Method for authorizing user equipment migration and network access server
A technology for user equipment and network access, applied in the field of network security, can solve problems such as unfavorable system operation and potential safety hazards in processing processes, and achieve the effect of preventing forgery attacks and maintaining rights
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0040]In this section of the detailed description, there is shown and described the preferred embodiment of the invention by way of illustration only of the best mode contemplated by the inventors for carrying out the invention. As will be realized, the invention may be modified in various obvious respects without departing from the invention. Accordingly, the drawings and description are to be regarded as illustrative in nature and not restrictive.
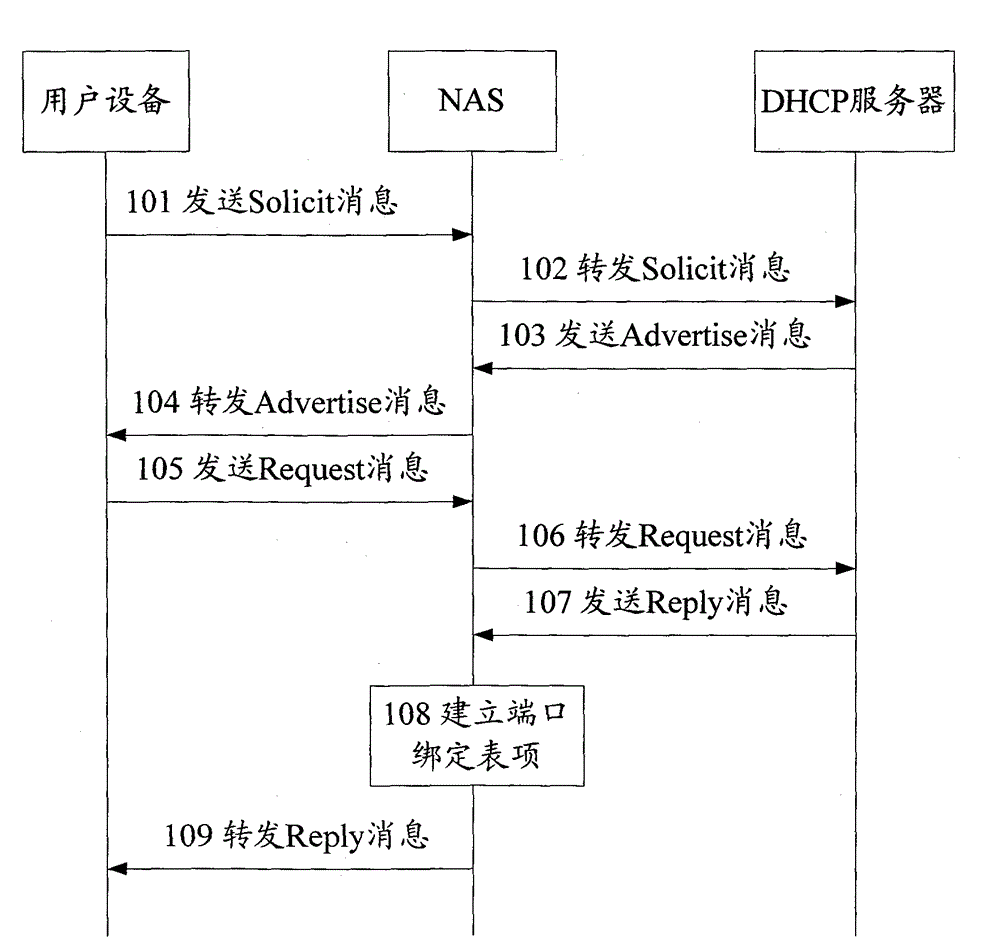
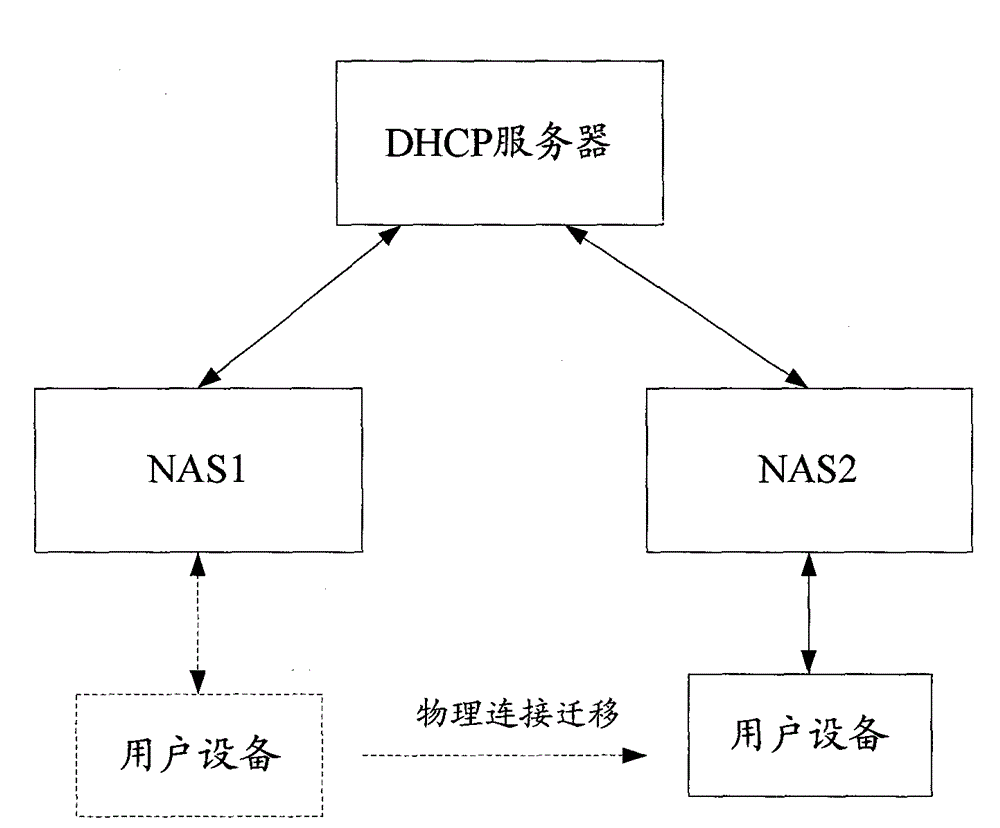
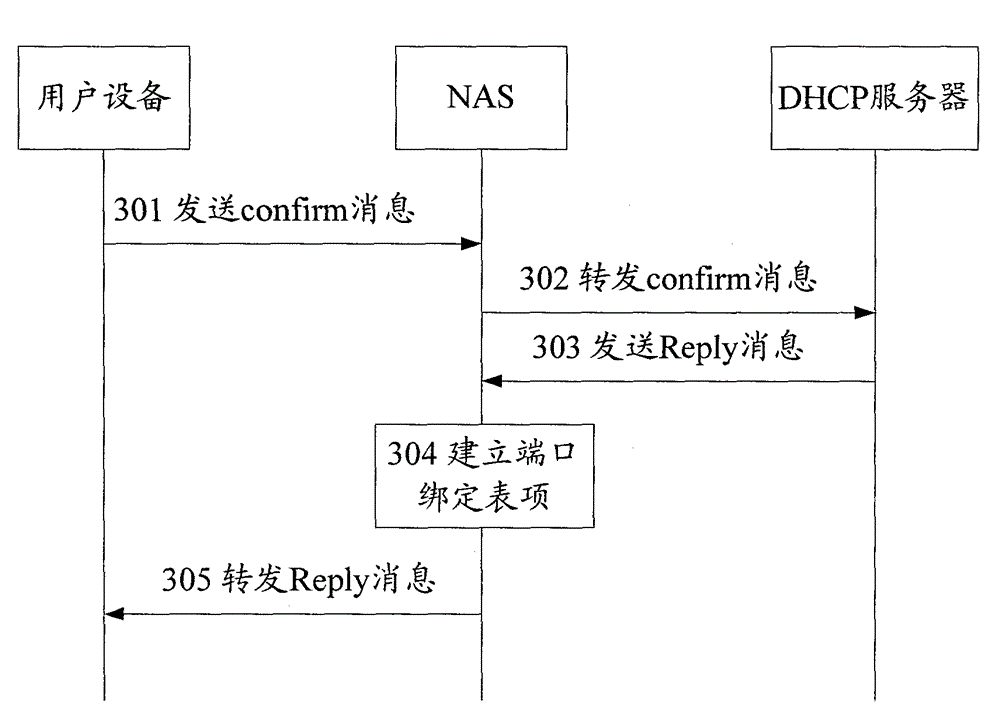
[0041] In order to prevent the forgery attack initiated by the attacker, in the technical solution of the present invention, when assigning the IPv6 address / prefix, record the correspondence between the assigned IPv6 address / prefix and the MAC address of the NAS accessed by the user equipment; After the physical connection migration of the user equipment occurs, check whether there is a user equipment using the IPv6 address / prefix under the original NAS according to the corresponding relationship. If it exists, refuse to generate...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com