Identity and authentication system using aliases
An alias and identity technology, applied in the field of identity and verification systems using aliases, can solve problems such as not being able to meet all the needs of online communities
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
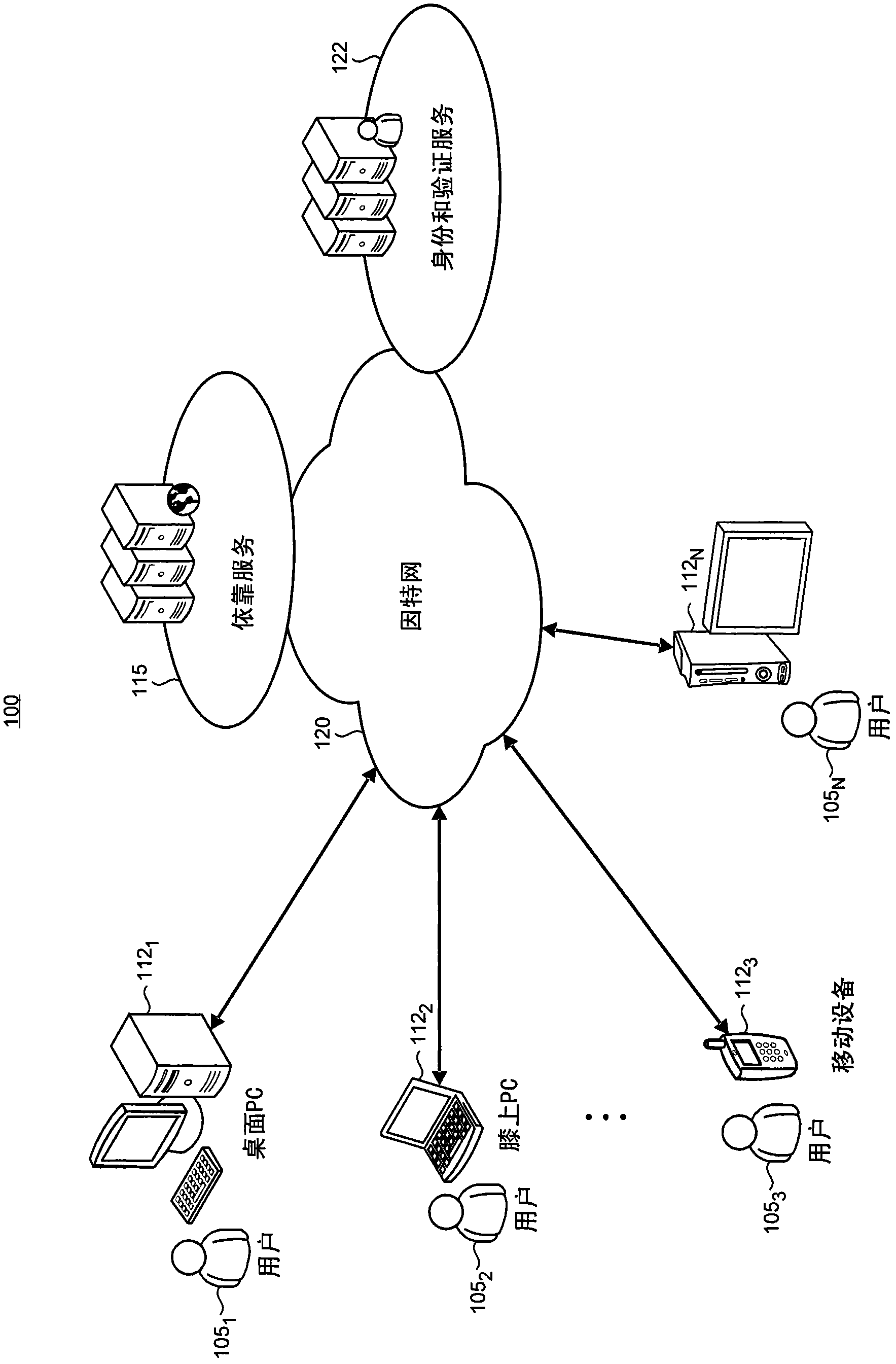
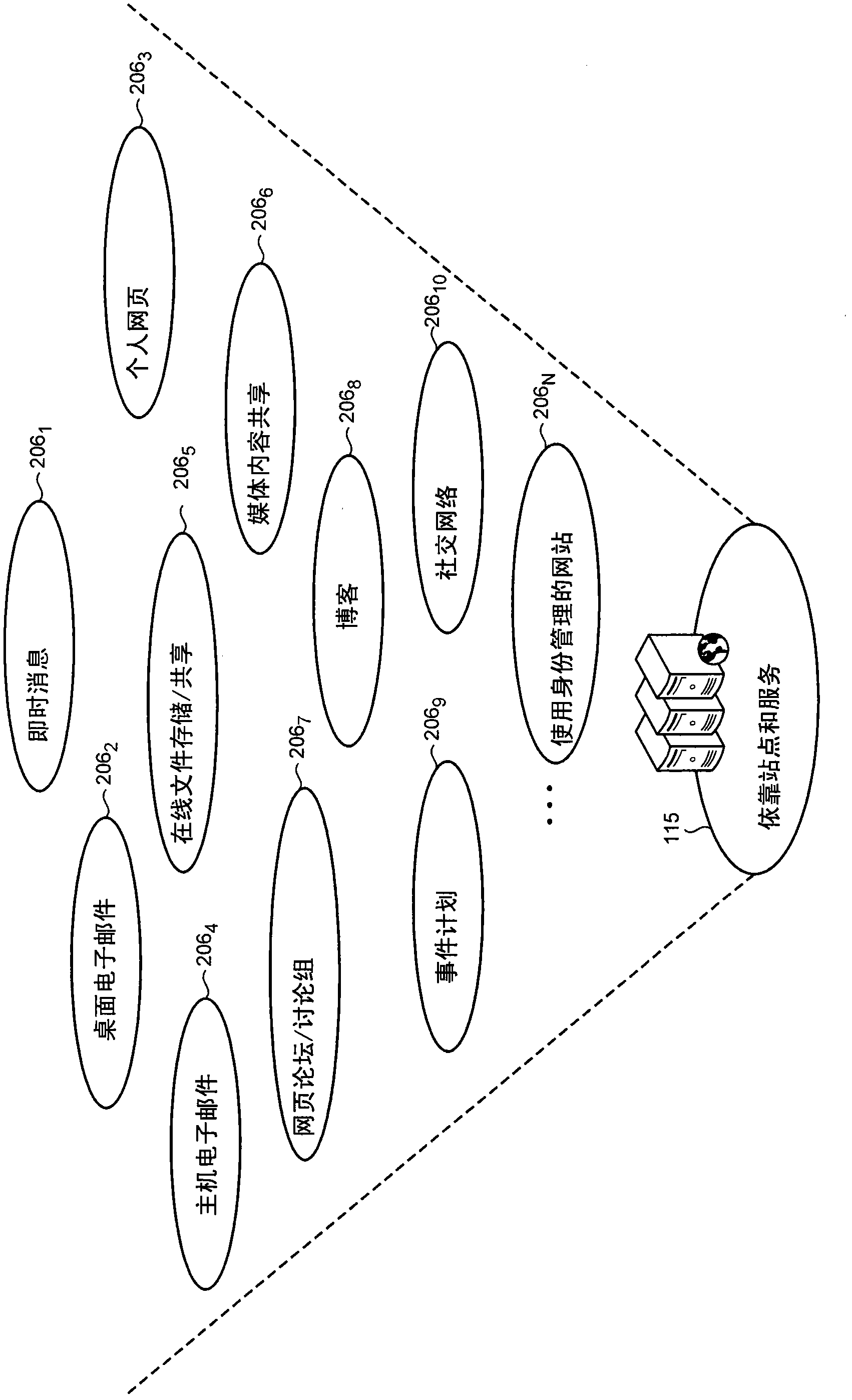
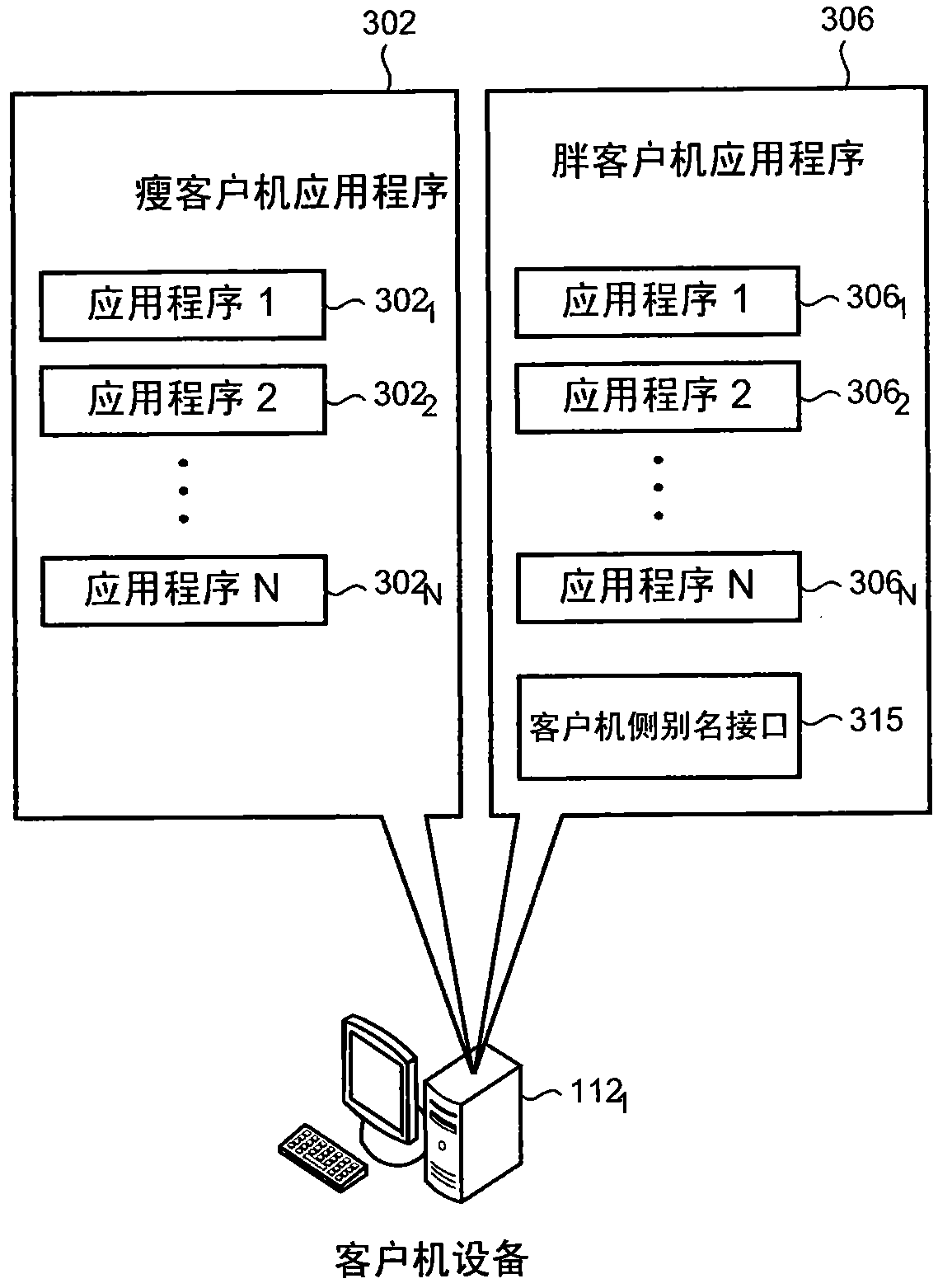
[0023] Computer users often maintain different identities for different online sites and services. A single user can use various identifiers, such as email addresses, nicknames, user names, mobile phone numbers, game names or IDs, and other structures to reflect the user's online identity at different times and in different settings. Therefore, for example, a user can utilize a mobile phone number based on an existing network service, such as instant messaging ("IM") that can be operated with a mobile phone based on an existing network service. In addition, users can log in to online social networking sites with their usernames and use email addresses when logging in to their frequent flyer accounts.
[0024] Users can find it troublesome to maintain multiple scattered identities. For example, because more and more sites and services require account creation to use them, the proliferation of different account names and passwords will lead to user "password fatigue". For these u...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com