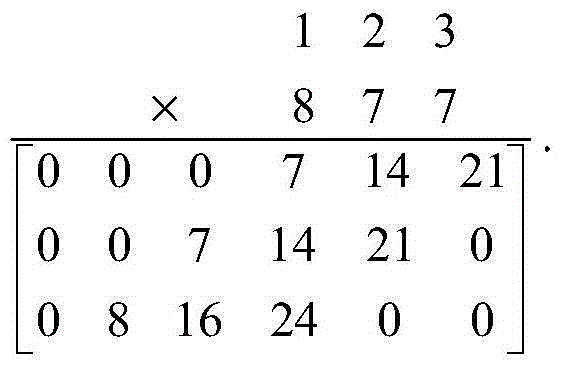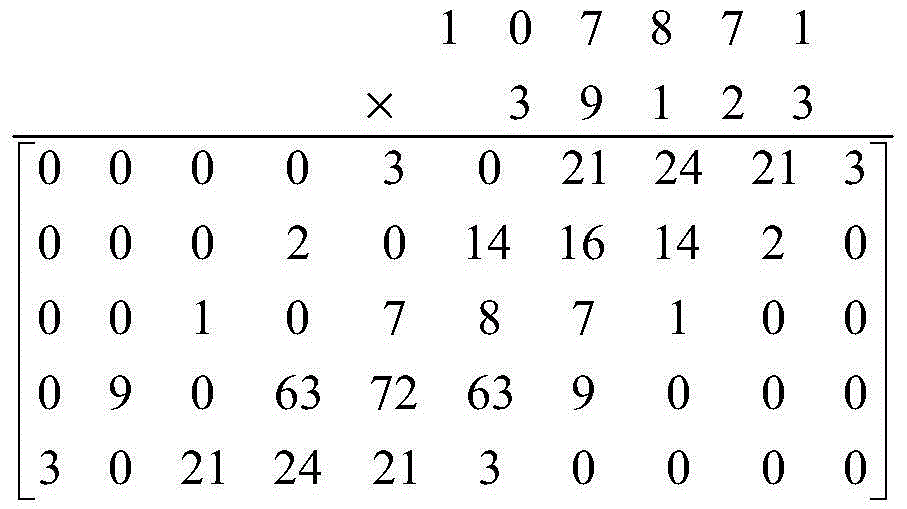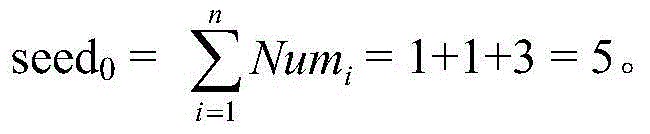Hash algorithm based on extensible precision chaos
A technology of extended precision and information security, which is applied in the fields of pattern matching, computer science, digital communication, computer security, information security, and cryptography. and other issues to achieve the effect of convenient selection and reduction of conflicts
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
[0059] Example 1: A hash table based on scalable precision chaos.
[0060] Here we assume that the input information is three numbers 123 (keywords), and the address space of the hash table is 0 to 20.
[0061] The specific steps to implement the hash table based on scalable precision chaos are as follows:
[0062] (1) The input information is used as the initial parameters and control parameters based on the scalable precision Logistic mapping, and the number of iterations of the Logistic mapping and the number of digits (precision) of the random sequence obtained by specifying the Logistic mapping are set.
[0063] The input information is used as the initial parameters and control parameters of the Logistic mapping, respectively:
[0064] x0=0. 123 , a=3.9 123 .
[0065] Set the number of Logistic mapping iterations equal to 2, and specify that the number of digits of the obtained random sequence is equal to 20.
[0066] (2) Extensible precision chaotic iteration is pe...
example 2
[0106] Example 2: Information summarization based on scalable precision chaos.
[0107]Here we assume that the input information is a letter "q", and the length of the specified output information summary is 500 decimal digits.
[0108] The specific steps of information summarization based on scalable precision chaos are as follows:
[0109] (1) The input information is used as the initial parameters and control parameters based on the scalable precision Logistic mapping, and the number of iterations of the Logistic mapping and the number of digits (precision) of the random sequence obtained by specifying the Logistic mapping are set.
[0110] The input information is used as the initial parameters and control parameters of the Logistic mapping. Here we extract the ASCII code value (113) of the letter "q". The initial parameters and control parameters of the Logistic mapping are:
[0111] x 0 =0. 113 , a=3.9 113 .
[0112] Set the number of Logistic mapping iterations equ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com