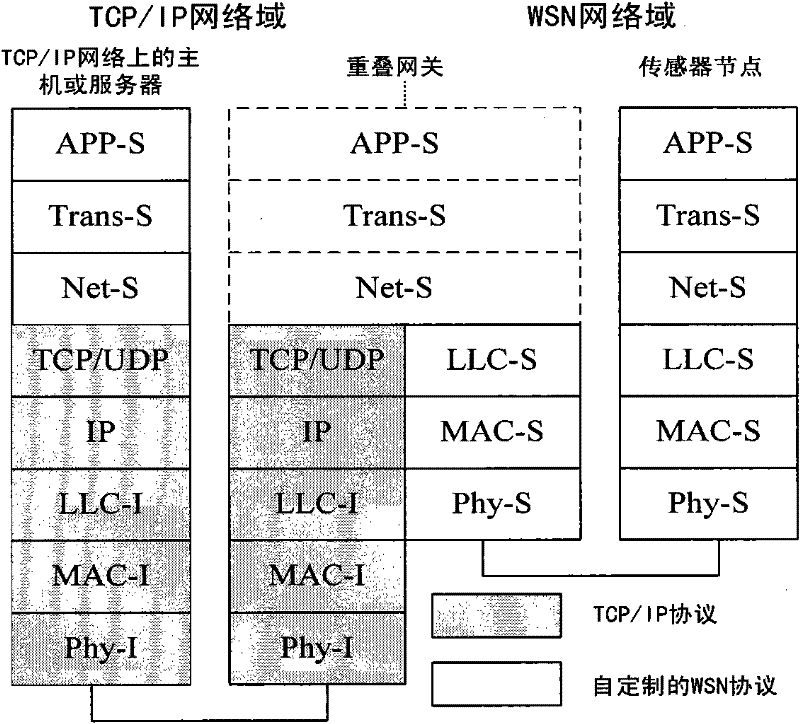
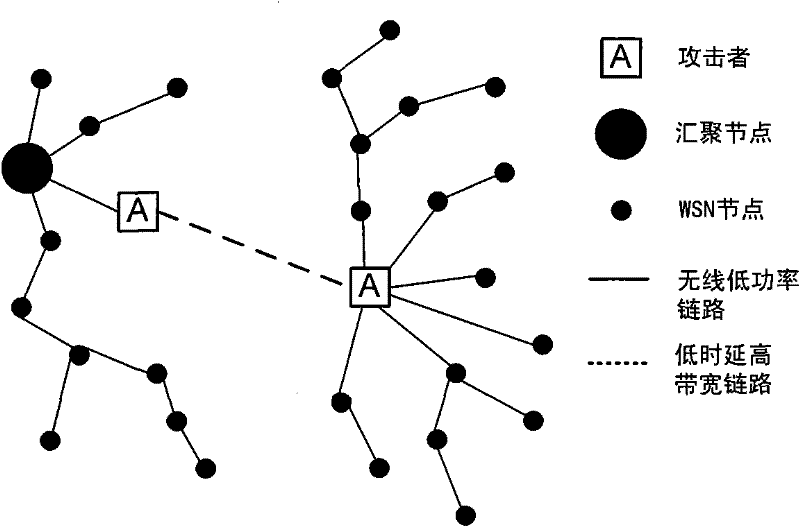
Secure routing method for converged network of wireless sensor network and computer network
A technology of wireless sensor network and fusion network, which is applied in the field of secure routing of wireless sensor network and computer network fusion network, can solve the problems of limited research work, achieve the effects of prolonging the life span, resisting selective forwarding attacks, and expanding the scale
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
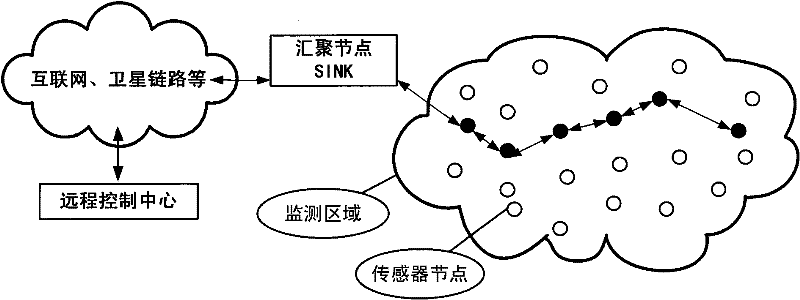
[0066] Figure 5 The secure routing method of wireless sensor network and computer network fusion network of the present invention is shown, comprising the following steps:
[0067] A) the whole fusion network is divided into several clusters, each cluster includes a cluster head node and some member nodes selected before each round of communication;
[0068] B) After the cluster is established, the aggregation node starts and establishes the multi-hop multi-path of the inter-cluster nodes by broadcasting the routing discovery packet (Route-Find-Pkt);
[0069] C) The cluster head node monitors the forwarding behavior of the neighbor cluster head node, and adjusts the trust value of the neighbor cluster head node according to the monitoring result, and the sink node collects the trust value information reported by each cluster head node in the network, and real-time Evaluate the running status of each cluster head node, and generate notification messages of different levels ac...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com