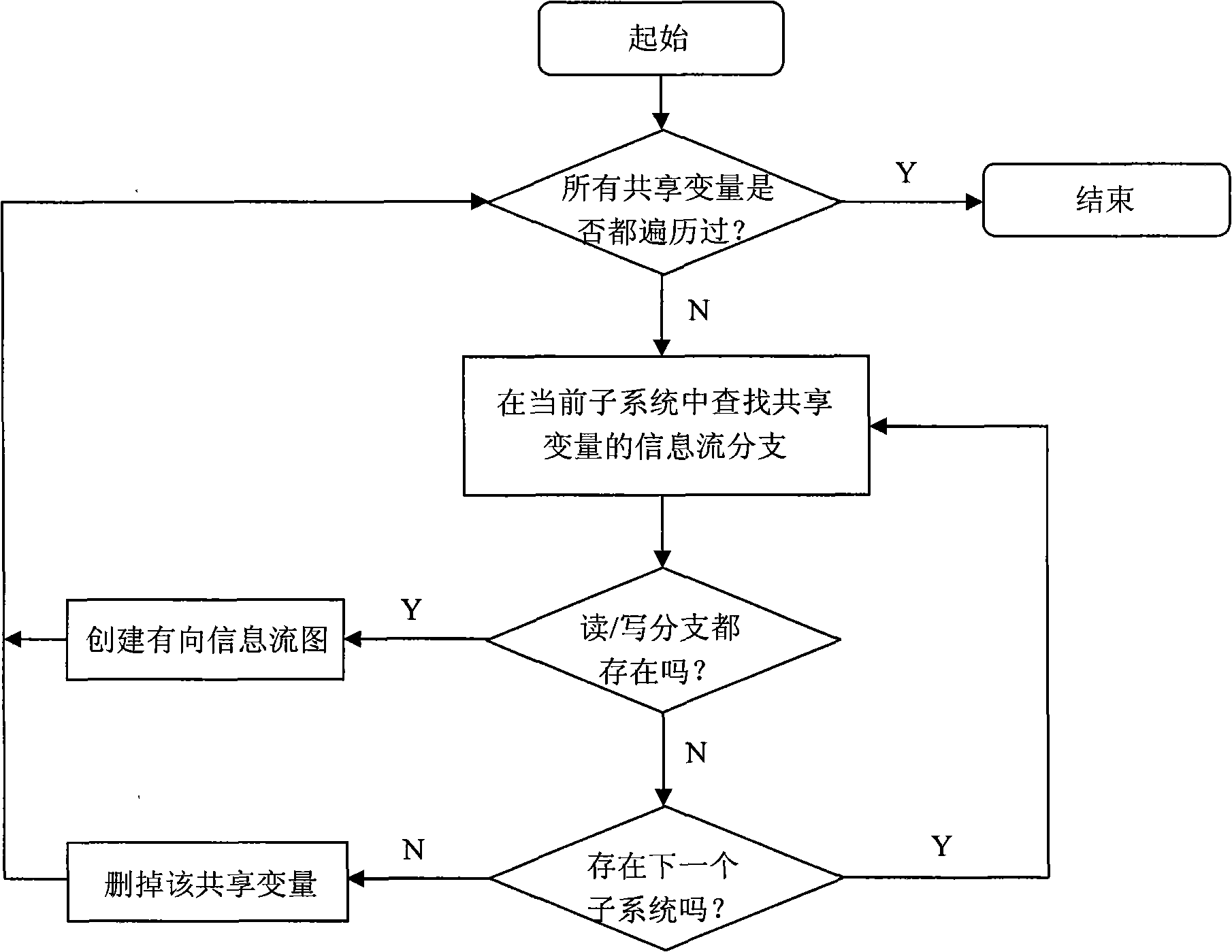
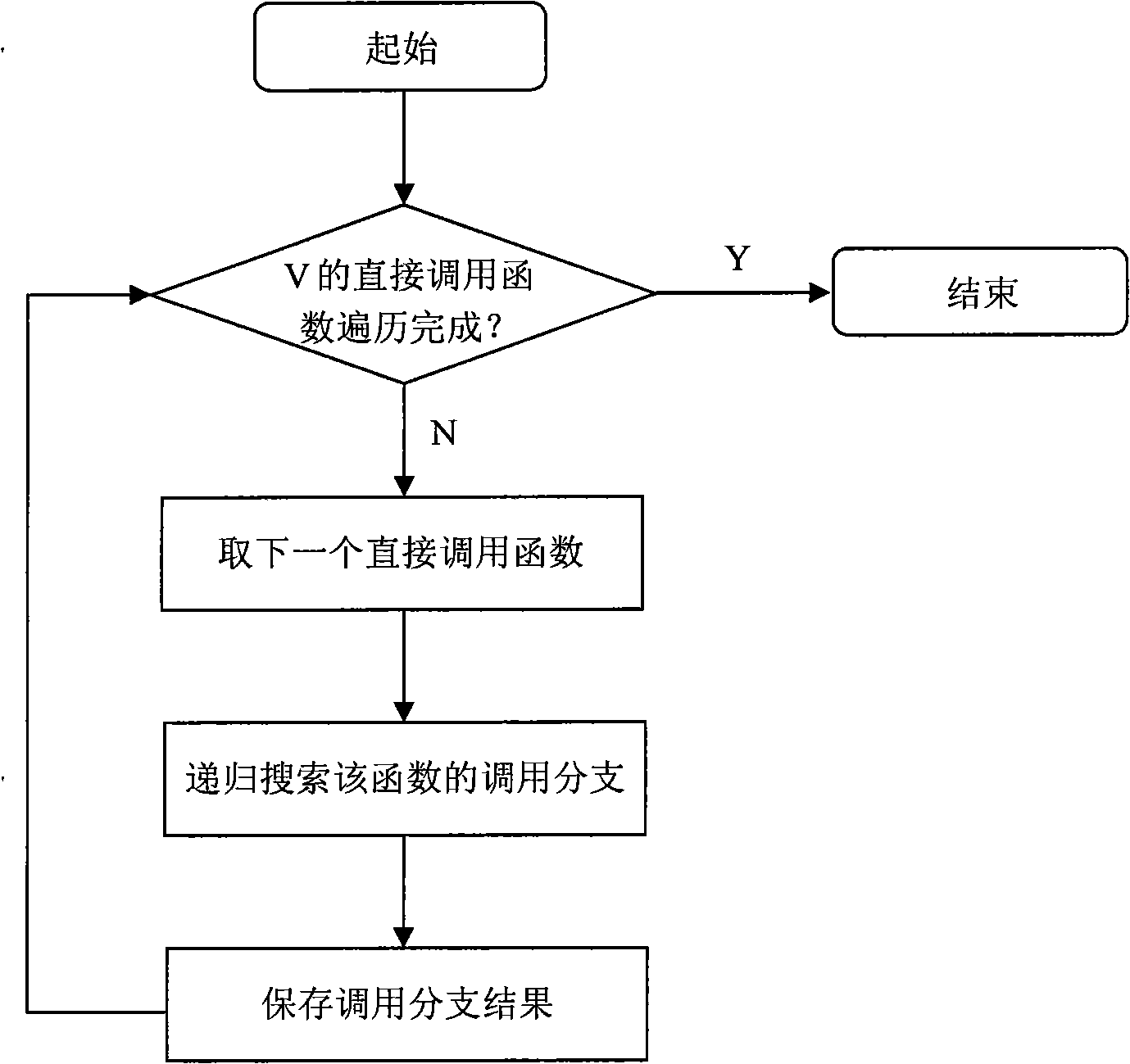
[0041] The overall flow of the code layer covert channel identification method based on the directed information flow graph of the present invention is as follows figure 1 As shown, taking the covert channel identification of the Linux system as an example, it specifically includes:
[0042] 1) First, divide the Linux system into relatively independent sub-modules (subsystems) according to the principle of low cohesion and high coupling. The sub-modules include {kernel, mm, ipc, fs, net, init, block, ...} , each submodule is analyzed separately as an independent part.
[0043] 2) Take the independent sub-module fs as the analysis object. Its shared variables include {i_hash_mask, last_type, s_free_inodes_count, s_free_blocks_count, nr_files, last_ino, inodes_stat.nr_inodes, inotify_mnt, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com