Memory leak positioning method, server, client and system
A memory leak and server-side technology, applied in the network field, can solve problems such as memory leaks and impossibility, and achieve the effect of improving speed and efficiency and being easy to operate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
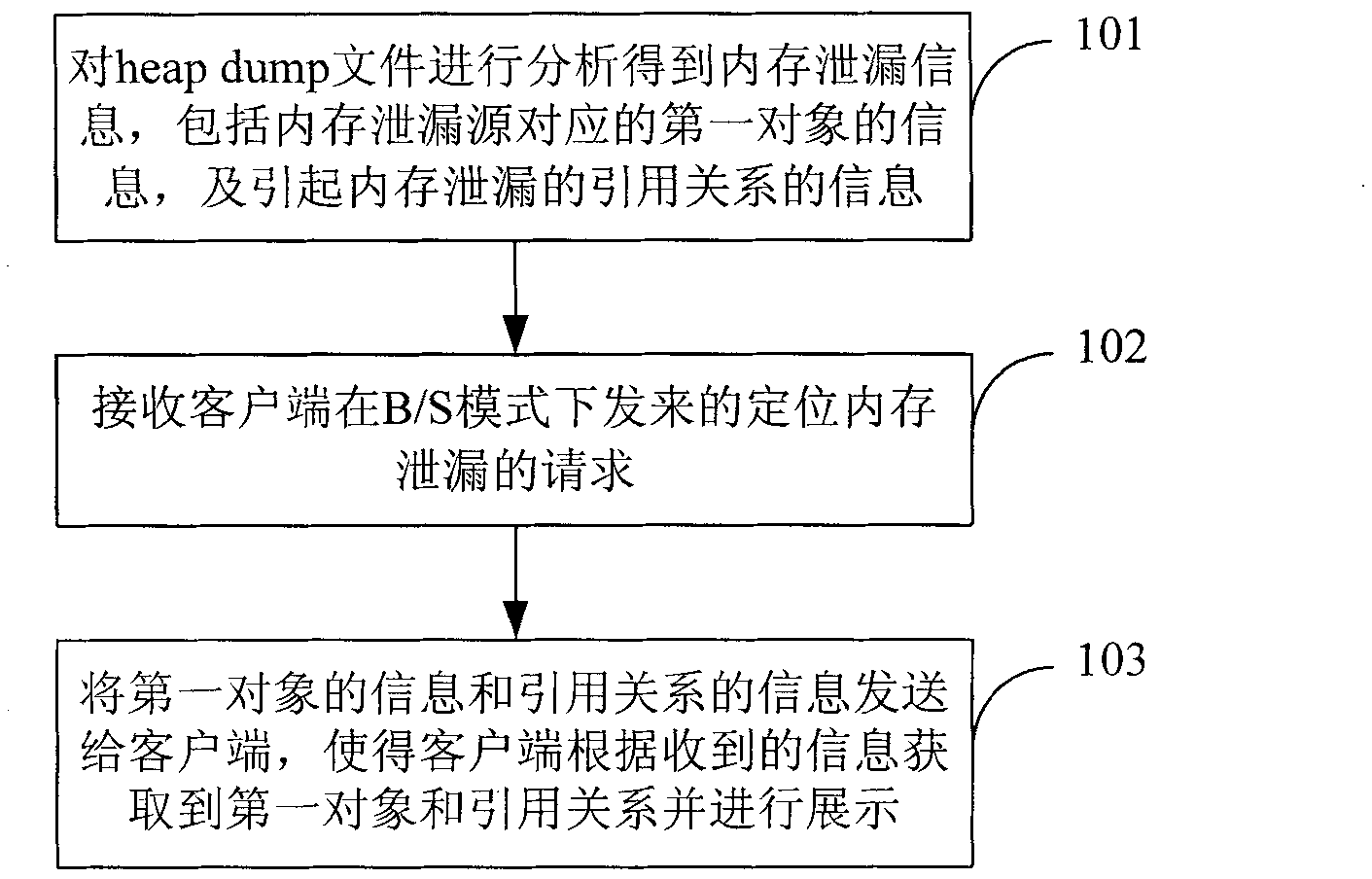
[0047] For remote location of memory leaks, see figure 1 , this embodiment provides a method for locating memory leaks, including:
[0048]101: Analyze the heap dump file to obtain memory leak information. The memory leak information includes information about the first object corresponding to the source of the memory leak, and information about the reference relationship that causes the memory leak. The termination object of the reference relationship is the first object. object;
[0049] In this embodiment, the source of the memory leak refers to the place where the memory leak directly occurs during the running of the program. The program usually includes multiple objects, and multiple reference relationships usually exist among the multiple objects. One memory leak may occur when the program is running, or multiple memory leaks may occur, and each memory leak source corresponds to an object. When multiple memory leaks occur, analyze the heap dump file to obtain objects ...
