Active learning based network data anomaly detection method
A network data and anomaly detection technology, applied in data exchange networks, digital transmission systems, instruments, etc., can solve the problems of many training samples, difficult to have good classification characteristics, and high complexity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach 1
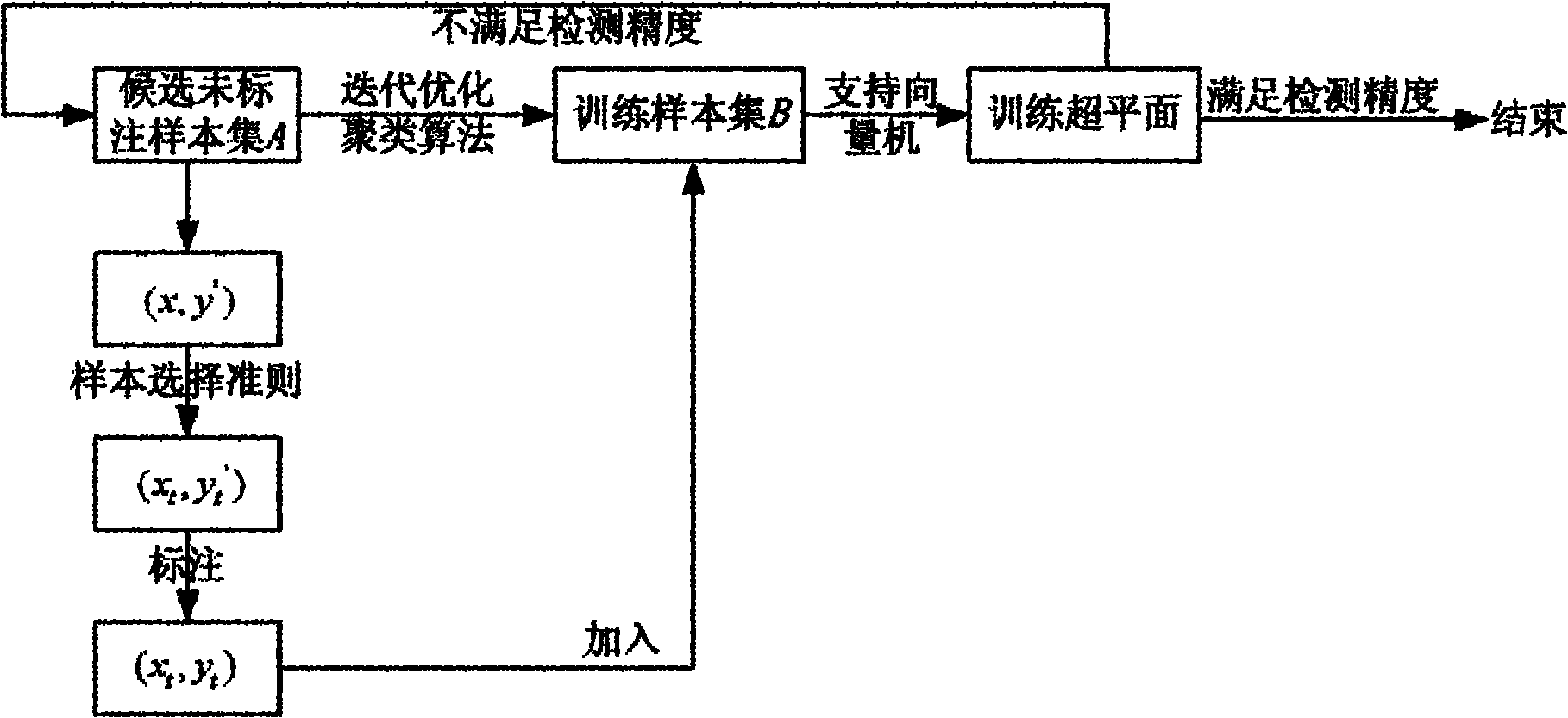
[0014] Specific implementation mode one: combine figure 1 To illustrate this embodiment, in the active learning mode, the training samples are actively selected according to the learning process, and the learning process is: the initialization phase and the cyclic learning phase, and the specific steps are as follows:
[0015] Candidate unlabeled sample set A, training sample set B, the number of samples in the initial training set N, and the number of current training samples n.
[0016] Step 1: Select C points in the unlabeled samples of candidate unlabeled sample set A as candidate cluster centers, perform iterative optimization clustering operation on candidate unlabeled sample set A, and select representative samples in the iterative clustering results Build a training sample set B;
[0017] The classification function surface of the support vector machine is a hyperplane H in the kernel space, and the hyperplane trained on the initial training set is H s , the actual o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com