Key recovery mechanism for cryptographic systems
A cryptographic system and key technology, applied in the field of cryptographic systems, can solve problems such as damage to keys and their scheduling secrecy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0018] Implementation of AES Encryption Engine
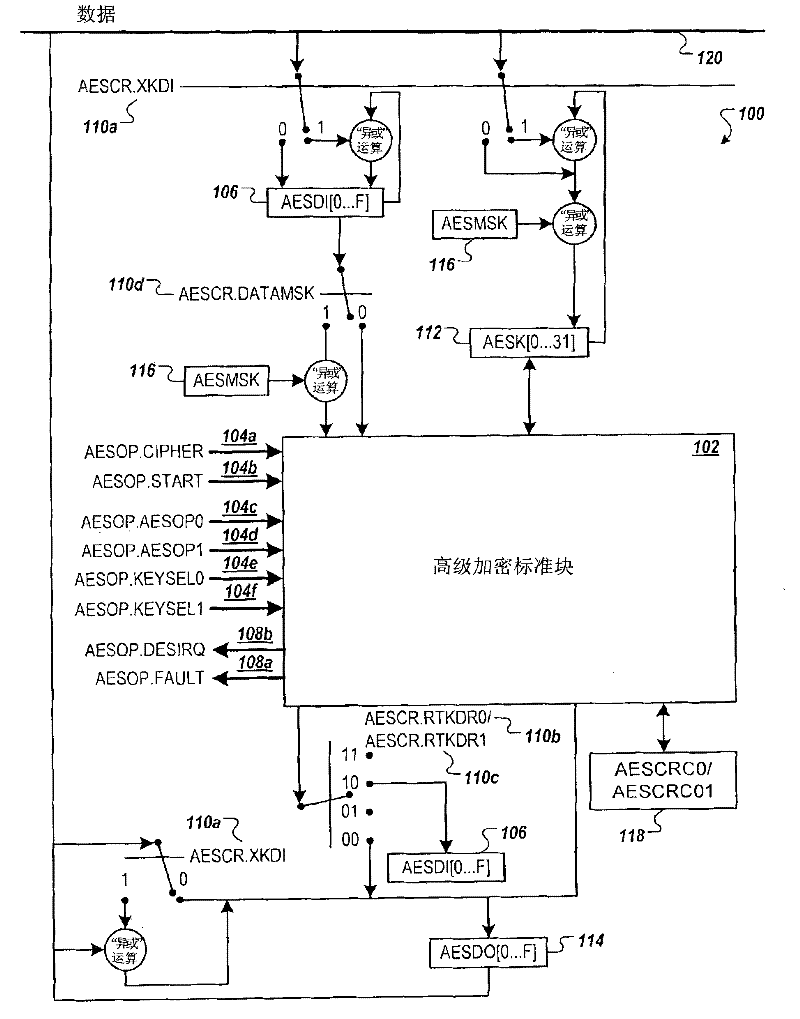
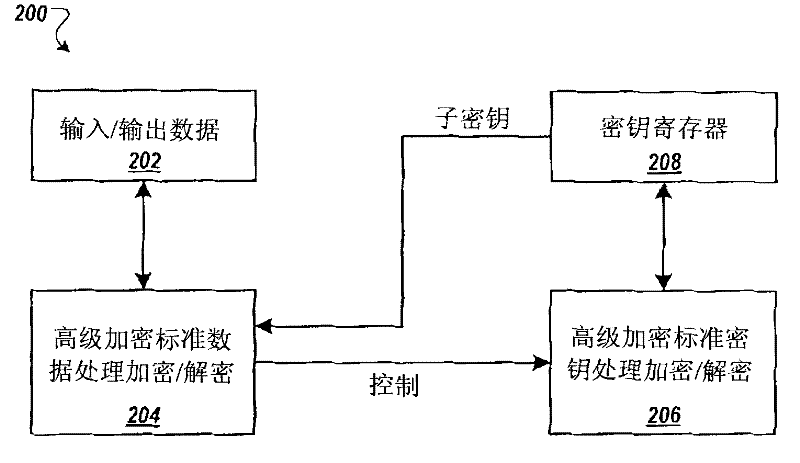
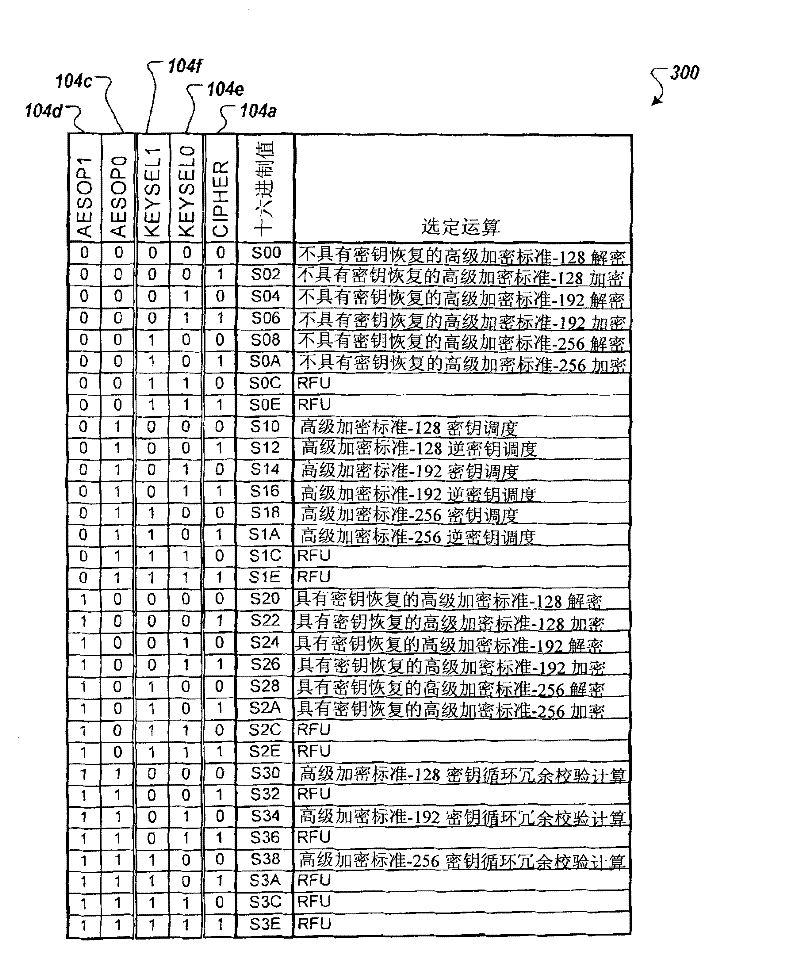
[0019] figure 1 is a block diagram of an example implementation of an Advanced Encryption Standard (AES) cryptographic engine 100 . Engine 100 may perform AES calculations, which may include AES encryption and decryption operations on blocks of electronic data to generate ciphertext and plaintext, respectively. Engine 100 may be included in a cryptographic system.
[0020] like figure 1 As shown in , the engine 100 includes registers that can provide inputs to the AES block 102 that enable and control the AES encryption and decryption operations performed by the AES block 102 . Registers may provide data (eg, ciphertext or plaintext) for AES operations. The registers may provide cryptographic key data for use in AES encryption and decryption operations. In addition, the registers may provide result and status information related to the AES operations performed by the AES block 102 . A register may provide the resulting dat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com