Method for analyzing safety defect of network protocol
A technology for network protocol security and defect analysis, applied in electrical components, transmission systems, etc., can solve problems such as the lack of formalization of idealized steps, the lack of formalization of the determination of initial assumptions, and the lack of semantic basis for BAN logic.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0026] In order to make the object, technical solution and advantages of the present invention clearer, the implementation manner of the present invention will be further described in detail below in conjunction with the accompanying drawings.
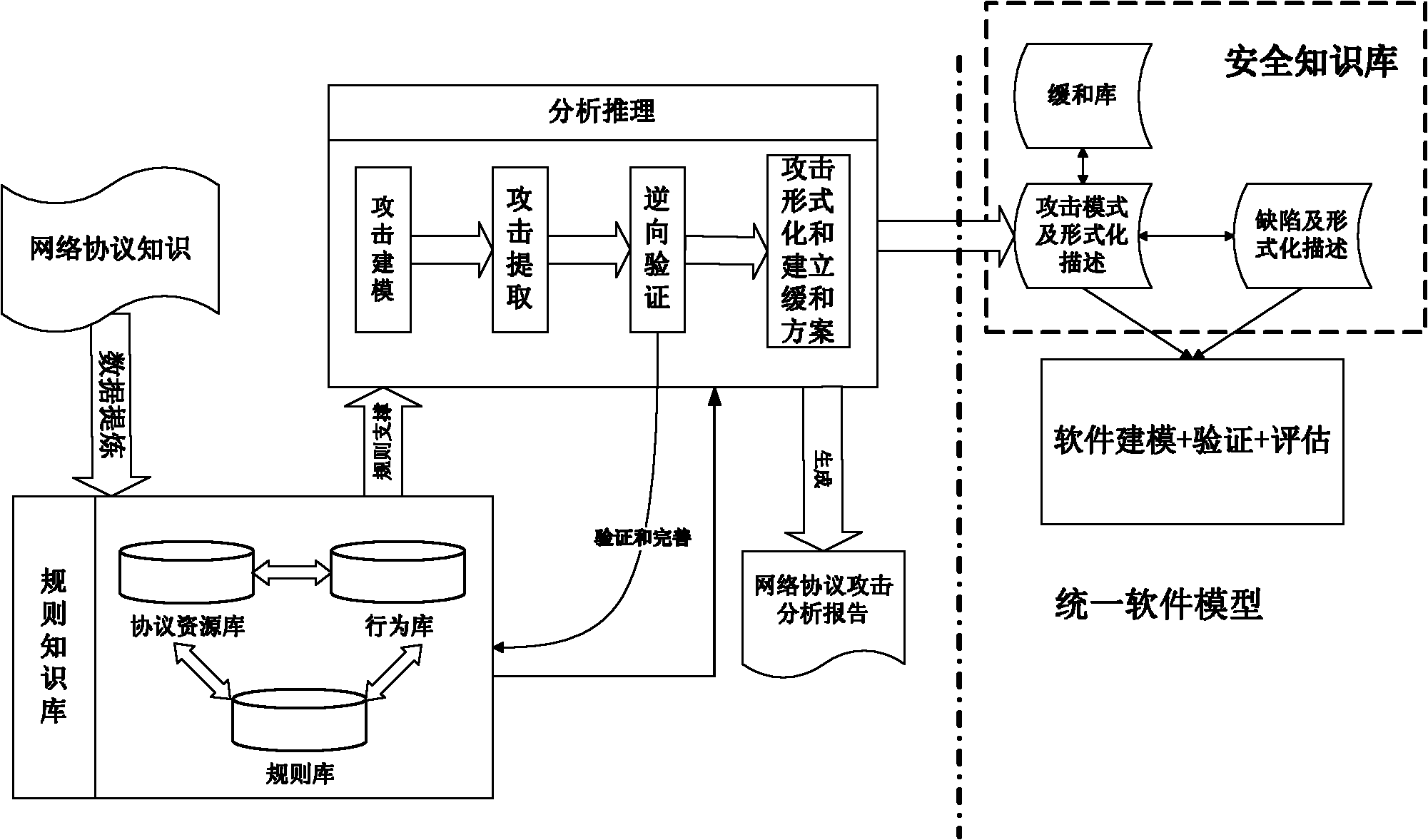
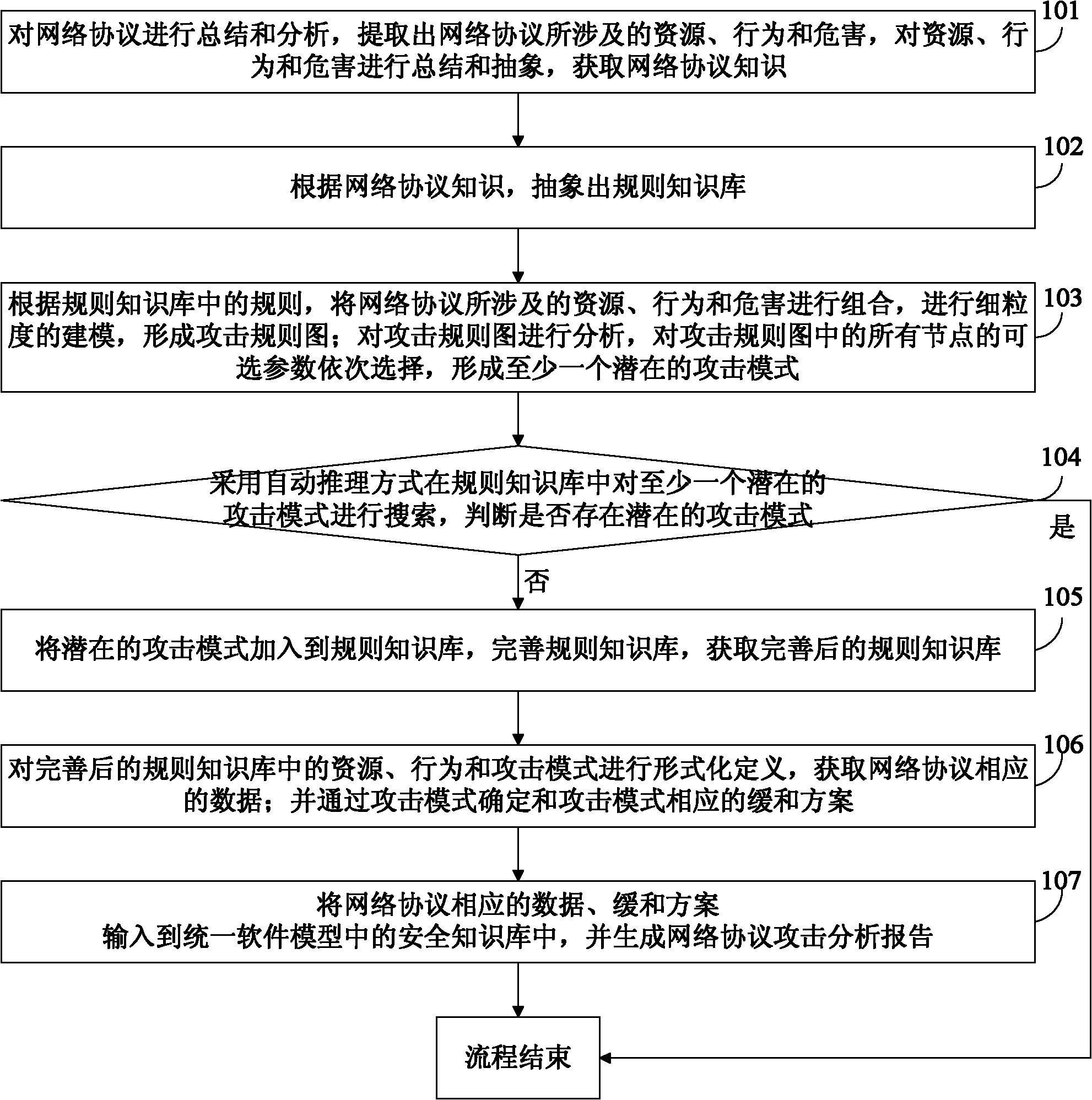
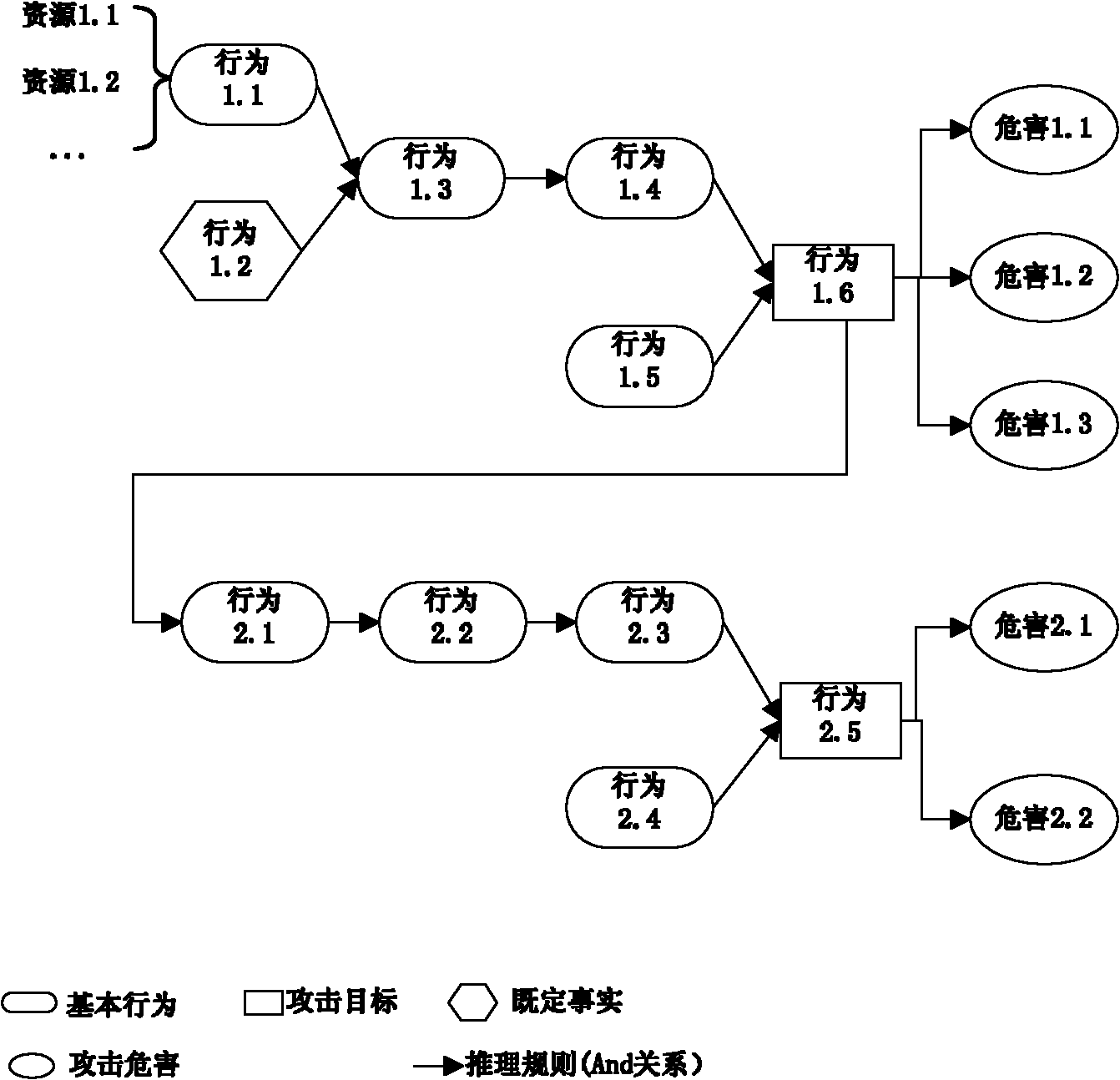
[0027] In order to overcome the deficiencies in the prior art and meet the needs of practical applications, the embodiment of the present invention provides a network protocol security defect analysis method, see figure 1 with figure 2 , see the description below:
[0028] 101: Summarize and analyze network protocols, extract resources, behaviors and hazards involved in network protocols, summarize and abstract resources, behaviors and hazards, and acquire knowledge of network protocols;
[0029] Summarize the involved resources, behaviors, and hazards from network protocols. Network protocols vary widely due to their different functions, and therefore network attacks are of various types. However, the ideas of many network attacks ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com