Method and device for realizing monitoring on SQL (structured query language) database
A database and configuration file technology, applied in the computer field, can solve problems such as low execution efficiency and unsuitability for monitoring, and achieve the effects of reducing impact, facilitating maintenance of business programs, and improving execution efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
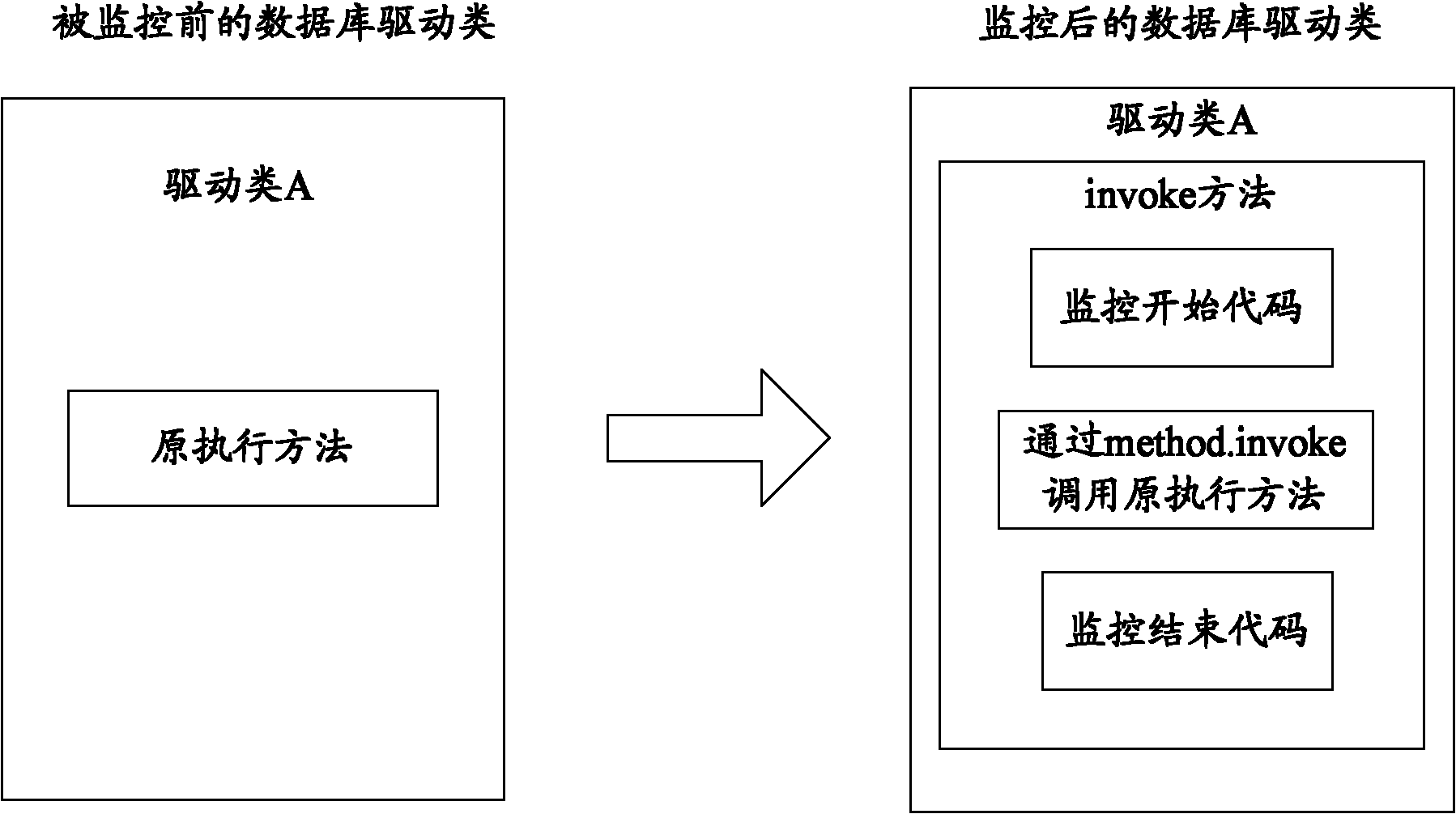
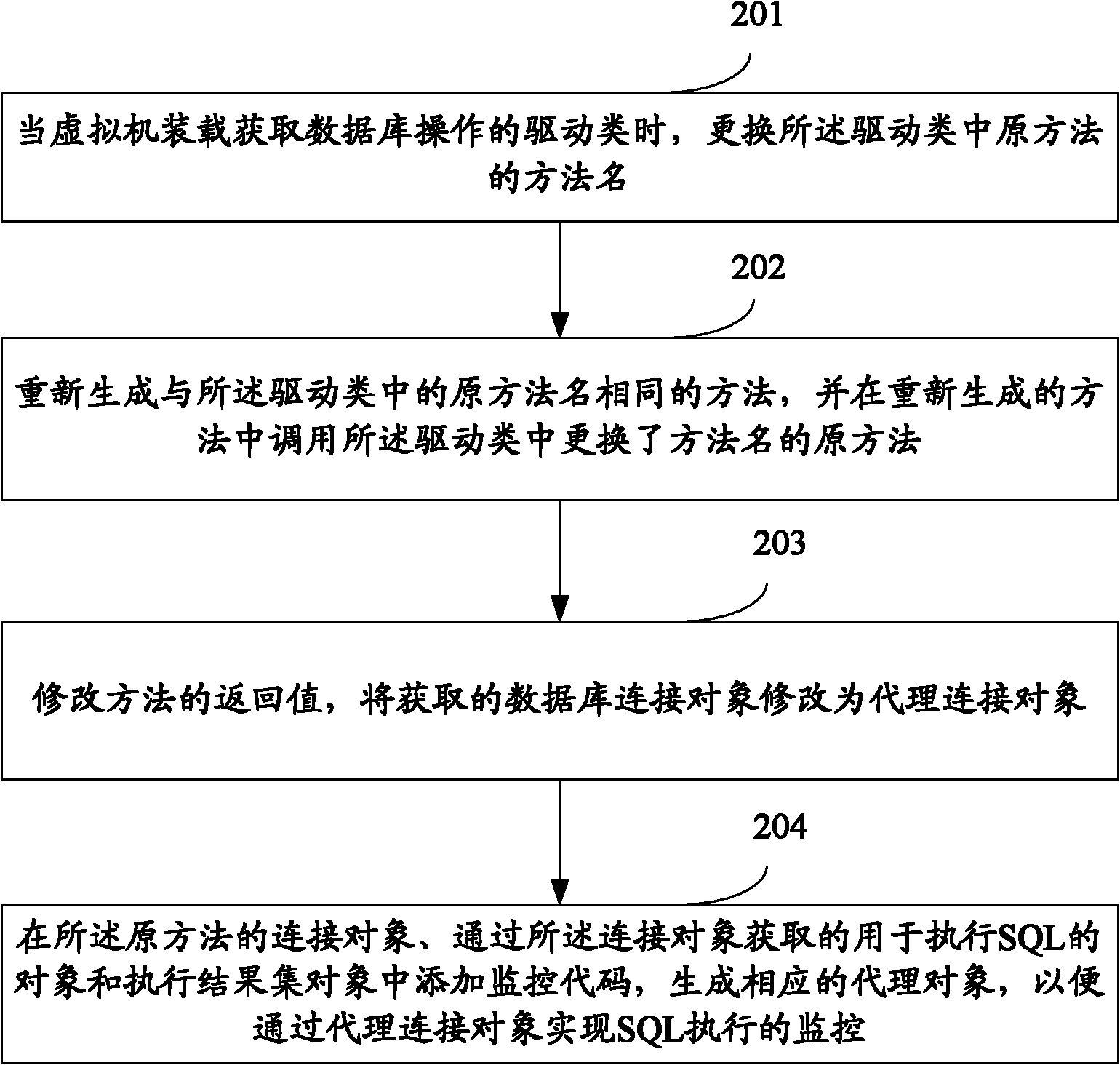
[0026] see figure 2 , which is a flowchart of an embodiment of a method for implementing SQL database monitoring in the present application, the method includes the following steps:
[0027] Step 201: When the virtual machine loads the driver class for obtaining database operations, replace the method name of the original method in the driver class;
[0028] For example, in a business application system using the Spring framework, when the virtual machine loads the driver class DriverManagerDataSource that performs database operations, all methods for obtaining connections are modified by bytecode injection, such as changing the method name getConnectionFromDriverManager to getConnectionFromDriverManager_$Monitor .
[0029] Step 202: Regenerate a method with the same name as the original method in the driver class, and call the original method in the driver class with the method name replaced in the regenerated method;
[0030] Still taking getConnectionFromDriver-Manager i...