Embodiment 2
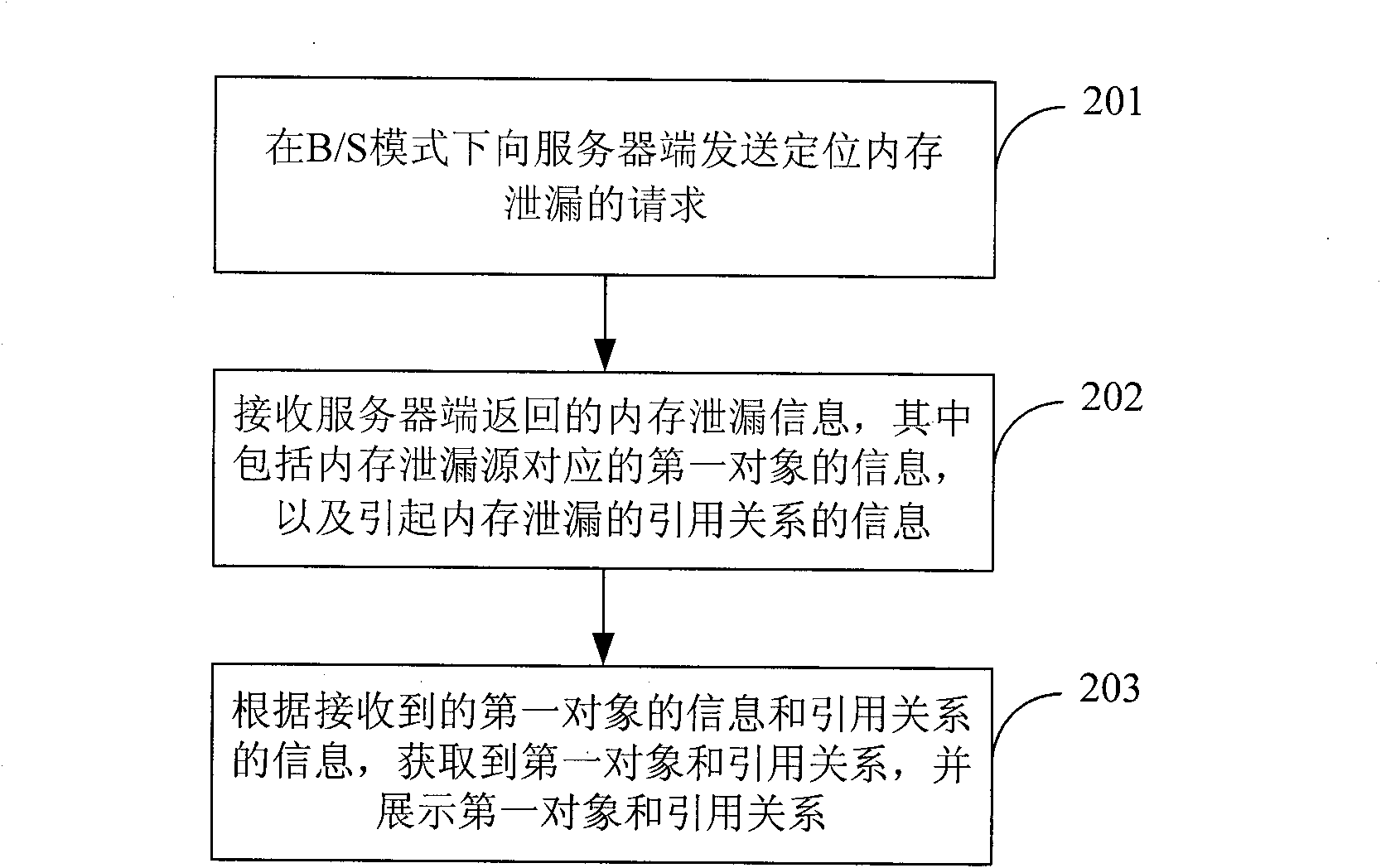
[0057] For remote location of memory leaks, see figure 2 , this embodiment provides a method for locating memory leaks, including:
[0058] 201: Send a request to locate a memory leak to the server in B / S mode;
[0059] 202: Receive the memory leak information returned by the server. The memory leak information includes the information of the first object corresponding to the source of the memory leak and the information of the reference relationship causing the memory leak. The end object of the reference relationship is the first object, and the The memory leak information is obtained after analyzing the heap dump file on the server side;
[0060] 203: Acquire the first object and the reference relationship according to the received information of the first object and the information of the reference relationship, and display the first object and the reference relationship.