Embodiment 2
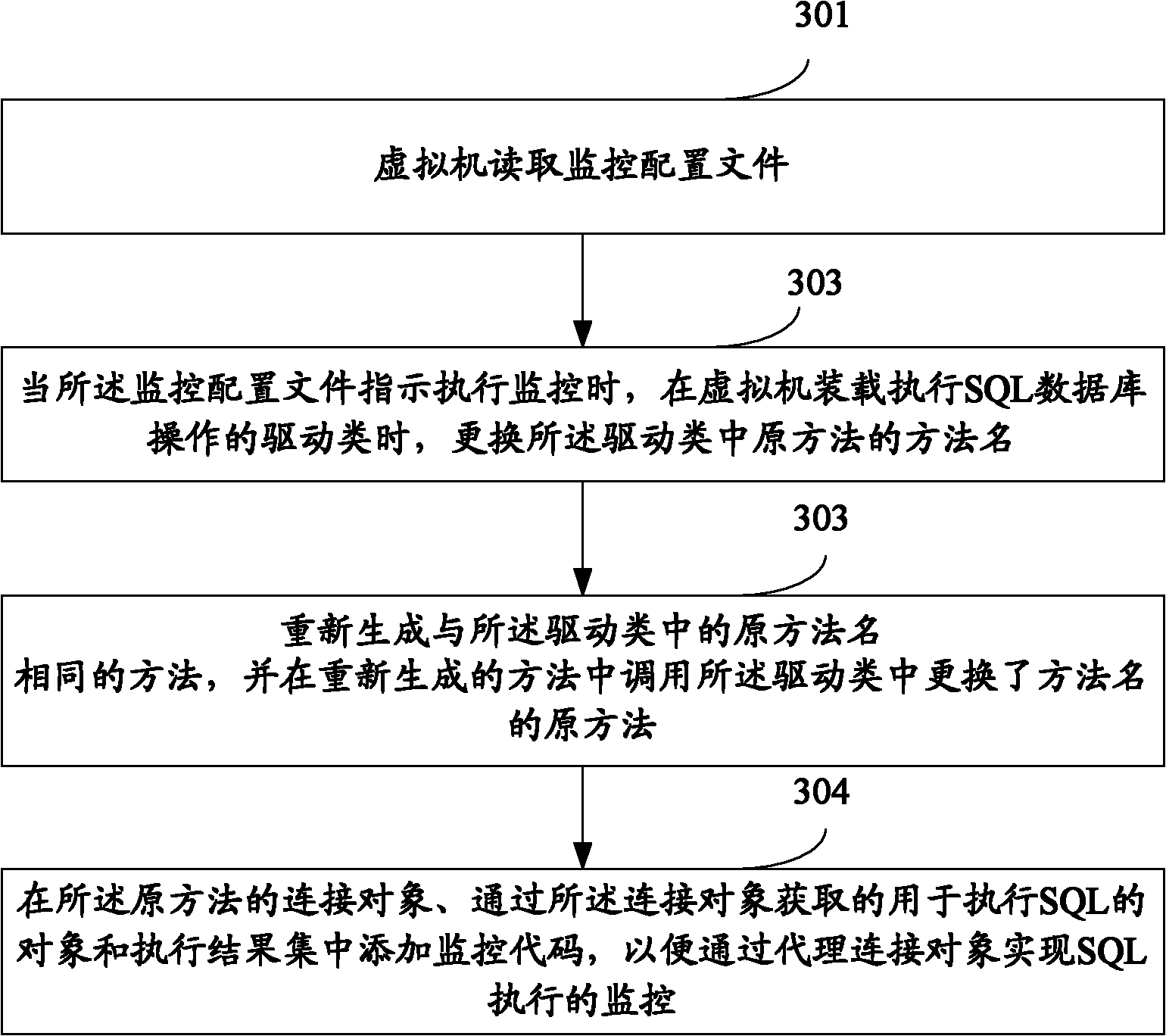
[0040]This embodiment also provides a method for realizing SQL database monitoring. The difference between this embodiment and Embodiment 1 is: before the virtual machine loads and obtains the driver class for database connection, the monitoring configuration file is read, because the monitoring configuration file indicates Therefore, according to the instructions of the monitoring configuration file, the virtual machine modifies the driver class to the agent driver class only when monitoring needs to be performed. see image 3 , which is a flow chart of another embodiment of a method for implementing SQL database monitoring in the present application, the method includes the following steps:
[0041] Step 301: the virtual machine reads the monitoring configuration file;
[0042] Step 302: When the monitoring configuration file indicates to perform monitoring, when the virtual machine loads the driver class for obtaining the database connection, replace the method name of the...
Embodiment 3
[0052] This embodiment provides a method for completing SQL monitoring by proxying the driver class of the database. see Figure 4 , which is a flow chart of another embodiment of a method for implementing SQL database monitoring in the present application, the method includes the following steps:
[0053] Step 401: Obtain the proxy connection class through the modified database driver class;
[0054] Step 402: The proxy connection class records monitoring information while completing the original connection function, and the execution object obtained through the proxy connection class is a proxy Statement object (eg, ProxyStatement);
[0055] Step 403: the proxy execution object ProxyStatement records monitoring information while executing SQL;
[0056] Step 404: The proxy result set object ProxyResultSet records the result set information.
[0057] It can be seen from the above embodiments that, unlike the prior art, the embodiment of the present application modifies the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com