[0061] The method provided by this embodiment is usually implemented on the client side, which us...
Embodiment 3
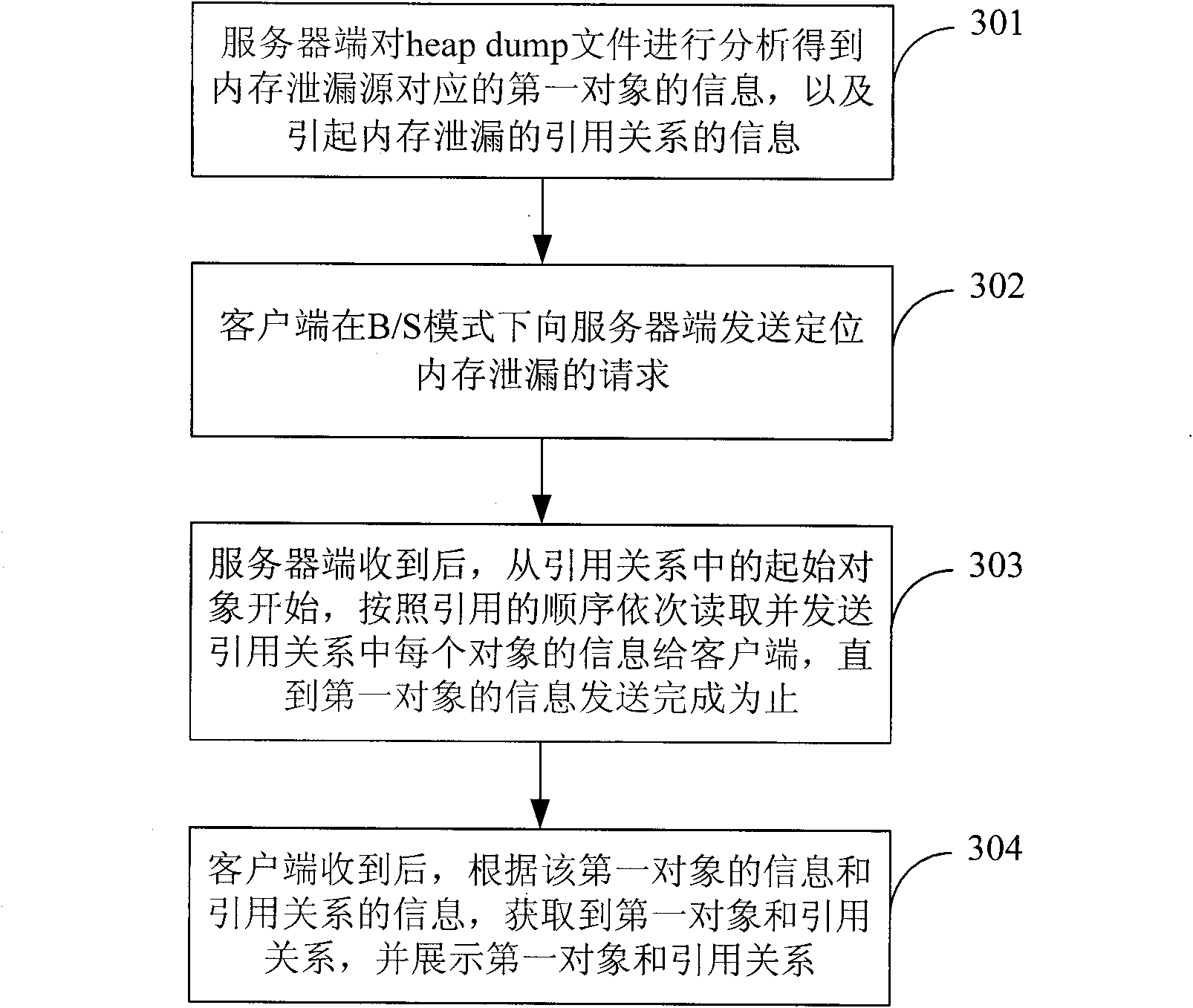
[0064] In order to realize remote location of memory leaks and prevent memory leak information confusion caused by multiple requests, see image 3 , this embodiment provides a method for locating memory leaks, including:
[0065] 301: The server analyzes the heap dump file to obtain memory leak information. The memory leak information includes information about the first object corresponding to the source of the memory leak, and information about the reference relationship that causes the memory leak. The termination object of the reference relationship is first object;
[0066] 302: The client sends a request to locate a memory leak to the server in B / S mode;
[0067] In this embodiment, the server and the client interact based on the web. The client sends a request to the server through an existing browser, and the browser receives the information returned by the server, and then displays it to the user. Specifically, AJAX (Asynchronous JavaScript and Extensible Markup Lan...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com